Domain Persistence AdminSDHolder
In this post, we will discuss the Persistence attack on Active Directory by abusing AdminSDHolder. This attack is an actual threat because of This attack leverage into another dynamic attack such as DCSync Attack and Golden ticket Attack.
AdminSDHolder
Active Directory Domain Services uses AdminSDHolder, protected groups and Security Descriptor propagator (SD propagator or SDPROP for short) to secure privileged users and groups from unintentional modification. Unlike most objects in the Active Directory domain, which are owned by the Administrators group, AdminSDHolder is owned by the Domain Admins group.
The AdminSDHolder object has a unique Access Control List (ACL), which is used to control the permissions of security principals that are members of built-in privileged Active Directory groups. Every hour, a background process runs on the domain controller to compare manual modifications to an ACL and overwrites them so that the ACL matches the ACL on the AdminSDHolder object.
Read from here for more detail.
AdminSDHolder Persistence Attack
On compromised domain controller with administrator privilege, the attacker is capable to create a permanent backdoor for his future attack by abusing AdminSDHolder. With the help of this attack, we will be able to alter AdminSDHolder by adding a new user to its Access Control List.
Here we will try to add user Yashika into ACL of AdminSDHolder object in order to change privilege for user yashika. Current User yashika is a domain user as shown below.

Follow the step to learn how an attacker can conduct AdminSDHolder attack.
- Navigate to Active Director User and Computers
- Explore Menu > View> Advanced Features

- Explore System > AdminSDHolder > Properties

- Add user to whom you want to give Full Permission. Here I have chosen user: “Yashika”

5.Give Full Permission by enabling All check box.
As we mention background process runs, by default, every sixty (60) minutes but default frequency for running Security Descriptor Propagator process could be changed by creating a REG_DWORD registry entry and setting the new frequency value.
This can be done on compromised DC by executing the following command inside command prompt which will reset Security Descriptor Propagator process for 3 minutes (300 as decimal & 12c as hexadecimal)
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Parameters /V AdminSDProtectFrequency /T REG_DWORD /F /D 300
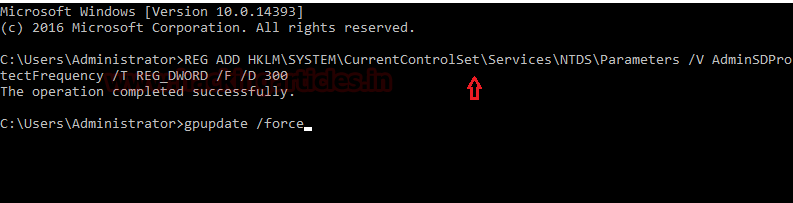
To ensure the fruitful result of the above command, explore the following path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters

After three minutes we checked to identify for user “yashika” using net user command and notice Yashika has become the member of the domain admin group.
net user yashika /Domain
Even if the administrator tries to remove yashika form domain admin group then after 3 minute due to Security Descriptor Propagator process it will again add Yashika into Domain Admin Group.

Good post