DOS Attack Penetration Testing (Part 2)
In our previous “DOS Attack Penetration testing” we had described several scenarios of DOS attack and receive alert for Dos attack through snort. DOS can be performed in many ways either using a command line tool such as Hping3 or GUI based tool. So today you will learn how to Perform Dos attack using GUI tools as well as a command line tool and get an alert through snort.
Let start!!
TCP Flood Attack using LOIC
As we have described in our both article Part 1 and part 2 that in target system Snort is working as NIDS for analyzing network traffic packets. Therefore first we had built a rule for in snort to analysis random TCP packets coming in our network rapidity.
Execute given below command in ubuntu’s terminal to open snort local rule file in text editor.
sudo gedit /etc/snort/rules/local.rules alert TCP any any -> 192.168.1.10 any (msg: "TCP Flood"; sid:1000001;)
The above rule will monitor incoming TCP packets on 192.168.1.10 by generating alert for it as “TCP Flood”. Now turn on IDS mode of snort by executing given below command in terminal:
sudo snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i eth0

LOIC: It stands for low Orbit iron cannon which is a GUI tool developed by Praetox Technologies which is a network stress testing tool. We had used it only for educational purpose in our local network, using it over public sector will consider as crime and take an illegal job. Download it from Google.
We had downloaded LOIC in our Windows system run the setup file for installation. Start the tool follow the given below step:
- Select your target: Here we will go with IP option and enter the victims IP: 192.168.1.10 then click on Lock on the tab.
- Attack Option: Enter port no. and select method such as TCP and enter no. of threads. If you want to wait for a reply packet from the victim’s network then enable the checkbox else to disable it.
- Adjust the scale: Drawn the cursor left or right for setting the speed of your TCP packet either faster or slower mode.
- Attack status: describe the attack state such as connecting or request or etc.
- Ready: Now click on IMMA CHARGIN MAH LAZER to launch the DOS attack and click on stop flood In order to stop DOS attack.

We are involving Wireshark in this tutorial so that you can clearly see the packet sends from an attacker network to targets network. Hence in given below image, you can notice endless TCP packet has been sent on target’s network. It is considered as Volume Based DOS Attack which floods the target network by sending infinite packets to demolish its network for other legitimate users.

Return to over your target machine where you will notice that snort is exactly in same way capturing all incoming traffic, here you will observe that it is generating alerts for “TCP Flood”. Hence you can block the attacker’s IP (192.168.1.16) to protect your network from discard all further coming packets toward your network.

UDP Flood Attack using LOIC
I think now everything is clear to you how you can build rule in snort get alert for the suspicious network again repeat the same and execute given below command in ubuntu’s terminal to open snort local rule file in text editor and add a rule for UDP flood.
sudo gedit /etc/snort/rules/local.rules
alert UDP any any -> 192.168.1.10 any (msg: "UDP Flood"; sid:1000003;)
The above rule will monitor incoming UDP packets on 192.168.1.10 by generating alert for it as “UDP Flood”. Now turn on IDS mode of snort by executing given below command in terminal:
sudo snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i eth0
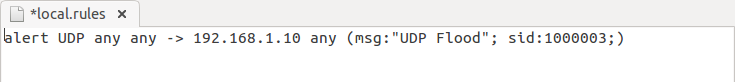
Repeat the whole steps as done above only change the method attack option to choose UDP method and launch the DOS attack on target IP. You can set any set number of threads for attack since it is tutorial, therefore, I had set 20 for UDP. It is considered as Volume Based DOS Attack which floods the target network by sending infinite packets to demolish its network for other legitimate users.
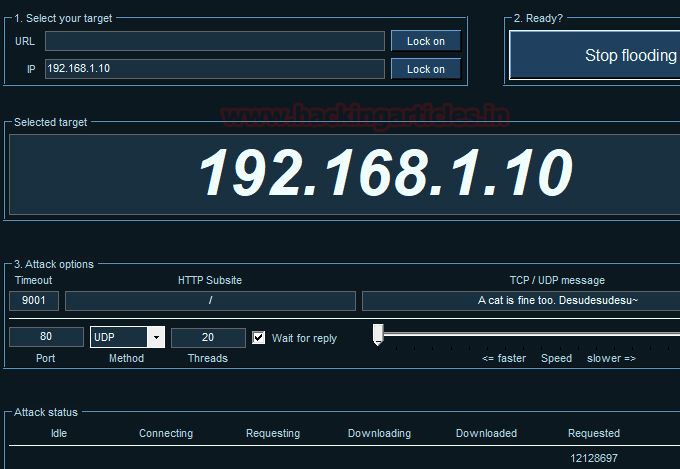
Return to over your target machine where you will observe that snort is precisely capturing all incoming traffic in the same way, here you will observe that it is generating alerts for “UDP Flood”. Hence again you can block the attacker’s IP (192.168.1.16) to protect your network from discard all further coming packets toward your network on port 80.

TCP Flood Attack using HOIC
Next, we are using HOIC which is also a GUI tool for tcp attack and if you remember we had already configured TCP flood rule in our local rule file. Now turn on IDS mode of snort by executing given below command in terminal:
sudo snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i eth0
HOIC: It stands for higher orbit ion cannon developed by Praetox Technologies which is a network stress testing tool. We had used it only for educational purpose in our local network, using it over public sector will consider as crime and take an illegal job. Download it from Google.
We had downloaded HOIC in our Windows system run the setup file for installation. Start the tool follow the given below step:
Add the target by making Click on plus symbol “+”

A list of attack option will get pop up as shown in the given below image and follow the given below step:
URL: Enter your target network address as http://192.168.1.10
Power: Low/medium/high to decide the speed of packet to bent to the target machine.
At last click on Add.

From give below image you can check the status of attack “ready”, now set number of threads and then click on FIRE THE LAZER tab to lunch the dos attack.

You can clearly observe the TCP packet is sending from the attacker network to targets network. In given below image you can notice the endless TCP packet has been sent on target’s network using TCP Flags such as SYN/RST/ACK. It is considered as Volume Based DOS Attack which floods the target network by sending infinite packets to demolish its network for other legitimate users.

Return to over your target machine where you will notice that snort is capturing all incoming traffic exactly in same way as above, here you will observe that it is generating alerts for “TCP Flood”. Hence you can block the attacker’s IP (192.168.1.11) to protect your network from discard all further coming packets toward your network on port 80.
GoldenEye
Goldeneye is a command line tool used for security testing purpose we had used only for tutorial don’t use it over public sector it will consider as crime and take an as an illegal job. Execute given below in your Kali Linux to download it from GitHub.
git clone https://github.com/jseidl/GoldenEye.git

Now give all permission to the python script and execute given below command for Launching a DOS attack on the target network. Basically, Goldeneye is used for HTTP dos testing for testing any web-server network security.
./goldeneye.py http://192.168.1.10
Using Wireshark you can observe the flow of traffic between victim and attacker network. So if notices were given below image then you will find that first attacker (192.168.1.103) sends TCP syn packet for establishing a connection with victim’s network then the attacker is sending http packet over victim’s network.

Here you will observe that it is generating alerts for “TCP Flood” since the port is 80 follow TCP protocol, therefore, snort captured the traffic generated by goldeneye. Hence you can block the attacker’s IP (192.168.1.103) to protect your network from discard all further coming packets toward your network on port 80.

Slowloris
Slowloris is a command line tool used for security testing purpose we had used only for tutorial don’t use it over public sector it will consider as crime and take an illegal job. Execute given below in your Kali Linux to download it from GitHub.
git clone https://github.com/llaera/slowloris.pl.git

Now give all permission to the Perl script and execute given below command for Launching the DOS attack on the target network.
perl slowloris.pl -dns 192.1681.10

Using Wireshark you can observe the flow of traffic between victim and attacker network. So if notices were given below image then you will find that first attacker (192.168.1.103) sends TCP syn packet for establishing a connection with victim’s network then victim’s is sending SYN, ACK packet over attacker’s network and then attacker sends ACK packet and this will keep on looping.
Return to over your target machine where you will notice that snort is capturing all incoming traffic exactly in same way as above, here you will observe that it is generating alerts for “TCP Flood”. Hence you can block the attacker’s IP (192.168.1.11) to protect your network from discard all further coming packets toward your network on port 80.

Xerxes
Xerxes is a command line tool used for security testing purpose we had used only for tutorial don’t use it over public sector it will consider as crime and take an as the illegal job. Execute given below in your Kali Linux to download it from GitHub.
git clone https://github.com/zanyarjamal/xerxes.git

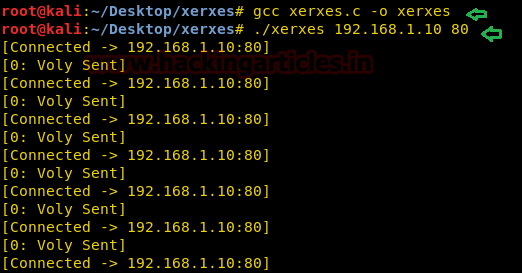
Since it is written in c language there we need to compile it using gcc as shown in given below command and run then run the script in order to launch DOS attack.
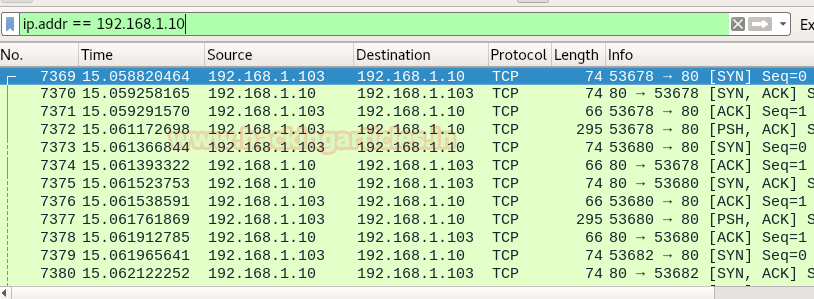
gcc xerxes.c -o xerxes ./xerxes 192.168.1.10 80
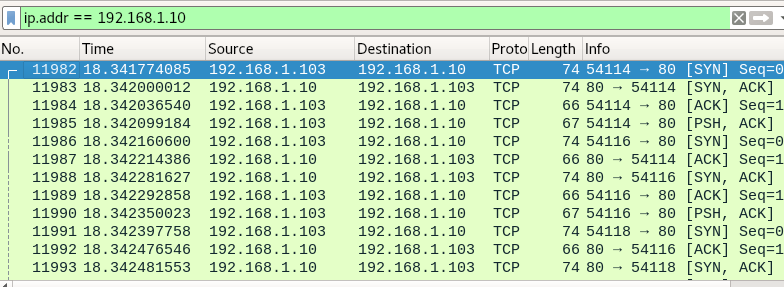
You can clearly observe the TCP packet is sending from the attacker network to targets network. In given below image you can notice the endless TCP packet has been sent on target’s network using TCP Flags such as SYN/ACK/PSH. These packets are sent in a loop between the attacker can target network.
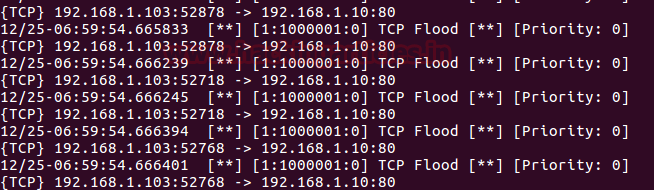
Return to over your target machine where you will notice that snort is capturing all incoming traffic exactly in same way as above, here you will observe that it is generating alerts for “TCP Flood”. Hence you can block the attacker’s IP (192.168.1.11) to protect your network from discard all further coming packets toward your network on port 80.
Well in this tutorial we had used most powerful top 5 tools for DOS attack.
Author: Rahul Virmani is a Certified Ethical Hacker and the researcher in the field of network Penetration Testing (CYBERSECURITY). Contact Here
when i use LOIC tool for dos attack . it only down the target machine only for me whereas the target machine/server is up for other user.
can you explain this.
It depends whether other user use the same zone server or the other zones. like if i use yahoo.in as my target. it down the in.yahoo not yahoo.com or yahoo.au . to down the main server it takes a lots of time.