How to study Forensics Evidence of PC using P2 Commander (Part 2)
Now we are studying about the forensic evidence which we have collected in the previous article using P2 Commander.
If you want to see the collection of forensic evidence, please click on the below link.
http://www.hackingarticles.in/how-to-collect-forensics-evidence-of-pc-using-p2-commander-part-1/
Step-by-Step Guide to Evidence Analysis in P2 Commander
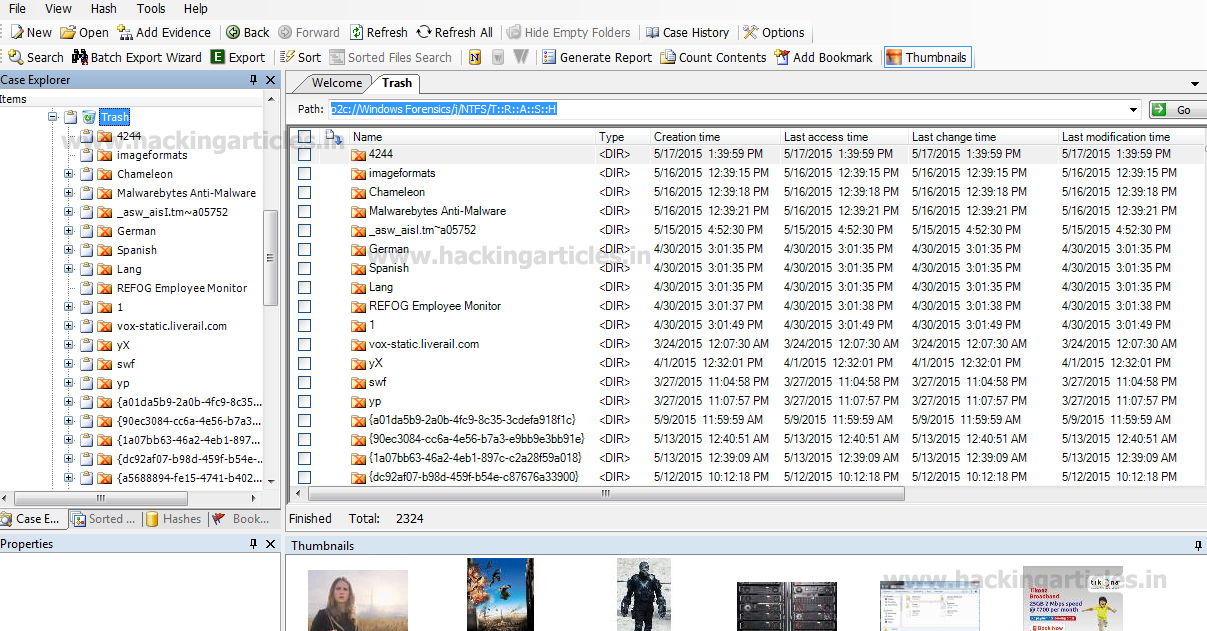
Firstly, we will look into the Trash folder (which contains the files and folders deleted by the user but not erased permanently from system yet).
By clicking on Trash folder, it will show us the different files and folders with their Creation Time, Last Access Time, Last Change Time, and File Size.
Now click on Advanced Registry and System Analyzer and then Auto Run Option.
Go to Run option. It will Show all the programs that can run automatically at the time of booting of the system.

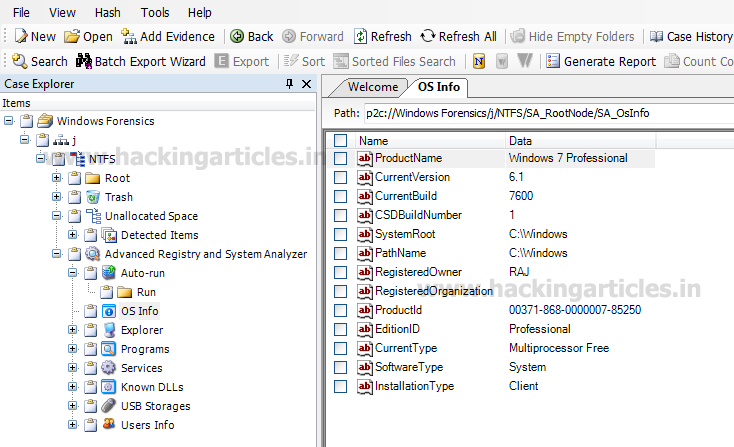
Now Select OS Info option. Through OS Info, we can see the Root Path, Current Version, Registered User, Product ID, Edition ID, and Installation Type.
Now select Uninstall Option from Programs Option. By Uninstall Option, we can see all the programs which are installed in the system.

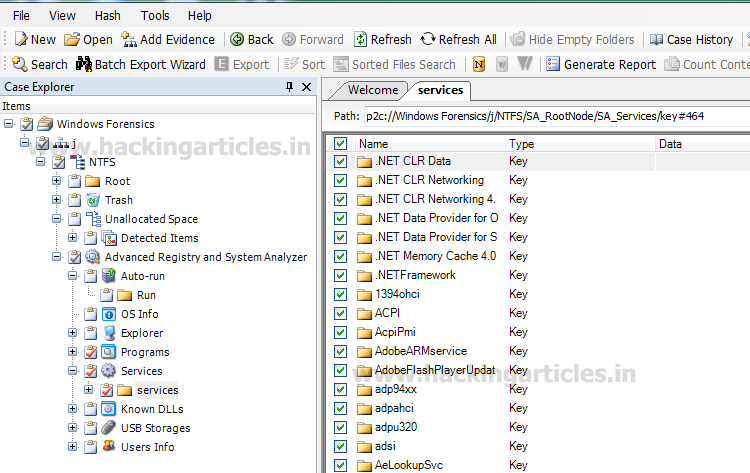
To see the running services in the system, select Services option.
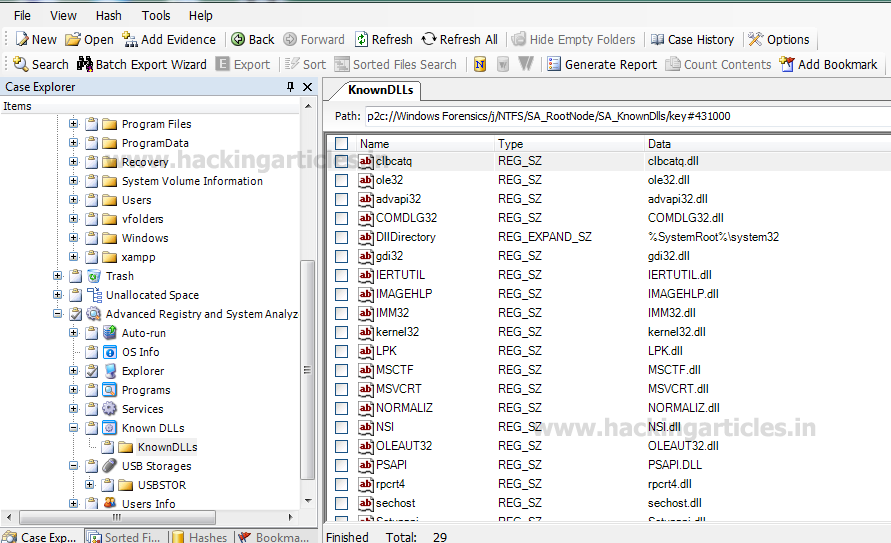
Then, click on Known DLLs to see the Dynamic Link Libraries (which different programs use simultaneously for data and code).
Now to get the information about the removable disks used recently or in the past. First click on USB Storage and then select USBSTOR. It will show the name of the Disks.
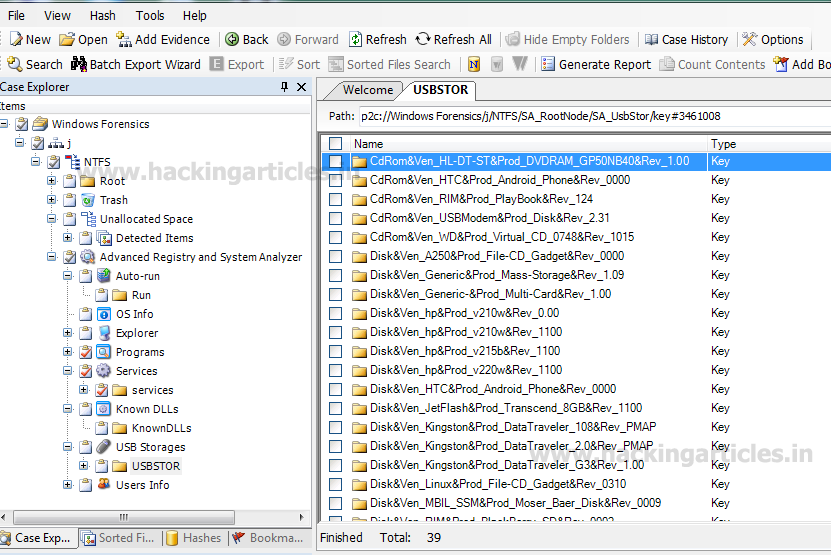
Now select any one of the disk and it will show us the size as well as the manufacturer name.

To see the history of most recently used commands from the Run command on the Start menu click on Users Info Option. Select a user; in my case we are selecting Raj. Now click on RunMRU.

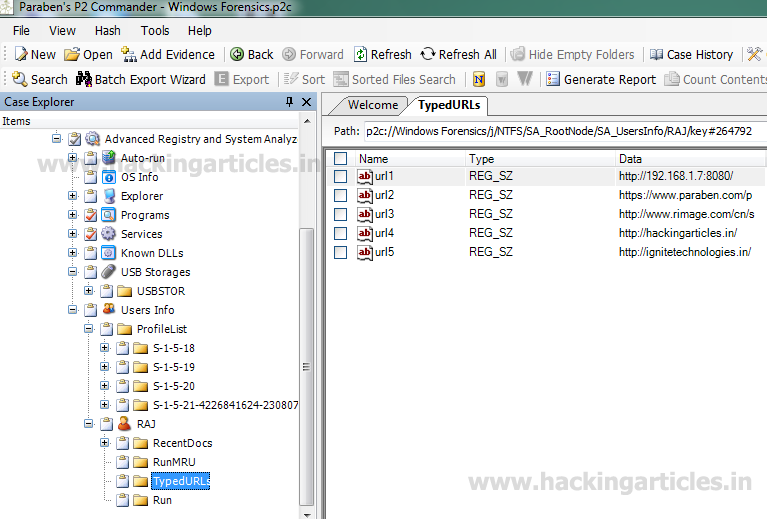
To see the user-based web activities, click on the TypedURLs, which will show the recently visited web sites.
Summary
P2 Commander offers an in-depth forensic analysis environment for registry insights, user activity tracking, connected hardware logs, and deleted file recovery — making it a vital tool in digital investigations.
Author: Mukul Mohan is a Microsoft Certified system engineer in security and messaging. He is a Microsoft Certified Technology Specialist with high level of expertise in handling server side operations based on windows platform. An experienced IT Technical Trainer with over 20 years’ Technical Training experience you can contact him at Linkedin, mukul@ignitetechnologies.in,