Web Application Pentest Lab setup Using Docker
For web application penetration practice, we all look for vulnerable applications like DVWA and attempt to configure vulnerable practice environments. As we all know, it’s time consuming activity and it takes a lot of effort, but this can be done in a couple of minutes with the help of the docker.
In this post you will learn how to configure vulnerable web applications (DVWA, BWAPP & etc) with the help of docker.
Table of Content
- Requirement
- Objective
- Web application
- DVWA
- Mutillidae
- bWAPP
- Another Method
Requirement-Ubuntu 18.0
Objective:
Configure web application server on docker
Web Application
A web application is a computer program that utilizes web browsers and web technology to perform tasks over the Internet. Web apps can be built for a wider uses which can be used by anyone; from an enterprise to an entity for a variety of reasons. Frequently used Web applications can include webmail.
Docker
Docker is a third-party tool developed to create an isolated environment to execute any application. These applications are run using containers. These containers are unique because they bring together all the dependencies of an application into a single package and deploy it. Now, to work with docker you will need to install docker-engine in your host.
Run following the command to install docker:
apt update apt install docker.io

Then execute the following command to start and enable the service of docker:
systemctl start docker systemctl enable docker
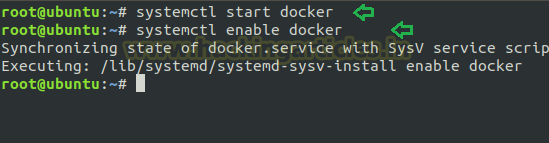
And we have installed docker version 18.09.7 in our local machine.

Configure DVWA on Docker
Damn Vulnerable Web Application (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goal is to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and to aid both students & teachers to learn about web application security in a controlled classroom environment.
The aim of DVWA is to practice some of the most common web vulnerabilities, with various levels of difficulty, with a simple straightforward interface. Please note, there are both documented and undocumented vulnerabilities with this software. This is intentional. You are encouraged to try and discover as many issues as possible.
To install and configure DVWA through docker is quite simple then manual approach, you can search for its docker image directly by typing following command on the terminal.
docker search web-dvwa

Here you can observe that it has shown the docker image for dvwa as per given rating and even you can search for the same over the internet. You will obtain the same output as shown below.

Now we can directly pull the package by executing the following command:
docker pull vulnerables/web-dvwa
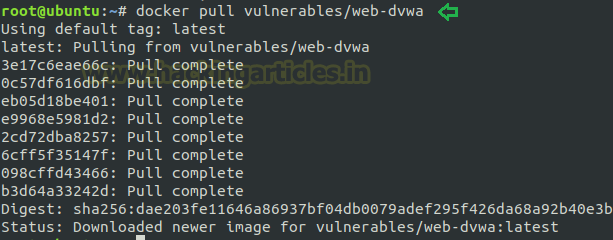
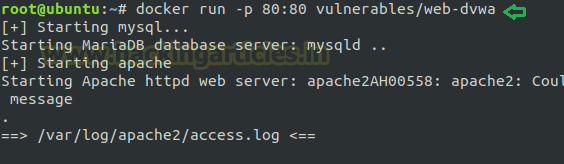
And then to start docker service for dvwa; enter below command in your terminal.
docker run -p 80:80 vulnerables/web-dvwa
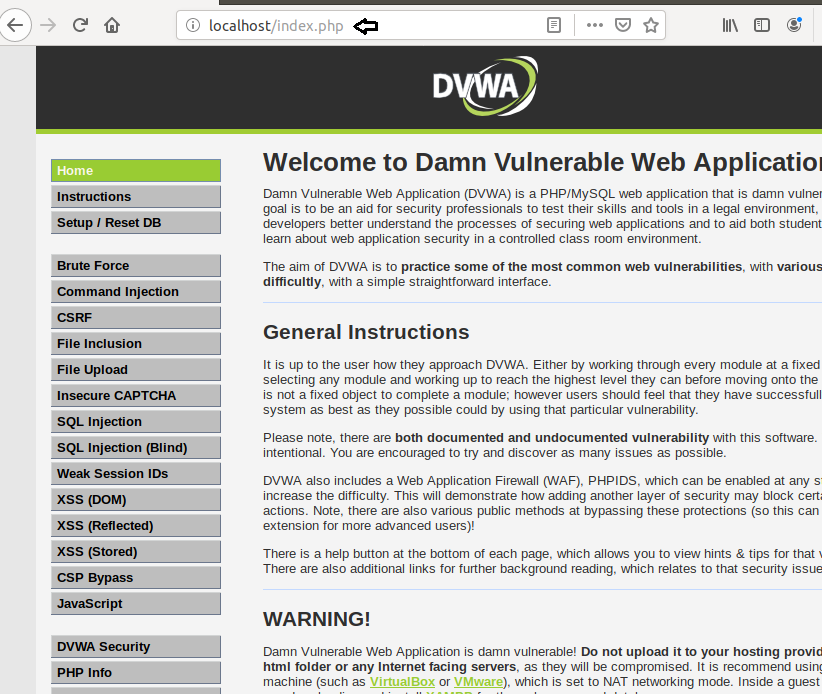
Good! We have successfully configured the dvwa lab in ubuntu as we can see that we are welcomed by the login page.

Enter the following URL and click on Create/Reset Database.
http://localhost/dvwa/setup.php

Once the database will get create you can login into application to access the web console.

And we have our DVWA application ready for use, thus we can see it required very less effort.
Configure Mutillidae on Docker
OWASP Mutillidae is a free open source purposely vulnerable web application providing an enthusiastic goal for web security. It’s a laboratory which provides a complete test environment for those who are interested in SQL injection acquisition or improvement. This is an easy-to-use Web hacking environment designed for laboratories, security lovers, classrooms, CTFs, and vulnerability assessment targets, and has dozens of vulnerabilities and tips to help the user.
Similarly, we can run mutillidae using docker without wasting much time in manual configuration. Repeat the same step as done before, first pull the package and then use the docker to start mutillidae over a specific port.
docker pull szsecurity/mutillidae docker run -p 1337:80 szsecurity/mutillidae

This time we had chosen port 1137 to launch the mutillidae application. Thus, we will open this our local browser by the following URL: localhost:1337 where we will find an option of reset database. Just click on it to reset the database.

Configure WebGoat on Docker
WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons.
This program is a demonstration of common server-side application flaws. The exercises are intended to be used by people to learn about application security and penetration testing techniques.
Similarly, we can run WebGoat using docker without wasting much time in manual configuration. Repeat the same step as done before, first pull the package and then use the docker to start WebGoat over a specific port.
docker pull szsecurity/webgoat

docker run -p 1337:80 szsecurity/webgoat
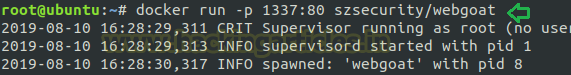
To access the webgoat application run following URL in the web browser.
http://localhost:1337/WebGoat

Configure bWAPP on Docker
A buggy web application that is purposely unsafe. Enthusiasts of security, system engineers, developers can find out about Web vulnerabilities and prevent them.
Repeat the same approach and execute following command to pull its docker image.
docker pull raesene/bwapp

then use the docker to start WebGoat over a specific port.
docker run -d -p 8080:80 raesene/bwapp

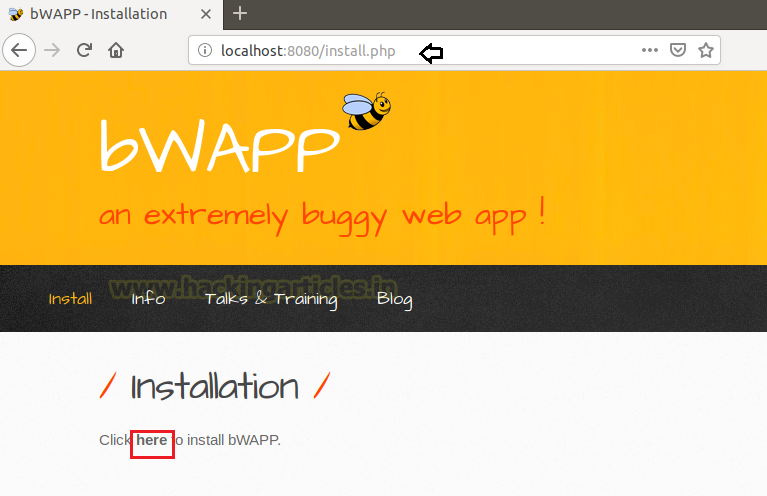
Now go to your browser and open bWAPP installation file by the following command and click on here as shown in the image below
http://localhost:8080/install.php
Now you will get a login page of bWAPP where we will use the default username which is bee and default password which is bug and you are logged in in bWAPP.

Enter the credential bee:bug and get access of the web console.

Now you can start working on bWAPP.
Another Method
We can use PentestLab Management Script because this script uses docker and hosts alias to make web apps available on localhost” and it can pull the following applications.
- bWAPP
- WebGoat 7.1
- WebGoat 8.0
- Damn Vulnerable Web App
- Mutillidae II
- OWASP Juice Shop
- WPScan Vulnerable WordPress
- OpenDNS Security Ninjas
- Altoro Mutual
Install and configure PentestLab Management Script
git clone https://github.com/eystsen/pentestlab.git cd pentestLab ./pentestLab.sh --help

To checklist of a web application, use list option along with the script.
./pentestLab.sh list
To start the web application, just write the name of web application after executable script as shown here.
./pentestLab.sh start juiceshop

Execute the following URL to browse the web application.
http://127.0.0.1 or http://juiceshop
Conclusion:
Vulnerable web application lab set-up using docker is very easy and fast as compared to other approaches. A pen-tester can easily set up his/her own vulnerable lab using docker in a very short period of time.
Hope you liked this technique to web application configuration.
Happy Hacking!!

Author: Kavish Tyagi is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here
Hello Kavish,
I like your post and I am interested to learn penetration testing, I did CEH v10 and I am IT auditor by profession. So could you please help me with this.
Thanks in advance.
contact ignite technologies
https://ignitetechnologies.in/
git clone https://github.com/eystsen/pentestlab.git
when we are using this command it is asking for the username and password sir…..
Its working sir…no probelm
Thanks for a good article!
I’m using that script myself and it used different localhost IPs for each app.
So it will not use 127.0.0.1 as you mentioned above. It will use:
127.1.0.1,
127.2.0.1,
127.3.0.1, etc
can the lab be accessed via the internet without using vps?