A Little Guide to SMB Enumeration
We will shine the light on the process or methodology for enumerating SMB services on the Target System/Server in this article. There are numerous tools and methods to perform enumeration, we will be finding different types of information on SMB throughout the article.
Table of Contents
- What is SMB?
- SMB Working
- SMB Versions
- SMB Security
- SMB Enumeration
- Hostname
- nmblookup
- nbtscan
- nbstat NSE Script
- nbtstat
- ping
- smb-os-discovery NSE Script
- Share and Null Session
- SMBMap
- Smbclient
- smb-enum-shares NSE Script
- Net view
- Metasploit: smb_enumshares
- CrackMapExec
- rpcclient
- Users
- Metasploit: smb_lookupsid
- Impacket: Lookupsid
- Vulnerability Scanning
- smb-vuln NSE Script
- Overall Scanning
- Enum4linux
- Hostname
- Conclusion
What is SMB?
SMB or Server Message Block is the modernized concept of what was used to known as Common Internet File System. It works as an Application Layer Network Protocol. It is designed to be used as a File Sharing Protocol. Different Applications can on a system can read and write simultaneously to the files and request the server for services inside a network. One of the interesting functionalities of SMB is that it can be run atop of its TCP/IP protocol or other network protocols. With the help of SMB, a user or any application or software that is authorized can access files or other resources on a remote server. Actions that can be performed include reading data, creating data, and updating data. The communication between clients and servers is done with the help of something called SMB client request.
SMB Working
The SMB Protocol delegates the client to communicate with other participants in the same network, allowing it to access files or services open to it in the network. In order for it to function the other device also requires the implemented network protocol and receive and process the respective client request using an SMB server application. Client computers using SMB connect to a supporting server using NetBIOS over TCP/IP, IPX/SPX, or NetBEUI. The initial establishment of the connection is required for exchanging information. Subsequent data transport is regulated by the provisions of the TCP protocol. SMB functions as a request-response or client-server protocol. Once the connection is established, the client computer or program can then open, read/write, and access files similar to the file system on a local computer.
SMB Versions
- CIFS: The old version of SMB, which was included in Microsoft Windows NT 4.0 in 1996.
- SMB 1.0 / SMB1: The version used in Windows 2000, Windows XP, Windows Server 2003 and Windows Server 2003 R2.
- SMB 2.0 / SMB2: This version used in Windows Vista and Windows Server 2008.
- SMB 2.1 / SMB2.1: This version used in Windows 7 and Windows Server 2008 R2.
- SMB 3.0 / SMB3: This version used in Windows 8 and Windows Server 2012.
- SMB 3.02 / SMB3: This version used in Windows 8.1 and Windows Server 2012 R2.
- SMB 3.1: This version used in Windows Server 2016 and Windows 10.
Presently, the latest version of SMB is the SMB 3.1.1 which was introduced with Windows 10 and Windows Server 2016. This version supports AES 128 GCM encryption in addition to AES 128 CCM encryption added in SMB3, and implements pre-authentication integrity check using SHA-512 hash. SMB 3.1.1 also makes secure negotiation mandatory when connecting to clients using SMB 2.x and higher.
SMB Security
The SMB protocol supports two levels of security. The first is the share level. The server is protected at this level and each share has a password. The client computer or user has to enter the password to access data or files saved under the specific share. This is the only security model available in the Core and Core plus SMG protocol definitions. User level protection was later added to the SMB protocol. It is applied to individual files and each share is based on specific user access rights. Once a server authenticates the client, he/she is given a unique identification (UID) that is presented upon access to the server. The SMB protocol has supported individual security since LAN Manager 1.0 was implemented.
SMB Enumeration: Hostname
We will start the enumeration of the SMB by finding the hostname of the target machine. This can be done by various tools.
nmblookup
We started with nmblookup tool. It is designed to make use of queries for the NetBIOS names and then map them to their subsequent IP addresses in a network. The options allow the name queries to be directed at a particular IP broadcast area or to a particular machine. All queries are done over UDP.
For unique names:
00: Workstation Service (workstation name)
03: Windows Messenger service
06: Remote Access Service
20: File Service (also called Host Record)
21: Remote Access Service client
1B: Domain Master Browser – Primary Domain Controller for a domain
1D: Master Browser
For group names:
00: Workstation Service (workgroup/domain name)
1C: Domain Controllers for a domain
1E: Browser Service Elections
nmblookup -A 192.168.1.17
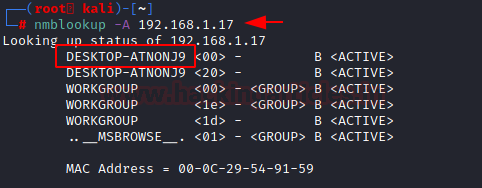
Here, we can see that we have enumerated the hostname to be DESKTOP-ATNONJ9.
nbtscan
Moving Forward we used nbtscan tool. NBTscan is a program for scanning IP networks for NetBIOS name information. It sends NetBIOS status query to each address in supplied range and lists received information in human-readable form. For each responded host it lists IP address, NetBIOS computer name, logged-in user name and MAC address (such as Ethernet).
nbtscan 192.168.1.17
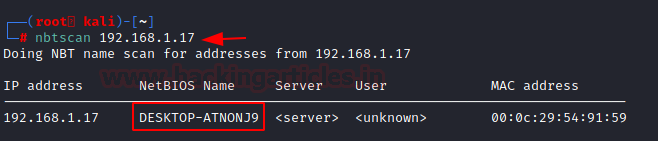
Here, we can see that we have enumerated the hostname to be DESKTOP-ATNONJ9.
nbstat NSE Script
This nmap script attempts to retrieve the target’s NetBIOS names and MAC address. By default, the script displays the name of the computer and the logged-in user; if the verbosity is turned up, it displays all names the system thinks it owns. It also shows the flags that we studied in nmblookup tool.
nmap --script nbstat.nse 192.168.1.17
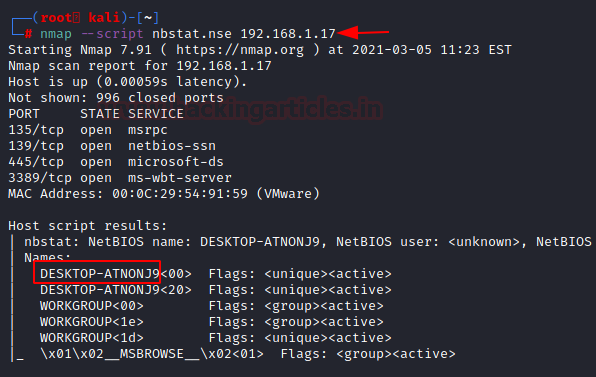
Here, we can see that we have enumerated the hostname to be DESKTOP-ATNONJ9.
nbtstat
This Windows command displays the NetBIOS over TCP/IP (NetBT) protocol statistics. It can read the NetBIOS name tables for both the local computer and remote computers. It can also read the NetBIOS name cache. This command allows a refresh of the NetBIOS name cache and the names registered with Windows Internet Name Service (WINS). When used without any parameters, this command displays Help Information. This command is available only if the Internet Protocol (TCP/IP) protocol is installed as a component in the properties of a network adapter in Network Connections.
nbtstat -A 192.168.1.17
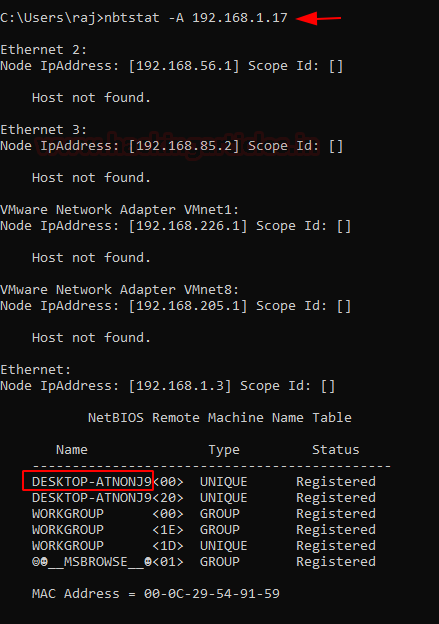
Here, we can see that we have enumerated the hostname to be DESKTOP-ATNONJ9.
Ping
We can also use the ping command to detect the hostname of an SMB server or machine. The -a parameter specifies reverse name resolution to be performed on the destination IP address. If this is successful, ping displays the corresponding hostname.
ping -a 192.168.1.17
Here, we can see that we have enumerated the hostname to be DESKTOP-ATNONJ9.

smb-os-discovery NSE Script
This NSE script attempts to determine the operating system, computer name, domain, workgroup, and current time over the SMB protocol (ports 445 or 139). It is achieved by initiating a session with the anonymous account (or with a proper user account, if one is given; it likely doesn’t make a difference); in response to a session starting, the server will send back all this information.
The following fields may be included in the output, depending on the circumstances (e.g., the workgroup name is mutually exclusive with domain and forest names) and the information available:
- OS
- Computer name
- Domain name
- Forest name
- FQDN
- NetBIOS computer name
- NetBIOS domain name
- Workgroup
- System time
nmap --script smb-os-discovery 192.168.1.17
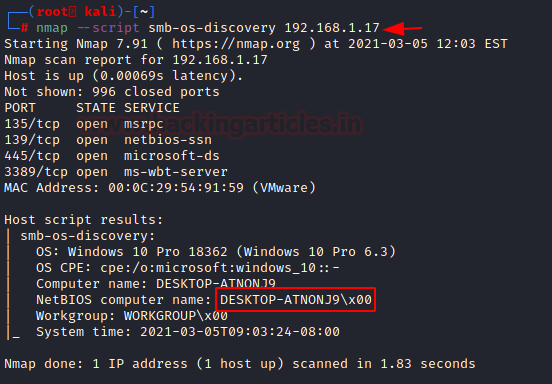
Here, we can see that we have enumerated the hostname to be DESKTOP-ATNONJ9.
SMB Enumeration: Share and Null Session
As we discussed earlier that SMB works on sharing files and resources. In order to transfer these files or resources, there are data streams that are called shares. There are public shares that are accessible to everyone on the network and then there are the user-specific shares. Let’s enumerate these shares.
SMBMap
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download functionality, file name auto-download pattern matching, and even execute remote commands. This tool was designed with pen testing in mind and is intended to simplify searching for potentially sensitive data across large networks.
smbmap -H 192.168.1.40
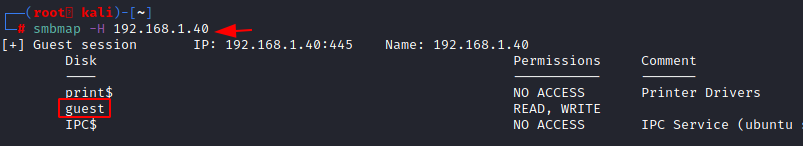
Here we see that the target machine has some shares. There is a share by the name of the guest. That must be a public share. Let’s enumerate a user-specific share using the credentials for that user. We are enumerating the share for the user raj as shown in the image below.
smbmap -H 192.168.1.17 -u raj -p 123
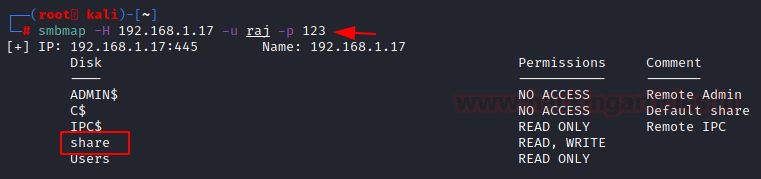
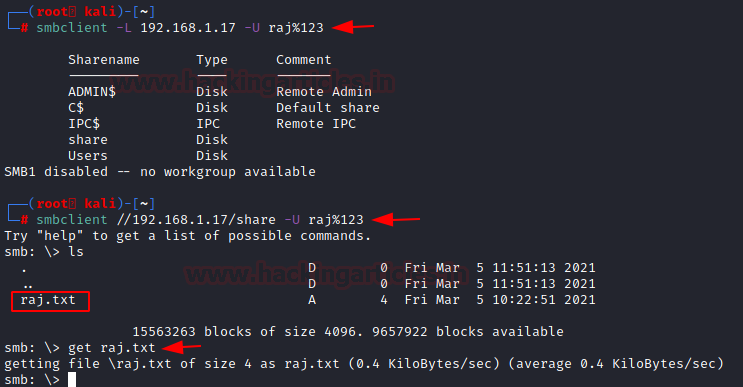
smbclient
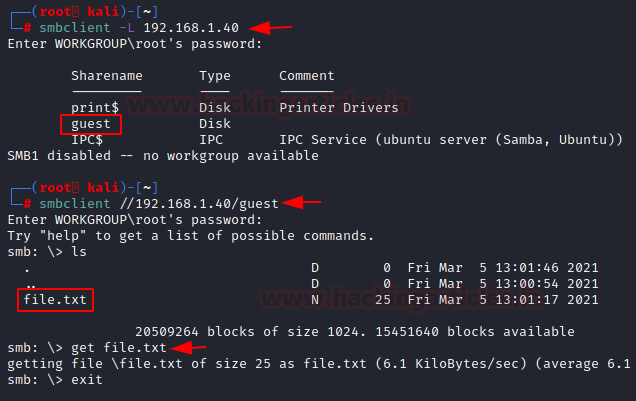
smbclient is samba client with an “ftp like” interface. It is a useful tool to test connectivity to a Windows share. It can be used to transfer files, or to look at share names. In addition, it has a nifty ability to ‘tar’ (backup) and restore files from a server to a client and vice versa. We enumerated the target machine and found the guest share using the smbclient directly. Then we connect to the guest share and see that there is a text file by the name of file.txt. We can download it using the get command.
smbclient -L 192.168.1.40 smbclient //192.168.1.40/guest get file.txt
Now we enumerate the user-specific share. We connect to the SMB as user raj and find a share by the name of ‘share’. We reconfigured the smbclient command to access the share and we see that we find a file named raj.txt. Again, we can download this file as well as using the get command.
smbclient -L 192.168.1.17 -U raj%123 smbclient //192.168.1.17/share -U raj%123 get raj.txt
smb-enum-shares NSE Script
This NSE scirpt attempts to list shares using the srvsvc.NetShareEnumAll MSRPC function and retrieve more information about them using srvsvc.NetShareGetInfo. If access to those functions is denied, a list of common share names are checked. Calling NetShareGetInfo requires an administrator account on all versions of Windows up to 2003, as well as Windows Vista and Windows 7 and 10, if UAC is turned down. Even if NetShareEnumAll is restricted, attempting to connect to a share will always reveal its existence. So, if NetShareEnumAll fails, a pre-generated list of shares, based on a large test network, are used. If any of those succeed, they are recorded. After a list of shares is found, the script attempts to connect to each of them anonymously, which divides them into “anonymous”, for shares that the NULL user can connect to, or “restricted”, for shares that require a user account.
nmap --script smb-enum-shares -p139,445 192.168.1.17
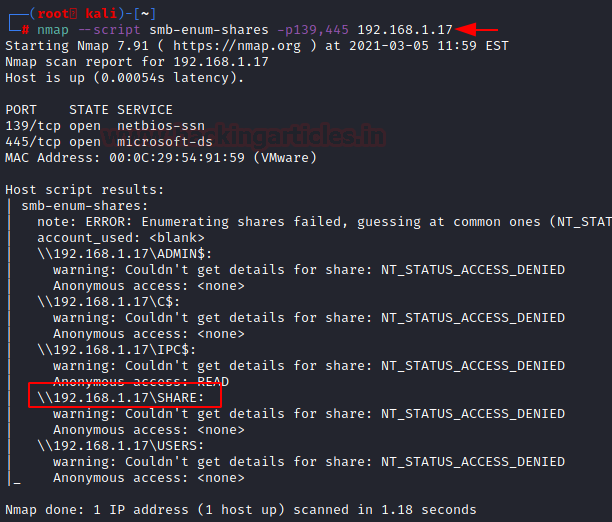
Here, we can see that we have the shares listed although the Access is Denied the existence of the share is confirmed.
Net view
Displays a list of domains, computers, or resources that are being shared by the specified computer. Used without parameters, net view displays a list of computers in your current domain. This time we are on the Windows machine. We used the net view with the /All parameter to list all the shares on the target machine.
net view \\192.168.1.17 /All

Then we changed the command by adding the share and we are able to read the contents of that share. Now using the copy command, we can download the file from share.
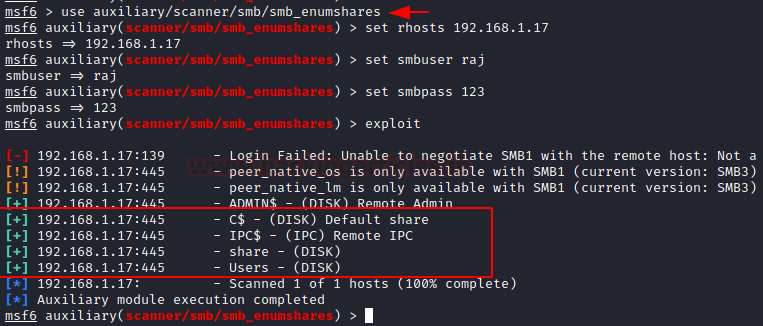
Metasploit: smb_enumshares
The smb_enumshares module enumerates any SMB shares that are available on a remote system. It requires the IP Address of the target server or machine followed by the set of credentials that can be used to access the share.
use auxiliary/scanner/smb/smb_enumshares set rhosts 192.168.1.17 set smbuser raj set smbpass 123 exploit
CrackMapExec
CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of “Living off the Land”: abusing built-in Active Directory features/protocols to achieve its functionality and allowing it to evade most endpoint protection/IDS/IPS solutions. CrackMapExec can Map the network hosts, Generate Relay List, enumerate shares and access, enumerate active sessions, enumerate disks, enumerate logged on users, enumerate domain users, Enumerate Users by bruteforcing RID, enumerate domain groups, Enumerate local groups etc.
crackmapexec smb 192.168.1.17 -u 'raj' -p '123' --shares

Here, we can see different shares and the permissions that are allowed on that particular share.
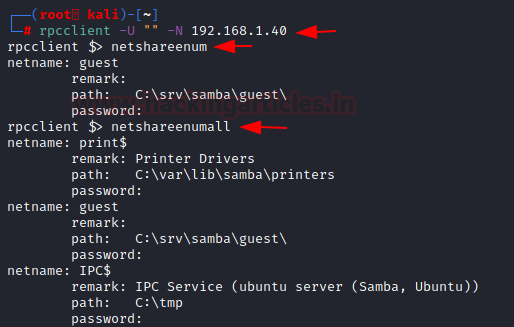
rpcclient
rpcclient is a utility initially developed to test MS-RPC functionality in Samba itself. It has undergone several stages of development and stability. Many system administrators have now written scripts around it to manage Windows NT clients from their UNIX workstation. We will be using it to enumerate the users on the SMB shares using the option of netshareenum as shown in the image below.
rpcclient -U "" -N 192.168.1.40 netshareenum netshareenumall
SMB Enumeration: Vulnerability Scanning
We enumerate a SMB server in order to compromise we need to enumerate and find possible vulnerabilities that can be used to exploit the server. In order to do this in an optimized method, we can perform a Vulnerability Scanning. There might be multiple tools to perform this kind of Scanning but here we will be focusing on this NSE script.
smb-vuln NSE Script
Nmap in past used to have a script by the name of smb-check-vulns. It used to scan the target server for the various vulnerabilities such as:
- conficker
- cve2009-3103
- ms06-025
- ms07-029
- regsvc-dos
- ms08-067
Then the script was divided into single vulnerability checks that can run individually such as smb-vuln-ms08-067. Hence to check all SMB vulnerabilities available in the Nmap Scripting Engine we use the * with the script.
nmap --script smb-vuln* 192.168.1.16
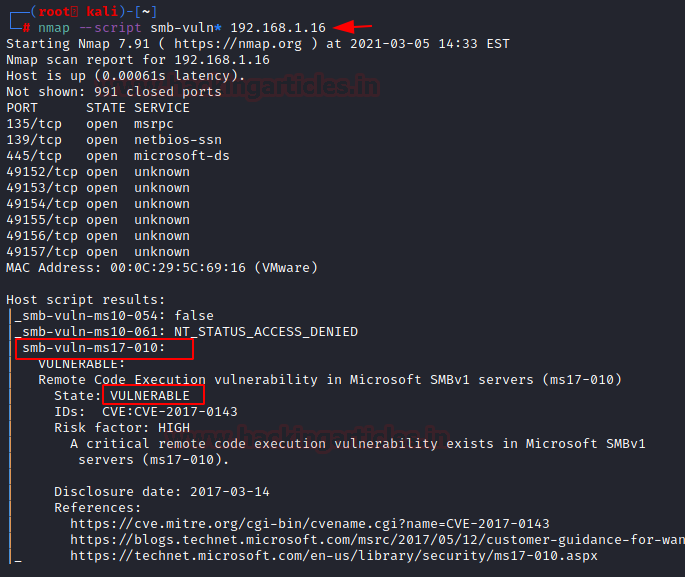
SMB Enumeration: Users
In a Windows environment, each user is assigned a unique identifier called Security ID or SID, which is used to control access to various resources like Files, Registry keys, network shares etc. Hence the SID of a user shouldn’t be compromised.
smb_lookupsid
The smb_lookupsid module brute-forces SID lookups on a range of targets to determine what local users exist in the system. Knowing what users exist on a system can greatly speed up any further brute-force logon attempts later on.
use auxiliary/scanner/smb/smb_lookupsid set rhosts 192.168.1.17 set smbuser raj set smbpass 123 exploit

Here, we can see that through enumerating SMB we have extracted two users: raj and aart.
Impacket: Lookupsid
A Security Identifier (SID) is a unique value of variable length that is used to identify a user account. Through a SID User Enumeration, we can extract information about what users exist and their data. Lookupsid script can enumerate both local and domain users. There is a Metasploit module too for this attack. If you are planning on injecting a target server with a golden or a silver ticket then one of the things that are required is the SID of the 500 user. Lookupsid.py can be used in that scenario. When we provide the following parameters to the Lookupsid in such a format as shown below.
Requirements:
- Domain
- Username
- Password/Password Hash
- Target IP Address
python3 lookupsid.py DESKTOP-ATNONJ9/raj:123@192.168.1.17

SMB Enumeration: Enum4Linux
Enum4linux is a tool that is designed to detecting and extracting data or enumerate from Windows and Linux operating systems, including SMB hosts those are on a network. Enum4linux is can discover the following:
- Domain and group membership
- User listings
- Shares on a device (drives and folders)
- Password policies on a target
- The operating system of a remote target
We start to normal scan using enum4linux. It extracts the RID Range, Usernames, Workgroup, Nbtstat Information, Sessions, SID Information, OS Information.
enum4linux 192.168.1.40

We see that it has also extracted the two uses based on the SID. These two users are privs and ignite. This user information was extracted through the communicating via the SMB channels by the enum4linux script.

At last, we have the Share Enumeration which had the guest share that we enumerated earlier. Then we see that it tried to enumerate inside the print share and IPC but was restricted. Then we have the Password Policy Information regarding the users on the system. It enumerates if the password was changed recently or if it has never been changed. It also tells us the complexity and other stuff regarding users and the operating system of the target system.

Conclusion
In this article, we discussed the various scripts and tools that can be used to enumerate with the SMB/MSRPC services on a target system. Enumeration is the key step in order to compromise and in order to defend your system and network. Be sure to safeguard your SMB service.
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn
nice work you helped me alot thanx
cool write up man
Hi, very good article lots of info for me.
I’m running Kali enum4linux against metasploitable and getting
[E] Server doesn’t allow session using username ”, password ”. aborting remainder of tests. nullinux doesn’t work so well either. I’ve been all over google trying to find out why this is. My teacher says enum4linux is funny.. and can’t explain it. enum4linux is used in 3 different lessons and I need it to work. Thank You!
Great article man! Keep it up 👍
enum4linux is great tool if system allows null session or if you already have user and password. In fact, most of the information you can collect comes from rpcclient and smbmap and smbclient. So, the important point is understand the protocols and what you can collect from them.
Thanks a lot sir really very informative.
Hello, Kindly clear this doubt for me.
smbmap -H 192.168.1.102 -d metasploitable -u msfadmin -p msfadmin
This about commad, Did you randomly guessed user ‘msfadmin’ or Is this a default user?
Its default parameter in metasploitable for username and password.
Nice
thanks lol!!!!!!!!!
This is just awesome!
Really useful article. But I can’t understand where the attacker took username.
On a pictures I didn’t see that.