Active Directory Enumeration: RPCClient
In this article, we are going to focus on the enumeration of the Domain through the SMB and RPC channels. The tool that we will be using for all the enumerations and manipulations will be rpcclient. The article is focused on Red Teamers but Blue Teamers and Purple Teamers can also use these commands to test the security configurations they deployed.
Table of Content
- Introduction
- Logging and Server Information
- Domain Information Query
- Enumerating Domain Users
- Enumerating Domain Groups
- Group Queries
- User Queries
- Enumerating Privileges
- Get Domain Password Information
- Get User Domain Password Information
- Enumerating SID from LSA
- Creating Domain User
- Lookup Names
- Enumerating Alias Groups
- Delete Domain User
- Net Share Enumeration
- Net Share Get Information
- Enumerating Domains
- Enumerating Domain Groups
- Display Query Information
- Change Password of User
- Create Domain Group
- Delete Domain Group
- Domain Lookup
- SAM Lookup
- SID Lookup
- LSA Query
- LSA Create Account
- Enumerating LSA Privileges
- Enumerating LSA Group Privileges
- Enumerating LSA Account Privileges
- LSA Query Security Objects
- Conclusion
Introduction
RPC or Remote Procedure Call is a service that helps establish and maintain communication between different Windows Applications. The RPC service works on the RPC protocols that form a low-level inter-process communication between different Applications. In this communication, the child process can make requests from a parent process. The child-parent relationship here can also be depicted as client and server relation. RPC is built on Microsoft’s COM and DCOM technologies. In general, the rpcclient can be used to connect to the SMB protocol as well. rpcclient is a part of the Samba suite on Linux distributions. The rpcclient was designed to perform debugging and troubleshooting tasks on a Windows Samba configuration. During that time, the designers of the rpcclient might be clueless about the importance of this tool as a penetration testing tool. There are multiple methods to connect to a remote RPC service. However, for this particular demonstration, we are using rpcclient
Logging and Server Information
To begin the enumeration, a connection needs to be established. This can be done by providing the Username and Password followed by the target IP address of the server. After establishing the connection, to get the grasp of various commands that can be used you can run the help. One of the first enumeration commands to be demonstrated here is the srvinfo command. It can be used on the rpcclient shell that was generated to enumerate information about the server. It can be observed that the os version seems to be 10.0. That narrows the version that the attacker might be looking at to Windows 10, Windows Server 2016, and Windows Server 2019. Learn more about the OS Versions.
rpcclient -U Administrator%Ignite@123 192.168.1.172

Domain Information Query
The next command that can be used via rpcclient is querydominfo. This command retrieves the domain, server, users on the system, and other relevant information. From the demonstration, it can be observed that the domain that is being enumerated is IGNITE. It has a total of 67 users. There was a Forced Logging off on the Server and other important information.
querydominfo

Enumerating Domain Users
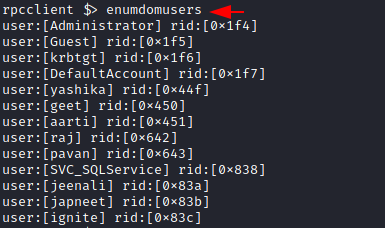
Another command to use is the enumdomusers. The name is derived from the enumeration of domain users. Upon running this on the rpcclient shell, it will extract the usernames with their RID. RID is a suffix of the long SID in a hexadecimal format. In this specific demonstration, there are a bunch of users that include Administrator, yashika, aarti, raj, Pavan, etc.
enumdomusers
Enumerating Domain Groups
Since we performed enumeration on different users, it is only fair to extend this to various groups as well. The group information helps the attacker to plan their way to the Administrator or elevated access. The polices that are applied on a Domain are also dictated by the various group that exists. Many groups are created for a specific service. So, it is also a good way to enumerate what kind of services might be running on the server, this can be done using enumdomgroup. The name is derived from the enumeration of domain groups. Upon running this on the rpcclient shell, it will extract the groups with their RID.
enumdomgroups

Group Queries
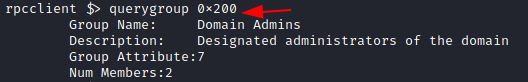
After enumerating groups, it is possible to extract details about a particular group from the list. This information includes the Group Name, Description, Attributes, and the number of members in that group. It is possible to target the group using the RID that was extracted while running the enumdomgroup. For the demonstration here, RID 0x200 was used to find that it belongs to the Domain Admin groups. This group constitutes 7 attributes and 2 users are a member of this group.
querygroup 0x200
User Queries
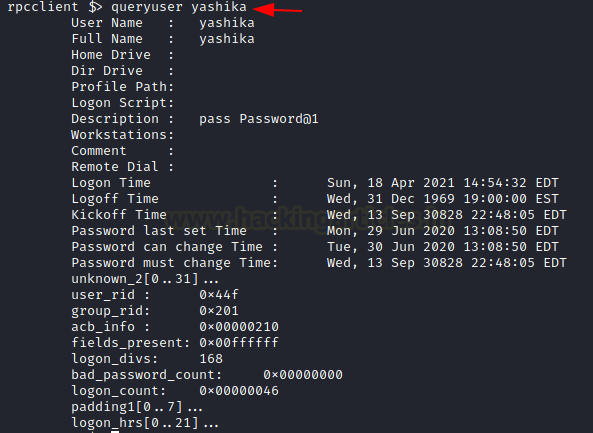
The ability to enumerate individually doesn’t limit to the groups but also extends to the users. To enumerate a particular user from rpcclient, the queryuser command must be used. When provided the username, it extracts information such as the username, Full name, Home Drive, Profile Path, Description, Logon Time, Logoff Time, Password set time, Password Change Frequency, RID, Groups, etc. In the demonstration, it can be observed that the user has stored their credentials in the Description. Hence, the credentials were successfully enumerated and the account can be taken over now.
queryuser yashika
Enumerating Privileges
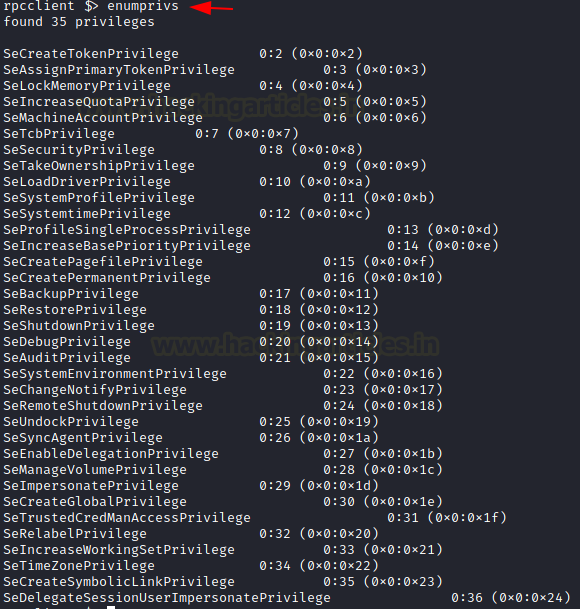
After the user details and the group details, another information that can help an attacker that has retained the initial foothold on the domain is the Privileges. These privileges can help the attacker plan for elevating privileges on the domain. The privileges can be enumerated using the enumprivs command on rpcclient. In the demonstration, it can be observed that the current user has been allocated 35 privileges.
enumprivs
Get Domain Password Information
To enumerate the Password Properties on the domain, the getdompwinfo command can be used. This is made from the words get domain password information. This will help in getting the information such as the kind of password policies that have been enforced by the Administrator in the domain. It is possible to enumerate the minimum password length and the enforcement of complex password rules. If these kinds of features are not enabled on the domain, then it is possible to brute force the credentials on the domain.
getdompwinfo
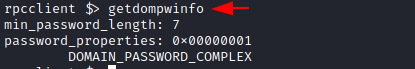
Get User Domain Password Information
In the previous command, we used the getdompwinfo to get the password properties of the domain administrated by the policies. But it is also possible to get the password properties of individual users using the getusrdompwinfo command with the user’s RID. In the demonstration, the user with RID 0x1f4 was enumerated regarding their password properties.
getusrdompwinfo 0x1f4

Enumerating SID from LSA
Learning about various kinds of compromises that can be performed using Mimikatz we know that the SID of a user is the security Identifier that can be used for a lot of elevating privileges and minting tickets attacks. It can be enumerated through rpcclient using the lsaenumsid command. In the demonstration, it can be observed that lsaenumsid has enumerated 20 SIDs within the Local Security Authority or LSA.
lsaenumsid
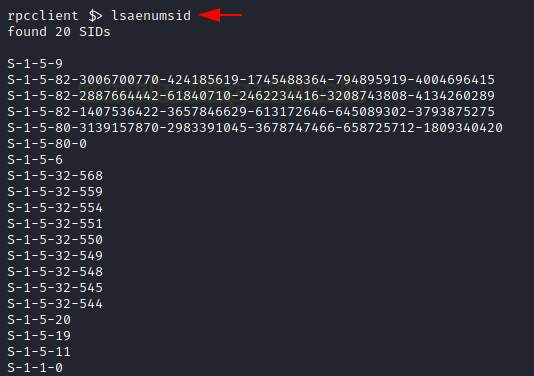
Creating Domain User
While having some privileges it is also possible to create a user within the domain using the rpcclient. It can be done with the help of the createdomuser command with the username that you want to create as a parameter. In the demonstration, a user hacker is created with the help of a createdomuser and then a password is provided to it using the setuserinfo2 command. At last, it can be verified using the enumdomusers command.
createdomuser hacker setuserinfo2 hacker 24 Password@1 enumdomusers
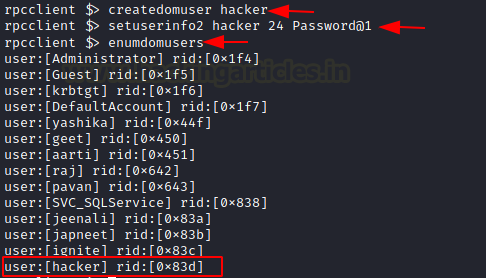
Lookup Names
We can also check if the user we created has been assigned a SID or not using the lookupnames command on the rpcclient. As with the lsaenumsid, it was possible to extract the SID but it was not possible to tell which user has that SID. This problem is solved using lookupnames whereupon providing username the SID of that particular user can be extracted with ease.
lookupnames hacker
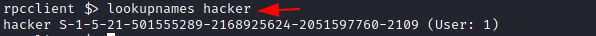
Enumerating Alias Groups
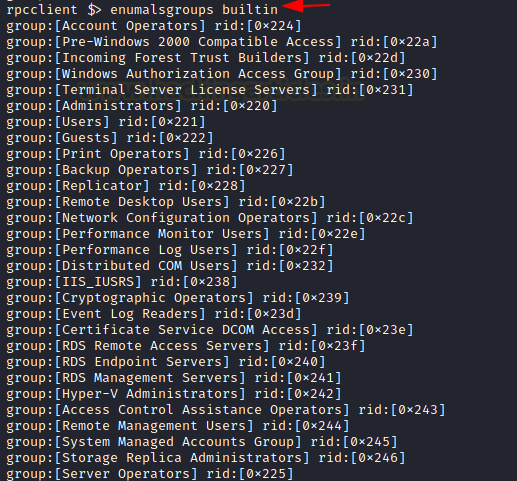
The next command that can be used is enumalsgroups. It enumerates alias groups on the domain. The alias is an alternate name that can be used to reference an object or element. When used with the builtin parameter, it shows all the built-in groups by their alias names as demonstrated below.
enumalsgroups builtin
Delete Domain User
The ability to manipulate a user doesn’t end with creating a user or changing the password of a user. If proper privileges are assigned it also possible to delete a user using the rpcclient. The deletedomuser command is used to perform this action.
deletedomuser hacker
Net Share Enumeration
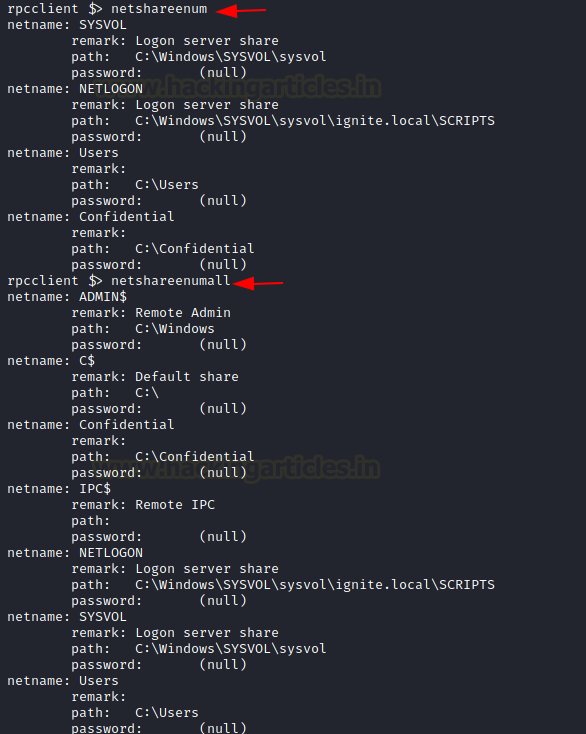
When dealing with SMB an attacker is bound to be dealt with the Network Shares on the Domain. Most of the Corporate offices don’t want their employees to use USB sticks or other mediums to share files and data among themselves. Hence, they usually set up a Network Share. There are times where these share folders may contain sensitive or Confidential information that can be used to compromise the target. To enumerate these shares the attacker can use netshareenum on the rpcclient. If you want to enumerate all the shares then use netshareenumall.
netshareenum netshareenumall
Net Share Get Information
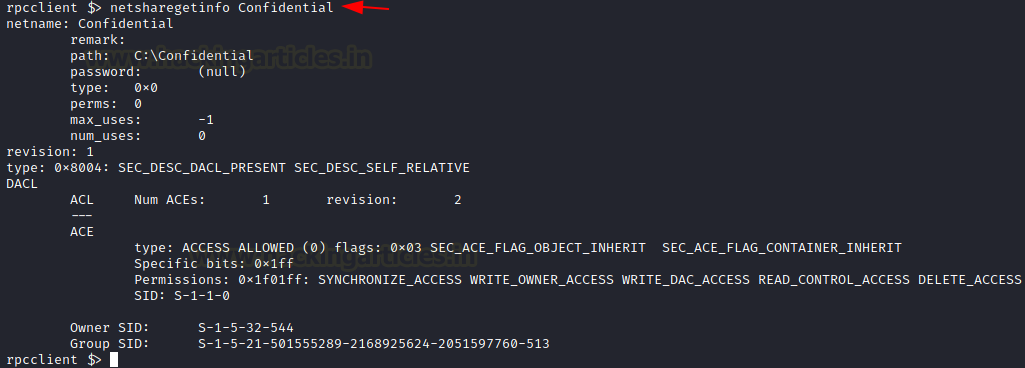
As with the previous commands, the share enumeration command also comes with the feature to target a specific entity. The command netsharegetinfo followed by the name of the share you are trying to enumerate will extract details about that particular share. This detail includes the path of the share, remarks, it will indicate if the share has a password for access, it will tell the number of users accessing the share and what kind of access is allowed on the share.
netsharegetinfo Confidential
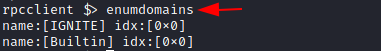
Enumerating Domains
In the scenarios where there is a possibility of multiple domains in the network, there the attacker can use enumdomains to enumerate all the domains that might be deployed in that network. In the demonstration presented, there are two domains: IGNITE and Builtin.
enumdomains
Enumerating Domain Groups
Next, we have two query-oriented commands. These commands can enumerate the users and groups in a domain. Since we already performed the enumeration of such data before in the article, we will enumerate using enumdomgroup and enumdomusers and the query-oriented commands in this demonstration. When using the enumdomgroup we see that we have different groups with their respective RID and when this RID is used with the queryusergroups it reveals information about that particular holder or RID. In the case of queryusergroups, the group will be enumerated. When using querygroupmem, it will reveal information about that group member specific to that particular RID.
enumdomgroups enumdomusers queryusersgroups 0x44f querygroupmem 0x201

Display Query Information
From the enumdomusers command, it was possible to obtain the users of the domain as well as the RID. This information can be elaborated on using the querydispinfo. This will extend the amount of information about the users and their descriptions.
querydispinfo

Change Password of User
As from the previous commands, we saw that it is possible to create a user through rpcclient. Depending on the user privilege it is possible to change the password using the chgpasswd command.
chgpasswd raj Password@1 Password@987

Create Domain Group
After creating the users and changing their passwords, it’s time to manipulate the groups. Using rpcclient it is possible to create a group. The createdomgroup command is to be used to create a group. It accepts the group name as a parameter. After creating the group, it is possible to see the newly created group using the enumdomgroup command.
createdomgroup newgroup enumdomgroups

Delete Domain Group
The manipulation of the groups is not limited to the creation of a group. If the permissions allow, an attacker can delete a group as well. The command to be used to delete a group using deletedomgroup. This can be verified using the enumdomgroups command.
deletedomgroup newgroup enumdomgroups

Domain Lookup
We have enumerated the users and groups on the domain but not enumerated the domain itself. To extract information about the domain, the attacker can provide the domain name as a parameter to the command lookupdomain as demonstrated.
lookupdomain ignite

SAM Lookup
Since the user and password-related information is stored inside the SAM file of the Server. It is possible to enumerate the SAM data through the rpcclient as well. When provided with the username to the samlookupnames command, it can extract the RID of that particular user. If used the RID is the parameter, the samlookuprids command can extract the username relevant to that particular RID.
samlookupnames domain raj samlookuprids domain 0x44f

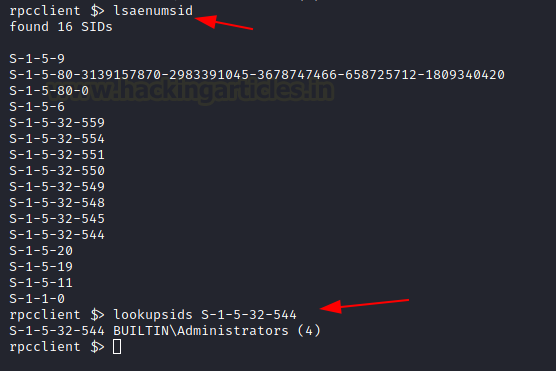
SID Lookup
The next command to demonstrate is lookupsids. This command can be used to extract the details regarding the user that the SID belongs. In our previous attempt to enumerate SID, we used the lsaenumsid command. That command reveals the SIDs for different users on the domain. To extract further information about that user or in case during the other enumeration the attacker comes into the touch of the SID of a user, then they cause to use the lookupsids command to get more information about that particular user. In the demonstration, it can be observed that the SID that was enumerated belonged to the Administrator of the Builtin users.
lsaenumsid
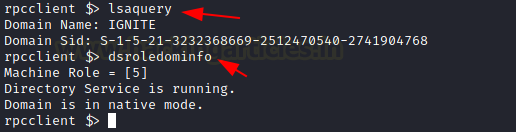
LSA Query
The next command that can help with the enumeration is lsaquery. This command can help with the enumeration of the LSA Policy for that particular domain. In the demonstration, it can be observed that a query was generated for LSA which returned with information such as Domain Name and SID. Similarly to enumerate the Primary Domain Information such as the Role of the machine, Native more of the Domain can be done using the dsroledominfo command as demonstrated.
lsaquery dsroledominfo
LSA Create Account
An attacker can create an account object based on the SID of that user. For this particular demonstration, we will first need a SID. This can be extracted using the lookupnames command used earlier. Passing the SID as a parameter in the lsacreateaccount command will enable us as an attacker to create an account object as shown in the image below.
lookupnames raj lsacreateaccount S-1-5-21-3232368669-2512470540-2741904768-1103

Enumerating LSA Group Privileges
During our previous demonstrations, we were able to enumerate the permissions and privileges of users and groups based on the RID of that particular user. It is possible to perform enumeration regarding the privileges for a group or a user based on their SID as well. To do this first, the attacker needs a SID. This can be obtained by running the lsaenumsid command. In the demonstration below, the attacker chooses S-1-1-0 SID to enumerate. When it was passed as a parameter in the command lookupsids, the attacker was able to know that this belongs to the group Everyone. Further, when the attacker used the same SID as a parameter for lsaenumprivaccount, they were able to enumerate the levels of privileges such as high, low, and attribute. Then the attacker used the SID to enumerate the privileges using the lsaenumacctrights command. This command was able to enumerate two specific privileges such as SeChangeNotiftyPrivielge and SeNetworkLogonRight privilege.
lsaenumsid lookupsids S-1-1-0 lsaenumacctrights S-1-1-0

The ability to interact with privileges doesn’t end with the enumeration regarding the SID or privileges. It is also possible to manipulate the privileges of that SID to make them either vulnerable to a particular privilege or remove the privilege of a user altogether. To demonstrate this, the attacker first used the lsaaddpriv command to add the SeCreateTokenPrivielge to the SID and then used the lsadelpriv command to remove that privilege from that group as well. All this can be observed in the usage of the lsaenumprivaccount command.
lsaaddpriv S-1-1-0 SeCreateTokenPrivilege lsaenumprivsaccount S-1-1-0 lsadelpriv S-1-1-0 SeCreateTokenPrivilege lsaenumprivsaccount S-1-1-0

Enumerating LSA Account Privileges
In the previous demonstration, the attacker was able to provide and remove privileges to a group. It is also possible to add and remove privileges to a specific user as well. The lsaaddacctrights command can be used to add privileges to a user based on their SID. The SID was retrieved using the lookupnames command. After verifying that the privilege was added using the lsaenumprivaccount command, we removed the privileges from the user using the lsaremoveacctrights command.
lookupnames raj lsaaddacctrights S-1-5-21-3232368669-2512470540-2741904768-1103 SeCreateTokenPrivilege lsaenumprivsaccount S-1-5-21-3232368669-2512470540-2741904768-1103 lsaremoveacctrights S-1-5-21-3232368669-2512470540-2741904768-1103 SeCreateTokenPrivilege lsaenumprivsaccount S-1-5-21-3232368669-2512470540-2741904768-1103

After manipulating the Privileges on the different users and groups it is possible to enumerate the values of those specific privileges for a particular user using the lsalookupprivvalue command.
lsalookupprivvalue SeCreateTokenPrivielge

LSA Query Security Objects
The next command to observe is the lsaquerysecobj command. This command is made from LSA Query Security Object. This command helps the attacker enumerate the security objects or permissions and privileges related to the security as demonstrated below.
lsaquerysecobj

Conclusion
In this article, we were able to enumerate a wide range of information through the SMB and RPC channel inside a domain using the rpcclient tool. This article can serve as a reference for Red Team activists for attacking and enumerating the domain but it can also be helpful for the Blue Team to understand and test the measures applied on the domain to protect the Network and its users.
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn