Threat Detection for your Network using Kfsensor Honeypot
In this article, however, we will set up a framework to draw in attacker so we can catch or study them. Since almost the majority of the attackers around the globe are focusing on Windows servers for the various of their known defects and vulnerabilities, we will set up a Windows framework to do only that. we will set up a honeypot. In the event that you abandon it ready for action, you can watch other attackers rehearsing their attack and prepare for it.
Table of Content:
- Introduction to Honeypot
- Introduction to KFSensor
- Working of KFSensor
Introduction to Honeypot
Honeypot disguises itself as an actual server to give the false idea to the attackers and divert their attacks. Therefore,a honeypot should be set up just like the real server so that data can appear to be authentic by showing fake files, fake ports, fake directories, etc. As the honeypot creates the illusion of being legitimate; the attacker tends to believe that they have gained accessed of the real deal. One of the main differences is the area of the machine in connection to the genuine servers. The disguised machine is normally set someplace in the DMZ. This guarantees the inner system isn’t presented to the attacker. Honeypots work by checking and\or once in a while controlling the interloper amid their utilization of the Honeypot. This should be possible whether the assault originated all things considered or within the system, contingent upon the area of the distraction framework. Honeypots are commonly intended to review the action of an interloper, spare log documents, and record such occasions as the procedures began, orders, a record includes, erases, changes, and even keystrokes.
Introduction to KFSensor
KFSensor is a honeypot for a windows system. it also acts as an IDS. Its job is to attract and detect all the attackers in the network, hence the name ‘Honeypot’. It does so by imitating a vulnerable environment and disguising itself as a server and it way, it succeeds to not only catch the attacker but also helps to know their motive. It is specifically designed for windows therefore it contains a lot of windows dedicated unique features. It’s quite convenient to use and a user friendly due to its GUI based console, along with its low maintains.
Working of KFSensor
KFSensor’s role is to be a decoy server for the attackers in order to protect the real thing. It does its job perfectly by opening fake ports on the system where it’s installed and gathering the information when a connection is made. It does this in precisely the same way as a routine server program, such as a web server or an SMTP server. By doing this it sets up a target, or a honeypot server, that will record the activities of an attacker.
Working with KFSensor
After downloading and installing KFSensor, when you turn it on, you will see the following window. Here, click on next.
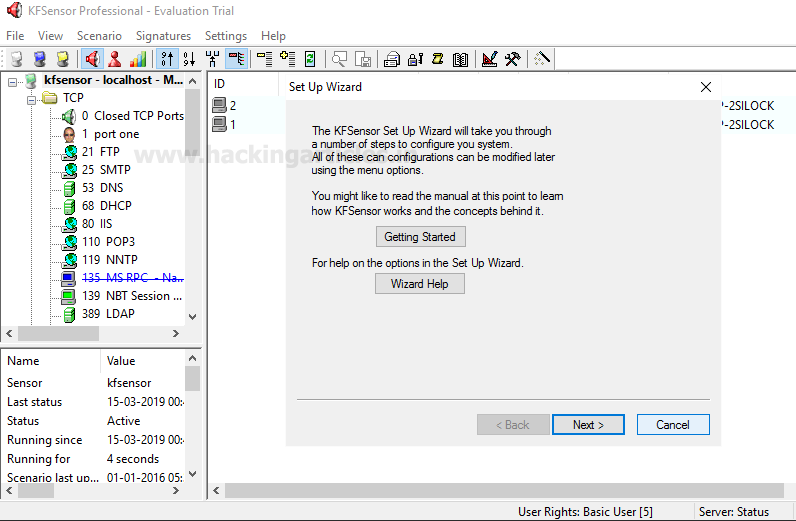
Then it will ask you to select the ports as shown in the image below, after selecting the ports click on next button.
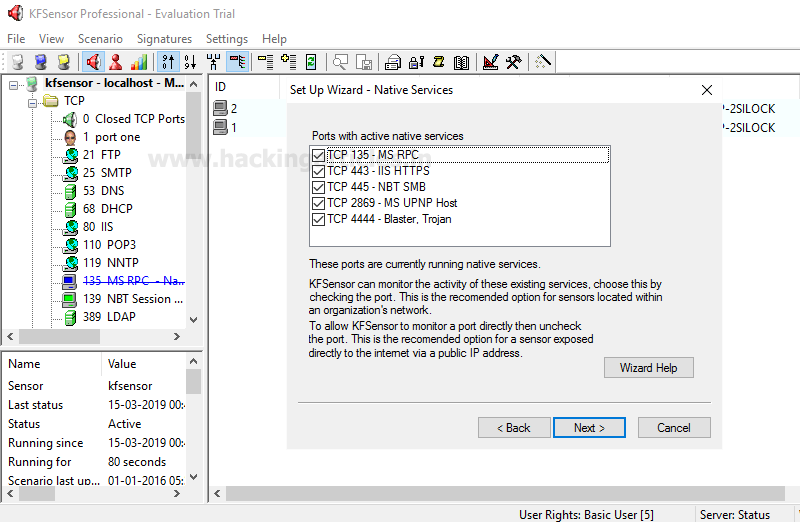
Then it will ask you if you want get email notification of its alerts over the time. So, here, you can add the email from which you want to send and the email where you want to receive the mails.

After these formalities, click on finish button.
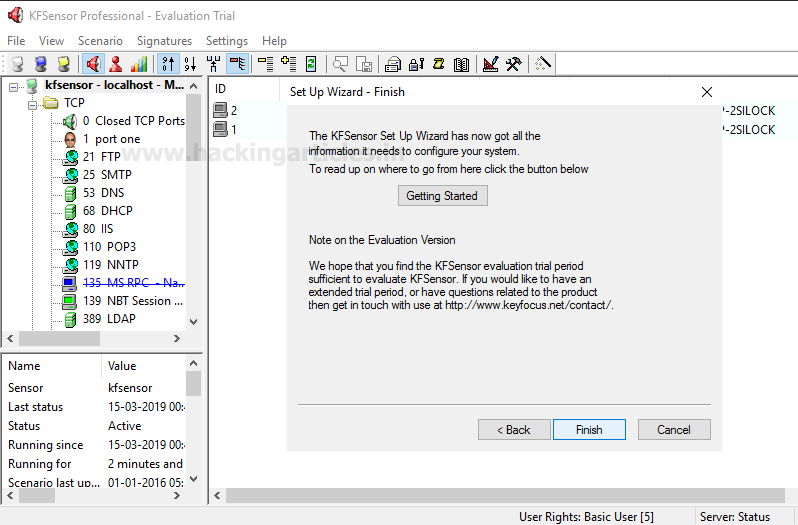
Once, you click on the finish button, it will show you the following window.

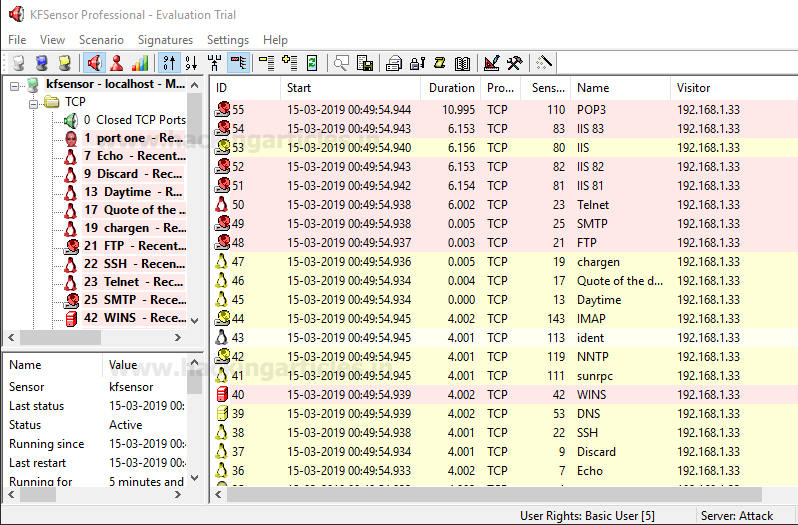
Now, as the honeypot has been setup, if you scan the victim target (which is installed with honeypot) using nmap, it will show you all the ports open ass a decoy, just like its shown in the image below :

And in KFSensor it will show the details of the scan along with its IP. It will also generate an alarm to alert you.
If the attacker is using any other tool to scan the network, like Nessus, even then the working of KFSensor will be same. For instance, if the attack is through Nessus as shown in the image below :
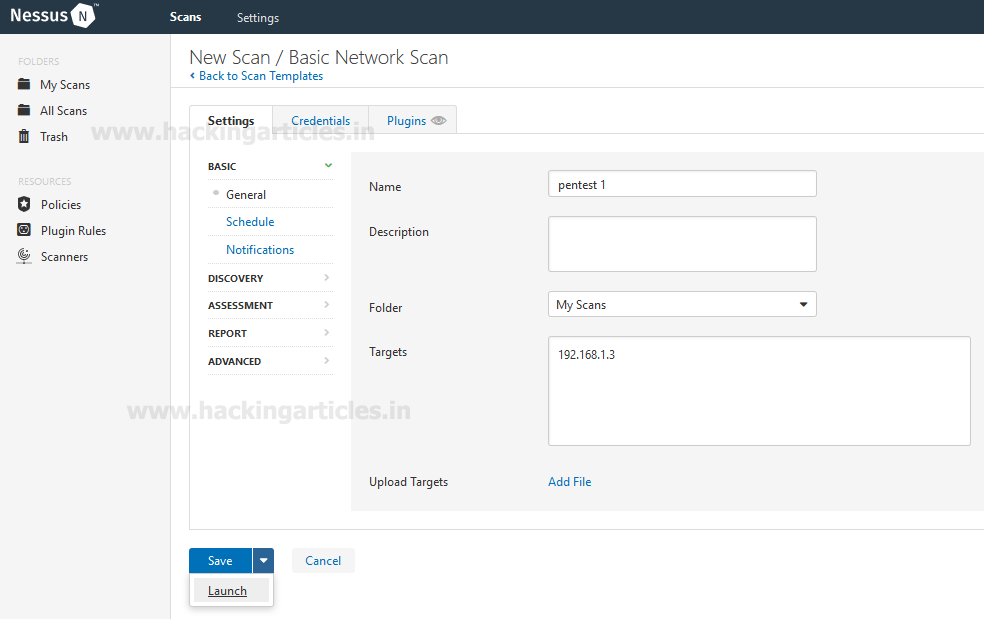
And when the attack from Nessus is completed, it will show you the faux result as you can see in the image below :
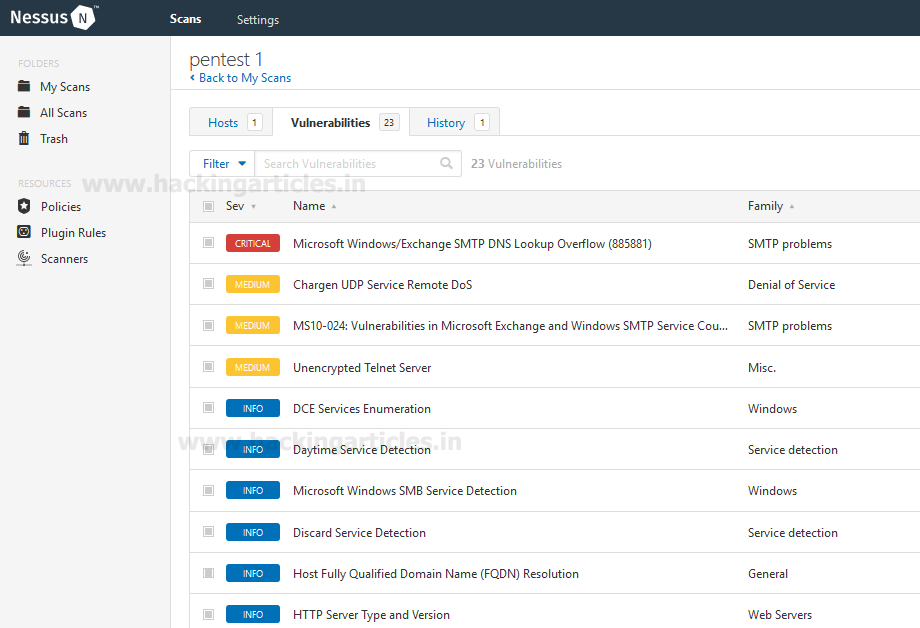
And similarly, the KFSensor will alert you as it is shown in the image below :

This way, KFSenor is the best way to detect and confuse the attacker in order to save yourself and be cautious.
Author: Shubham Sharma is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here
what if we do a stealth scan (-sS) to the target? Will our scanning activity will be logged?