MinU: v2 Vulnhub Walkthrough
Today we are going to take another CTF challenge Minu:v2. The credit for making this VM machine goes to “8bitsec” and it is a boot2root challenge where we have to root the server and capture the flag to complete the challenge. You can download this VM here.
Security Level: Beginner
Penetrating Methodology:
- Scanning
- Netdiscover
- NMAP
- Enumeration
- Web Directory Search
- Exploitation
- Command Injection
- SSH
- Privilege Escalation
- Exploiting Suid rights
Walkthrough:
Scanning:
Let’s start off by scanning the network and identifying the host IP address. We can identify our host IP as 192.168.1.101 by using Netdiscover.
netdiscover

Then, as usual, we used our favourite tool Nmap for port enumeration. We found that port 22 and 3306 are open.
And we observed that on port 3306 http service was running.
nmap -A 192.168.1.101

Enumeration:
We found nothing useful on the index page so we used dirb for brute-forcing and found one directory with .html extension.
dirb http://192.168.1.101/3306 -X .html

We tried to access the URL and found that it is an upload page and accepts only .svg files as input.
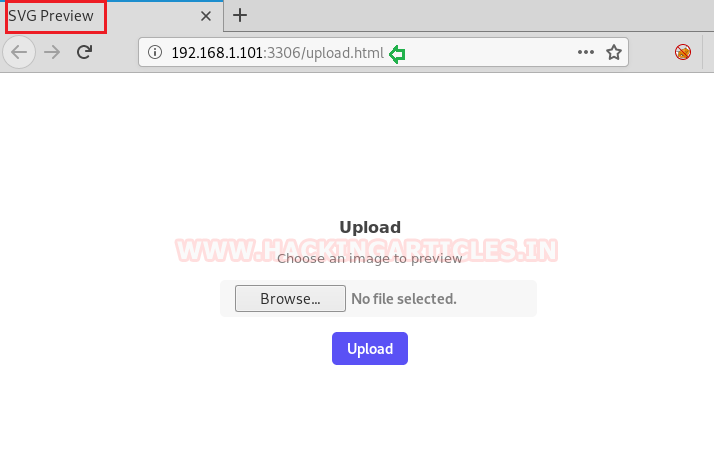
So we took help of the google to find any script in SVG format which we can utilize for xxe injection.

After doing some research we found on such script in which we are injecting /etc/passwd command. We copied the script and saved it as .svg file.

Exploitation:
We tried to upload the script file and it got successfully uploaded. And after uploading, we checked for the page source and got the output of /etc/passwd file.
We came to know that the target has multiple users like employee, chrony, nobody etc.

We thought of exploring other commands using the same script.
Since the target machine is using the /bin/ash shell, we thought of checking the shell history in the /.ash_history directory by editing the script file.

After editing we uploaded the file and got some useful information from the history file, which gave us a username and a password.

So we tried to ssh the target machine with username employee and a password superultrapass3 which we got above and were successfully able to login.
After logging in we checked for the suid permissions for privilege escalation and got one file with name micro which came out to be an editor tool.
ssh employee@192.168.1.101 find / -perm -u=s -type f 2>/dev/null /usr/bin/micro

Privilege Escalation:
We tried to pipe the contents of /etc/passwd file into the macro editor where we can edit or add new users with root privileges
cat /etc/passwd | /usr/bin/micro


We created the password for the new user using the openssl tool.
openssl passwd -1 -salt user3 pass123

After that, we added the new user test and hashed password with root privileges into the /etc/passwd file and saved it.

Once we had a user with root privileges we switched to that user and successfully got the shell with root shell and eventually got the flag.
su test id cd /root cat flag.txt

Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here
i have created the user test added the user test with root privilege but ,when i tried to switch user using su command ,and entered the password its says (can’t execute bin/ashh, no such file or directory)
but i have added the user test and saved the file also
When you are editing the etc/passwd file, write bin/ash not bin/ashh (Its a typo in the screenshot here.)