Comprehensive Guide to Steghide Tool
In this article, we’ll learn about Steghide. There are various steganography tools available but the part that differentiates it is that it uses a variety of algorithms to encrypt the data. Moreover, Steghide supports to hide data behind any image(jpg/jpeg/png/gif/bmp), audio (mp3/wav), excel, etc.
Table of Content
- Introduction to Steganography
- Introduction to Steghide
- Features
- Installation of Steghide
- Getting Start with Steghide
- Functionality of Steghide
- Embedding of Data Via Steghide
- Extraction of Data Via Steghide
- Password Protect Files
- Retrieve Information of Embedded File
- Verbose Mode
- Compression Mode
- Anti-compression Mode
- Embedding File Without Name
- Encrypting Algorithms
- Overwriting the Existing File
Introduction to Steganography
In digital steganography, electronic communications may incorporate steganographic coding inside of a transport layer, such as a document file, picture file, program or convention. Media records are perfect for steganographic transmission since of their expansive estimate. For instance, a sender might begin with a harmless picture and make few alterations to it in order to hide data, so that, this alteration goes unnoticed for someone who is not particularly seeking out for it.
The upside of steganography over cryptography alone is that the planned mystery message does not stand out to itself as an object of examination. Clearly obvious scrambled messages—regardless of how unbreakable—stimulate intrigue, and may in themselves be implicating in nations where encryption is illicit. In this manner, while cryptography is the act of securing the substance of a message alone, steganography is worried about hiding the way that a mystery message is being sent, just as disguising the substance of the message.
Introduction to Steghide
Steghide may be a steganography device which permits you to cover up confidential records inside a picture or sound record with a passphrase. Bolsters BMP and JPEG picture groups, AU and WAV sound groups. By default, its employments Rijndael calculation to scramble the record and the key measure is 128 bits. This tool has its advantages and disadvantages. One upside is that it is significantly better at covering up and can without much of a stretch shroud any document type. It does as such by utilizing a propelled calculation to shroud it inside the picture (or sound) record without changing the look (or sound) of the document. This additionally implies without utilizing steghide (or if nothing else a similar scientific methodology as steghide) it is hard to extricate the concealed documents from the picture.
Features
- Compression of embedded data
- BMP, GIF and JPG supported
- Encryption of embedded data
- Decryption via password
- Uses various algorithms for encryption
Installation
Let’s start with the installation of steghide. In windows, we can download steghide from http://steghide.sourceforge.net/download.php. After downloading we have to simply unzip the files and use it through the cmd. In Linux, open your terminal and type the following command to download Steghide :
apt-get install steghide
Getting Started with Steghide
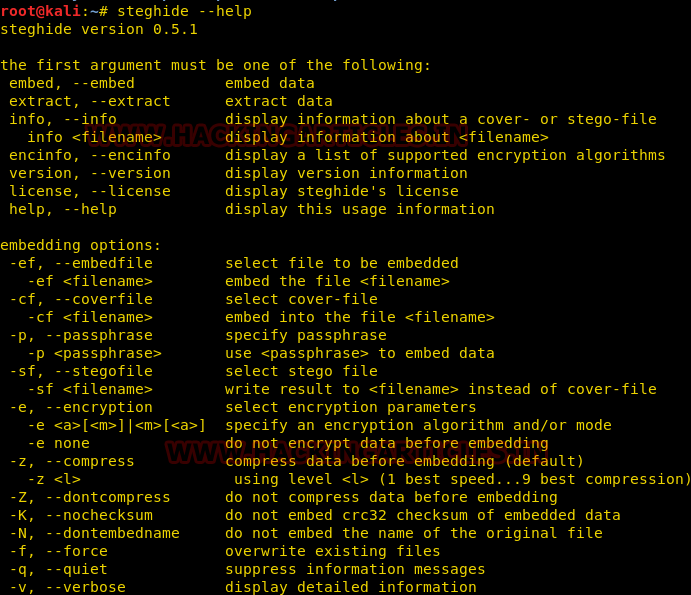
To start Steghide, the most basic option we use the help command. This command will display us all the options that Steghide provides us.
steghide --help
Embedding Data in The Image
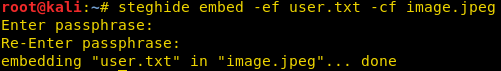
We hide data in the image using Steghide so that only the person who acknowledges it can read that. So, we made a text file named as user.txt in which we wrote our confidential data and image.jpeg is that file in which we are embedding our data. To achieve this, we’ll be executing the following command:
steghide embed -ef <txt filename> -cf <media filename>
Here, ef and cf are termed as embedded file and cover file respectively.
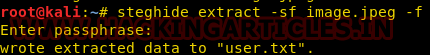
Extraction of Data Via Steghide
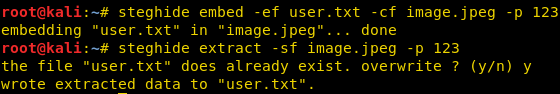
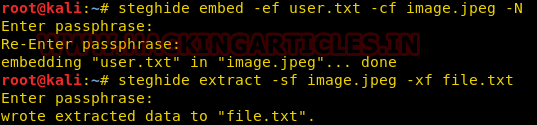
Using Steghide adds an extra layer of security by allowing us to use a password for it. Now, to extract the hidden data use the following command :
steghide extract -sf <media filename>
Then enter the password in order to extract the file.
Here,
sf is a secret file

Password Protect Files
Now, we can also extract the files using the following command. This command is different is that it specifies a password in the command itself, therefore, we do not need to specify it separately.
steghide embed -ef <txt filename> -cf <media filename> -p <password>
Retrieve Information of Embedded File
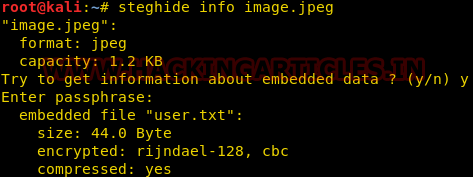
If we have an image that is suspected to have data hidden and if so, then which algorithm is used to encrypt the data in the file. Then we will use the following command :
steghide info <media filename>
Verbose Mode
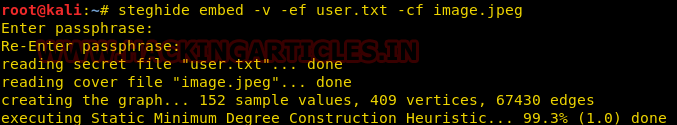
To get each and every information of a file during its extraction, we can use the verbose mode. The verbose mode gives you the detailed information. We can use the verbose mode by executing the following command :
steghide embed -v -ef <txt filename> -cf <media filename>
Compression Mode
Now if we want to compress text file before hiding it then we would use the following command. The compression level can vary from 1 to 9. The first level gives you speed to compress whereas, at 9th level, it will provide you with the best compression techniques.
steghide embed -ef <txt filename> -cf <media filename> -z 2

Anti Compression Mode
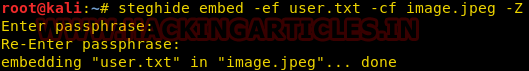
Now if we don’t want to compress a file before hiding it then we will use the following command :
steghide embed -ef <txt filename> -cf <media filename> -Z
Embedding File Without Name
We can also hide a file without naming it. We will use this command :
steghide embed -ef <txt filename> -cf <media filename> -N
Encrypting Algorithms
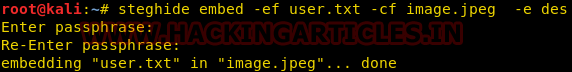
We can encrypt the data that we are hiding by using encryption techniques. And this can be easily achieved by just using the following command :
steghide embed -ef <txt filename> -cf <media filename> -e <algorithm name>
Overwriting the Existing File
When extracting the file let’s assume we have already have a file in the same directory with the same name. then we can use the following command to overwrite the existing file if that is desired. And for this use the following command :
steghide extract -sf <media filename> -f
Conclusion
So, this was the short guide about Steghide. And as you can see, it is an easy tool for steganography. It’s also user-friendly. It has, therefore, become one of the finest steganography tools for extracting and embedding information in a multitude of media files Steghide has many uses and its other notable characteristics such as file encryption make it one of the finest steganography.
Author: Dheeraj Gupta is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast in the field of Network & Cyber Security. Contact Here
Nice artical , Can you tell me what is passphrase ? AS i know it is a login credentail.
About encrypting algorithms, where I can find any info about supported encryption?
Steghide use libmcrypt library, I think all encription algoritms that supports by this lib also avialable in the steghide.(http://mcrypt.sourceforge.net/)
I like your blog and how you explained it. You made it so understandable and easy to use with examples. This is a great way to send hidden information. What about hiding malicious code?
Great Articles