Incident Response: Windows Account Management Event (Part 2)
For a system to perform well and ensure its maintenance, it is extremely important to monitor and manage events on a system. Event Logs are part of the Windows system, that are created by on a system and can be checked locally or remotely on regular intervals by an administrator or any user. These logs can then be imported and viewed in a SIEM tool to ensure efficient Incident Response.
Incident Response: Windows Account Management Event (Part 1)
Table of Contents
- Security Policy Settings
- Advantage of security settings
- Event Log
- Account Management Events
- Events in Windows Server 2016
Security Policy Settings
They are set of rules that an administrator uses to configure a computer or multiple devices for securing resources on a device or network. The Security Settings extension of the Local Group Policy Editor allows you to define a security configuration as part of a Group Policy Object (GPO).
The GPOs are linked to Active Directory containers such as sites, domains, or organizational units, and they enable you to manage security settings for multiple devices from any device joined to the domain. Security settings policies are used as part of your overall security implementation to help secure domain controllers, servers, clients, and other resources in your organization.
Advantage of Security Setting
- User is authenticated in a network or device.
- The defined resources that any user is permitted to access.
- Whether to record a user’s or group’s actions in the event log.
- Membership of a user in a group.
Event Log
The event logs usually keep a record of services from various sources and then stores them in a single place. Events logs can be of Security, System and Application event. As an incident responder, you should look for multiple sources of log information and should not forget to look at the older log files which may be present in backup systems or volume shadow copies.
When the Event logs are assessed, the Event ID have various field details with them;

Account Management Events
The Account Management is extremely important and these events can be used to track the maintenance of users, group, and computer objects in Local users and groups, Active Directory.
Account Management events can be used to track a new user account, any password resets, or any new members being added to groups or being deleted from the group.
The account management events can be categorised into different types:
Events in Windows Server 2016
Now, Switch on your Windows Server 2016 to get you started.
Event ID 4727

When you create a security-enabled – global(scope) group, then this event is generated.

Event ID 4728
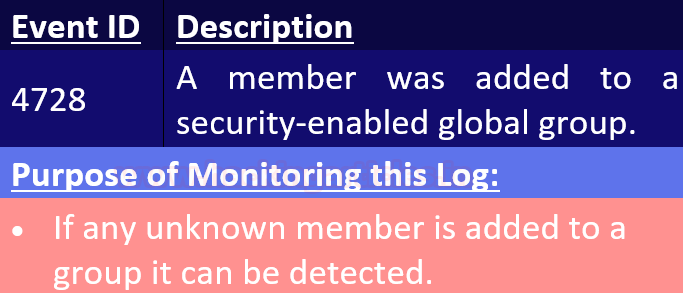
When you add a new member to a security-enabled -global group, then this event is generated.
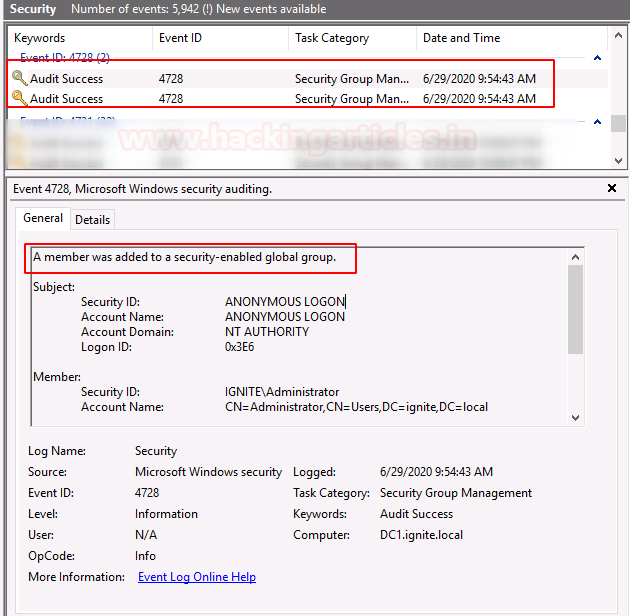
Event ID 4729

You can go to the properties of the user and remove the user from the group.
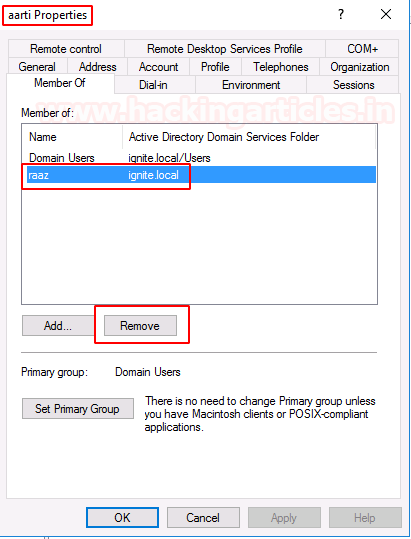
When a member is deleted from a group, this event is created.

Event ID 4737

When security enable group was changed, or any changes were made, this event was created.

Event ID 4741

Create a new computer account, using system properties by changing settings.

When a new computer account is created, this event is created

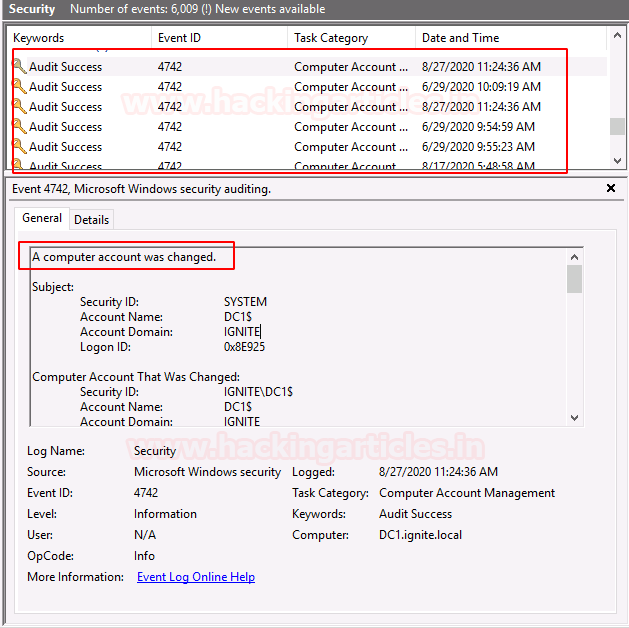
Event ID 4742
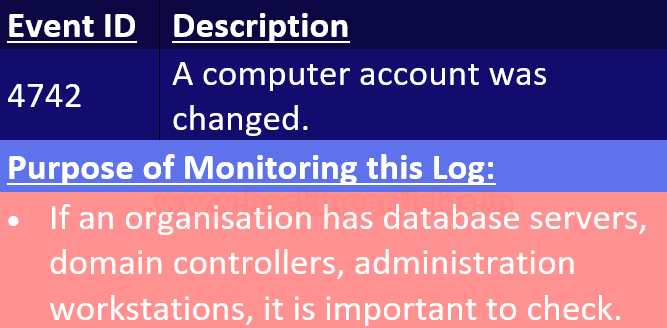
When any changes are made to the computer account, this event is generated.
Event ID 4743

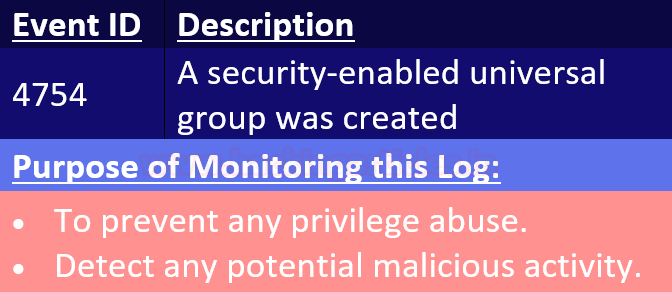
Event ID 4754
When a computer account is deleted, this event is generated.

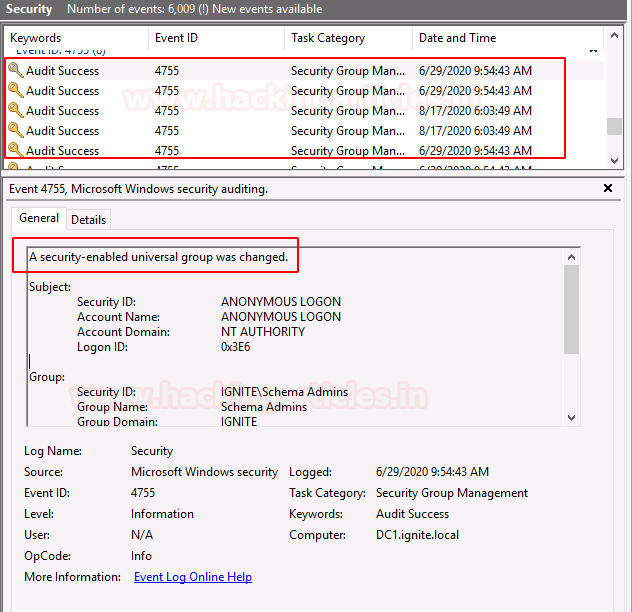
Event ID 4755

When any changes are made in a security-enabled universal(scope) group, this log is created.
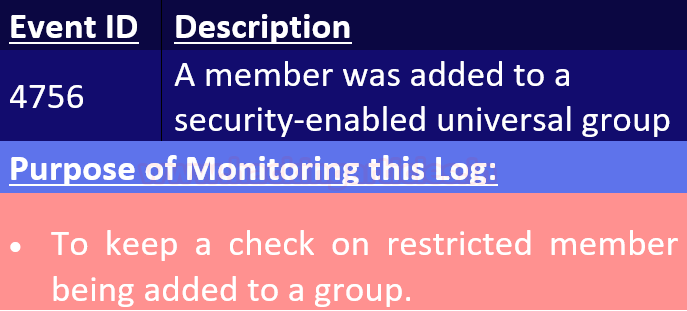
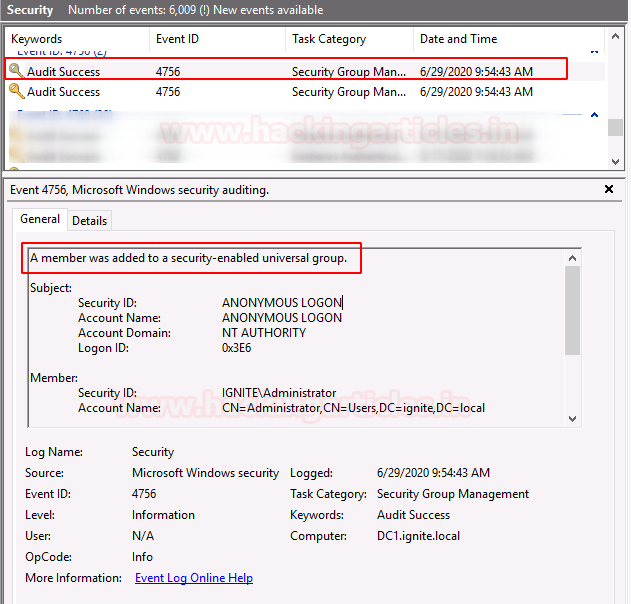
Event ID 4756
You can add the user to the group using
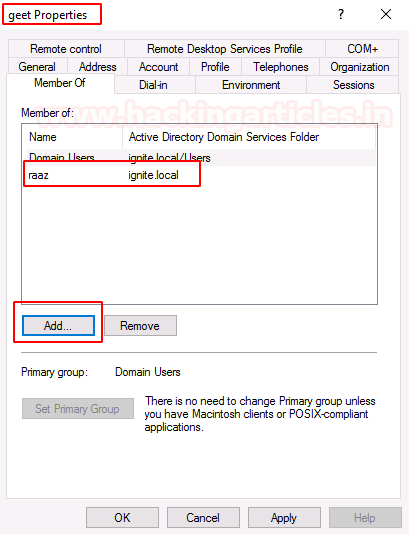
When a new member is added to a security-enabled universal group, add this event is created.
Event ID 4799

When a member from a group is enumerated, this event will be generated.

You can try out the below event ID using Domain Controller:
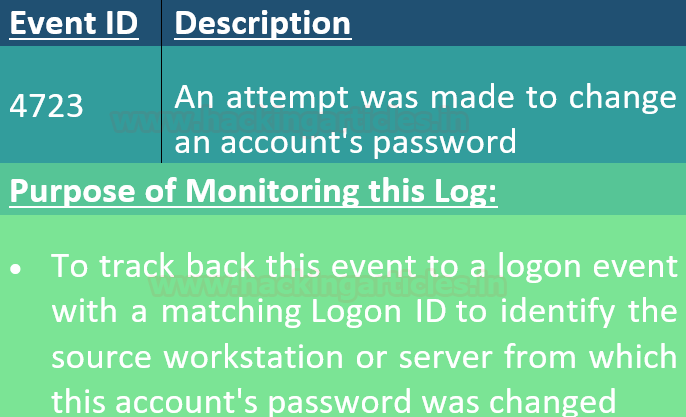
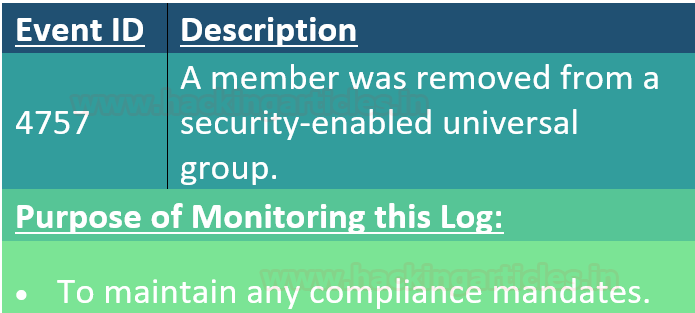
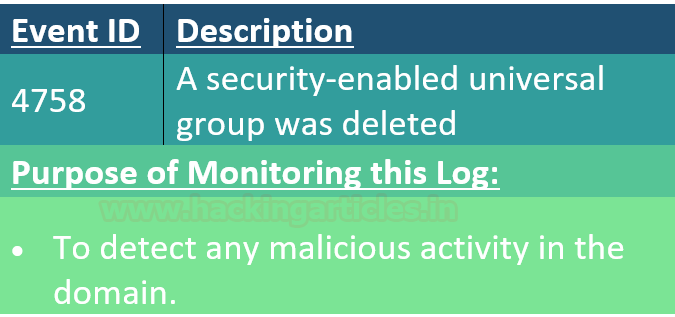
Conclusion: Hence, being an incident responder, you can maintain the activity of users using account management event in windows.
Author: Jeenali Kothari is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here