Empire for Pentester: Active Directory Enumeration
In this article, we take a look inside Active Directory through PowerShell Empire. PowerShell Empire consists of some post-exploitation modules inside the situational awareness section. PowerView is integrated inside the Empire to extract data from a Domain.
Table of Contents
- Introduction
- Get User
- Get Computer
- Get Loggedon
- Process Hunter
- Get OU
- Get Session
- Get Domain Controller
- Get Group
- Get Group Member
- Get Cached RDP Connection
- Find Local Admin Access
- Share Finder
- Get Subnet Ranges
- Get Forest
- Get Forest Domain
- Get GPO
- Get Domain Policy
- Get RDP Session
- Get Site
- Conclusion
Introduction
In our previous article focused on Active Directory Enumeration: PowerView, we discussed a ton of options some of those are also present in Empire so those can seem to be repeating the similar approach but there are some more interactive modules here that are worth looking into. We will be using the same Active Directory Lab configuration from the PowerView Article mentioned above. In this Article/Demonstration, we are focused on our ability to Enumerate Information that can be then further be used to elevate privileges or be able to help with Lateral Movement. A tool by the name of PowerView was developed and integrated by Will Schroeder (a.k.a harmj0y) for PowerSploit. It soon became an integral toolkit to perform Active Directory Attacks and Enumeration. We will be using PowerShell Empire to demonstrate the various Enumeration Tactics by PowerView.
What is Situational Awareness?
Situational Awareness is defined as: “Within a volume of time and space, the perception of an enterprise’s security posture and its threat environment; the comprehension/meaning of both taken together (risk); and the projection of their status into the near future.” In simpler terms learning and understanding the structure of any enterprise or network in a particular set of time while making a note of potential risks and making a plan of action is called Situational Awareness.
Get User
In our Active Directory Lab Setup, we created 8 users with different roles and privileges. Then when we emulate the attack on the AD from PowerShell Empire using Kali Linux as demonstrated, we generate the following result.
usemodule situational_awareness/network/powerview/get_user execute
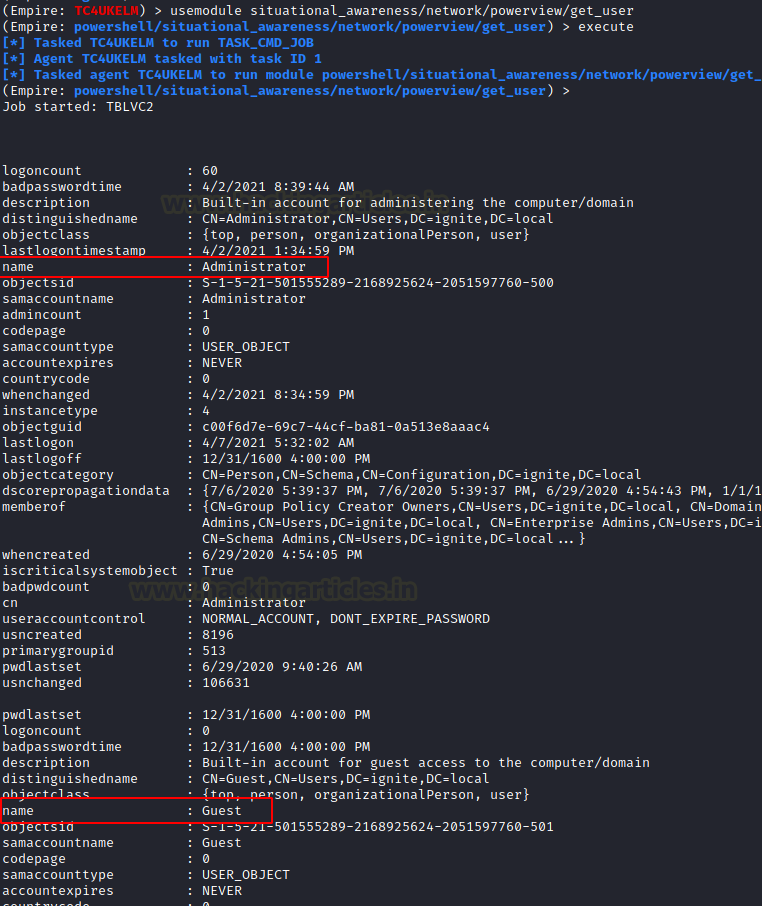
Users that are enumerated are not just restricted to Usernames. Data collected consist of logoncount that can give an idea of an active or inactive user in the network. Next, there is a badpasswordtime which tells the last time and date that an attempt to log on was made with an invalid password on this account. Then a small description of the user with the names of groups that this particular user is part of. At last, it shows the date and time since the last password change. All this information is very important when the attacker is trying to learn about the User Behavior.

Users Extracted are Administrator, Guest, Yashika, Geet. It is clear from the output that the user’s Administrator and Guest are the part of Users Group. This can be verified using our Active Directory Setup as shown below.

And the users Yashika, Geet, etc are part of Tech OU. More data will be extracted on OU later.

Get Computer
The next module that the attacker can use against the target server is the Get Computer module. The information this module target is primarily the Computer Name. It also extracts other information as demonstrated.
situational_awareness/network/powerview/get_computer execute

The output of the result that is generated by the module starts with information like pwdlastset information. This is the date and time when the user has reset their password. As discussed earlier it can help the attacker distinguish between active and inactive users. It can also help the user distinguish between the users that use proper security mechanisms and change passwords regularly and those who don’t. Moving on, it also prints the username that is logged in on the Computer. Then it informs the attacker about the Operating System that is running on the target machine.

The output also tells the attacker the last time when the target machine was logged off. This can also help differentiate among users. Some other information that is extracted contains the badpwdcount that tells the number of times an incorrect password was attempted on that particular machine. Then we have the when-created option that can help the attacker figure out the older accounts and relatively new users that are created on the target machine.
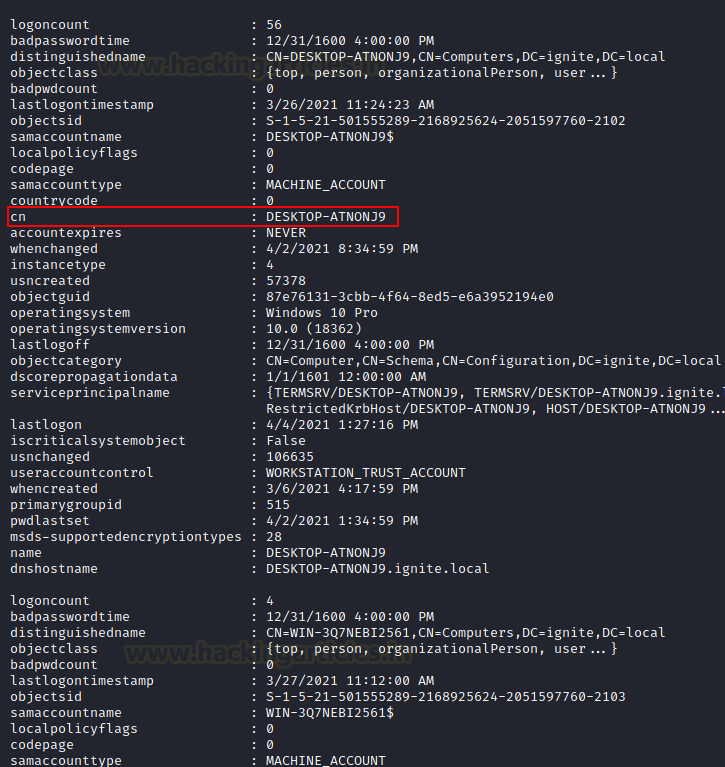
Moreover, the attacker can also enumerate the SID of the user and OU of that particular user that is logged in on the machine. This can also tell the attacker if a particular user is about to be expired or is it set to never expire. Then we have the Group Details of the user as well.

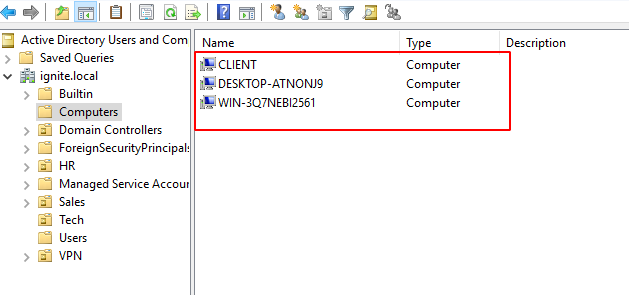
We can see that the output suggests that there are 3 machines in the Domain. Named as CLIENT, DESKTOP-ATNONJ9, and WIN-3Q7NEB12561. This can be verified from the Domain Controller as shown in the image below.
Get Loggedon
To enumerate users on the local or remote machine the attacker can take advantage of the GetLoggedon module. It should be noted that Administrative Rights are required to use this module. This module executes the NetWkstaUserEnum Win32API call to extract the users that are currently logged on. It can be observed the module has extracted the users that are logged in.
situational_awareness/network/powerview/get_loggedon execute

Process Hunter
Process Hunter module is an interesting one as it enumerates the running process on the target machine. It can help the attacker deduce a lot about its target. It can extract information about any services that might be vulnerable. It can tell if any process is running with elevated privileges. It also tells the Process ID of the process so if the attacker has access to that process, they can tinker around with it such as stopping or restarting such process.
situational_awareness/network/powerview/process_hunter execute
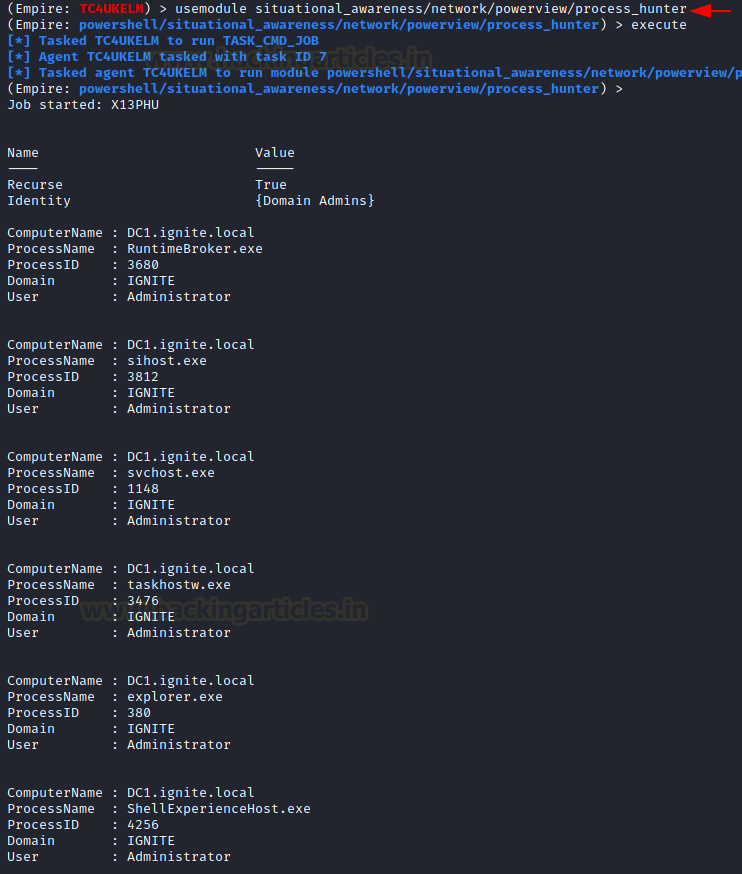
The correlation can be done between the extracted data from Process Hunter and the actual tasks running on the machine by listing the process on the target machine. It has been demonstrated below using the tasklist command. The PID can be used to verify the process status.

Get OU
OUs are the smallest unit in the Active Directory system. OU is abbreviated from is Organizational Unit. OUs are containers for users, groups, and computers, and they exist within a domain. OUs are useful when an administrator wants to deploy Group Policy settings to a subset of users, groups, and computers within your domain. OUs also allows Administrators to delegate admin tasks to users/groups without having to make him/her an administrator of the directory.
To Enumerate, Choose the Agent and then Load the module using the usemodule command. Then run execute the command.
usemodule situational_awareness/network/powerview/get_ou execute
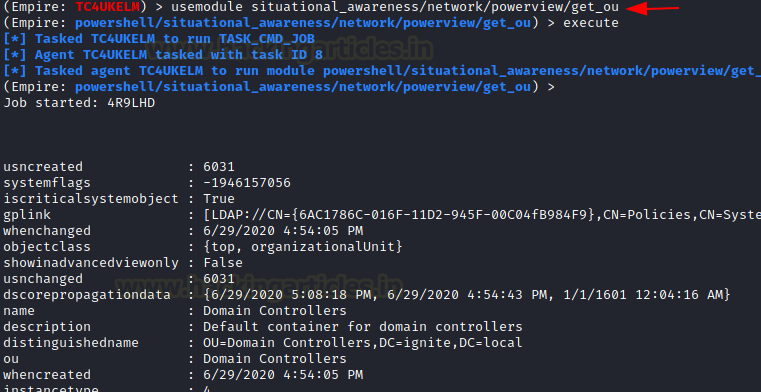
As soon as the module is executed, it contacts the Target Server and extracts the requested information and then PowerShell Empire starts to print the response. Information such as gplink, object class, name of OUs, Date and Time of Creation, etc is printed for each OUs.

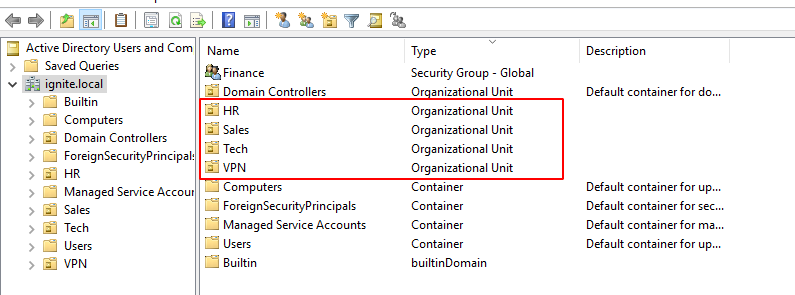
It can be observed that there are 4 OUs on the Target Server. Namely, Tech, VPN, Sales, and HR. To verify, we can take a look at the OUs directly from the Server. There are 4 OUs listed. This means that our module worked accurately.
Get Session
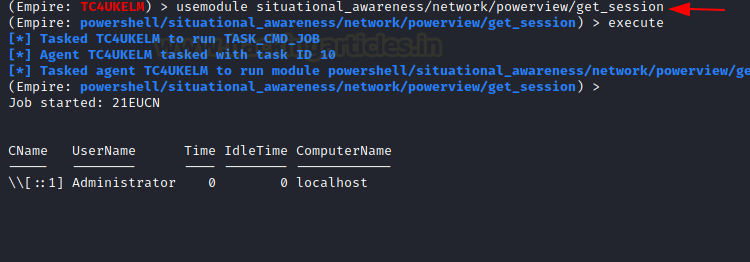
Get Session module can enumerate the sessions that are generated inside a Domain. Upon running this module, the attacker can extract the session information for the local or a remote machine. This function executes the NetSessionEnum Win32API call for extracting the session information.
situational_awareness/network/powerview/get_session execute
Get Domain Controller
Next on the lineup, we have the Get DomainController. This provides the information of the particular server device instead of the domain. When an attacker wants to extract the data about the Domain Controller Machine then this tool can be used. It extracts the Forest Information, with the Time and Date configured on the Server. It tells the OS Version that can help constraint the search for Kernel Exploits for the attacker. Then the attacker has the IP Addressing data with the Inbound and Outbound connections.
situational_awareness/network/powerview/get_domain_controller execute

Get Group
Enumerating group information is one of the most important pieces of information an attacker should enumerate on its target. Group Information categories the uses and helps understand the users that have the high privilege or they might be the one that has the access to a particular database. This can be performed using the get group module as demonstrated.
situational_awareness/network/powerview/get_group execute

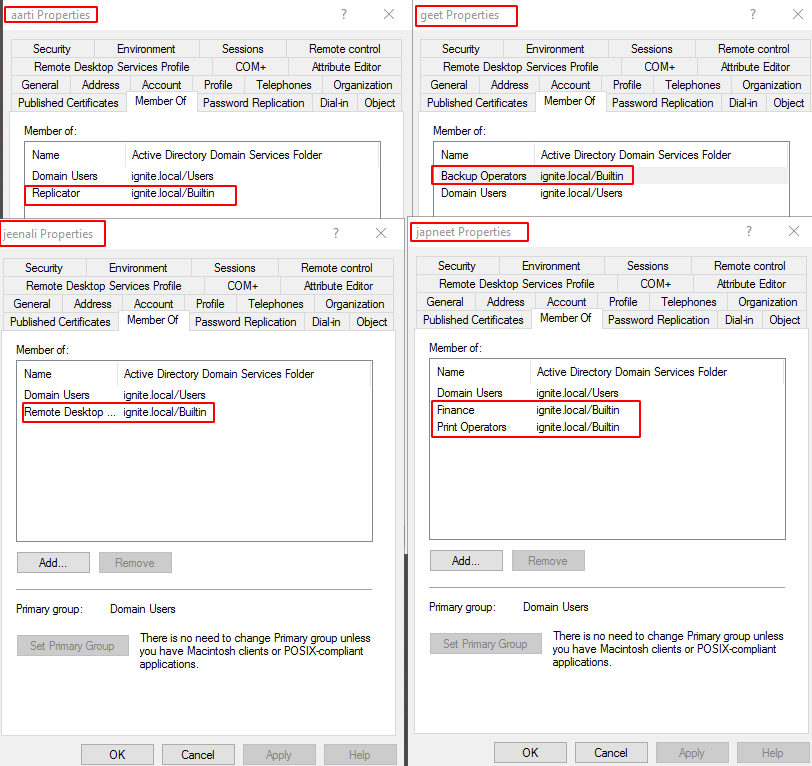
Upon analyzing the output of the module that we just discussed, we can see that we get a group by the name of Print Operators. To find the user inside that particular group there is a parameter named member. It can be seen that user Japneet is a part of the Print Operators group. Similarly, the Backup Operators group has the user geet. The interesting part about the backup operators is that they can read almost all the files on the system as you cannot make a backup of a file that you don’t have permission to read. Hence it is worth trying to take over the user that is a part of the Backup Operators group.
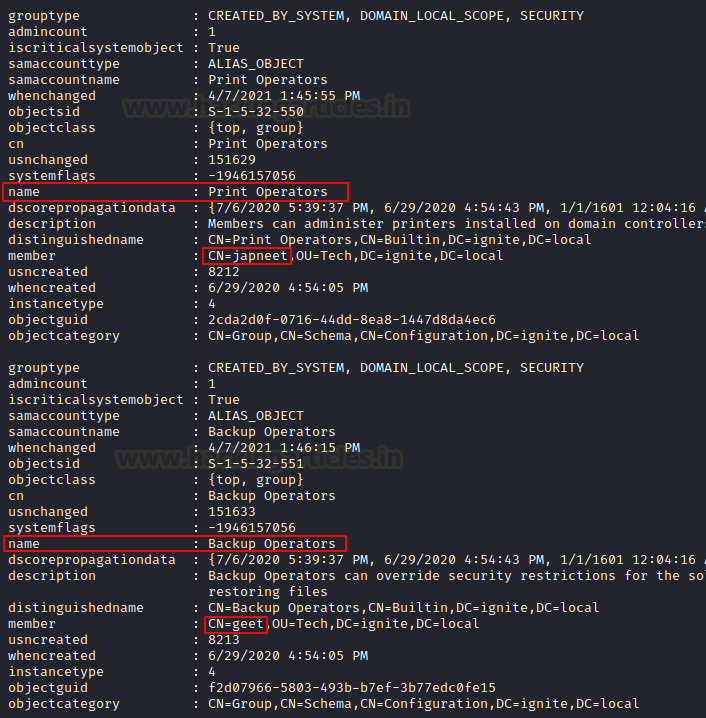
Moving down the output we can see that there is a group by the name of Replicator. The member of Replicator is an aarti user. The members of this group can replicate the Active Directory Architecture. Next, we have the Remote Desktop Users group. This is also a group if compromised can pose disastrous consequences. This a group of users that have the privilege to access the desktop users. As can be observed from the screenshot the Jeenali user is a member of the Remote Desktop Users group.

All the information that we extracted using the PowerView Module can be directly verified from the Domain Controller by checking the Properties of users. The properties will have a tab named Member Of. It will contain the name of the group that the user is part of.
Get Group Member
In the previous stage, we extracted the groups from usernames but this next module named get group member does the exact opposite. It requires the attacker to provide a group name and then it works to extract all the members of that particular user. In the demonstration below, we try to enumerate the users of the Domain Admin group. The module tells us that the Yashika user a member of the Domain Admin Group.
situational_awareness/network/powerview/get_group_member set Recursive "Domain Admins" execute

As always this can be simply verified on the Domain Controller by running the net group command with the group whose member you are trying to enumerate.

Get Cached RDP Connection
RDP or Remote Desktop Connections are one of the most used functionalities that are used in an enterprise. The work of induvial employees is also heavily dependent on the Remote Desktop connections while working from home. Windows can cache the devices that the user is trying to connect to using RDP. The get cached RDP connection uses remote registry functionality to query all entries for the “Windows Remote Desktop Connection Client” on the local (or a remote) machine
situational_awareness/network/powerview/get_cached_rdpconnection execute

As can be observed from the above image that the module has extracted 2 users that are supposed to be cached in the registry of the target machine. This can be verified from the RDP Connection Windows as shown below. The IP Address 192.168.1.16 and 192.168.1.45 are the devices that are controlled using RDP. This can help the attacker map other machines in the network and it also informs the attacker that RDP is enabled on these machines.

Find Local Administered Access
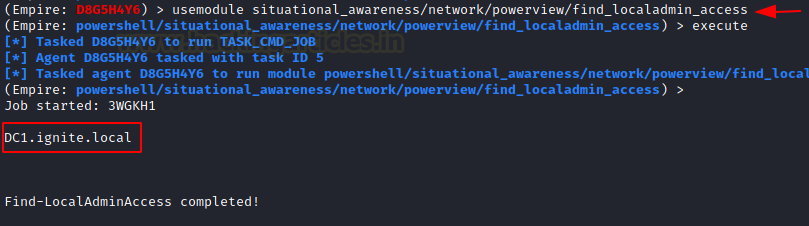
This next module helps that attacker to enumerate where the current user has local administration access. In simpler terms, it enumerates all machines on the current domain and for each machine, it checks if the current users have local administrator access. From the demonstration, it can be concluded that DC1 user has local administration access on this machine only.
situational_awareness/network/powerview/find_localadmin_access execute
Share Finder
As the name suggests that this module can help the attacker extract shares hosted on the network. Any inexperienced attacker can tell that why is there a need for enumerating the shares when that can be done externally using the SMB enumeration. But an experienced attacker will know that some shares are not visible for all. It can be configured as to if that particular share is visible and accessible to all or some specific user.
situational_awareness/network/powerview/share_finder execute

From the module above and the image of Server Manager below it can be seen that there shares by the name of Confidential and Sales Report in the network.

Get Subnet Ranges
Enumerating Subnets may seem like not a useful idea but there is something that could help the attacker to understand how the domain is laid out. Several hosts are connected to this particular subnet. It can also inform the attacker of other subnets in which the network is divided. In the demonstration below, there are 4 hosts connected to this particular subnet. That would probably split into 3 clients.
situational_awareness/network/powerview/get_subnet_ranges execute

Get Forest
Apart from the domain information and the user information, the attacker can also gain information about the forests and there can be multiple forests inside a domain. To procure information about the forest in the current user’s domain is to use the get forest module.
situational_awareness/network/powerview/get_forest execute

Get Forest Domain
In simpler terms, a domain is a set of computers inside a boundary, which have a particular rule for accessing data and administering data values. Domains are situated inside trees. It can be said that a tree is a group or collection of domains that are arranged systematically bearing the same namespace. To enumerate the Forest Domain details including the name of the forest with its children and Domain Level then the attacker can use the get forest domain module.
situational_awareness/network/powerview/get_forest_domain execute

Get GPO
A Group Policy is created to figure out how the Domain is set up and what set of rules and policies are designed by the Administrator to govern the Domain. This can be enumerated using this module. It will extract all the information regarding Group Policies that are configured on the Target System.
situational_awareness/network/powerview/get_gpo execute

Get Domain Policy
The Domain Policy of a Domain can reveal some information such as extracting the policy of the current domain. It reads the default domain policy or the domain controller policy for the current domain or a specified domain/domain controller. In the demonstration, it can be observer a set of System Access Policy defined which include the Password Expiration Time and Minimum Password Length.
situational_awareness/network/powerview/get_domain_policy execute

This can be verified from the Group Policy Management Editor on the Domain Controller. You can create more policies and just configure other policies.

Get RDP Session
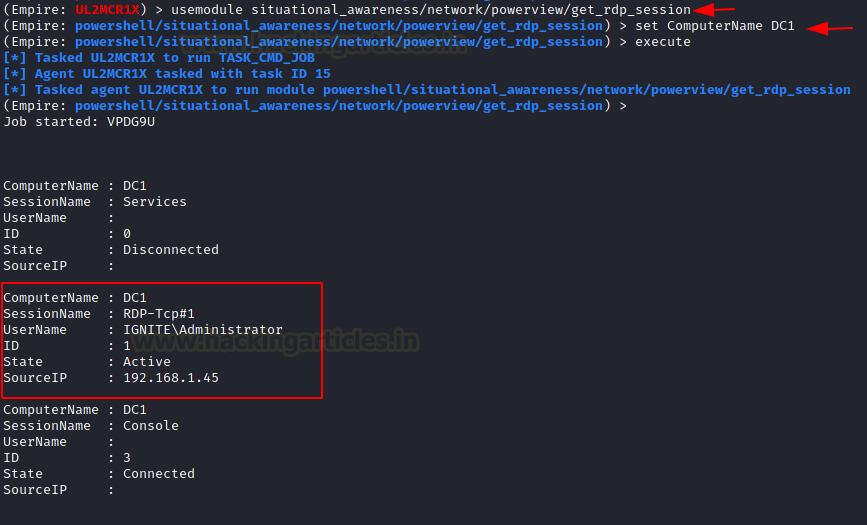
This module enumerates the remote (or local) RDP sessions on a remote machine that the Administrator has access to. It also pulls in the originating IP of the connection as well. In the demonstration, it can be observed that there are 3 connections one of them is the Active with an IP of 192.168.1.45. The attacker can also provide the ComputerName option to get refined results.
situational_awareness/network/powerview/get_rdp_session set ComputerName DC1 execute
Get Site
Finally, this module enumerates and provides the attacker with a list of all the sites in the current domain. This can help the attacker to get details about the sites and their location. Coupled with other vulnerabilities this kind of information can lead to big attacks.
situational_awareness/network/powerview/get_site execute

Conclusion
This concludes our second article on Active Directory. It is still a very extensive topic. We provide this detailed resource so that you can enumerate your Active Directory Deployment from Kali and with the help of PowerShell Empire and understand the information that an attacker can extract. If you want a direct PowerShell-based enumeration, check out this article.
Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn